Access control definition
Access control is a process that allows companies to determine who has access to sensitive applications and data. Whether you are protecting a cardholder data environment or guarding health records, restricting access to network resources is critical.
Access control systems check the identity of users and assign access rights according to user roles. They exclude illegitimate users, reducing the risk of data breaches and other cyber-attacks.
This blog will look at access management basics. We will explore critical issues like:
- Why access control policies matter
- Critical components of access control solutions
- Different types of access control systems
- Important access control challenges
Why is access control important?
Effective network access control helps companies to serve customers, satisfy regulators, and maintain critical systems. In an age of massive data breaches and reputational risk, it is not an optional extra. Most importantly, access control prevents data breaches and excludes malicious attackers.
Without robust authentication, attackers can easily breach network defenses. Without properly configured authorization settings, attackers can move freely within the network. This puts confidential data at risk and limits companies' ability to detect and mitigate attacks.
Access control is also a major compliance issue across all business sectors. HIPAA, GDPR, and PCI-DSS mandate robust access control policies to protect customer data. The same applies to commonly used information security standards like ISO 27001.
Access control components
The access control process has five main components. Each component plays a critical role in controlling access and protecting network resources.
- Authentication – This establishes the user's identity. Every user connecting to the network must prove they are who they claim to be. This could include simple user ID and password filters. Extra authentication systems like multi-factor authentication provide more robust security.
- Authorization – This provides access rights to network resources. Privileges establish which resources a user can access, and the powers they have when using those resources. For example, they may be authorized to create but not transfer customer records. Users may also have restricted access to specific apps for security reasons.
- Access – The access control solution permits access to network resources. Users can carry out their duties according to security policies.
- Management – Network administrators must manage user profiles and change access policies as needed. Access control solutions allow admins to create and remove users. Access systems should combine easily with identity directories for both cloud and on-premises assets.
- Auditing – This monitors security levels and remedies weaknesses, such as users receiving more access than required, which could create data breach risks.
Access control is a process, not a fixed set of technologies. Managing access is not a "set it and forget it" challenge. An effective access control model must be dynamic and flexible.
How does access control work?
The two core types of access control are physical and logical. Both are important, but they play very different roles in security systems.
Physical access control
Physical access controls manage access to workplaces and data centers. Controls in this category include:
- Security cards
- Locks
- Biometric scanners
- Cameras to verify individuals.
Logical access control
Logical access control manages access rights to digital infrastructure and confidential data. LAC tends to involve electronic access control methods. This could include passwords and user IDs, as well as MFA.
In practice, organizations usually use both types of access control in their security systems. But in terms of cybersecurity, the critical question is what types of logical controls to put in place.
Some features are common to all access control solutions.
- Access controls use authentication factors to assess user identities. This could involve information the user knows (such as a password). It could be something they are (such as a biometric scan). Or the factor could be something the user possesses (such as security tokens or one-time codes).
- Access controls locate the user on the authorization database and assign privileges that fit their identity or role.
- The access system logs information about the user session. This is used to detect anomalies and feeds into regular security audits.
Access systems vary beyond those core features. It's important to know the main types when putting in place solid access controls.
Main access control types
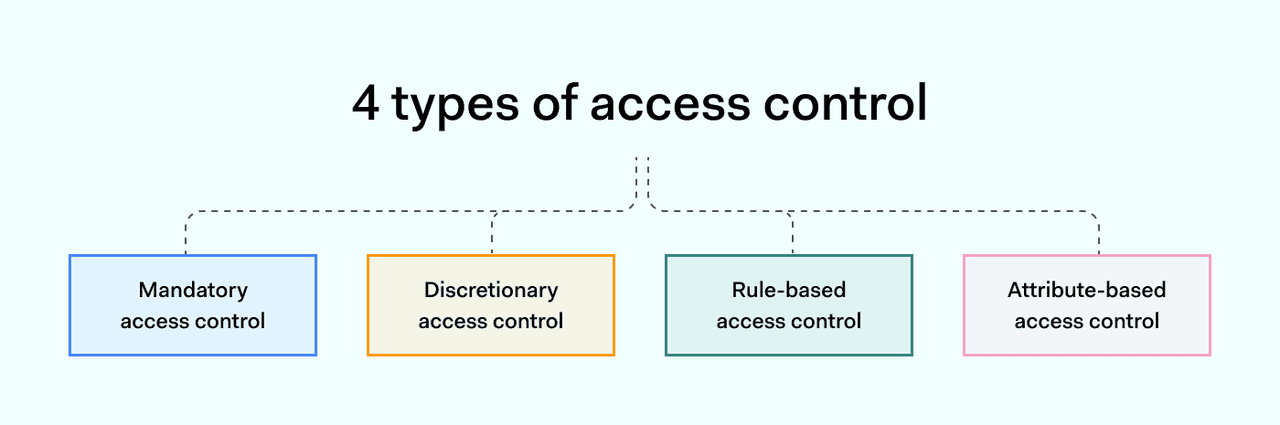
Access controls come in various forms, with different functions and use cases. Common variations include:
Discretionary access control
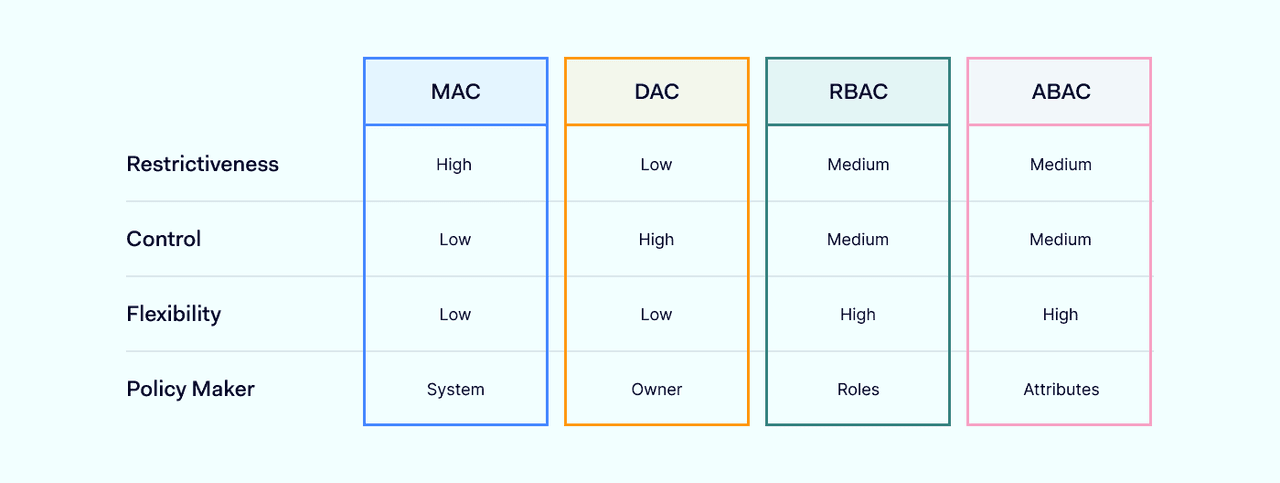
Administrators set access control policies for each resource. Resource owners have the flexibility to change user privileges and create role-based groups.
This works well in rapidly-changing environments with short-term project timescales. However, discretionary control systems tend to lack centralized oversight. Security teams may struggle to enforce policies consistently.
Mandatory access control
In these systems, access management is centrally controlled. A single authority governs authentication and authorization policies for all computer systems.
Mandatory access management can be inflexible. However, organizations can lock down access to critical resources and only permit access to approved devices or users.
Mandatory systems tend to focus on clearance levels. They typically grant wide authorizations to users with different clearance classifications. This makes them a common access solution for military environments.
Role-based access control
RBAC assigns privileges to roles within the organization. Roles authorize the user to access resources required during their professional tasks. RBAC can last throughout a user's term of employment, but can also be time limited. For example, employees may need elevated privileges during a specific project.
Like mandatory access control, RBAC is centrally administered. However, RBAC focuses on authorizing ways to use network resources. For instance, roles may have read but not write privileges.
Attribute-based access control
Attribute-based access control uses attributes as the basis for authentication. Examples could include the user's location or age. Users do not necessarily need to supply complete proof of their identity. Instead, the system grants access if the user has the required attributes.
Attribute-based controls are an efficient way to manage access to less sensitive resources. And they also provide granular control over how resources are used.
Rule-based access control
Rule-based controls use sets of rules to determine user access. For example, rules may allow access to applications at specific times of the day. Rule-based access control works alongside MFA and privileges management. It provides administrators with granular controls to govern network access.
Benefits of access control
Access controls are an essential cybersecurity tool for several reasons:
Reduced risk of data breaches
Authentication admits legitimate users and blocks those without credentials. Privileges limit the power of attackers if they steal credentials. This presents a major obstacle for data thieves.
Compliance with data protection regulations
Poor data security can lead to massive financial or even criminal penalties. Robust access controls limit access to confidential data, in line with HIPAA or PCI-DSS regulations.
Enhanced network visibility
Companies manage large communities of devices and users. Solid access controls h elp to manage connected devices. Only users with the right credentials can connect to sensitive resources. Devices and users must be logged and identified before they are granted access.
Access control challenges
Managing access is not simple, even in smaller organizations. The task is magnified with hundreds of users and a mix of on-premises and cloud resources. Common access management challenges include:
- Creating centralized user directories – All users should be visible to security managers. But unsecured application silos can emerge if managers delegate access controls to resource owners.
- Unsafe user behavior - Users may use unsafe passwords, connect via insecure public wifi, or add unknown devices to the network. Access systems must identify these issues. Training should ensure all staff follow cybersecurity best practices.
- Managing complex environments – Distributed networks may blend on-premises and cloud assets. Remote access control and managing third parties complicate the picture. Controls must adapt to reflect the network environment. This potentially creates a huge workload for administrators.
- Reporting – Systems to control access must log access requests. They also need to generate reports for auditing and compliance purposes. Both tasks represent a challenge in larger organizations.
Access control is an essential mechanism in cybersecurity. Solid access controls allow authorized individuals to access data and resources when and where they need them.
Access systems consist of many components, and there are various types. Controlling access provides various benefits such as regulatory compliance and improved security. Nonetheless, it can be complex and challenging to put in place. And making access control work efficiently requires careful consideration.
