Learning Objectives
After reading this article, you will be able to:
- Define what a web application firewall is and how it functions to filter HTTP traffic at the application layer
- Explain the different types of web application firewall deployments including network-based, host-based, and cloud-based
- Understand common web application threats like SQL injection, XSS, DDoS attacks and how WAFs help prevent these
- Describe how WAFs can be used to enforce security policies, detect threats, and apply allowlists/blocklists
- Compare the benefits and limitations of on-premises versus cloud-based WAF solutions
- Give examples of how WAFs are used in practice to secure websites, prevent downtime, meet compliance requirements, and patch vulnerabilities
- Identify the key attributes of WAFs, like their ability to allow/block access, track threats, and only protect HTTP-based apps and web servers
What is a web application firewall (WAF) in cybersecurity?
A web application firewall is a network security device that creates a secure barrier between web apps and the external internet. WAF systems filter HTTP traffic to mitigate attacks and apply protection policies to allow or block access to web applications.
WAF solutions are intrusion prevention systems that protect against application layer attacks like SQL injection and cross-site scripting (XSS). These vulnerabilities are common vectors for data breaches. Application-focused firewalls reduce the threat surface and make critical threats much less likely.
Why is WAF important?
WAFs play a key role in web security by filtering HTTP traffic and protecting apps from common threats like SQL injection, cross-site scripting, and API exploits. WAFs help prevent data breaches, denial of service attacks, malicious code injection, and other incidents that could compromise sensitive information or disrupt core services.
WAFs are also crucial for regulatory compliance. Standards like PCI DSS impose strict security requirements on how organizations must safeguard sensitive data handled by web-facing applications and solutions. Non-compliance can result in costly fines and a loss of customer trust.
When used as part of a defense-in-depth approach with measures like multifactor authentication and malware protection, WAFs are an essential layer of protection for organizations’ digital assets and web applications.
How does a web application firewall (WAF) work?
Like remote proxies, web application firewalls filter traffic arriving at the network edge before communicating with local servers. But they do so at OSI Layer 7 and only deal with web applications.
A web application firewall enforces control policies between web applications and clients seeking network access. If users meet access conditions, the firewall allows access. Up until that point, there has been no direct connection between users and servers.
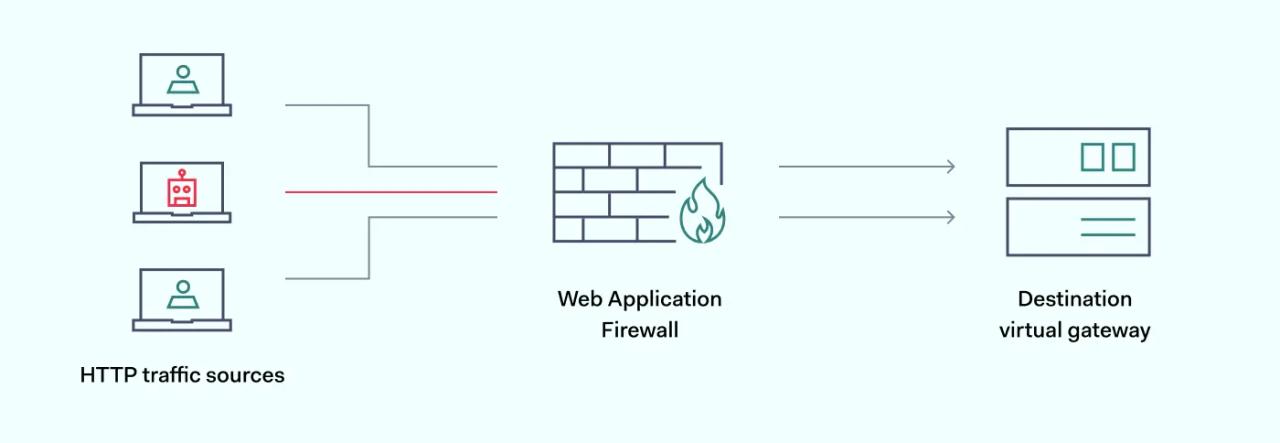
WAF systems also manage access to server content by applying allowlists or blocklists. Allowlists (positive security model) restrict access requests from all users unless they are listed in the firewall security policy. Blocklists—negative security model—operate in reverse. They allow every request unless the IP address is specifically blocked.
However, web application firewall tools are limited in fully securing today's threat landscape. Most importantly, they do not filter protocols like FTP or SMTP. WAFs are only designed to protect web assets.
As a result, WAF systems usually form part of wider cybersecurity architecture. They are a critical component of internet safety. However, organizations may need additional tools to prevent malicious traffic and protect data.
The different ways to deploy a WAF
Organizations should understand the architecture and licensing models available when choosing a WAF. Fundamentally, WAFs can be open-source, commercial/paid, or hybrid. An open-source solution offers more flexibility in customizing and integrating the WAF configuration with other tools. However, internal resources are also required to support and maintain the WAF software.
- Open-source WAFs are becoming increasingly popular. They are easier to customize, provided organizations possess development expertise. And open source versions benefit from the skills of the global OWASP community. Community input from OWASP helps to neutralize emerging exploits and SQL vulnerabilities.
- Commercial/paid WAFs can be purchased from vendors as off-the-shelf application firewalls. This option simplifies installation. However, users will have fewer customization options. They must also rely on their vendor to supply updates and maintain up-to-date threat databases.
Types of Web Application Firewalls
Network-based WAF
Network-based WAF technology protects local network assets. This type of network-based WAF is usually installed on a hardware appliance. The web firewall device connects to local servers and the external internet. It filters traffic as it arrives and leaves, not unlike the role of a reverse proxy firewall.
Network-based WAFs often deliver high speeds and low latency. This is because they are installed extremely close to the assets they secure. But there are disadvantages. Hardware devices cost more to install. They also need space, which can be scarce in office settings. And all hardware appliances will need regular maintenance.
Host-based WAF
Hosted application firewalls are installed locally on network hosts. They generally integrate with the applications they protect, providing users with more flexibility than other WAF solutions. Technicians can toggle access settings for each web application and set priorities for the most sensitive network assets.
The downsides of host-centered web firewalls include high data consumption. Installing WAF systems for each core application can reduce network capacity. Web firewalls are often complex to set up. Multiple WAFs may be needed for different workstations or servers. They take time to install and can become expensive in some cases.
Cloud-based WAF
Cloud-hosted web firewall systems protect Software-as-a-Service (SaaS) applications stored in a public or private cloud. Locally hosted web firewalls struggle to safeguard cloud assets. But cloud WAFs are designed to regulate traffic flows to SaaS applications. This makes them the only secure web firewall option when protecting cloud-stored data.
Cloud WAFs are generally purchased via subscription models. Users purchase coverage from cloud security providers (CSPs). The CSP maintains the cloud firewall. They will apply updates and counter emerging threats. And cloud firewalls are usually simple to install. They simply bolt onto cloud environments to provide instant coverage.
Most major cloud platforms provide firewall solutions. For example, AWS (Amazon) allows users to create individual app security policies. Users can track threats, deny exploits, and monitor access requests.
Alongside basic protection, cloud firewalls have another important benefit. They are fully integrated with cloud development processes. DevOps teams can add new content or services to virtual environments securely. Companies can develop and reshape cloud deployments without compromising safety.
On the negative side, cloud-hosted WAFs are always managed by third parties. Users hand over some controls to their service providers. There will be fewer customization options as well. But for many cloud-reliant companies, this is a worthwhile trade-off.
Attacks that WAFs prevent
Web firewall solutions can neutralize many of the most common web vulnerabilities. This matters because online threats are a frequent cause of damaging data breaches. Here are some of the most common web exploits a WAF protection model will defend against.
Attack category | Explanation | WAF protection technology |
|---|---|---|
Cross-site scripting (XSS) | Cross-site scripting attacks involve injecting client-side scripts into publicly viewable web pages. Attackers turn a harmless website into a source of malicious Javascript. | WAFs apply security policies to filter access requests and block suspicious digital signatures. |
SQL injection attacks | SQL injection attacks use unsecured web forms to "inject" malicious code into websites, allowing attackers to compromise servers and data. | WAFs protect against SQL injection by identifying threats before they reach servers. |
Distributed-Denial-of-Service (DDoS) attacks | DDoS attacks direct large traffic at targeted servers to force them offline or conceal other attacks. | WAFs automatically provide DDoS protection through limited access requests exceeding a traffic threshold. |
Web scraping | Attackers extract data from websites without permission to use it for copycat sites or other malicious purposes. | WAFs detect suspicious scraping patterns and add scrapers to a blocklist. |
Unauthorized data extraction | Web application firewalls help track various types of malicious traffic, including unauthorized transfer of sensitive files. | WAFs enable the creation of data protection policies and the detection of policy violations in HTTP traffic. |
WAF use cases
Application-level firewalls are being used to secure network servers and online content. The WAF security model has a range of use cases, making it a common addition to corporate cybersecurity architecture. Let's run through a few practical use cases to show how valuable the technology can be.
Website protection
Most importantly, web firewalls secure the applications used to deliver web services. Most customer-facing companies use online sales portals and forms to sell products. Customers and companies interact via web applications, which are a prime target for malicious attackers.
WAFs filter and track HTTP traffic. They monitor activity across API endpoints, ensuring API protection and including cloud-hosted assets. The same technology maintains threat visibility and quickly detects threats before compromising assets. This ensures smooth eCommerce activities, remote work, and customer management.
Downtime prevention by DDoS protection
Companies must maximize network uptime. Any outages can dent the bottom line and cause reputational harm. However, companies need robust protection against denial-of-service attacks to ensure reliable operations.
WAF systems provide strong DDoS protection. When bots swarm and attack servers, the web firewall applies rate limiting to keep legitimate traffic flows in check. They also track bot behavior to prevent data extraction and defeat data scrapers.
Data security compliance
Data protection is a regulatory priority for all companies. Standards like GDPR, CCPA, and HIPAA mandate robust data security policies. Governments worldwide seek to penalize weak safety measures and protect citizens' data. Poorly secured web applications are likely to incur large fines.
WAFs have many compliance benefits. For instance, they guard credit card payment portals. They prevent SQL attacks that steal financial data. Web firewalls secure healthcare records, banking data, and student information. Any data stored behind web applications requires specialized firewall protection.
Simple content management
Companies often want to manage the content available to local network users. For example, managers might restrict social media sites during working hours as part of their security framework. Or IT teams could maintain blocklists of phishing-related websites. And schools may block unauthorized access to all adult content.
A web firewall helps manage web content access. IT teams can use the web app firewall's HTTP filtering capabilities to allow or deny access to individual websites. DNS redirects make it easy to control which sites are visible to local users.
Apply patches and counter exploits
Web applications can develop vulnerabilities due to outdated versions. Vendors don't always deliver automated patches to clients. Patching schedules can be slow and unreliable. Moreover, IT teams aren't always able to devote enough time to update every application promptly. This creates space for zero-day exploits to cause carnage.
WAFs provide an insurance policy against exploits. Even if web applications are unpatched, the firewall offers constant security. It tracks network traffic and prevents malicious activity. And in some situations, web firewalls are the only viable security option. For example, if companies rely on legacy apps that are no longer updated.
Cloud WAF vs on-premises WAF
Web application firewalls have many use cases and benefits. But there is one important question to answer. Should network managers choose next-generation cloud firewalls? Or do older on-premises WAF solutions offer sufficient security?
This is an urgent practical question for many companies. And the answer is simple. Companies should choose the right web firewall for their networking needs.
On-premises WAF
On-premises web firewalls are ideal for securing locally-hosted web content. A web firewall can secure remote access gateways to locally hosted apps and private clouds. WAF solutions can also effectively protect network servers connected to the external internet.
Hardware firewalls are adaptable and managed rules remain totally under the control of local IT professionals. Companies can extend security rules to their servers and apply granular security policies for each web application.
However, on-premises web firewalls are complex to install and maintain. If companies plan cloud migrations in the future, their web firewall may swiftly become obsolete. And it is not easy to estimate firewall capacity needs. Adding more capacity can become expensive. So hardware firewalls are less well-suited to companies that plan to grow.
Cloud firewalls
Cloud WAF is delivered in the form of security-as-a-service. WAFs in the cloud are managed by separate cloud vendors, who sell coverage on a subscription basis. The firewall secures all cloud applications, and clients can set security policies via centralized dashboards.
Cloud WAF is a reliable way to lock down SaaS applications and confidential data held on cloud containers. The cloud firewall tracks access and blocks threats – generally more efficiently than on-premises alternatives. It gathers data for audit purposes and neutralizes cloud DDoS attacks.
WAF in the cloud also scales smoothly. Users can purchase extra capacity in the vendor's virtualized data center. There are few limits to data processing capacity or the size of a client's full cloud-based WAF deployment. Cloud WAF is therefore a sound option for companies with growth potential.
Key points about web application firewalls
- Sit between network servers and the external internet.
- Filter incoming and outgoing traffic. Separates the server from internet users.
- Operate at OSI Layer 7 (the Application Layer).
- Can allow or restrict individual users, or determine levels of access to web content.
- Only defend against HTTP-based attacks such as SQL.
- Available as hardware appliances, server applications, or cloud solutions.
FAQ
What does WAF mean?
WAF stands for web application firewall. Web applications are apps hosted on network servers. These servers could be locally hosted or stored in the cloud. Firewalls are network security tools that filter traffic and restrict malicious access. When combined with web apps, firewalls block website threats and keep user data safe from data thieves.
What is the difference between a WAF and a firewall?
A web firewall is a type of firewall, but there are many other varieties. For instance, you will find next-generation firewalls, packet filtering firewalls, proxy firewalls, and hardware firewalls. The key aspect of WAF is that firewall protection extends security rules to web applications. A WAF operates by specifically filtering HTTP traffic. It will not shield general network infrastructure or track TCP/IP transfers.
Is WAF a DDoS protection?
Yes, in many cases. Distributed Denial-of-Service (DDoS) attacks seek to flood servers with traffic. The aim is to take servers offline and cause damage to networks and websites. A web firewall can prevent DDoS floods by detecting suspicious traffic and regulating access requests. If the firewall keeps request rates low, the server should remain online and healthy.