Role-based access control allows organizations to connect access privileges to user roles. RBAC makes it easier to manage user permissions and protect sensitive data from unauthorized access. These abilities make it a go-to cybersecurity tool. This article explains how to implement role-based access control, alongside some helpful tips to manage it effectively.
How to implement role-based access control
Setting up role-based access control requires careful planning. Improperly defined role groups can lead to security gaps and user access problems. This neutralizes the benefits of RBAC and may put critical assets at risk.
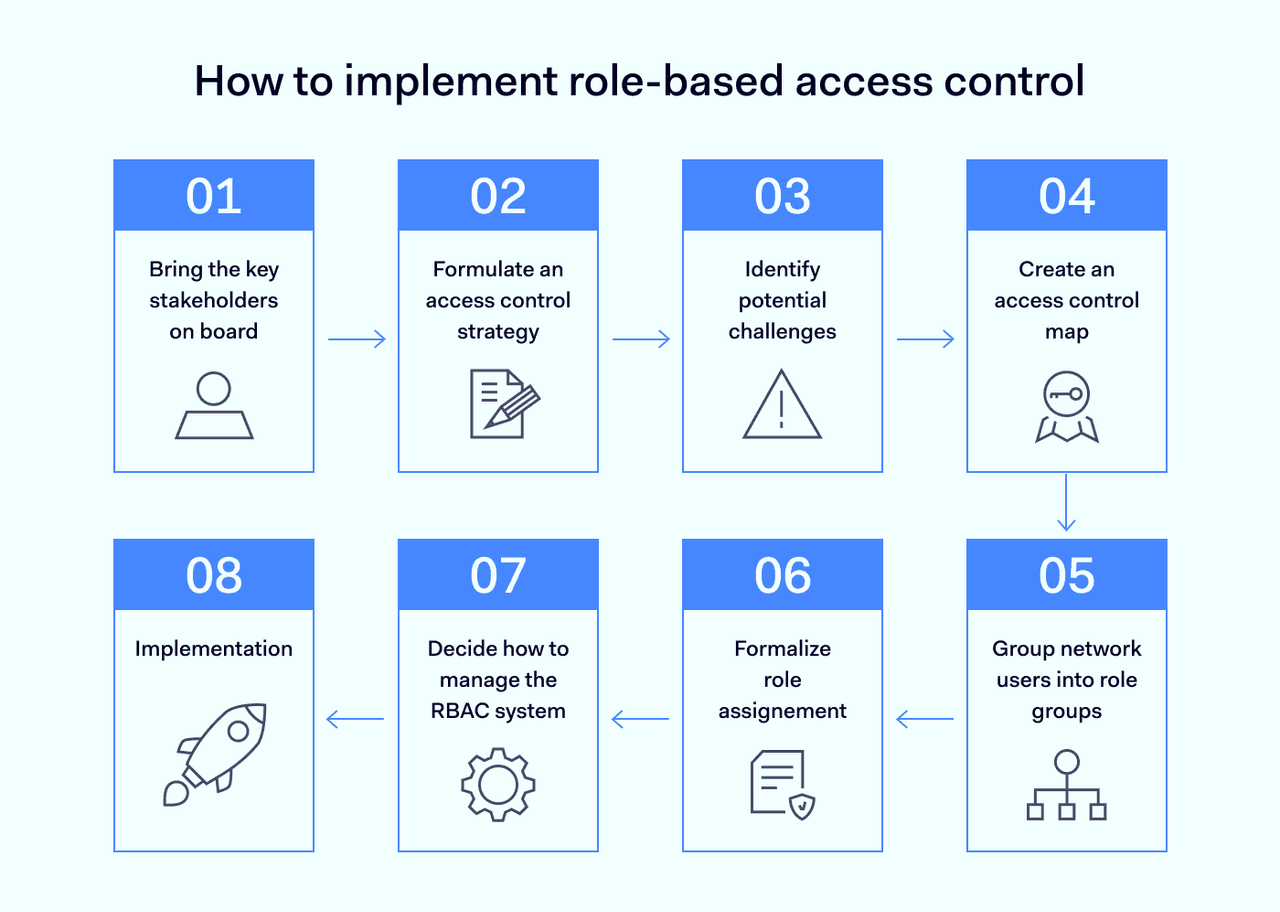
The process below sets out a typical route to a robust access control setup. It provides a good starting point for RBAC implementation.
Step 1: Bring the key stakeholders on board
Creating a solid RBAC setup starts with communication. The implementation team should bring all department managers into the conversation. And they need to explain how role-based access works. Security teams rely on other departments to define role groups and necessary access rights. So smooth communication is essential.
Step 2: Formulate an access control strategy
The next step is creating a clear implementation plan. Think about what role RBAC will play within your organization. Are there any critical assets that require enhanced protection? Is the organization likely to expand, adding new hires, locations, or cloud-hosted assets?
It is important to define the desired outcome of the project. For example, your goal could be "a role-based access control system with automated provisioning and off-boarding, and scope to add additional controls for confidential data."
Step 3: Identify potential challenges
Look for any possible obstacles to RBAC implementation. This could include inconsistent use of multi-factor authentication or the use of multiple operating system formats. Managing access for users based on-premises or at home can also be problematic.
Regulatory compliance is also vital. Role-based access controls should meet regulatory standards and help you achieve your regulatory aims.
Step 4: Create an access control map
Create a catalog of assets that require access controls. Include cloud and on-premises applications, email servers, every financial and customer database, confidential employee records, and cloud collaboration tools that employees use.
Step 5: Group network users into role groups
Role groups are collections of users with similar access privileges. In an ideal world, RBAC setups feature the smallest possible number of roles. This makes managing privileges easier and reduces the scope for human error. But organizations are complex. Balance simplicity with the user needs to define roles that function properly.
One way to find the right balance is by adopting a two-strand approach. Enlist departmental managers to suggest roles that meet the needs of their workforce. At the same time, IT teams can monitor access patterns. This makes it possible to detect groups of workers that need the same access rights.
Step 6: Formalize role assignment
Use the information gathered from your earlier analysis to populate the RBAC system with functional roles. Apply the principle of least privilege to minimize the access rights of each user group. Roles should only have access to the resources that users need. The system should deny access to all other assets.
This is why information gathering is so important. For example, IT teams need to know which Salesforce users have write and delete permissions, and who can only read or search customer database records.
Step 7: Decide how to manage the RBAC system
Before role-based access control systems go live, it's important to create RBAC management policies. Explain how administrators will audit roles to prevent role explosion and avoid privileges creep. Schedule compliance audits to prove that access controls are functioning as designed.
Governance is also important . Define who is responsible for generating and maintaining roles. Ensure no single person has the ability to approve administrative privileges. And communicate security policies to all network users.
Step 8: Implementation
Roll out RBAC systems slowly and check for any problems during the implementation process. Extend access controls to a single department at first, and use this first stage as a chance to fix any issues before full rollout.
RBAC is a learning process. Don't expect frictionless operation immediately. Access controls always have teething problems in the first few months of operation.
Be attentive to feedback from individual users and managers. It should quickly become clear if roles have been improperly assigned. If the planning phase was carefully managed, minor changes should be required and nothing more.
Tips on how to manage role-based access control
Robust access control is an essential part of an organization's security posture. But how should RBAC users administer access control systems to ensure integrity, security, and efficiency? Here are some tips that will simplify access management challenges.
Be prepared to make changes
Role-based controls are created at a single point in time. But as time progresses, organizations change. Access controls must change in step with the organization that they serve.
It is important to review roles and privileges regularly. Schedule periodic audit exercises that cover several critical areas:
- Check that roles match the actual needs of users. Users may switch applications, change their organizational structure, or switch to different work locations. All of these shifts can affect the integrity of role-based access controls.
- Establish whether any new controls are needed. For example, a company might implement RBAC before migrating sales data to a cloud-hosted solution. Admins will need to adjust any roles that access data on the new system.
- Ask for feedback from stakeholders. Bring senior managers into the audit process. RBAC works best when all users are engaged and willing to provide information. IT teams cannot operate in a silo as they manage the access system.
Remain vigilant to potential vulnerabilities
RBAC management should be continuous. IT teams need to track suspicious system access requests and patterns of behavior.
For example, a cluster of denied access requests from users in a role group could be evidence of a phishing attack. Or it could be a flaw in the way that role is configured. Constant monitoring can detect the real issue and make any necessary changes.
It helps to log data about requests for security assistance. From time to time, there may be spikes in assistance requests from departments or project teams. Monitor those spikes and use them to fine-tune roles if needed.
Create clear processes for privileges escalation
Sometimes, administrators provide users with temporary privilege escalations. Users may need access rights for short-term projects. A flexible RBAC system can accommodate these adjustments, enabling seamless workflows.
Implementing temporary role changes can be risky. When they grant access administrators should log all escalation requests. They should also track user activity for the duration of the escalation. It is also essential to remove any additional privileges when the user reverts to their original role.
Consider adding ABAC to manage granular security
Controlling access can become harder as RBAC expands. Privileges creep can see users acquiring too many permissions. Roles can overlap as organizations become more complex. And the number of roles can become unmanageable. When this happens, applying additional controls can help.
Attribute-based access control (ABAC) supplements role-based systems. ABAC allows admins to secure assets with contextual or environmental controls. For example, system access to financial records could be limited to employees using MFA within office hours, in a specific location.
Access Control Lists are another option. Administrators can configure ACLs for individual devices or applications. They can be a useful way to control access temporarily.
ABAC and ACLs can compensate for some of RBAC's weaknesses. But it is not a substitute for properly modeling and implementing role-based access architecture.
Conclusion
RBAC is a powerful way for organizations to strengthen their security posture. Role-based controls are simple to manage, prevent unauthorized access, and help organizations comply with security regulations. However, to deliver these benefits RBAC systems must be well-constructed.
Planning, communication, and awareness are the keys to successful implementation. By following the steps outlined in this article and implementing the management tips provided, organizations can protect their data efficiently.
