Zero Trust is a strategic framework that enhances security and reduces the risk of breaches. It treats every user and device as a potential threat, requiring verification at every step rather than assuming everything inside the network is safe.
Due to its complexities, implementing Zero Trust can be challenging, including the need for extensive setup or system adjustments. However, the benefits of Zero Trust are substantial, offering secure access, improved compliance, and fortifying companies’ cybersecurity posture.
Zero Trust definition
The Zero Trust security model follows the principle of "Never trust, always verify." It means not automatically trusting every user or device inside the network. This approach helps prevent breaches.
The Zero Trust security: key takeaways
- Understanding Zero Trust security: the Zero Trust security model is a vital network strategy where trust is never assumed. Every user and device is verified, enhancing network security and preventing breaches.
- How Zero Trust works: Zero Trust network access involves continuous verification, ensuring a secure and resilient network.
- Key aspects of Zero Trust: it's a strategic approach, not just technology. It extends beyond traditional network boundaries and involves rigorous verification within the network.
- Benefits and challenges of Zero Trust: it ensures secure access and robust network security. It also enhances compliance and endpoint security but can be complex to implement and require frequent updates.
- Implementing Zero Trust security should focus on network segmentation and identity verification.
- The key elements of Zero Trust Architecture: user identity is critical in managing access rights and monitoring, ensuring each person gets appropriate access. Device control ensures secure network access, with each device being thoroughly verified. The network itself is segmented to enhance control and security.
Core Zero Trust principles
Zero Trust security is an approach that doesn't automatically trust any user or device inside and outside networks. It enforces mandatory checks at every access step, keeping network strict network control. And ensures network security.
Zero Trust treats all network traffic as untrustworthy, whether it comes from inside or outside. Connections from your internal network's inside could be just as malicious as those from external networks.
As modern enterprise IT infrastructures are extensive, monitoring everything in the network can be very challenging. Just because a device is already inside your perimeter doesn't mean its user has good intentions. Zero Trust enforces stricter controls for each user, regardless of where they connect from.
The key defense in the Zero Trust security model is thorough authentication and re-authorization for every data access. It's a radical shift from previous perimeter-based security models that trusted connections based on their network location. With digital transformation making network boundaries vague, relying on a perimeter for security is outdated.
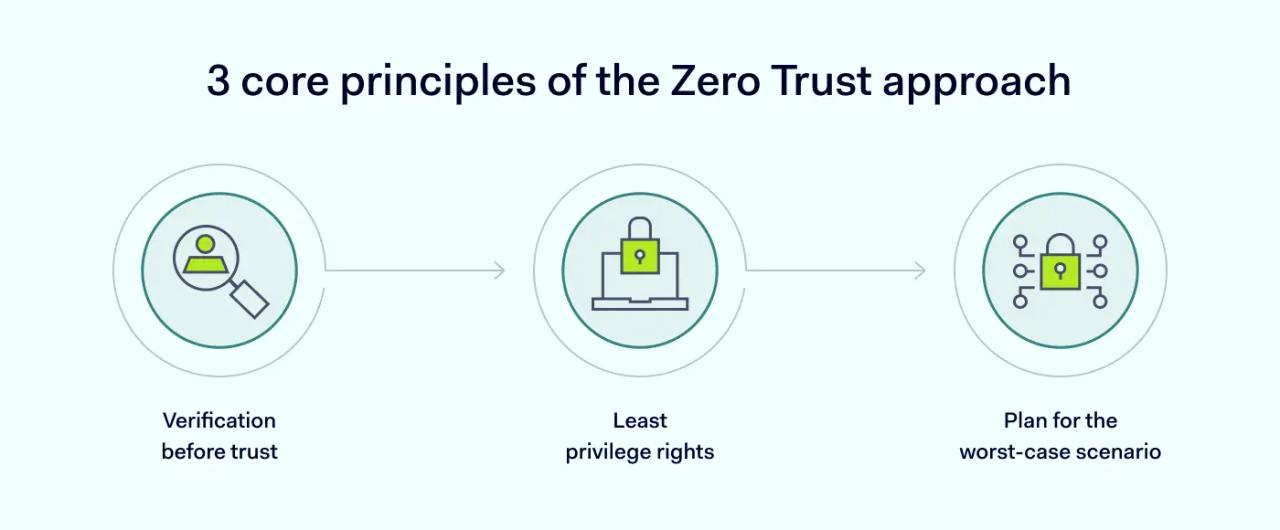
Three core principles of the Zero Trust approach include:
- Verification before trust : every time a user or a device connects, it's essential to verify their access rights.
- The least privileged rights: users should be given essential access rights they need for their job. Additional rights should be granted only if it is necessary for their tasks.
- A plan for the worst-case scenario : consider a data breach a real threat and shrink the total attack surface to a minimum.
Pros and cons of Zero Trust security
The Zero Trust core principle, "Never trust, always verify," helps protect your team, data, and organization. Here is a list of Zero Trust benefits for modern businesses:
- Cloud adaptability: Zero Trust offers a dynamic and scalable solution tailored for cloud-based networking, aligning with modern business needs.
- Remote work compatibility: Zero Trust ensures secure and efficient operations for organizations embracing remote work, regardless of location.
- Efficiency through SSO: Single Sign-On (SSO) simplifies access management, enhancing productivity by consolidating authentication across services.
- Centralized visibility: Provides leaders with comprehensive network activity and user behavior oversight, facilitating proactive security management.
- Robust security measures: incorporates encryption, Privileged Access Management (PAM), microsegmentation, and continuous monitoring to fortify defenses against cyber threats.
- Compliance and audit readiness: Streamlines compliance efforts with enhanced data security and clear audit trails, easing the regulatory burden.
Despite its many benefits, Zero Trust can also have its drawbacks—the list of potential Zero Trust challenges includes:
- Complex implementation : transitioning to a Zero Trust architecture requires careful planning and execution to minimize disruption and ensure continuity.
- Security strategy overhaul: adopting Zero Trust requires a thorough review of existing security protocols to prevent potential vulnerabilities during the switch.
- Legacy system compatibility: integration with older applications may present challenges, requiring strategic updates or replacements to maintain security integrity.
- Initial investment: the upfront costs of adopting Zero Trust can be significant
How does the Zero Trust model work?
First verify, then double-check, then decide if you can trust a device or a user. That's, in short, the ground rule of Zero Trust. Let's have a look at how this model works:
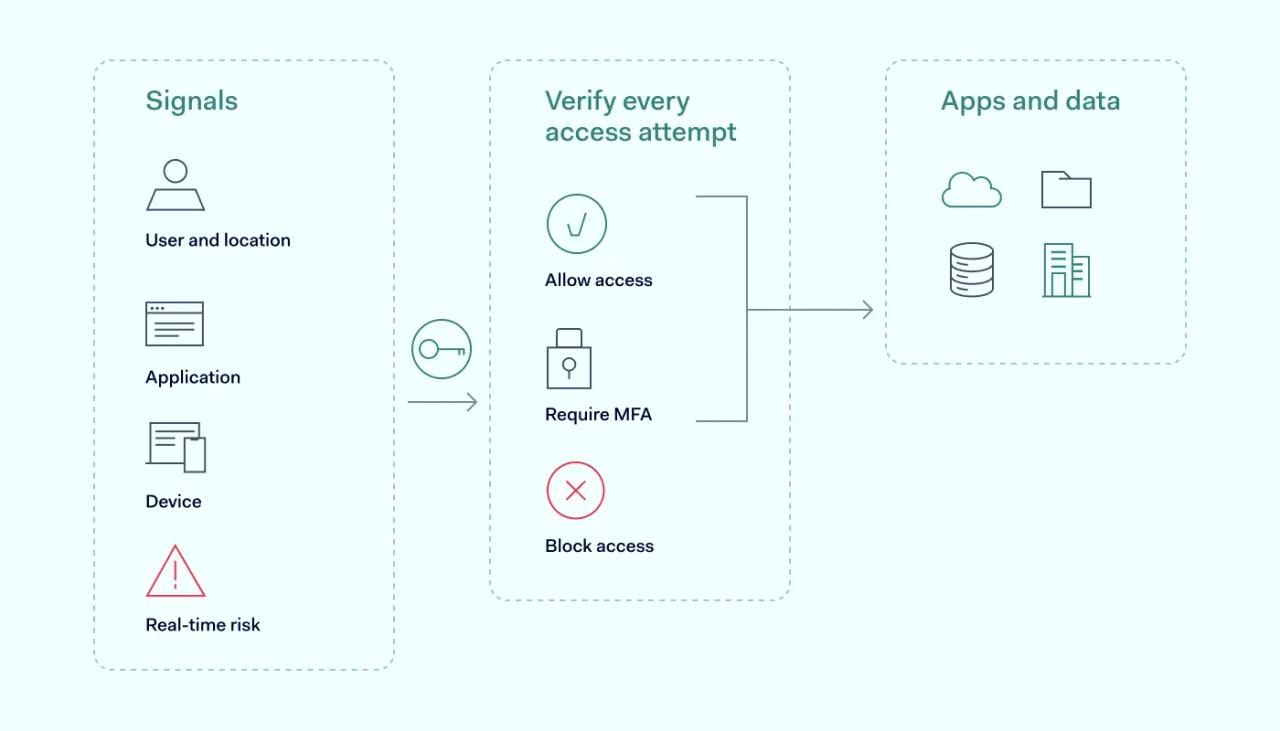
As we can see, the Zero Trust model is like a vigilant security system that constantly verifies every user and every device. It ensures trust is always earned, providing a strong defense against ever-changing cyber threats.
Zero Trust architecture and its requirements
The Zero Trust principles apply the Zero Trust security strategy to a practical IT infrastructure planning framework. Using the Zero Trust approach as a core design philosophy, various network components are added to implement mechanisms for strict access control.
Zero Trust network access offers a more flexible alternative without emphasizing assets or network location.
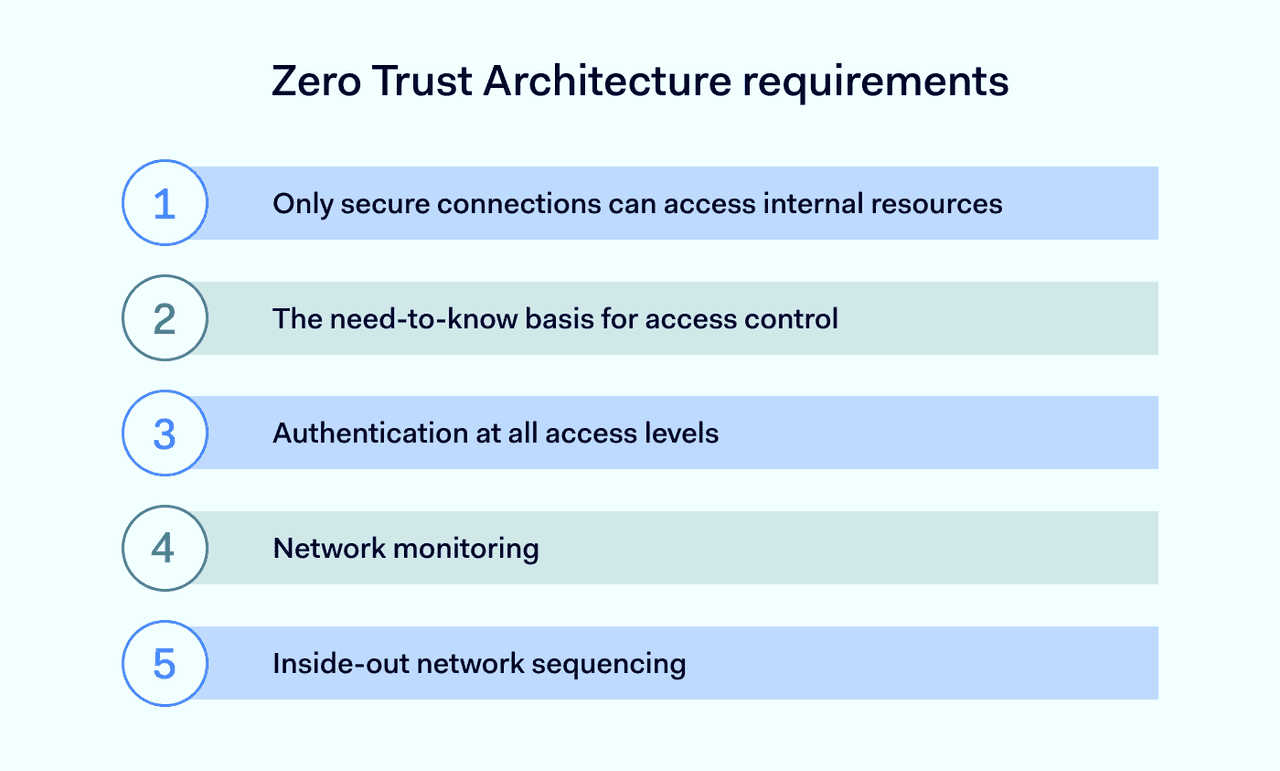
Some requirements apply when building a Zero Trust network:
1. Only secure connections can access internal resources
Technologies like VPN can help encrypt data in transit, preventing hijacking. This ensures that only verified connections interact with your network. By doing this, the integrity and confidentiality of data are maintained, safeguarding against external threats.
2. Need-to-know basis for access control
Granting only limited access rights prevents privilege escalation and limits potential damage from compromised accounts. This access strategy minimizes risk exposure and ensures that users can only reach the information essential for their roles.
3. Authentication at all access levels
Users must authenticate at network entry and undergo additional checks for specific data, reinforcing security at each step. This multi-layered approach, deeply rooted in user identity verification, ensures that each interaction within the network is validated, adding depth to the security protocol.
4. Network monitoring
Constant surveillance of your network detects unusual behavior, helping to prevent breaches before they escalate. This ongoing vigilance allows for quick response to threats and continuous adaptation of security measures.
5. Inside-out network sequencing
Start with stringent controls inside the network, then apply these rules outward, ensuring a solid core that's progressively secured. It first fortifies the most critical assets, then layers security outward, creating a comprehensive protective shield.
These Zero Trust principles team up to add extra checks, making it harder for attackers to get into the network. Even if they breach the perimeter, they can't access much due to strict authorization checks.
Trends like using personal devices (BYOD) for work and remote work have boosted the popularity of Zero Trust. Its design is evolving as more people connect from outside the traditional network. In 2021, the U.S. government started requiring Zero Trust across all departments, and it's useful for companies dealing with sensitive data.
Zero Trust is a forward-thinking strategy that's set to grow in importance, helping to protect against threats from both inside and outside an organization.
6 pillars of Zero Trust
The Zero Trust Architecture (ZTA) model is grounded in six fundamental pillars that form its backbone. They are essential for a robust and effective Zero Trust strategy.
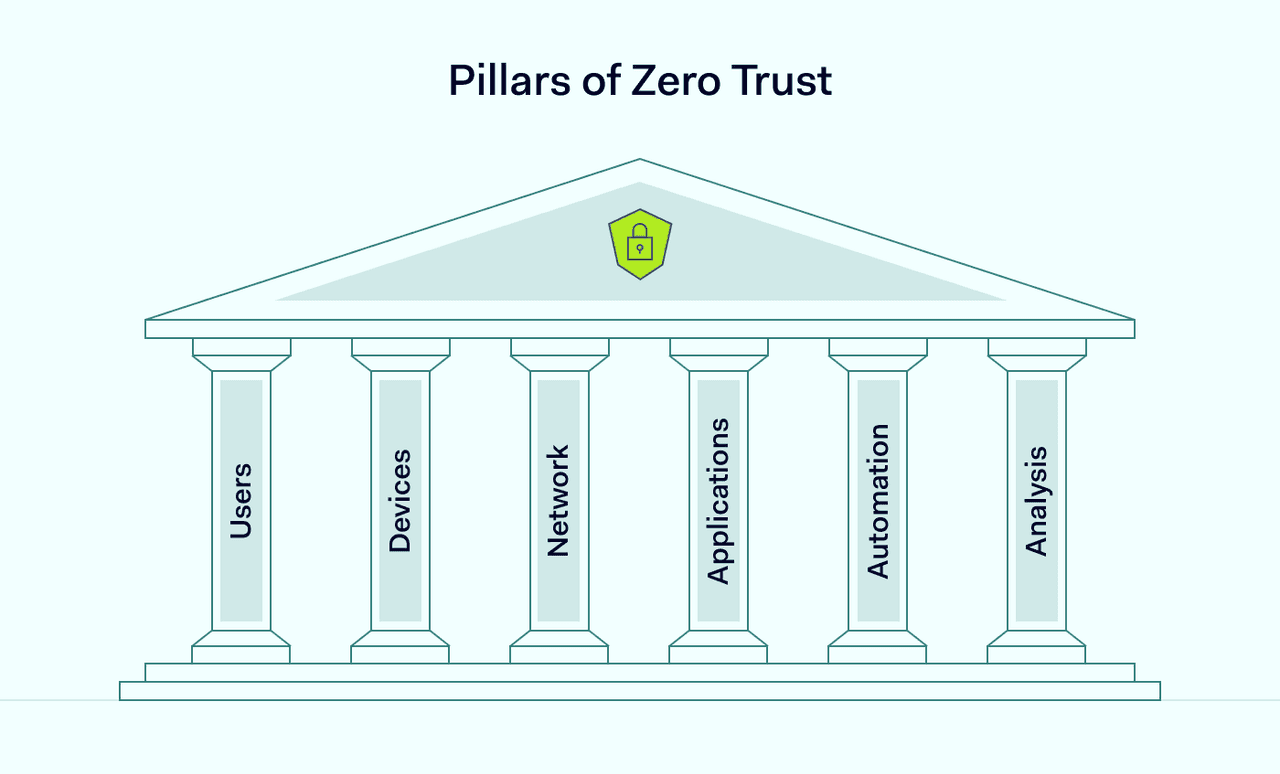
#1 Users
Users are crucial in the Zero Trust framework as they can be targets for cyber-attacks. It's important to manage their access rights carefully, limiting them enough to secure the network but not so much that it hinders their work. This requires strong authentication tools and ongoing monitoring.
#2 Devices
With more devices connecting to networks, controlling each device is vital in Zero Trust. This means possibly removing devices that pose a threat and using methods like allowlisting to permit only certain devices on the network.
#3 Network
Network administrators should segment internal networks into smaller subsections to ensure better oversight and control. Access should be limited to only those users who need specific resources. With micro-segmentation and data-focused approaches, the Zero Trust approach focuses more on protecting data than just securing the perimeter.
#4 Applications
Used applications should be monitored, and their execution controlled within the company's network and the cloud. Controlling access at the application level is paramount when implementing the Zero Trust model. Each such component used within an enterprise is a potential attack vector and shouldn't be taken lightly.
#5 Automation
Automated monitoring and controlling application use within the network and cloud is key. It is one of the most important tools when detecting suspicious behavior or real-time threats. Each application is a potential risk, so controlling access at this level is crucial in Zero Trust. Automation also frees up admins' time to spend on other, more complex tasks.
#6 Analysis
Tools like security information management systems (SIM) or security user behavioral analytics (SUBA) provide insights into network activity. Regardless of network location, device, and user count, better visibility also contributes to the company's overall security.
This helps in preparing for threats, not just reacting to them. The difference between Zero Trust and traditional security is invisible to users, as all changes occur behind the scenes.
NIST 800-207 and Zero Trust
In 2020, the National Institute of Standards and Technology (NIST) released a guide detailing the Zero Trust Architecture model. This guide describes what to focus on when building a secure Zero Trust network:
- Use software-defined perimeter
- Break the network into segments with their own rules and access policies.
- Verify identities and adjust access based on context.
A Zero Trust Architecture deployment in a business consists of several key parts. These can be managed either on-site or through cloud services. This basic model below shows how these parts interact:
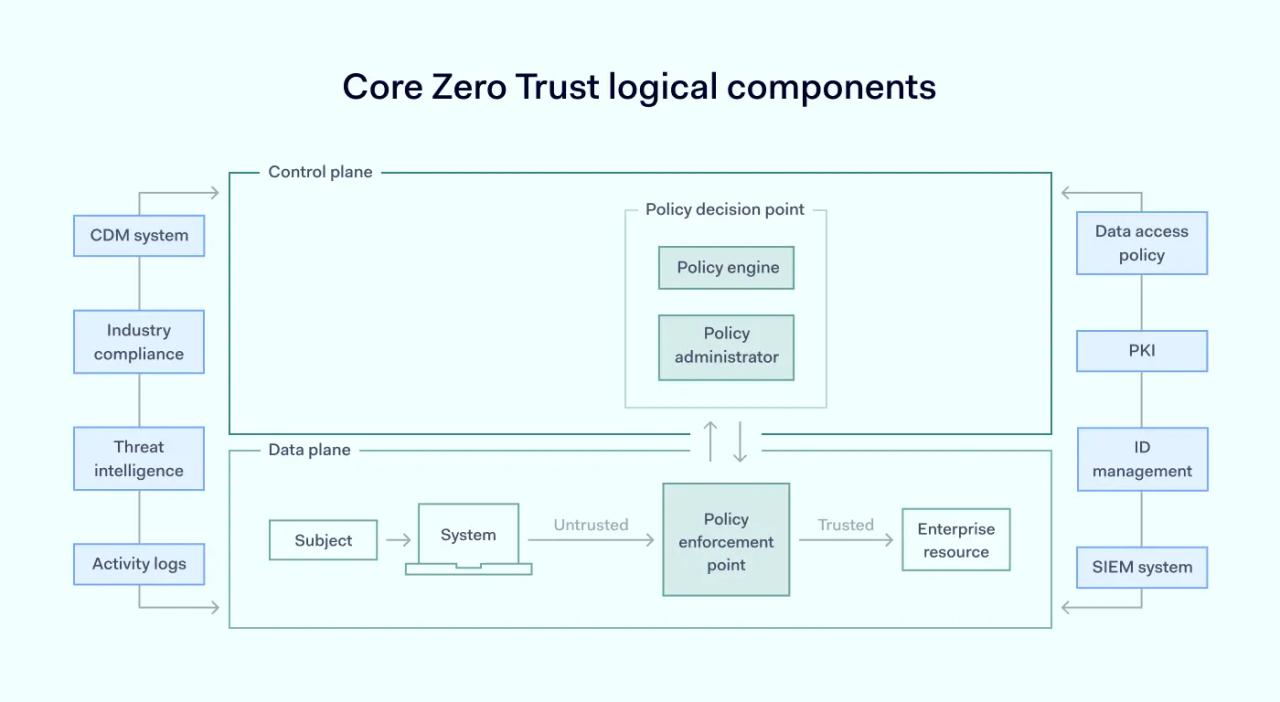
In this ideal setup, the policy decision point is split into two parts: the policy engine and the policy administrator. ZTA's components communicate via a separate control channel, while the application data moves through a different channel.
Here is how these components of Zero Trust work:
- Policy engine: allows or denies the user access to company resources.
- Policy enforcement point (PEP): monitors connections between a user and company resources.
- Policy administrator: an intermediary between the policy engine and PEP. It sends commands to PEP depending on the policy engine's decision.
It's important to note the flexibility in the implementation of these components. They don't have to be separate entities; they can be integrated into a single asset. Conversely, several different assets might handle just one component.
Zero Trust security for enterprises
Implementing Zero Trust in your business means rethinking how you manage users, applications, and infrastructure . It involves seeing users as both potential risks and assets, with a focus on robust identity verification and limited access.
The Zero Trust approach also shifts the emphasis from network connectivity to application access, which helps minimize attack surfaces. In this model, infrastructure primarily facilitates connectivity, with the main security emphasis on network policies. This strategic shift aligns well with modern cybersecurity challenges, making it a key business move.
Discover NordLayer's Zero Trust solutions to explore how this approach can be integrated into your business, enhancing your security posture.