PCI-DSS is a regulatory framework for the online payment processing industry. With online fraud rising and data breaches constantly in the news, protecting payment data is more important than ever. Understanding PCI-DSS is a critical business requirement.
This article will explain:
- What is PCI-DSS?
- What it means to be PCI-DSS compliant.
- The core principles behind the regulations.
- How compliance levels work.
- Why compliance is so important for modern businesses.
- A quick PCI-DSS compliance checklist.
PCI DSS definition
PCI-DSS is a set of standards that seeks to protect the security of online payments. Any company handling online payments must comply with PCI-DSS. If they fail to comply, organizations risk large fines and reputational damage. And they will also face a higher risk of data breach attacks.
- PCI stands for "Payment Credit Information." This includes any private financial data that customers provide to online businesses.
- DSS stands for "Data Security Standard." Standards are rules that operate across business sectors. PCI-DSS applies to all companies handling online payments. And it specifically relates to Data Security. This involves storing, moving, and accessing cardholder information.
The PCI-DSS standards were introduced by the PCI Security Standards Council in 2006. The PCI Security Standards Council is an umbrella group featuring the world's largest credit companies. Members include Visa, Mastercard, American Express, and JCB International.

PCI-DSS is not a set of federal regulations. Companies cannot be prosecuted for non-compliance. However, in practice, PCI rules are the basis for robust compliance strategies.
The rules were designed to meet legal requirements. They are updated regularly to reflect technological developments. And information security laws have generally followed industry recommendations. As a result, following PCI-DSS is widely seen as a regulatory standard.
What is PCI DSS compliance?
An organization is PCI-DSS compliant if its cardholder data environment meets PCI-DSS credit handling rules. PCI compliance is the task of meeting these rules. But it is not just a goal to reach. Compliance is a continuous challenge.
To comply fully with PCI-DSS, companies must audit and test their cardholder security systems. They must make sure that stored cardholder data is only accessible to authorized users. And they need to protect cardholder data in secure locations, locked away from malicious actors.
PCI-DSS rules also change regularly. For example, PCI-DSS 4.0 arrived in 2022. Version 3.0 was introduced in 2014, with a 3.1 revision in 2015 and a further revision in 2016. Compliant organizations must keep track of updates. They must amend their security posture to reflect new requirements and technical advice.
Why is PCI DSS compliance important?
PCI compliance is a critical part of running an online business. The reason is simple. PCI-DSS standards provide the best available guidance to lock down sensitive data and protect customer information.
Poor data security is expensive. According to IBM, the average breach costs $4.35 million. Robust PCI compliance is the best way to minimize data loss risks. This doesn't just limit financial losses resulting from attacks. Compliance also protects against reputational damage. And it reduces exposure to federal prosecution for putting data at risk.
PCI certification covers the most common causes of data breaches. Compliant organizations have controls in place to manage:
- Insecure payment processing devices such as in-store readers.
- Digital cardholder data environments.
- Paper financial records of card data (if they exist).
- Security devices like cameras that record credit card data.
- Unsecured network access points.
How does PCI DSS compliance work?
PCI compliance is overseen by the PCISC. The PCI Security Standards Council manages a document library that contains the latest regulatory standards. This library also includes "at a glance" digests, quick reference guides, and summaries of recent changes.
PCI regulations function like checklists. Organizations compare their security framework to PCI-DSS recommendations. And they make changes based on these recommendations. This process usually takes a three-stage format:
- Assessment. Auditing the cardholder data environment. Organizations must list all devices or applications that handle credit card data. They must apply PCI recommendations to identify potential vulnerabilities that may expose cardholder data.
- Mitigation. Organizations need to put in place controls to bring their security systems in line with PCI-DSS standards.
- Documentation. Organizations must log and report any changes made to harmonize their systems with PCI-DSS. This provides documentary evidence that the organization is compliant with current security standards.
Core principles of PCI DSS compliance
Most PCI compliance strategies involve the application of six core PCI-DSS principles. These principles summarize the most important information security obstacles. They simplify a complex challenge and help organizations focus on what matters.
Principle 1: Network security
Protecting the network edge is a critical part of securing credit card data. Firewalls, software updates, and threat detection systems guard against malicious agents and intruders.
Principle 2: Data protection
Cardholder data should be logged and stored in secure locations. Customer data should be separated from other network assets. And security teams should apply encryption of all critical information.
Principle 3: Ongoing vulnerability management
Organizations should assess potential vulnerabilities. Security teams should leverage all available tools, such as malware scanners and anti-virus software. And PCI requirements should be built into daily data security tasks.
Principle 4: Access control
Cardholder data should only be accessible to authenticated and authorized users. Apply role-based controls to manage access and remove privileges when they are not required. This may also involve the need to restrict physical access to devices holding cardholder data.
Principle 5: Security testing
Penetration testing should detect security weaknesses. Audit trails should accurately record user activity. Audit logs should be stored securely and testing should take place regularly.
Principle 6: Robust security policies
Information security policies must document security controls and explain user responsibilities. They should be accessible and delivered to all relevant individuals. And they should always be written with PCI-DSS in mind.
PCI DSS compliance levels
PCI compliance falls into four categories or levels. PCI DSS levels are linked to the number of transactions processed by the organization. So for example:
- Level 1: Deals with companies processing over 6 million credit card transactions per year.
- Level 2: Companies processing between 1 and 6 million transactions annually.
- Level 3: Companies processing between 20,000 and 1 million transactions annually.
- Level 4: Companies that process fewer than 20,000 transactions per year.
Generally speaking, Level 1 organizations have much more complex compliance requirements than businesses operating at Level 4. The system helps to reduce the burden on small businesses and organizations that rely less on credit card processing. And it identifies larger companies with a very high risk of credit card fraud.
Who must comply with PCI DSS?
Any organization that maintains a cardholder data environment (CDE) must comply with PCI standards. This includes merchants who sell products or services online. But it also includes companies that store personal financial information. And it covers companies that process or communicate credit card information for third parties.
Benefits of PCI-DSS
The main benefit of PCI-DSS compliance is obvious: compliant companies meet the highest data security standards. Their data security systems accord with industry best practices. And the organization faces a relatively low risk of experiencing regulatory penalties. But benefits go beyond simple compliance.
- Trust. Customers assess companies based on their honesty, openness, and commitment to security. PCI-DSS compliance is a strong signal that a company respects customer privacy. A compliant company is more likely to protect payment card industry data against external threats. This builds trust and encourages sustained customer loyalty.
- Dynamic security. Compliance is a moving target. To remain compliant, companies must be aware of the latest security tools and trends. This encourages a dynamic security posture. IT teams will constantly update their systems to stay compliant and meet PCI standards.
- Data breach risk. Data loss is a nightmare for online retailers. Complying with PCI standards reduces data breach risks. External attackers will find it harder to access the cardholder data environment. Systems will neutralize threats before outsiders gain access to cardholder information.
- Compliance strategies. PCI compliance builds internal knowledge. IT teams gain experience in implementing regulatory standards. They can use this knowledge to comply with other regulations such as HIPAA or GDPR.
- Smooth third-party relationships. Third parties may require PCI compliance as a condition for working with partners. Compliance makes it easier to collaborate securely with other companies. It demonstrates that a company focuses on protecting payment card industry data. This makes it a much more attractive partner.
Consequences of not complying with PCI DSS
There is another way of looking at PCI-DSS compliance. Not complying has very serious negative consequences, including:
- PCI-DSS penalties. The PCI-DSS Security Standards Council has the power to levy financial penalties on non-compliant merchants. Fines vary depending on the organization's compliance level. But they range from $5,000 to as much as $100,000 per month.
- Lawsuits. Compliance shields companies against data breaches and class action litigation. Compliant companies are far less vulnerable to legal action and settlement costs.
- Government fines. Non-compliance also raises the risk of regulatory fines from governments. For example, the European Union's GDPR can levy fines of $20 million for poor privacy protection.
- Reputational harm and lost revenues. The most serious long-term effect of data breaches is loss of trust. Brands can lose market share to compliant competitors. Customers will prefer companies that take information security seriously.
12 PCI DSS requirements
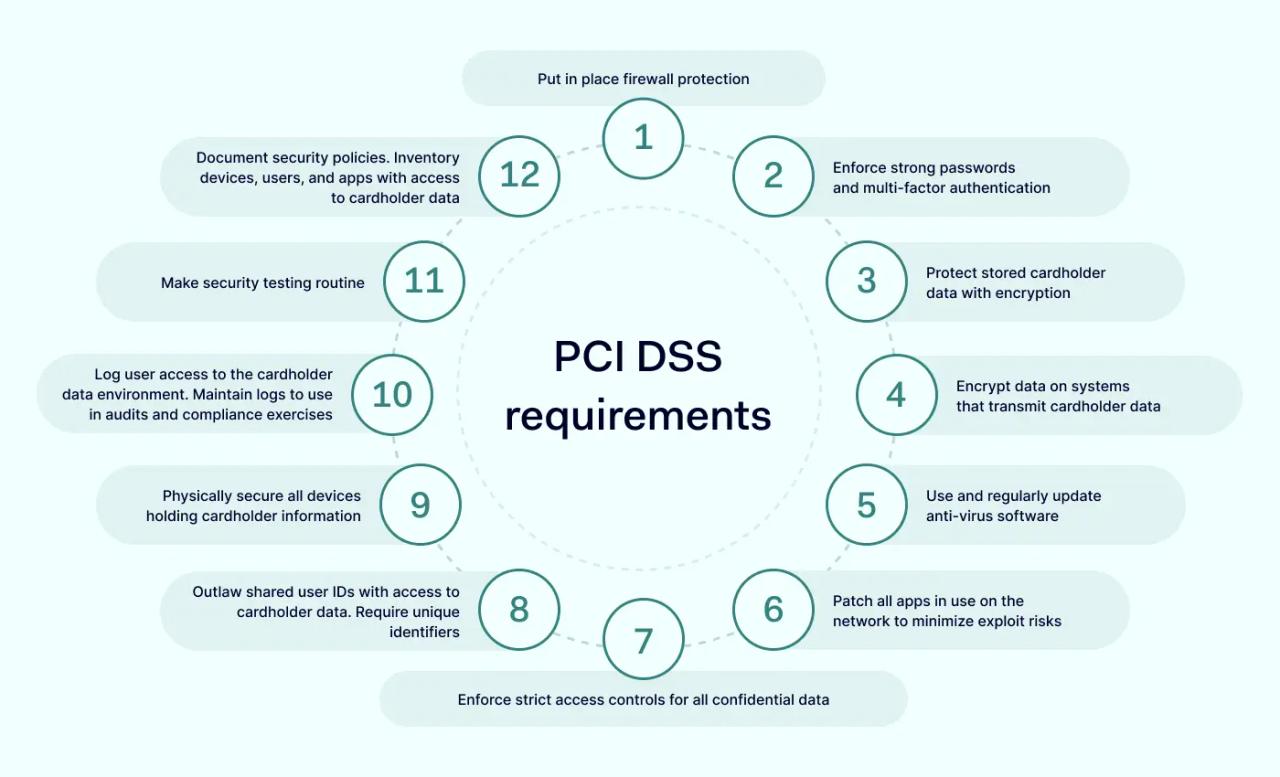
- Put in place firewall protection.
- Enforce strong passwords and multi-factor authentication.
- Protect stored cardholder data with encryption.
- Encrypt data on systems that transmit cardholder data.
- Use and regularly update anti-virus software.
- Patch all apps in use on the network to minimize exploit risks.
- Enforce strict access controls for all confidential data.
- Outlaw shared user IDs with access to cardholder data. Require unique identifiers.
- Physically secure all devices holding cardholder information.
- Log user access to the cardholder data environment. Maintain logs to use in audits and compliance exercises.
- Make security testing routine.
- Document security policies. Inventory devices, users, and apps with access to cardholder data.
PCI-DSS compliance helps organizations secure customer data and maintain effective security controls across the cardholder environment. Robust compliance strategies reduce the risk of data breaches and external attacks. They build trust and internal knowledge. And they shield organizations from regulatory penalties.