Networks are always weak at the point of access. Attackers can breach defenses, steal data, or implant malware when endpoints are poorly secured. Identity and access management solves this security problem by controlling who has access to apps and data.
This glossary will look at how to design robust access controls. We will see IAM standards and how access management has become vital to data protection regulations. But first, let's introduce some key IAM concepts and system components.
IAM definition
Identity and access management is a security framework that combines user authentication and privileges management. The goal of IAM is to exclude unauthorized users from network assets. IAM is not a single solution with one standard implementation. Instead, it is an approach to security that considers every network's architecture and needs.
A solid IAM system guarantees user access to resources employees need. Workers can log on quickly and easily using secure forms of authentication. IT staff can manage privileges across an entire network without accessing specific apps. However, attackers will find it much harder to compromise critical assets.
Key takeaways
Here are the main points about IAM that we discuss in-depth later in this article:
- Poorly secured access points can cause data breaches.
- IAM includes authentication (verifying users) and authorization (granting appropriate access).
- Components of IAM include Single Sign-On (SSO), Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), analytics, and Zero Trust.
- IAM technologies include SAML, OpenID Connect, and SCIM.
- IAM is not a one-size-fits-all solution. It adapts to network architecture and needs.
Why is identity and access management important?
Identity and access management solves some of the most urgent network security challenges. Data breaches often result from credential theft and unauthorized network access. Poorly managed user profiles put apps and databases at risk. This may enable attackers to roam freely within network boundaries.

An IAM solution allows companies to guard the network perimeter at a critical point of vulnerability – the sign-on stage. Watertight user access systems protect on-premises and cloud deployments. This protection goes well beyond traditional password-based security.
Main IAM benefits
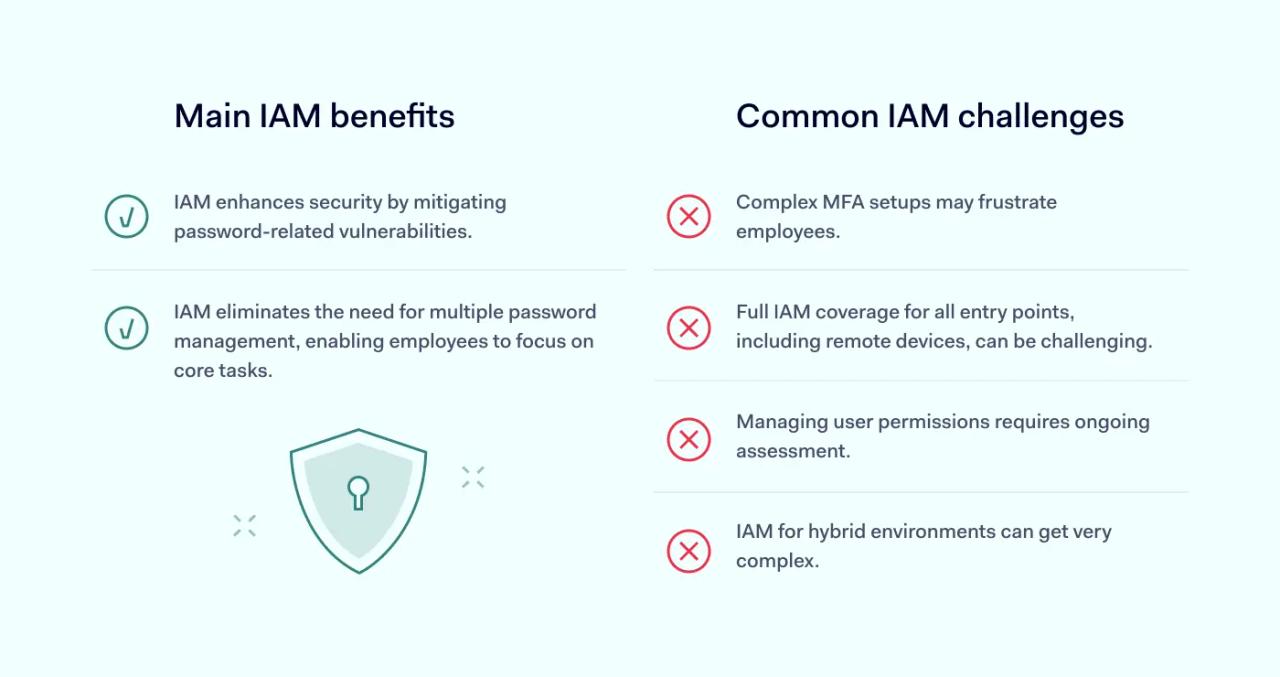
Improved security
Passwords are a major security vulnerability, especially when used on their own. Thieves can steal credentials and use them to gain access to sensitive data. Password recovery systems can also be compromised, making the life of cyber-criminals even easier.
IAM solves the password problem in two ways. Firstly, single sign-on (SSO) reduces the threat surface. A single login portal is easier to monitor and secure.
Secondly, IAM backs up SSO with authentication and authorization tools. IAM checks that every sign-on is legitimate. It rectifies employee mistakes and checks for potential threats. User privileges protect critical data while making it available if needed.
Productivity gains
The other main benefit of IAM is boosted productivity for employees.
SSO reduces the need to manage countless passwords. Employees no longer have to apply for access when they require specific resources. IAM matches roles and access privileges, allowing workers to concentrate on their core tasks.
Controlling user access with IAM simplifies the workload of IT experts. Role-based access controls make it unnecessary to manage profiles individually. Companies can automate the management of user privileges. This simplifies on-boarding and off-boarding staff.
Overall, IT professionals have more time and more control over network security.
However, it is essential to note that IAM can be complex. Common IAM challenges include:
- Implementing MFA. Employees may become frustrated with poorly designed MFA implementations with too many steps or complex requirements. Companies with a large remote workforce may also struggle to provide all workers with MFA hardware.
- Covering all endpoints. An IAM system must cover all network entry points. This includes IoT devices and work-from-home laptops. Provisioning all apps and users can take time and effort. However, SSO can solve this problem by bringing all apps under a single secure access process.
- Managing permissions. Determining appropriate permissions can be difficult. IT teams need to assess the needs of users and roles and constantly fine-tune privileges to balance security and access.
- Hybrid cloud deployments. IAM systems may cover both on-premises and cloud assets. Companies may have trouble finding a hybrid solution that covers all assets and is compatible with legacy software.
How IAM works
Identity and access management systems come in different forms. However, they usually have two critical functions.
1. Authentication
When users log onto networks remotely or devices are connected, companies need evidence that they are what they claim to be. IAM technology authenticates each access request.
Authentication entails comparing user credentials against a central database. This database generally extends beyond passwords or user names. It can also include MFA factors and contextual information about location and devices.
2. Authorization
After a user is authenticated, IAM systems must provide them with the right level of access to network resources. Each user must have the proper privileges to carry out their duties. But no user should have more freedom than they require.
IAM functions assign permissions to each user. Users can have access to groups of applications, but privileged access management can also be more detailed. For instance, users could have access to view data in a CMS. However, the IAM system may deny them the admin privileges needed to make changes.
In addition to those two key functions, IAM systems have an accounting function. They log user requests and report suspicious activity.

IAM technology must also establish visibility of the business user identity database. User profiles must be available for all services and devices at all times. This connection is necessary for authenticating and authorizing users.
IAM components
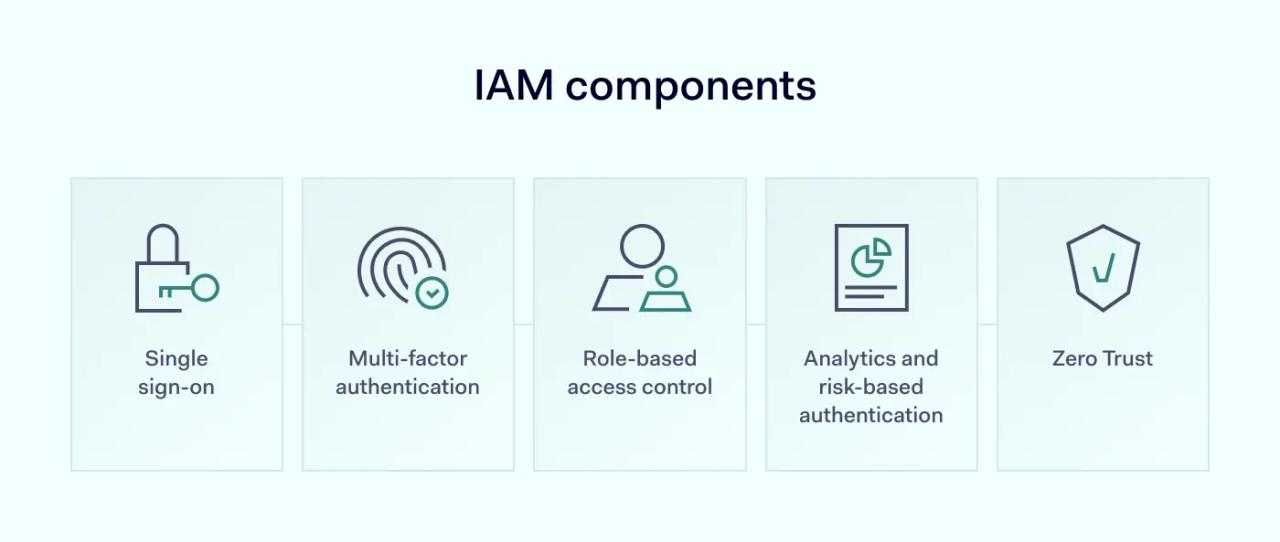
SSO
Single sign-on creates a single point of access for all cloud or on-premises resources.
Workers log on with passwords and MFA factors. The IAM system authenticates and authorizes their request. SSO provides access to any resources they require. There is no need to submit credentials for more than one service.
MFA
Multi-factor authentication strengthens perimeter defenses by adding extra access credentials. MFA factors include:
- Biometrics such as fingerprint or retinal scans
- Smart cards distributed across a remote access workforce.
- One-time passwords (OTP) supplied by third-party specialists like Google Authenticator. Employees receive a unique code to a personal device or specialist hardware tokens. Codes could arrive via email, SMS, or whatever is most convenient for the individual.
MFA adds another set of credentials above passwords and user IDs in all cases. MFA identification factors are time-limited or unique to the individual. They are, therefore, much stronger and more difficult to compromise than standard passwords.
RBAC
Role-based access controls allow security teams to provision users with privileges that fit their corporate role.
Role-based user provisioning reduces the workload on IT staff, making it easy to change user permissions as they change roles. RBAC automation helps avoid human error when off-boarding employees leaving the organization.
Analytics and risk-based authentication
IAM security systems may analyze contextual information and allow real-time permissions management. Risk-based authentication (RBA) assesses user activities and assigns each action a risk score. IAM controls deny access if actions are deemed too risky.
Analytic tools capture information about user activities. Activity logs provide valuable information to optimize network protection. They also record evidence to achieve regulatory compliance.
Zero Trust
Zero Trust Network Access (ZTNA) is a security model based on the "trust no-one, authenticate everyone" principle. The Zero Trust approach demands that users have minimal privileges inside network boundaries. This makes it a common aspect of IAM planning and architecture.
IAM implementation
IAM implementation requires to have a clear strategy in the first place. Your first step should be network architecture mapping. This way, you’ll be able to understand what resources you have and whether there are any existing IAM processes.
Afterward, list the users with wide-range access because they face the biggest risks. The second list should be for the rest of the users and their access levels. Then, make a risk assessment of all applications.
Now, you should improve your data storage practices. Data should be visible to security managers, and standardizing its formats is also highly recommended.
Finally, it’s time to choose the IAM solutions. They should have these main IAM functions: Authentication, Authorization, SSO, Auditing systems, and Identity federation. And don’t forget about the option to migrate from your existing tools.
While each IAM strategy differs according to the business type and its requirements, there are still key elements found in every instance:
- User management. Each user should get an identity that gives access to the resources. Your strategy should also address user (de-)provisioning.
- Authentication. All user identities must be verified at the point of entry. Using MFA and strong passwords is highly recommended.
- Authorization. Users should have access only to authorized resources. Administrators should have access to all sensitive information.
- SSO. It’s highly recommended because you get a single access portal for both cloud and on-premises resources.
- User directories. IAM works only with a constantly updated list of users. They shouldn't stay separated if there’s more than one user directory.
- Identity federation. An important part of any IAM strategy, identity federation allows users to connect with third-party SaaS apps and cloud platforms.
- IAM auditing. Regular auditing helps you track user activity and log security alerts. Audit data will also help to comply with data regulations.
To sum up, IAM implementation is a challenging feat. But with the right strategy and implementation of best practices, you will create a secure, convenient, and compliant system.
IAM standards
Identity and access management standards guide users when securing their network. Standards are security frameworks that explain how to comply with industry best practices or official regulations. They are a good foundation for implementation and compliance strategies.
Relevant standards to think about include:
- AAA. AAA is the standard IAM framework. It describes a three-part strategy, including authorization, authentication, and accounting (see above).
- ISO 27001. Created by the International Standards Organization, ISO 27001 deals with creating an information security management system. Part of this process involves controlling access and assigning privileges.
- NIST SP 800-63, Digital Identity Guidelines. Seeks to provide clear guidance for access management that applies to all corporate users.
IAM and compliance regulations

In the IAM domain, relevant compliance regulations include:
- GDPR (General Data Protection Regulation). Created by the European Union. This regulation deals with data security for businesses operating within EU boundaries; IAM is critical. Companies can achieve compliance by ensuring information is only accessible to authorized users.
- CCPA (California Consumer Privacy Act). Applies to companies operating in the State of California. This regulation dictates how companies should protect sensitive data, including limiting access to authorized individuals.
- HIPAA (Health Insurance and Portability Act). Sets out requirements for companies handling private medical records in the USA. Includes detailed requirements for protecting patient data via access management.
- SOX (Sarbanes-Oxley Act). Regulates financial corporations in the USA. Includes a sub-section on data protection. This explains how companies should secure financial data, including preventing unauthorized access.
IAM technologies and tools
Identity and access management technologies allow users to meet the above standards and regulations. Technologies include standard languages and tools that operate across any IAM platform.
- Security Access Markup Language. SAML is an open-source standard for exchanging authorization and authentication information. SAML uses digital signatures to exchange data, forming a core part of many SSO systems.
- OpenID Connect. Works on top of the OAuth 2.0 protocol, allowing third parties to access network resources securely. OpenID Connect adds IT management to OAuth and is commonly used to build SSO portals.
- System for Cross-Domain Identity Management. SCIM is a cloud-based standard for exchanging user profiles. It is generally used in privileges management setups, allowing the safe sharing of user profiles across cloud environments.
Learn more about IAM compliance
The importance of IAM in cloud computing
Several factors make IAM a critical technology for data management in the cloud.
Cloud assets are hard to secure via traditional passwords. Employees require many credentials to access the resources they use. Human error and credential thefts are common causes of external data breaches.
The cloud itself is device agnostic. Remote workers may use unsafe endpoints, putting cloud-hosted applications at risk. Attackers on public wifi could gain access to cloud assets while posing as legitimate users.
Instead of device or location-based security, IAM focuses on user identities. Identity-centered approaches are a much better way to handle cloud computing security risks.
- Systems assign privileges to roles or users. Under Zero Trust principles, users only have access to assets they need. Nobody can roam freely across cloud platforms and apps.
- SSO covers complex cloud deployments, bringing all cloud resources together under one access point.
Difference between identity management and access management
As the name identity and access management suggests, identity and access are distinct concepts. It’s essential to know the difference when implementing IAM.
- Identity management is the storage of information about user identities. It stores user data in a central database and compares access credentials against this data. If the information matches, identity management systems allow entry to network resources.
- Access management is the counterpart to identity management. It assigns privileges to legitimate users. Access management tools allow users to run specific apps or platforms while keeping sensitive resources off-limits.
Control dynamic perimeters with identity and access management
Information security starts with managing access. Companies need to allow access to workloads and operational databases. But they also need to prevent access for individuals who seek to cause harm. Identity and access management make this balancing act possible.
IAM tools allow organizations to protect hard-to-secure cloud assets. They make it easier to prove compliance with data security regulations. And they simplify network management via tools like SSO. These reasons make implementing IAM a must for most businesses.
