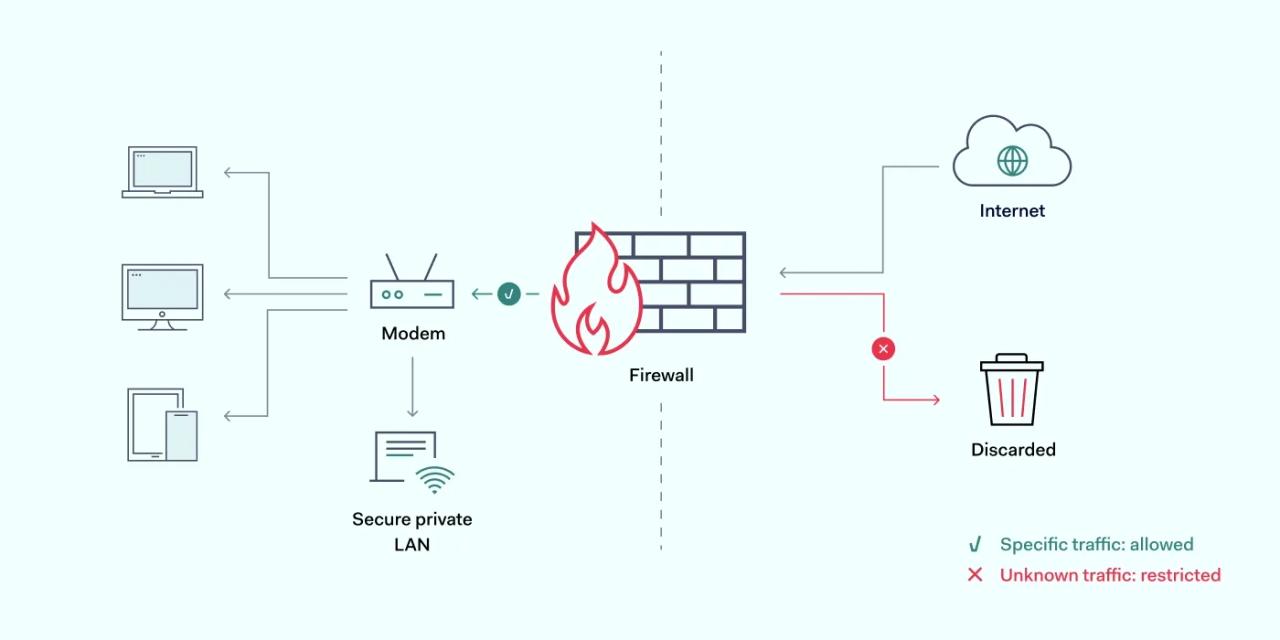
Network security is a critical priority for all modern organizations. And controlling access is one of the most important cybersecurity challenges. This makes firewalls an essential element of any security strategy.
Packet filtering firewalls are one of the most common firewall types. In this article, we will explore how packet filtering works. And we will learn about how packet filtering firewall technology compares to alternative security options.
Definition of packet filtering
Packet filtering is a type of firewall technology. Firewalls are appliances that protect networks against external intrusion by screening incoming data and admitting or excluding traffic. Packet filtering firewalls achieve this goal by applying security rules to data packets. If packets pass these tests, they can enter the network. If not, the data is rejected.
How packet filtering works
Packet filters perform firewall functions by assessing packet data. All data arriving at the network edge is divided into packets. These data containers are small enough to transmit efficiently and are also fault tolerant. If the transmission fails, the sender can retransmit a packet until the process succeeds.
Packets have two main components: the packet header and the payload.
- Headers. The packet header "wraps" the packet and contains information about its origin, identity, and destination. It acts like a taxi, transporting data on its journey.
- Payloads. The payload is the data being transmitted. Packet filters generally cannot analyze the payload. Instead, they rely on information found on the packet exterior.
Packet filtering firewall appliances decide whether individual packets should enter the network. To achieve this, they check information on the packet header. This could include:
- The Internet Protocol (IP addresses) of packets.
- The source and destination addresses of inbound and outbound packets.
- Data transfer protocols used in the transmission. This could include User Datagram Protocol (UDP), Transmission Control Protocol (TCP,) or ICMP.
- Header flags attached to the packet
- The NIC interface that the packet is transiting through
The firewall compares this information to predefined rule sets and access control lists (ACLs). If the packet meets the conditions for entry, it can continue its journey. If not, the firewall denies entry.
Key features of packet filtering firewalls
- Apply rule sets to data entering networks.
- Act on individual data packets.
- Use external packet data including IP addresses, source and origin ports, and data transfer protocols.
- Do not carry out deep packet inspection.
- Generally stateless. Packet filters assess packets on their own. They do not remember data or learn from previous actions.
What is packet filtering used for?
Packet filtering firewalls are primarily network security tools. They protect applications, devices, and data from external attacks. Filters can detect unauthorized packet transmissions and deny entry. This often excludes malware payloads and reduces the risk of data breaches.
Packet filters operate at a relatively superficial level compared to next-generation or stateful firewalls. This can have advantages. For example, PFFs are usually faster and impose a lower data processing burden. These benefits can be useful in contexts where network security is not a priority.
Packet filters can also apply IP allow lists to screen incoming traffic. Network managers can add authenticated user IP addresses to the ACL. When legitimate users attempt to access the network, they are recognized. Their data flows are not impeded. However, unrecognized IP addresses will not gain access. This ensures that only authorized users can access critical data.
Types of packet filtering firewall
There is more than one way to filter traffic by packet analysis. Types of packet filtering include:
Static packet filtering firewalls
Static packet filters are so-called because users set firewall rules and these rules remain the same until they are changed. Any rule changes to a static packet filter must be carried out by the network administrator. Network connections also stay closed or open until administrators change their settings.
Typically, users can configure a static packet filtering firewall in many different ways. They can manage ports and set specific rules, and users can apply access control lists to exclude unverified devices from their internal network.
Static packet filters are simple to install and easy to use. But they have some limitations. Users are responsible for updating settings and configuring firewalls properly. There are few or no automated elements. This makes static filters useful in small-scale settings. But they may be impractical for larger organizations.
Dynamic packet filtering firewalls
Dynamic packet filtering is named because dynamic firewalls adjust the way they operate according to pre-set parameters.
In these types of packet filtering initial configurations can adapt to changing security environments. For instance, managers can configure a dynamic packet filter to open or close ports for specified periods.
With dynamic packet filtering, users can intensify or relax security controls as they require. And they can automate these settings to reduce the administrative workload.
Dynamic packet filters should not be confused with next-generation firewalls. They do not generally include machine learning and other advanced security features. As with static filters, dynamic packet filters can also be stateless or stateful. Knowing the difference is extremely important.
Stateless packet filtering firewalls
Stateless packet filters analyze packets individually. They do not store or leverage information about the state of packets when deciding whether to admit traffic. Instead, they apply predefined rules to establish whether data packets are safe.
In the context of packet filters, stateless firewalls apply access control lists (ACLs). This includes information about the IP address of packets, as well as source and destination ports. Stateless filters only leverage this limited information when processing access requests. They do not store information after handling each individual connection.
Stateful packet filters
Stateful packet filters are more advanced than stateless alternatives. In this variety of packet filter, the firewall assesses the state of packets before deciding whether to allow entry.
Stateful firewalls continually assess network traffic. They store information about every access request in state tables for the major data transfer protocols (TCP and UDP). These tables allow the firewall to track access requests over time. The firewall can then build detailed profiles of users to detect potentially malicious network data.
Generally, stateful filters deliver more robust security. They are better at spotting IP address spoofing and other forms of illicit network entry to the internal network. But due to their data-gathering features, stateful packet filters may also be more vulnerable to traffic attacks such as distributed denial-of-service (DDoS) attacks.
Limitations of packet filtering firewalls
Packet filtering is an aging technology. The first packet filtering firewall appliances appeared in the 1980s, and many innovations have arrived since then. As a result, many security experts see packet filtering as largely obsolete. This is something to keep in mind when designing any firewall architecture.
Specific limitations of packet filtering firewall systems include:
1. Poor security
Packet filtering firewalls use superficial information to make decisions about network access. They use IP addresses, protocol data, and port numbers. But they do not take into account contextual information about user devices or application usage.
Additionally, packet filters cannot penetrate beyond the packet exterior. They can only inspect the outside of network data. If payloads contain malicious code, the firewall will allow this code to enter the network. Hackers can simply use address spoofing to fool the firewall into believing traffic is legitimate.
Stateless packet filters bring extra security risks. In stateless varieties, every access request is processed separately. Hackers have many opportunities to mount attacks. And when they do, the packet filtering firewall does not store any information about their activities.
Companies must also meet strict data protection standards such as PCI-DSS or HIPAA. In these situations, solutions like web application firewalls are a more precise solution. Firewalls installed on the web server protect web-facing assets and are much better at filtering HTTP traffic.
2. Primitive data logging
A packet filtering firewall usually logs very little information about network traffic. This can lead to serious compliance issues. Data regulations are becoming increasingly strict. Regulators expect to see evidence of firewall integrity. This is not always available with packet filtering technology.
The absence of logging also has implications for day-to-day network security. IT teams miss out on valuable data regarding access requests. They may fail to spot patterns of suspicious activity. And as a result, security vulnerabilities may go unaddressed.
3. Lack of flexibility
Packet filters provide users with very little flexibility about how they manage network access. Packet filters are designed to track small amounts of information. They may filter IP addresses or port numbers. But this is a very limited set of criteria in the context of modern access management.
Ideally, security teams should have maximum visibility of how users connect to network assets. Advanced firewalls deliver insights about the location of users, the devices they use, and even how they use those devices. They can also automatically adapt to reflect developing security concerns.
By contrast, packet filtering firewalls are rigid and primitive. Users have to manually set up rule lists or control lists for their packet filtering firewall. Threat management is rarely automated and packet inspection is generally absent.
4. Poor suitability for larger organizations
Packet filters are lightweight and simple to use – when employed on a small scale. But a packet filtering firewall can quickly become cumbersome when applied across larger organizations.
Security teams must manually configure rule sets for their packet filtering firewall. These sets may vary between departments or branch locations. Updating rules and firewall settings are also challenging without automated processes. The result is a high workload and increased scope for human error.
5. Excessive trust
Many organizations are seeking to implement Zero Trust Network Access (ZTNA). Zero Trust applies the principle "trust no one, verify everything". However, this is impossible with standard packet filtering systems.
A packet filtering firewall will not inspect payloads. This makes spoofing easier. Malicious actors can gain access while disguised as trusted users.
Packet filters also do not log historical data. They do not keep records that prove that users are trusted or not. Instead, a packet filtering firewall will rely on access control lists. These rule lists may be out of date or compromised by spoofing attacks.
Packet filtering firewall vs proxy
Proxy servers are an alternative to appliance-based packet filtering firewall systems. Both protect the network edge by filtering traffic. But they do so in different ways.
A proxy server sits between external devices and local networks, just like packet filtering firewalls. Unlike packet filters, proxies anonymize traffic passing through the firewall. They hide the IP address of users, making network traffic much harder to inspect from the outside.
Additionally, proxy servers can store cache data. Proxies record data about previously accessed websites. This makes accessing those sites faster in the future. It also keeps a record of access requests that the firewall can use when making decisions.
Some proxies perform the role of an application gateway. In this role, they screen entry to specific applications. The proxy can exclude certain types of traffic or requests from services like torrenting clients. And they can also screen outgoing network data to prevent access to prohibited websites.
However, proxies do not always possess packet inspection or filtering capabilities. Users can achieve enhanced security by installing firewalls on proxy servers. That way, they can combine the IP anonymization of proxies with the filtering provided by a packet filtering firewall.
Packet filtering vs stateful firewall
Packet filtering firewall appliance are almost always defined as "stateless." This means the firewall only assesses information on the surface of data packets. Information about the state of the packet is not included.
State refers to the relationship between protocols, servers, and data packets. When data passes to and from local networks, state information tracks the process. Stateful firewalls collect information about data origins and destinations. They track protocol usage, and ports. Some stateful firewalls may also gather payload information from inside network packets.
Stateful firewalls also use state tables to store historical information about data transfers. This creates a record of each access request and links requests from the same user. Firewalls use this data to make better-informed decisions about allowing or denying access.
A packet filtering firewall does not capture this amount of information. Because of this, packet filters are usually less able to detect malicious data packets. But security comes with costs. Packet filtering is generally faster and makes fewer demands on network resources.
Conclusion: understand the role and limits of packet filtering firewalls
Ensuring tight network security is vital. Choosing the right firewall can make a critical difference when defending against data breaches and malware infection.
Packet filters are one option when putting in place firewall systems. A packet filtering firewall inspects packet data and applies security rules. This allows filters to deny access to malicious traffic. But packet filtering has limitations. It cannot look inside packets. And it rarely includes stateful monitoring.
These limitations make packet filters less popular than in the past. A packet filtering firewall may still be useful when speed is essential and security is not a priority. But other firewalls will often be preferable when designing robust cybersecurity environments.