As modern workplaces evolve, with more employees working remotely or in hybrid environments, IT teams face increased challenges in safely enabling access to corporate systems and data. Traditional remote access methods like virtual private networks (VPNs) often expose too much of internal networks, requiring a move toward a Zero Trust model.
This article explores how Zero Trust Network Access (ZTNA) strengthens security for the remote workforce by restricting access based on user and device validation. Learn how a “never trust, always verify” principle can help your organization safely enable remote productivity while preserving network security.
ZTNA definition
ZTNA is a security concept that requires all users, even those inside the organization's corporate network, to be authenticated, authorized, and continuously validated. Before being granted or kept access to applications and data, their security configuration and posture need to be checked. This approach assumes that no user or system should be trusted by default, whether inside or outside the organization's perimeter.
Key takeaways
- ZTNA is a security concept that assumes no user or system should be trusted by default, requiring constant validation and authorization.
- It offers increased visibility, better data protection, and efficient automation, which suits modern business environments.
- ZTNA ensures that remote employees connecting from unsupervised networks are continually verified and authenticated, reducing the risk to the enterprise.
- It's particularly beneficial for businesses that have transitioned to multi-cloud environments.
- ZTNA is part of Secure Access Service Edge (SASE), a unified framework that includes various cloud-native cybersecurity solutions.
How does ZTNA work?
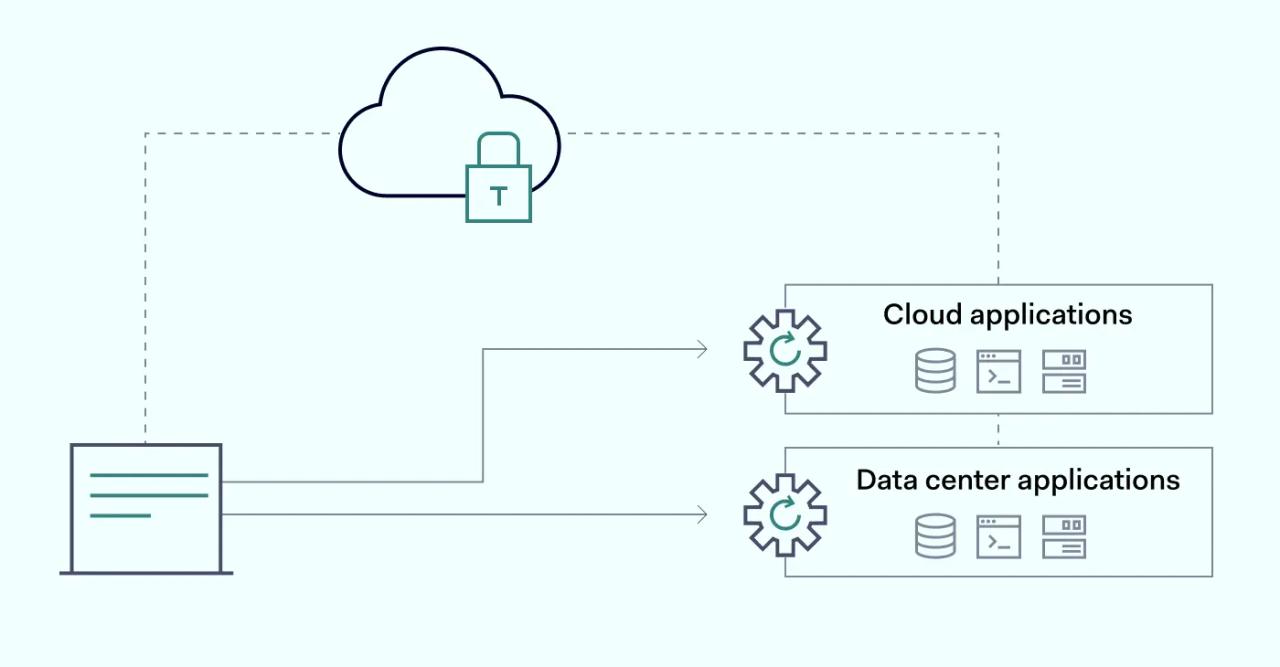
Zero Trust Network Access uses a Zero Trust security model to implement secure remote access to a company's resources. With a built-in cohesion to the Zero Trust security model, it aims to keep secure access to the corporate network from internal and external threats. It's done by enforcing strict verification procedures before each access session.
ZTNA has an edge in terms of security compared to other remote access solutions like VPNs—virtual private networks. VPN implementation usually entails full user access to a specific network, while ZTNA restricts it to a limited range of applications or services. This approach is less risk-prone and is more suited for modern business environments.
At its core, Zero Trust Network Access combines user validation with network invisibility. With ZTNA, connected devices aren’t aware of what other network resources are connected, nor do they have any means of accessing them. The second part of the formula ensures that users are validated and authenticated before access is granted. Here’s how this framework could be broken down:
1. Separation between network access and application access
While VPN has no distinction between the two, ZTNA separates the network from application access. This introduces additional obstacles for bad actors infiltrating the network, reducing overall risks.
2. Outbound-only connections
ZTNA allows only outbound connections, making application infrastructure and network invisible to unauthorized users—they’re locked out. In turn, IP addresses aren’t exposed to the public internet, making user location on the network impossible to pinpoint.
3. Limited application access
ZTNA uses native app segmentation to ensure users only access specific applications rather than the whole network. This mitigates the risks that could arise from overly permissive network user access.
4. User-to-application approach
Instead of focusing on network security, this approach focuses more on application security. End-to-end network components that directly participate in application access are in focus. This also means discarding highly secure MPLS lines in favor of encrypted tunnels.
ZTNA is both more secure and better adapted to today’s cybersecurity challenges. With users working from anywhere, Zero Trust helps businesses manage the online risks they’re facing. It’s a cloud-based approach accepting secure connections from managed and unmanaged devices, with much greater flexibility than traditional network setups.
Benefits of ZTNA
ZTNA allows network expansion while keeping the potential risks in check. It’s also especially appealing to businesses that have transitioned to multi-cloud environments. As resources are scattered across multiple locations, Zero Trust gives much better access to them. In comparison, perimeter-based solutions like VPNs are slowly phased out.
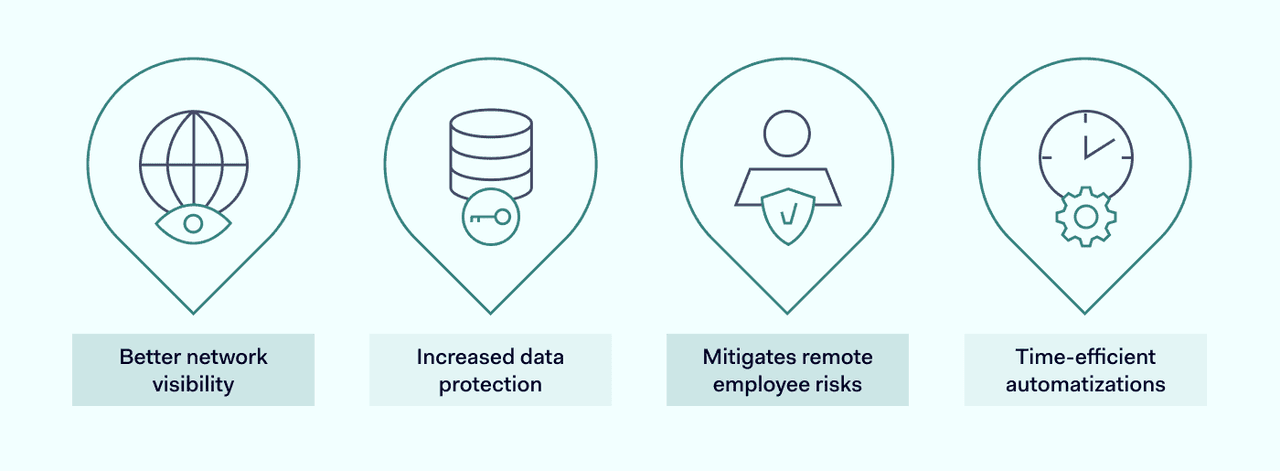
1. Better network visibility
As the allowed connections are severely reduced in number, this also cleans up the network overview. The only allowed connection has to pass through a strict set of parameters, so there are more parameters to use for tracking. These aspects can improve network visibility, including timestamps, application log-ins, access requests, and user actions. It also means abnormal behavior flagging for real-time analysis and investigation is much easier.
2. Increased data protection
Isolated access to an organization’s network also means less leeway to threaten it. Even when some weak link is exploited, ZTNA puts strict restraints on what can be done with them. Privilege escalation is hampered due to authentication requirements, while the rest of the network is inaccessible. These built-in constraints make damage mitigation much easier.
This helps to achieve not only the network’s security but also protects the most sensitive data of your organization. Zero Trust implementation can make a key difference between being breached and pulling through with the company’s reputation intact.
3. Mitigates remote employee risks
Remote employees are connecting from unsupervised networks with unmanaged devices, increasing the total attack surface. It’s one of the major challenges to an enterprise’s IT staff, as most workplaces have adapted a hybrid work approach.
ZTNA largely solves this problem by enforcing a requirement to verify and authenticate at every access level. The user is allowed inside if the device meets security requirements and there are no other red flags.
4. Time-efficient automatizations
Continuous monitoring is at the foundation of ZTNA. It’s a highly autonomous approach to network security management, and after preconfiguring specific parameters, the system can be left on its own. Various automation takes decisions of access requests based on the set rules and analyzes each situation’s context.
The gathered data can also be reused for in-depth analysis. So, this serves as the additional team member, and its use extends to additional areas. IT teams implementing Zero Trust are freed to focus on different tasks, passing mundane administrative checks to the software.
Top ZTNA use cases
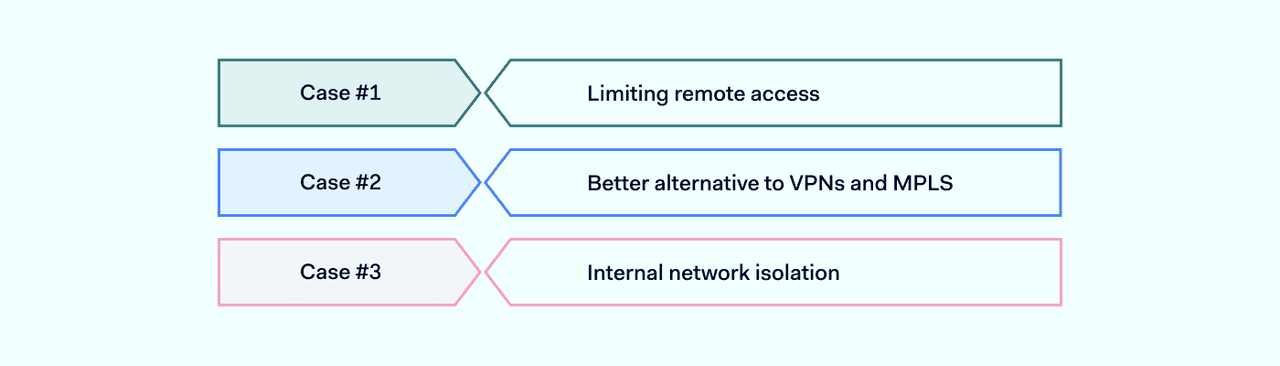
ZTNA can be a substantial help when it comes to stopping external threats and safeguarding internal assets. Here’s how ZTNA be used to benefit your organization:
Limiting remote access
If you’re looking into how to strike a balance between work-from-home and business network security, ZTNA might be a godsend. Zero Trust provides access to specific applications without giving too much freedom to roam the internal corporate network.
It’s a much more efficient solution that doesn’t clog up internal bandwidth. Users are connecting directly to where the resources are hosted, improving performance. Not to mention that application access is denied by default unless the authorized users have passed authentication.
2. Better alternative to VPNs and MPLS
There aren’t many technologies that allow closed-off networking that would be viable in a business setting. For instance, multiprotocol label switching (MPLS) requires additional hardware like routers and switches interconnected via leased lines or other links. One of the most expensive setups you could deploy is above the budget for many small to medium businesses.
VPNs are a much cheaper alternative using public internet and encrypted tunnels, but if your user base relies on cloud services, this isn’t a viable option either. ZTNA solves the drawbacks of both former connectivity technologies. It reduces network complexity and provides direct access to the cloud, improving connection performance.
3. Internal network isolation
Most remote work tools expose more enterprises’ internal resources than the employees would need for their job functions. Usually, this is due to the limited network segmentation options available. This severely contributes to the number of risks an enterprise is facing, including from compromised devices.
ZTNA implements the least privileged access framework to prevent damage from potential data breaches. Users are granted only the minimal rights to perform in their job role. A data breach would limit the data that malicious actors could expose.
Types of ZTNA
Zero Trust Network Access solutions are flexible enough to strengthen security across an organization's most important digital assets. There are three main types of ZTNA models based on the facets they aim to protect:
1. ZTNA for access management
This model ensures authorized users can securely access only the applications they are authorized for via a direct connection path. When a user tries to log in, their identity, device, and location are verified before allowing access. This prevents exposure to online threats throughout the access process.
2. ZTNA for resource protection
Workload ZTNA safeguards applications and internal communications frameworks from build through runtime. Strict policies are enforced to deny lateral threat movement between workloads and prevent data loss. This protects apps and services from compromise.
3. ZTNA for endpoint security
As more employees use personal devices, strong protections are needed for data transmitted to and from any endpoint. ZTNA leverages encryption, authentication, and device validation to shield information as it travels to managed or BYOD devices. This addresses growing security risks from unsupervised networks.
ZTNA 2.0
ZTNA 2.0 is the latest evolution of Zero Trust network access solutions. It builds upon the original ZTNA model to provide even stronger security as more people work from different places. Zero Trust Network Access 2.0 goes beyond just checking users and devices when they log in. It authenticates all types of digital things like applications, servers, and software tools. It also verifies if they can still be trusted more thoroughly at the individual app level.
Special monitoring keeps checking if devices, users and apps are still behaving safely after access is given. Any suspicious changes could cause access to be taken away right away. Deep scans of all traffic also help stop unknown tricks of malicious actors.
A unified system lets Zero Trust be easily applied across any computer setup, from cloud services to private networks and servers. Special analytics give great visibility into how apps and programs connect and usually operate.
ZTNA 1.0 vs 2.0
ZTNA has come a long way from its original 1.0 version. While ZTNA 1.0 helped set up basic network access controls, it focused only on user and device authentication. Zero Trust Network Access 2.0 builds upon the earlier foundation with many improvements to address today's complex hybrid work environments.
ZTNA 0.1 | ZTNA 2.0 |
|---|---|
Single initial authentication | Continuous trust verification |
No continuous inspection | Continuous security inspection of all traffic |
Not all data protected | Protects all data across applications |
Only some apps secured | Secures all traditional and cloud apps |
No ongoing monitoring | Continuously monitors devices, users, apps |
Potential security gaps existed | Addresses gaps of the previous version |
ZTNA 2.0 strengthens security with its enhanced capabilities like continuous authentication, analytics insights, and centralized policies. This evolution helps businesses finally attain resilient Zero Trust as their operations expand in hybrid, cloud-based landscapes.
How to implement ZTNA?
ZTNA can be implemented in these ways: using special software on each client device or a ZTNA service. Depending on the connection method and the location of the ‘agent’ (special software application), ZTNA setups come in two types:
Agent-based (or endpoint-initiated)—requires installing special software on the device which will be used to connect to specific applications.
Service-based (or service-initiated)—is added directly to the network between the user’s device and the accessed application. The special connector often comes with a Zero Trust cloud service but can also be deployed on-premises.
This brings us to the two delivery modes in which ZTNA could be deployed:
Standalone—all ZTNA elements in their entirety are deployed and managed by the organization that is using the service. This gives a much broader control over the ZTNA network and makes an organization responsible for cloud maintenance.
As-a-service—an organization brings access from ZTNA vendors. The service maintenance falls on the provider’s shoulders, while the enterprise can use the already established infrastructure. This simplified approach is optimal for most organizations that don’t want to create everything from scratch.
ZTNA user flow
While the user’s flow can vary depending on the setup model, here’s an approximate ZTNA process chain:
- The user initiates an application access request using an established secure channel.
- The Zero Trust controller processes the request from the used user’s endpoint (in an endpoint-initiated setup) or by the network connector (in a service-initiated model), authenticating
- If the authentication is passed, the user is let through. Otherwise, the access is denied
- At this stage, the Zero Trust controller may implement additional authentication steps like MFA, checking device attributes, and other data
- If no defense mechanism is triggered, the user is granted to use a specific application
The process could be repeated for each application or customized in other ways.
ZTNA and VPN
Both ZTNA and VPN are technologies that are used to provide remote access to private networks. The difference is how they operate, and they're also suited to different scenarios.
Zero Trust Network Access requires both the user and the device to be authenticated. Only then does it grant access based on specific policies like the user device's role, security state, location, and other context-aware factors.
It also creates an individual encrypted tunnel restricted to specific applications, such as private apps or third-party access to internal systems, to isolate traffic and prevent lateral movement in case the own device becomes compromised.
All in all, companies searching for modern and robust security services should turn to ZTNA solutions. On the other hand, smaller organizations with less complexity and traditional on-premises environments should turn to VPNs.
ZTNA and SASE
Secure Access Service Edge is a collection of frameworks unifying many cloud-native cybersecurity solutions into a single concept: security service edge. ZTNA is one-fifth of SASE, while the other four components focus on different areas.
In SASE setups, the ZTNA controller’s function is passed on to points of presence (PoPs) located as close to the dispersed user base. Devices connect to PoPs directly and, after being validated, are allowed to request application access. ZTNA controller’s function is passed to SASE PoPs, so a separate connector agent isn’t needed.
SASE attempts to create a holistic cybersecurity framework that would address a much broader scope of online threats. It still needs the deployment and a plan for how it could be introduced into the existing network, considering used hardware and legacy device support.
Using SASE solution de facto means using ZTNA with additional parts that SASE entails, like SD-WAN, SWG, CASB, ZTNA, and FWaaS.
ZTNA and firewall
While both ZTNA solutions and firewalls can secure network access and protect resources, there are key differences in their approaches and capabilities that should be understood when evaluating Zero Trust solutions.
Traditional firewall-based network access has some limitations that Zero Trust Network Access improves upon:
- Management: Firewalls require manual installation and configuration, while ZTNA offers centralized policy management via the cloud
- Performance: Connecting remote workers through a firewall can impact performance, whereas ZTNA directly connects users to application hosts
- Security: Firewalls don't continuously evaluate device security posture like ZTNA does with checks, multi-factor authentication, and identity integrations
- Scalability: It's more complex to add networks and users when using a firewall-based approach, whereas ZTNA easily scales through a unified cloud console
- Segmentation: Firewalls have limited ability to granularly segment access compared to how ZTNA can restrict access to specific apps for third parties
Therefore, ZTNA addresses key challenges around management overhead, network performance, advanced security, scalability, and granular access that traditional firewall-based network access faces limitations with.
ZTNA and CASB
While ZTNA and CASB (Cloud Access Security Broker) both aim to strengthen security, they approach it in different ways, each tailored to its specific purposes.
ZTNA acts like a protective gatekeeper. Its goal is to carefully verify anyone requesting access to protected network resources before granting approval. Through multi-factor authentication and continuous authentication checks, ZTNA confirms someone is who they say they are. This zero-trust approach helps ensure that only authorized access occurs regardless of location.
CASB watches over cloud application use like a guardian. It monitors activity in cloud applications and services like file sharing and collaboration tools to make sure data and usage comply with company policies. CASB aims to guide the secure use of cloud apps while still allowing flexibility and productivity. Its role is to help people leverage cloud tools safely according to security guidelines.
In essence, ZTNA focuses on enabling secure, verified access to internal networks from any device or place. CASB centers on governance and protection for cloud application usage in approved workflows. Both play critical parts in an integrated security model by controlling access and promoting responsible cloud usage by authorized users, respectively. Their goals complement each other to secure digital environments.
Conclusion
Traditional remote access approaches often grant too much trust and exposure, leaving critical vulnerabilities. ZTNA addresses this through its Zero Trust foundations of “never trust, always verify.” By consistently authenticating users, devices, locations and application interactions, ZTNA strengthens control and visibility into network activity.
Continuous validation tied to granular access policies also helps reduce security risks from remote and mobile workforces. Whether employees connect internally or externally, ZTNA applies uniform protections to critical data regardless of location.
When leveraged as part of a unified Secure Access Service Edge framework alongside tools like CASB, SWG, and Firewall-as-a-Service, ZTNA completes the shift to zero-standing trust and software-driven security. It enables modern organizations to safely enable productivity from any device on any network while maintaining rigorous access governance.