A next-generation firewall (NGFW) became a key part of modern cybersecurity setups. More companies now use NGFW tools to block threats, manage traffic, and improve visibility.
Unlike traditional firewalls, NGFWs dig deeper into network data. They spot risky behavior, stop complex attacks, and help keep systems secure without slowing them down.
What is a next-generation firewall?
A next-generation firewall (NGFW) is a cybersecurity tool that monitors network traffic to detect and block threats. It represents the 3rd generation of firewall technology, going beyond basic firewall tasks by deeply inspecting data packets and spotting malicious behavior. NGFWs use advanced features like intrusion prevention, application awareness, and threat intelligence. This makes them highly effective at protecting networks from complex cyber-attacks.
What does a NGFW do?
While NGFWs expand on the traditional firewall capabilities, they perform the same core firewall functionalities. This includes inspecting individual data packets, analyzing whether they align with the set security policies as well as identify encrypted VPN traffic.
The difference is that traditional firewall capabilities are limited at those core functions, NGFW builds on top of them to create a much more sophisticated suite. Based on Gartner, on top of basic firewall functions, a third-generation firewall should support server processing nodes running applications like firewall, deep packet inspection (DPI), and data interception without disrupting the network. In addition, it should also act as a platform for network traffic inspections and include these features:
- Integrated network intrusion prevention. It should function as an active monitoring solution to scan for malicious content.
- Application awareness with full-stack visibility. It should secure networks against application-level security threats independently fused port, protocol, or service.
- External intelligence sources. NGFW should rely on external sources to improve blocking decisions or optimize operations.
- Upgrade path support. NGFW should have room for expansion by providing customization options to add more features.
Additional features are possible because, unlike traditional firewalls, NGFWs can inspect network traffic at several OSI layers. Frequently hackers use exploits in one of these layers and work their way around to the application layer. NGFWs stop these attempts in their tracks by offering more well-rounded packages.
What are next-generation firewall types?
A wide variety of NGFW types are designed for different environments and use cases. Each of them might have different methods of deployment, i.e., hosted in a data center or locally, and better suited to tackle specific attack types.
No two next-gen firewall providers are identical, you may encounter varieties of them in three main types.
Software-based NGFW
Software next-generation firewalls are running like any other application you might have installed on your endpoint. This can be a great addition to your infrastructure as this method isn’t hogging your physical resources. The main downside is that this type needs to be installed for each network device.
Hardware-based NGFW
Hardware next-generation firewalls exist as physical devices that analyze all incoming traffic. The main benefit is that every user connected to the internal networks gets immediately covered by a firewall. However, each employee should be connected to the same network for this to work.
Cloud-based NGFW
Cloud next-generation firewall is very similar to a software firewall, with the main difference being that it’s deployed on the off-premise data center. While it doesn’t eat up your endpoint resources, this firewall type requires an uninterrupted network connection. The cloud could be managed by the company or the service provider’s responsibility.
History of third-generation firewalls
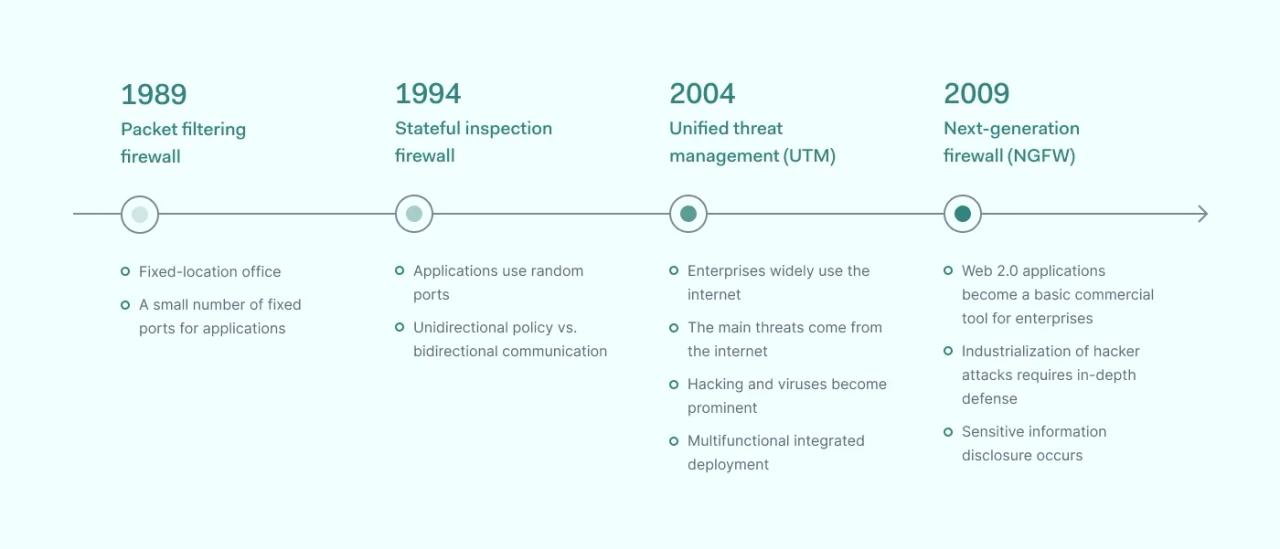
Majority of malware has always been targeted at exploiting applications. In cases when legacy security tools can’t keep up, on average, every application has at least ten vulnerabilities. It’s a no-brainer to target this area as it has the highest success rate, and hackers have been doing that for a long time.
In the days when most applications had very fixed port-protocol relationships, i.e., the popular game Doom used port 666 for TCP/UDP, packet filtering capabilities were much simpler. Administrators could simply block the port used by a given application, which effectively made the application unusable. Nowadays, most web applications use port 80 TCP, so shutting it down would also mean shutting down the internet access for the user. More granular traffic controls were needed.
This need spearheaded the development identity-based security approach. Instead of binding IP addresses, user identity is at the forefront, which also alters its permissions within the network.
NGFW offers much deeper inspection capabilities that are detached from conventional associations. As threats could be hidden within genuine-looking network traffic, it’s important to analyze the flow with scalpel precision. Using various integrated features, NGFWs allows the creation of very granular rule sets to control what’s coming in and out of the network.
Nowadays large businesses that handle sensitive data use NGFW solutions as it’s one of the best methods to secure the network. In other cases enterprise firewall capabilities are integrated into other systems security architecture like unified threat management.
What benefits does the next-gen firewall bring?
NGFWs can apply application-specific rules, detecting and blocking a wide range of anomalous behavior across multiple network layers. This means that hacking attempts by exploiting nonstandard ports are stopped in their tracks, a much more advanced security method than traditional firewalls can prevent.
In addition, NGFWs are much more living systems than their traditional counterparts. Taking context into consideration when making a decision allows them to block complex hacking attempts. A built-in functionality to constantly receive updates from external threat intelligence networks helps to catch up with emerging attack types and prevent them before they wreak havoc on your internal network perimeter.
Some NGFWs successfully integrate machine learning and various automations to be more autonomous solutions. That way, security policies can be updated according to the threat landscape without input from human network administrators. Similarly, the maintenance of the whole operation is made easier as all alerts and notifications are displayed through a single report system. It’s truly the next chapter when compared to stateful firewall security.
Next-generation firewalls vs. web application firewalls
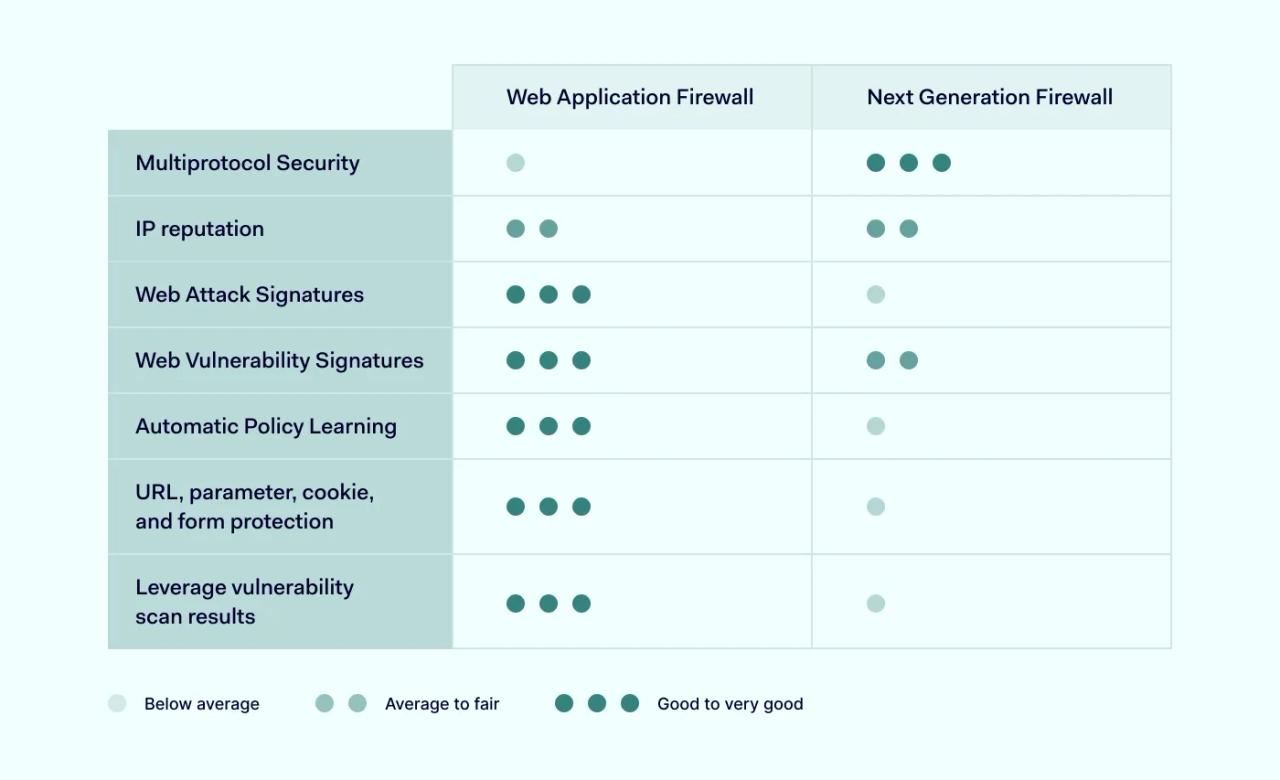
Web application firewalls, or WAFs, are tools to secure web applications against internet threats. It protects the server from malicious exposure by routing connections through WAF before reaching the hosted application’s server.
WAFs and NGFWs are similar in denying unapproved connections directed to protected resources. The main difference is their scope: WAFs are deployed to protect specific web applications, while NGFWs protect the entire network.
NGFWs protection isn’t limited to applications, as an organization could be attacked using various methods. WAFs can take care only of web-based attack types like distributed denial-of-service (DDoS) or SQL injection.
It wouldn’t be unfair to say that both solutions can provide similar functionalities. WAFs and NGFWs both base their blocking decisions on security policy rules. In most cases, WAFs and NGFWs are also deployed remotely as Software-as-a-Service offerings.
The key difference between those solutions is that NGFW oversees a much larger network traffic scope, allowing for a deeper contextual analysis. WAFs are much more straightforward, acting as a simpler barrier.
Next-generation firewall vs. traditional firewall
NGFWs and traditional firewalls perform identical functions at different scopes and depths. The key goal always remains the same, i.e., protecting an organization’s network.
The difference, however, is that a traditional firewall is quite limited in its threat detection. The only threats that traditional firewalls catch are via port and protocol inspection. NGFWs, however, use deep-packet filtering going beyond protocol or port inspections. When combined with intrusion prevention and data feeds from threat intelligence providers, it’s a much more potent solution.
Deep-packet inspection firewalls go beyond traditional firewall functionalities in routed as well as transparent modes. This means that filtering capabilities can be applied in modes when the firewall acts as a router and in cases when it’s inserted between legacy systems.
What is the difference between UTM and NGFW?
Unified threat management or UTM refers to a cybersecurity solution providing multiple security functions within a single appliance. That way, UTM encompasses firewalls, spam filters, antivirus, intrusion detection, and prevention systems. A wide range of solutions allows UTMs to provide comprehensive protection of modern threats.
In this sense, UTMs and NGFWs provide network protection with different scopes and focuses. UTMs incorporate NGFWs as a single component of the much bigger system. Therefore, their functionalities overlap in areas because, essentially, they are performing the same functions.
The most significant difference is that UTMs provide a much broader protection mechanism. UTMs care for endpoint, web, email, and webserver protection. Due to this versatility, UTMs are perfectly suited to small to medium businesses, while NGFWs are better for larger corporations due to the volume of online-exchange traffic.
NGFWs have become essential for effective cybersecurity today. They inspect traffic deeply, stopping threats that older firewalls might miss. With features like intrusion prevention and application awareness, NGFWs help keep networks safe from advanced attacks. For organizations seeking stronger protection, adopting a next-generation firewall is a smart choice.