Zero Trust Security is a set of network security principles based around the idea "never trust, always verify."
With Zero Trust every network user is verified and monitored constantly. No devices are authenticated without proper validation.
The main idea is that within a Zero Trust environment all traffic, devices, and users are hostile until proven otherwise. The aim is total protection against insider and external digital attacks.
This security concept emerged in response to innovations that have made network perimeters less relevant. Growing use of Cloud resources, web applications, Internet-of-things devices, and remote work have all outpaced traditional core and perimeter models. Security must now follow workloads across locations and through multiple Cloud resources.
Quick overview of pros and cons of Zero Trust Security
Here is a quick summary of the key benefits and challenges faced when switching to Zero Trust Security architecture:
Benefits of Zero Trust
- Zero Trust architecture offers a flexible solution for Cloud-based networking.
- Zero Trust is ideally suited to organizations reliant on remote work.
- SSO makes life easier for employees by bringing all relevant assets under one sign-on procedure
- Centralized tools allow managers to monitor network traffic and user behavior effectively.
- Encryption, PAM, microsegmentation and real-time continuous monitoring provide powerful ways to mitigate digital threats.
- Simplified audit trails and tightened data security assist with regulatory compliance
Zero Trust challenges
- The switch to Zero Trust architecture can be disruptive and lengthy
- Organizations need to take a careful approach to avoid leaving security gaps when implementing a Zero Trust security model.
- Some issues may occur with legacy applications, resulting in the need for costly updates
- Upfront costs can be high, but long-term security and efficiency benefits offset initial investments.
Core Zero Trust Security technologies
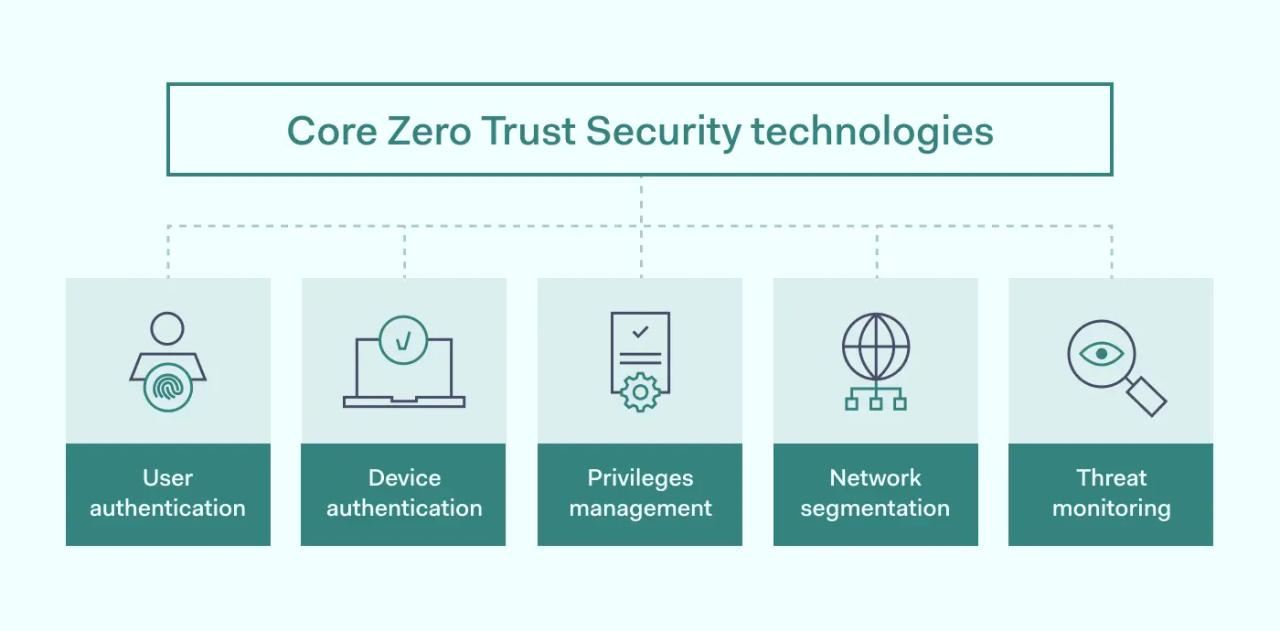
User authentication
ZTNA generally adopts Single Sign-On access control to enable simple authentication. SSO allows users to access resources quickly, while single or multi-factor authentication delivers a high degree of validation. Per session access is also preferred to maximize security.
Device authentication
User devices are scanned and can gain access to network resources only when they have been authenticated and received security approval.
Privileges management
Identity Access Management (IAM) systems set out the privileges of each user. Users are allowed to access the resources they need, and nothing more.
Network segmentation
Network architecture is divided into sections via Software Defined Perimeter (SDP) tools. SDP manage privileges and contains any threats if they emerge.
Threat monitoring
ZTNA employs continuous threat monitoring, providing real-time information to security teams about potential threats. User activity is logged and available for audit as required.
One way to view ZTNA implementations is via the triad comprising the policy engine, the policy enforcement point, and the policy administrator.
The policy engine is the software that provides privileged access to core resources. The enforcement point allows users to access those resources, while the administrator communicates between the two nodes.
Zero Trust Security differs from traditional moat and castle approaches relying on perimeter defenses such as firewalls and VPNs. Encryption may still be used on the network edge, but with ZTNA, SDP tools dynamically protect workloads as they pass through network resources. This approach is well-suited to remote working and Cloud-based organizations.
What are the main benefits of Zero Trust Security?
- Rely on remote work or hybrid remote and on-premises working.
- Regularly collaborate with external contractors and partners.
- Depend on Cloud resources and cannot rely on the performance of Cloud Security Providers (CSPs).
- Must guard sensitive data against data breaches and insider threats.
- Must meet high compliance requirements such as HIPAA or NIST standards.
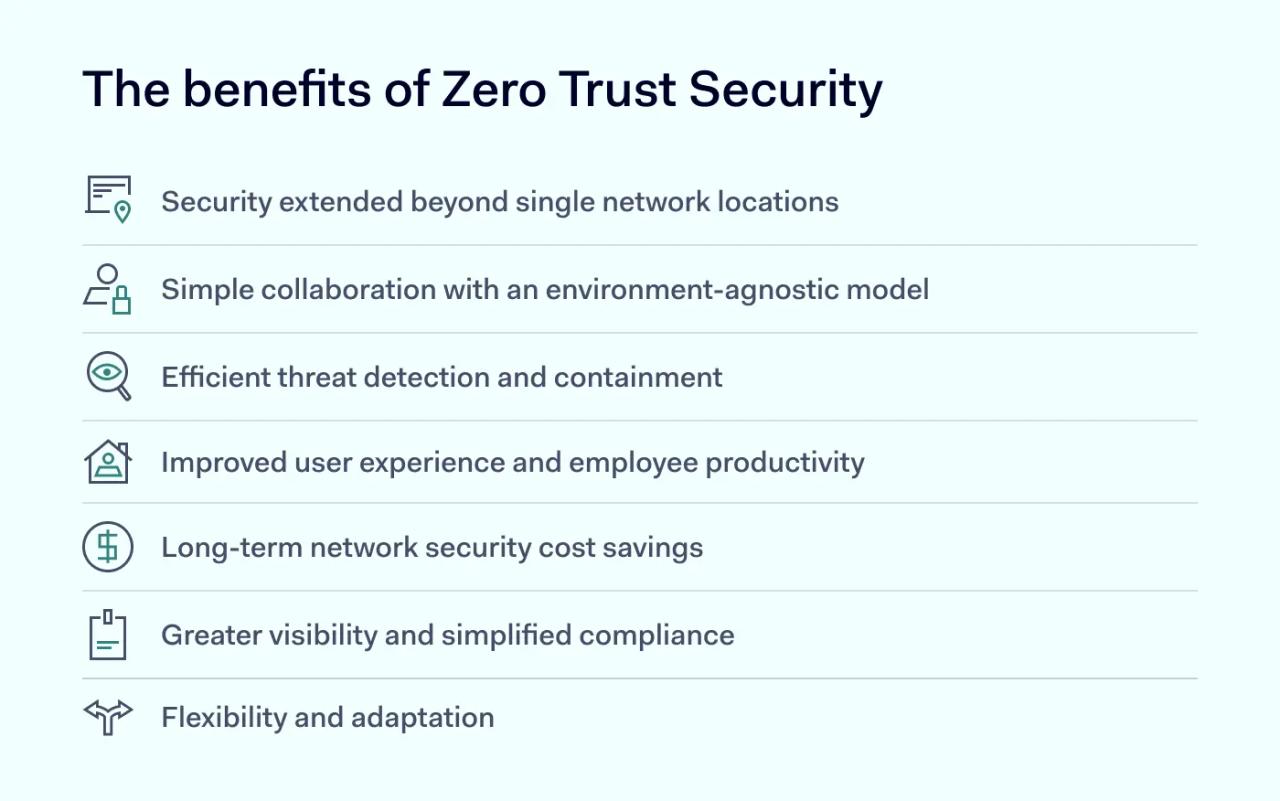
The benefits of adopting a Zero Trust Security strategy include:
1. Security extended beyond single network locations
Zero Trust approaches seek to secure modern networks that have grown beyond a single or multiple physical locations.
The traditional network perimeter no longer exists. Many companies rely on access to remote Cloud applications or data centers. They may also need to guarantee secure access for remote workers , or manage workloads on private and public cloud environments.
Zero Trust Security answers the security needs of those companies. Software Defined Perimeters and microsegmentation allow workloads to travel wherever they need to go within the entire network, while applying strict user access privileges.
Security is based on user authentication and privileges which follow the user across multiple locations. There is no need to supply credentials to access specific applications or services.
2. Simple collaboration with an environment-agnostic model
With ZTNA, different network architectures can also communicate securely without major structural updates or policy changes. Users simply require the correct privileges to access resources of any kind.
The fine-grained ZTNA model enhances cross-organizational collaboration. Companies can precisely determine who can access apps and resources such as documents and work files. Granular control makes collaboration smoother and safer, strengthening Intellectual Property (IP) protection and reducing the need for time-consuming security processes.
3. Efficient threat detection and containment
Zero Trust architecture makes it easier to contain data breaches or malware infections, allowing companies to adopt a dynamic security posture that's prepared for sudden alerts.
Individual users exhibiting suspicious behavior such as unexpected access requests can be confined via network segmentation, while direct user-to-app connections limit lateral movement within the network. Cyber-attackers can be contained rapidly and tightly, giving them minimal opportunity to access sensitive data or compromise core assets.
All users are monitored in real-time, delivering instant insights to managers. Monitoring tools also generate a legible audit trail that feeds into security responses, compliance and risk mitigation strategies.
Moreover, traffic on Zero Trust networks is rendered invisible to the external internet via high-grade encryption. This invisibility further reduces the threat surface and makes a damaging security breach less likely.
4. Improved user experience and employee productivity
Implementing Zero Trust improves interaction with core resources by employees and partners. SSO gateways remove the need to use separate passwords for multiple applications, and the implementation of simple MFA is faster and more secure.
Surveys of companies moving to Zero Trust architecture have also found benefits for remote workers. Simplifying access makes it easier to manage complex hybrid settings where a remote workforce needs round-the-clock global access to Cloud and on-premises assets.
5. Long-term network security cost savings
While transitioning to Zero Trust requires up-front investments in time and money, the process will have long-term cost benefits for almost any organization.
More effective threat neutralization systems result in lower mitigation costs when data breaches occur. IBM have calculated that companies implementing Zero Trust save $1.76 million per data breach – so the savings can be substantial.
Other studies suggest that long term security costs fall by 31 percent with an effective Zero Trust solution. This fall is probably due to lower licensing costs and savings from more efficient hosting setups.
6. Greater visibility and simplified compliance
Zero Trust systems provide complete visibility of corporate network traffic and user behavior. Heightened visibility assists security teams when analyzing internal performance, adjusting network architecture, and providing feedback to corporate managers.
Visibility is also a crucial part of network security compliance initiatives. ZTNA helps to reduce compliance risks posed by overprovisioned software and uncontrolled user privileges. Continuous compliance can be achieved with real time threat monitoring, while seamless audit trails provide valuable information to meet industry regulations such as NIST 800-207.
Specific data assets can also be segmented and locked down to meet regulatory data protection requirements. This focused segmentation can be particularly beneficial in sectors like healthcare, where the Health Insurance Portability and Accountability Act (HIPAA) makes rigorous demands on data security.
7. Flexibility and adaptation
One of the problems with traditional network architecture has been the secure addition of new devices and resources. With ZTNA, IT teams have greater flexibility to reshape which devices, resources, apps, and services connect to their networks.
Resources can be moved rapidly from a private data center to any Cloud environment without the need to create new security policies. A single security policy applies across all resources.
IT teams can revise security policies via centralized tools before migrating them as needed, and low level policy changes can be automated to save time. Centralized security policy management also means that companies can usually add Zero Trust architecture above existing assets with few fundamental changes.
All of this means that organizations can efficiently scale up network operations, switch between Cloud providers, shift to a different mix of central or remote work, and tackle many other aspects of digital transformations.
Common challenges encountered when adopting Zero Trust Security
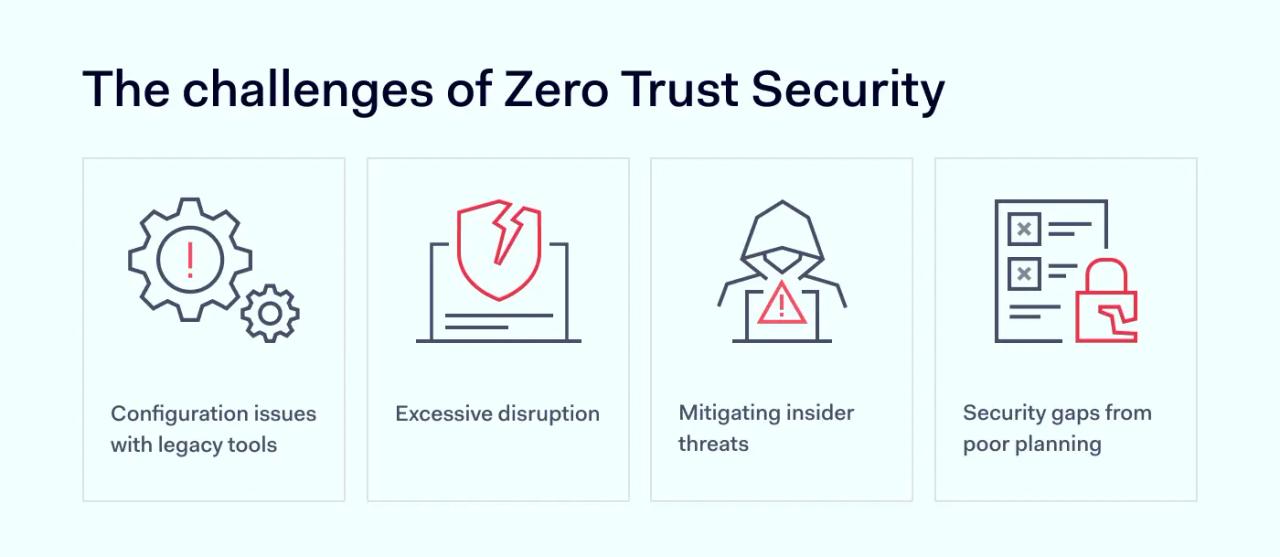
1. Configuration issues with legacy tools
Not all existing assets are set up to operate with Zero Trust systems. For instance, developers did not design many legacy payroll software tools to work with the principle of least privilege and microsegmentation.
Surveys have found many companies claim to implement Zero Trust principles, while struggling to authenticate and monitor users in the real world. It is essential to assess legacy applications and platforms, and ensure that existing assets can operate with SSO, IAM, and other ZTNA tools.
2. Mitigating insider threats
ZTNA systems minimize potential risks while ensuring seamless user experiences. However, they remain vulnerable to threats involving employees or partners with valid login credentials.
PAM systems like biometric MFA can help to keep these risks to a minimum. MFA makes it much harder for insiders to pass credentials to outsiders for malicious use. The architecture of well-configured Zero Trust networks also makes lateral movement harder, limiting the freedom of intruders.
However, the threat remains, and it is vital to consider insider threats when formulating security policies.
3. Security gaps from poor planning
There is always the risk of leaving security gaps while constructing Zero Trust architecture. Most companies choose a phased digital transformation to fill these gaps, including extensive testing and vendor trials.
Adopting Zero Trust can therefore be a labor intensive process. IT teams need to assess every device and application. Teams must create profiles for every user, with no exceptions.
Meticulous planning can also lead to a secondary risk of moving too slowly. If companies are excessively cautious, the process can become costly, while commissioned solutions could also become outdated when the process is complete.
4. Excessive disruption
Adopting the Zero Trust model can also be highly disruptive, causing problems for workforces and managers. Workers may encounter difficulties accessing core resources or logging into accounts remotely. Privileges can be improperly assigned, while conflicts with legacy software can lead to delays.
These potential problems make it essential to plan project milestones and inform staff at every stage of the Zero Trust rollout.
Conclusion
Modern businesses deal with diverse and dispersed ecosystem that traditional security models are incapable of protecting. Zero Trust Security offers a logical solution to a practical problem, but it comes with its own obstacles.
This method offers benefits such as better cloud networking, remote work management, single sign-on, and enhanced monitoring. However, it can be costly to start, disrupt current workflows, and may have compatibility issues with old applications. While different from old security measures, the Zero Trust approach is capable of providing a holistic, dynamic security model that can adapt to modern digital environments.