Through Zero Trust, you can hide the applications on your network from onlookers, with access restricted to only trusted users and via specific gateways (only with pre-assigned permissions). The broker then verifies the user's identity and access rank before allowing them inside the perimeter — minimizing lateral movement to other areas of the enterprise network.
Let's quickly remind ourselves of what a Zero Trust architecture is. Global research and advisory firm, Gartner, defines Zero Trust as a series of linked products and services that form an identity-based protective perimeter encompassing both specific users and applications within the network.
Modern solutions such as NordLayer are built with the Zero Trust principle in mind — 'deny all, permit some.' In other words, no user should be trusted until their identity is verified. Zero Trust, also referred to as Zero Trust Network Access effectively removes the implicit trust given to those entities outside of a given network.
While organizations have acknowledged Zero Trust as an effective method to combat cyberattacks, outdated legacy security infrastructure and the harsh nature of denying access to most users has left companies fearful of a problematic transition towards adopting the model. The truth is, it's far easier and far more crucial for businesses to implement these days than most would think.
Key takeaways
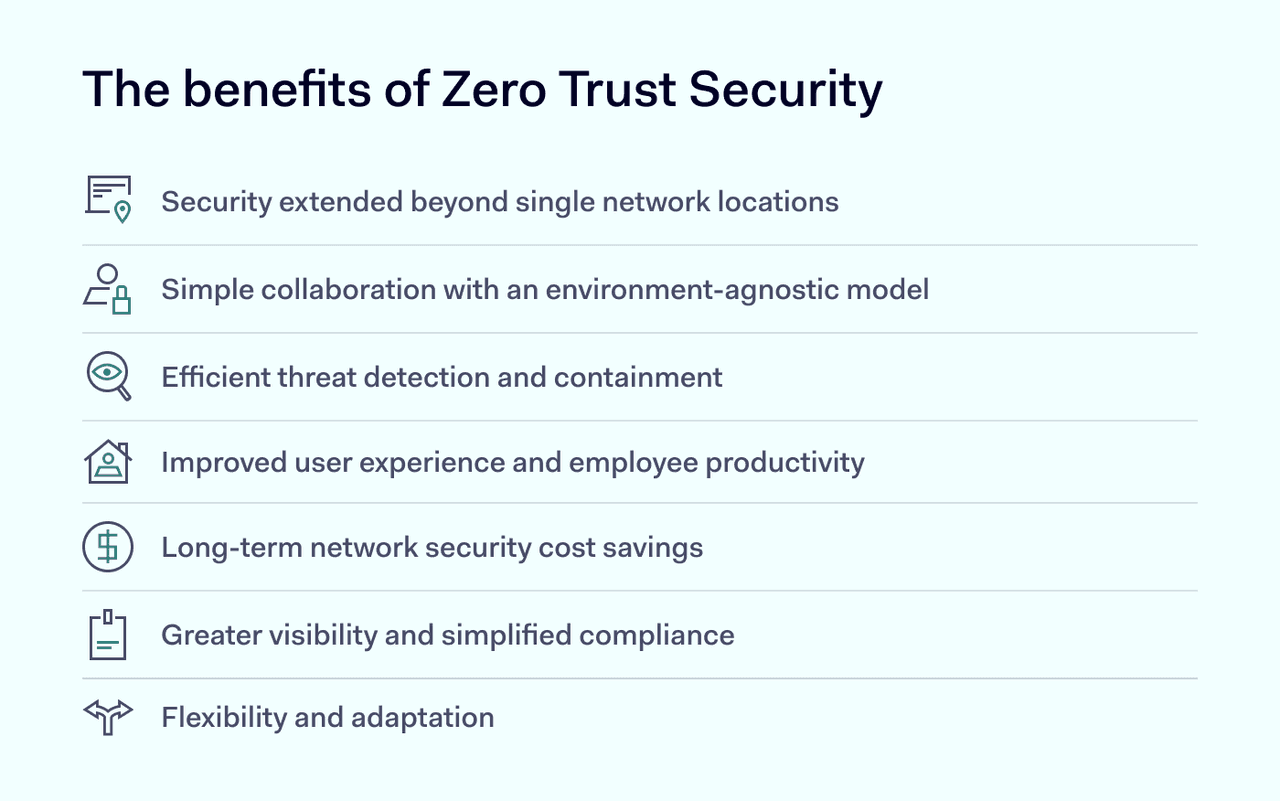
- Zero Trust hides network applications from outsiders, granting access only to trusted users via specific gateways after verifying their identity.
- The rise of remote work and external collaborations has expanded the traditional network perimeter, necessitating the Zero Trust model for enhanced security.
- Implementation steps include validating user identities with multi-factor authentication, monitoring device health, understanding network interactions, and continuously updating access controls.
- Challenges during implementation can include consistent monitoring, gradual introduction of new security practices, and potential disruptions due to added user identification steps.
- Zero Trust ensures that only trusted entities access critical data and resources, and generally is industry's best practice.
Why Zero Trust is important for business
As a result, surface areas for external cyberattacks and potentially harmful internal data breaches have grown exponentially, resulting in the traditional security setup becoming unfit for purpose in its existing form.
Despite the name, Zero Trust operates a 'trusted users only' policy. For business owners, this means you can segment certain areas of the network with access control. Admins can create teams and group user access permissions based upon which resources they need to fulfill their duties — keeping the enterprise network more secure.
A Zero Trust network that is invisible or inaccessible to outside entities offers businesses greater control over who is seeing and able to gain access to what. As a result, it takes less time to detect the source of breaches, and you have a holistic overview of the activity across your company network.
The complexities of implementing Zero Trust security
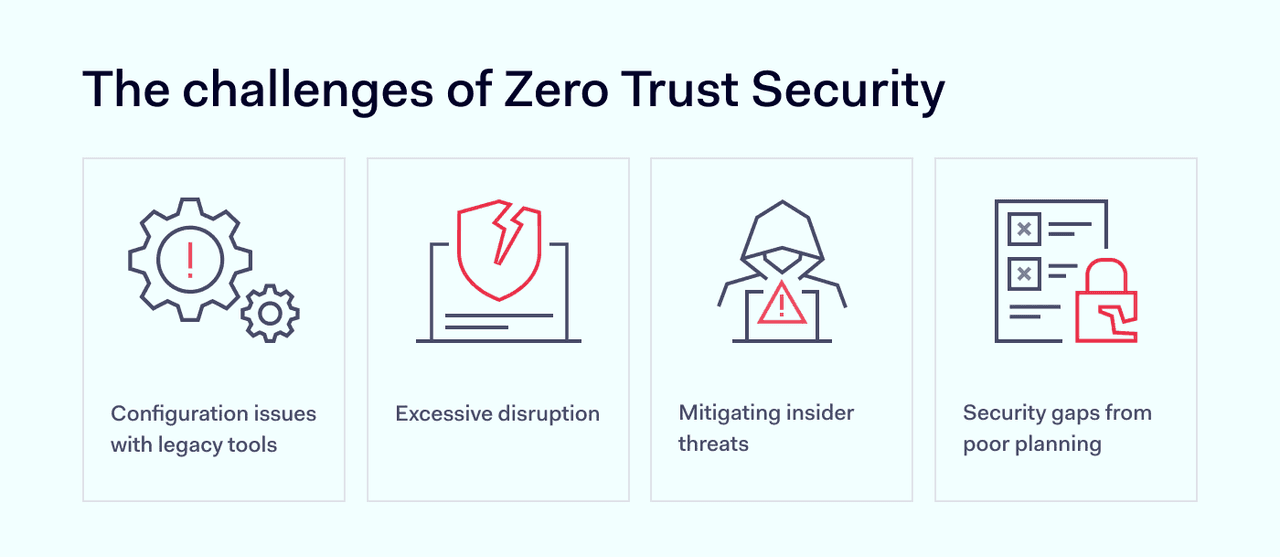
Excessive disruption
One of the core components of Zero Trust is granting access based on a "least privilege" principle. Implementing this requires an organization to have a deep understanding of their data, the associated workflows, and users' roles. This means segmenting the network, classifying data, and defining access rights at a granular level – a complex endeavor in large or rapidly evolving organizations.
Identity and authentication planning
For Zero Trust to be effective, organizations need robust identity and access management (IAM) solutions. This includes multi-factor authentication, continuous authentication, and dynamic risk assessments. While these tools enhance security, they can also add friction for users and complexity for IT departments and leave gaps that render Zero Trust ineffective.
Legacy systems and integrations
Many organizations operate with a mix of modern and legacy systems. Ensuring that legacy systems are compliant with Zero Trust principles can be technically challenging and costly. Moreover, integrating various systems, applications, and platforms while adhering to Zero Trust can add layers of complexity.
Mitigating insider threats
While Zero Trust excels at limiting lateral movement and segmenting access, its emphasis on strict verification can sometimes overlook the human element. Insiders, by virtue of their position, often have legitimate access to sensitive data and systems, making their malicious or inadvertent actions harder to detect. Their familiarity with the organization's processes and systems may also enable them to exploit vulnerabilities or bypass security controls.
Zero Trust implementation steps
Getting started with a Zero Trust security model doesn't have to be super challenging – as long as you follow the correct steps to prevent any sensitive data leaks.
1. Understand the areas you are protecting
Company networks aren't static entities but continually expand, making them difficult to holistically define, control, or protect. Instead, your admins should determine what and where your most protected Data, Applications, Assets, and Services - DAAS - are, rather than mapping out the entire network. Outlining this 'Protect Surface', is the first step towards Zero Trust.
2. Understand how applications interact on your network
Observe and record how specific applications interact with one another. Even without every piece of information available to you, your admins will gain a real insight into where controls are needed. Understanding how your systems are working will tell you where you need to create access controls. In other words, know what it is you're protecting before building the protection around it.
3. Outline your Zero Trust architecture
Remember, networks are not universal, so as you map the Protect Surface of your network, you'll be able to outline the architecture of your Zero Trust framework. The next step is to add security measures to limit the ability to gain access to your critical network areas.
4. Create your Zero Trust policy
The 'Who? What? When? Where? Why? How?' system, also known as the Kipling Method, is an effective way of determining whether a user or entity fulfills the correct criteria for gaining access to your protected areas. Essentially, there should be no communication between user and application that is unknown to your admins. Therefore, for all to be deemed trustworthy, strict criteria should be set (and met).
5. Maintain your network permissions
Documenting as much activity circulating your environment as you can, is at the forefront of what makes Zero Trust effective. Knowledge is power, so your admins can use this data to enhance your Zero Trust network security by implementing additional access permissions over time.
Zero Trust Network Access is a model you can introduce into your existing architecture relatively easily, meaning your admins can bypass carrying out a complete technology overhaul. When implementing Zero Trust, some of the challenges companies face are more teething problems while getting to the point where their security setup can defend against all manner of attacks.
Zero Trust is there to ensure that your most critical data and resources are only accessible to those who are trusted and nobody else.
What should I keep in mind when implementing Zero Trust?
We've developed a checklist for businesses looking to implement their own Zero Trust model to follow, based on recommended best practices:
- Validate the identities of all users through multi - factor authentication
- Keep all devices updated and in good health
- Conduct thorough observation and monitoring to obtain the most valuable data to inform access control implementation
- Limit access controls to specific applications, resources, data, and assets, rather than the broader network
What should I look out for when implementing Zero Trust?
Some of the most common challenges when implementing a Zero Trust framework include:
- Consistent monitoring to maintain Zero Trust effectiveness
- Needing a gradual and comprehensive introduction of new security practices (not being a one-size-fits-all solution)
- Potential disruption to work productivity through extra stages of user identification
While the challenges of implementing Zero Trust can seem daunting at first to businesses looking to make the transition, the positives greatly outweigh the negatives. Zero Trust sets company networks up to be able to tackle cyber threats both known and unknown.
Zero Trust industry best practices
Best practices can be quite misleading, in general, as usually, they boil down to opinions. Since Zero Trust has no real perfectly-defined meaning, best practices usually depend on the speaker.
With that said, generally following these will steer you right:
Identities protected by multifactor authentication (MFA)
The first step in your Zero Trust journey has to be MFA. Regardless of what solution you decide to realize, adding a second identity check into the process makes it far more difficult for outsiders to use a jeopardized identity over just passwords alone.
Healthy devices
Keeping devices healthy is a very important step, too. Running the latest software and security updates must be enforced to ensure no cracks or loopholes are found.
Telemetry
There is no use setting things up and leaving them to it. Proper monitoring and administration are required to ensure operations and compliance are tight and correct.
FAQ's
How do I choose a Zero Trust provider?
The ideal Zero Trust provider will be flexible, adaptive to your needs, and, most importantly, easy to use and manage. NordLayer is an adaptive network access solution built on the Zero Trust principle of 'deny all, permit some'.
Is Zero Trust replacing VPN?
No. Zero Trust is an identity-based access control model that fits in and around your existing security setup. Encompassing all devices and users, a VPN is a current security measure that can form part of that Zero Trust model.
How to deal with Zero Trust for guest access scenarios?
Just as businesses handle access permissions for freelancers and contractors, with an adaptive Zero Trust solution like NordLayer, your admins have the power to grant permissions to trusted guest users — only to the resources and data they need to fulfill their duties.
How long does it take to implement a Zero Trust system?
The time needed depends entirely on the specific solution that you'll be implementing and the overall complexity of your network. The bigger it is, the longer it will take to document everything and deciding which devices and accounts will be assigned to what segments.