If you’ve been wondering what SASE is, it’s an abbreviation for Secure Access Service Edge. It’s a cybersecurity framework combining various networking and security technologies into a single cloud-based platform. This facilitates IT infrastructure management encompassing all aspects of network security capabilities.
As more businesses move from premises-based IT assets to data centers, SASE effectively responds to modern cybersecurity needs. Globally distributed organizations can take advantage of the solution’s flexibility and ability to create a secure dome around every user, no matter where they are located physically.
What is SASE?
SASE, or Secure Access Service Edge, combines network security functions with wide-area networking (WAN) capabilities to support the dynamic, secure access needs of organizations. It connects and secures remote users, offices, and data centers to the applications and resources they need, no matter where they are located or hosted.
SASE simplifies traditional network architectures, making security seamless and management more centralized, especially in cloud-centric environments.
Key takeaways
- Unified cybersecurity solution: SASE is a blend of networking and security in a cloud-based platform, providing a comprehensive cybersecurity framework.
- Cloud-centric flexibility: it adapts to the shift towards cloud-based IT assets, offering scalable and cost-effective security solutions.
- Global protection: SASE ensures secure access for users anywhere, making it ideal for distributed organizations.
- Simplified IT management: it integrates various security technologies into one platform, streamlining network management and security.
- Zero Trust security: by implementing a Zero Trust approach, SASE requires strict verification for every access attempt, enhancing overall security.
- Cost and performance benefits: SASE offers potential cost savings and performance improvements by consolidating services and reducing infrastructure complexity.
- Future-Ready: as a forward-thinking model, SASE addresses modern cybersecurity challenges, supporting remote work and digital transformation efforts.
SASE architecture
IT security was focused inward for a long time: all your employees were in a single building. Therefore, network administrators’ main task was ensuring that your on-premise assets were secure. However, after the pandemic pushed employees to work remotely, and the approach to security had to change with network and security services.
SASE architecture is a new chapter in cybersecurity cloud services, solving problems that previous methods can’t tackle. It’s a unified method that treats all risk channels with the same attention, providing a holistic overview of the network’s health.
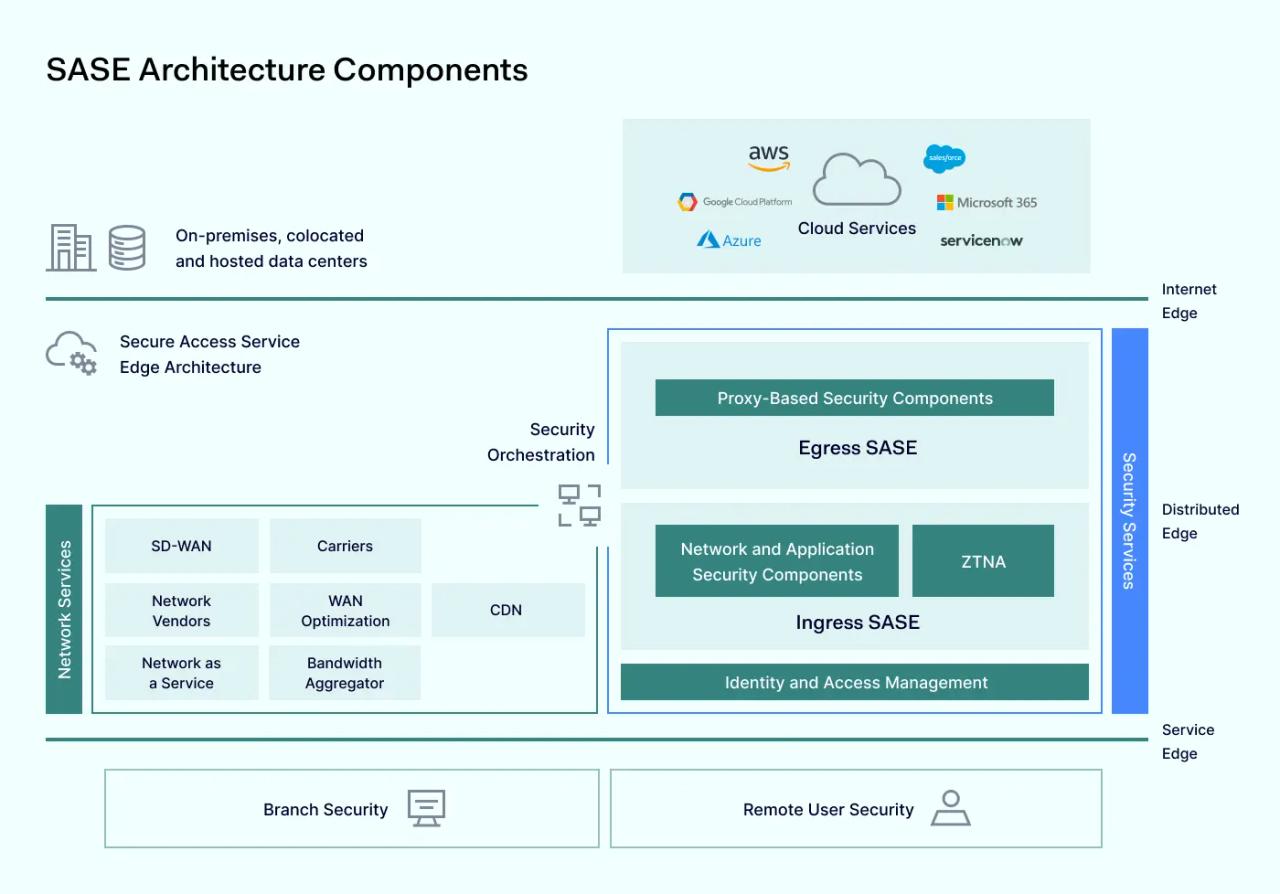
The sum of SASE’s parts consists of cloud-native security components, Zero Trust applied principles, and network service groundworks. Let’s look at each of these networking and security capabilities encompassing SASE.
1. Cloud-based infrastructure
SASE deployment is closely related to moving IT infrastructure to the cloud. This cloud-first approach helps ensure service accessibility and balance the server load. Cloud infrastructure offers the benefits of easy scalability, saving business costs, and paying only for used resources.
2. Zero Trust approach
A central component of SASE infrastructure is adapting the Zero Trust approach to cybersecurity. According to it, the connection shouldn’t be given trust based on its network location. The threats shouldn’t be expected only from the external network. All connections can be potentially harmful. Therefore, tighter access controls are needed to ensure that each user is who they claim to be.
3. Network components
Even though SASE rejects the notion that the internal network shouldn’t be considered safer, this doesn’t mean that the idea of a closed-off connectivity hub is obsolete. However, WAN functionality should be integrated into the framework to ensure tighter controls across all network planes.
SASE components
SASE relies on several interlinked technologies to create a universal cybersecurity solution covering all the bases. While using each of its components separately is completely viable, the main benefit of SASE is that it takes advantage of a single control center. The data and security policies are universal across the board, and each component works together.

- Firewall as a Service (FWaaS)—the backbone of network security, simplifying IT infrastructure by providing additional capabilities like next-generation firewalls, intrusion prevention systems, and other features.
- Secure Web Gateway (SWG)—you can think of SWGs as a secure access tunnel between the users’ endpoints and the Internet. To ensure the device’s security, SWG acts as a filter to block potentially malicious traffic before it can harm the user’s device. Therefore, it functions as a handy precaution against insider threats and may detect phishing links.
- Cloud Access Security Broker (CASB)—security policy enforcement point ensuring access and authorization to third-party applications. Essentially, it’s an intermediary that checks for authorization and grants or denies permission to access work resources. While it may seem like a nuisance for end-users, it can be a very effective policing tool that helps to ensure that set security policies are enforced for top-notch network security.
- Zero Trust Network Access (ZTNA)—as a practical implementation of the Zero Trust philosophy, ZTNA ensures that each access request passes authorization. ZTNA solutions can be in-depth and evaluate traits like connections, IP addresses, advanced context evaluation, and multifactor authentication.
- Software-defined WAN—virtual WAN setup allowing the connection of devices using various transport channels. This optimizes the network traffic and balances the load, taking advantage of multiple points of presence. The traffic is rerouted to SaaS providers, avoiding backhauling and wasting the company’s resources.
How SASE works
SASE merges several technologies into a unified solution to protect all network areas. The added value is created through their synergy as each component adds up to create a fully-fledged network security solution. All of them are active simultaneously to provide instantaneous data sharing within the framework.
The built-in systems supervise the user at every step of the connection. While most actions are invisible to the end-user, strict authentication procedures, web filters, and firewall blocks are always active. The system can also independently detect usage anomalies and flag network administrators asking for manual intervention when needed.
As the whole framework is realized with the help of cloud computing, this also provides unlimited remote access from any location. The user’s connections are passed to the nearest points of presence and routed to the assigned location, provided that authorization is passed. It’s a much more forward-thinking approach to solving the drawbacks of VPNs, like security and latency.
How can organizations benefit from a SASE model?
Secure Service Access Edge implementation can contribute to an organization’s digital transformation in many network and security functions.
Better flexibility—cloud-based infrastructure is much better suited for quick scaling with a much lower upfront cost. The benefits apply to end-users with lower latency when connecting from diverse locations.
Cost savings—separately implementing each SASE component can be very expensive. In addition, it may not bring the expected benefits as the ecosystem is lost due to different ways different providers set up their services.
Infrastructure streamlining—SASE can help declutter your infrastructure by minimizing the total number of IT assets that must be supervised. Centralized UI helps monitor everything happening on the network with greater efficiency.
Better performance—SASE facilitates the user’s connection to the third-party resources without backhauling. Users don’t have to deal with congested VPN gateways and can focus on productivity rather than troubleshooting.
Forward-thinking security—SASE includes concepts like Zero Trust, better adapted to tackling modern cyber threats. While it’s a strict procedure, this minimizes many risks.
Easier compliance—organizations that are subject to government regulations are pressed to invest in client data protection tools. SASE can be invaluable here as it points in the right direction and can fully transform the network to comply with data protection laws.
FAQ
How do I choose a SASE vendor?
Your selection of SASE providers should directly correlate with your risk model. SASE implementation is a strategic decision that will affect all business areas. Therefore, a thorough risk assessment is necessary to evaluate the critical areas, especially for remote users. Once completed, the SASE vendor should be based on the identified weaknesses. The best choice for the SASE provider will be the one that solves your business’s particular problems.
Is SASE only for big enterprises?
SASE is a universal concept for IT management, so it’s not reserved only for big corporations. In addition, small businesses may convert to SASE more quickly as they usually have smaller, more flexible infrastructure.
What is not SASE?
If a provider doesn’t converge network connectivity and security features, their service isn’t SASE. For service to meet the SASE mark, there must be a degree of interconnectivity, which is the main benefit that this approach brings to the table.
How does SASE compare to SD-WAN?
SD-WAN optimizes network traffic for better performance. SASE combines that optimization with security features for safe and efficient data flow. In short, while SD-WAN makes data move fast, SASE makes sure it moves fast and safely.