Discretionary Access Control is a decentralized access control policy that allows subjects to control access to objects. You can find DAC in smartphone apps, Google Docs, and Operating Systems worldwide.
In DAC systems, subjects can share information with other users. They can grant privileges to others. They can change object attributes, or choose which attributes are associated with newly created objects. And they can set different forms of access control without central authorization.
These capabilities are generally not allowed with mandatory access control (MAC). DAC provides freedom for object owners to set their access policies. MAC sets access policies centrally via tools like clearance levels.
But is DAC a secure access control method for your organization? This article will explain:
- How discretionary access control works
- The benefits of discretionary access controls
- Challenges associated with discretionary access systems
- Examples of DAC
- The differences between DAC and MAC
How does discretionary access control work?
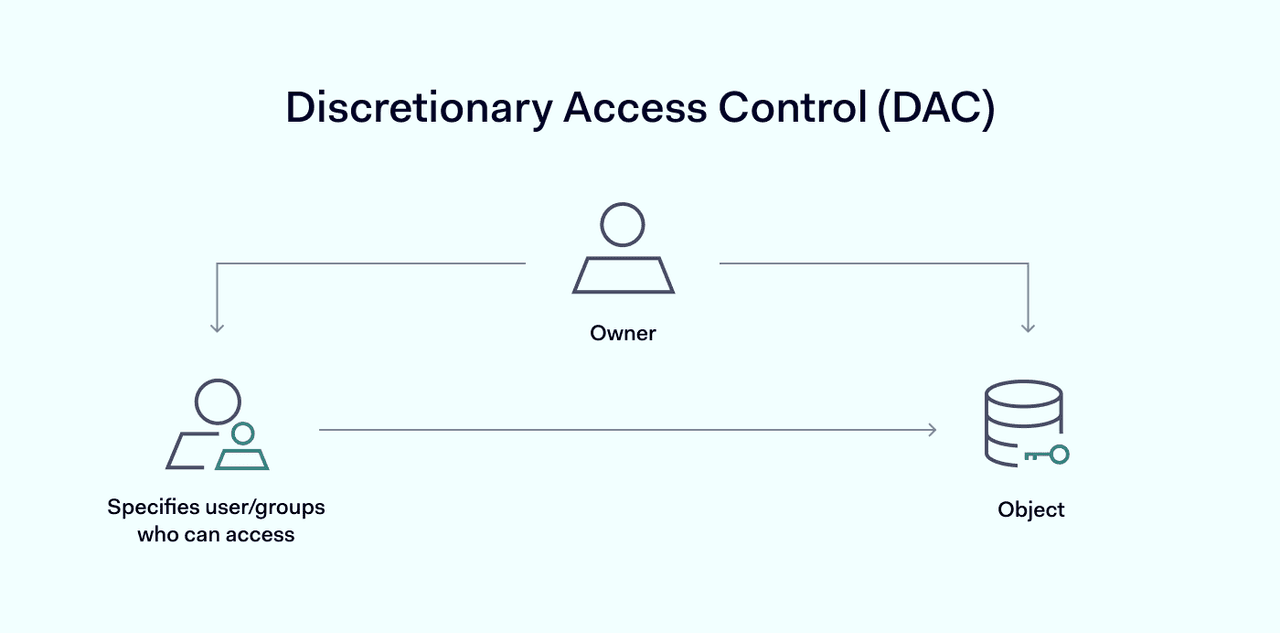
Discretionary access control relies on two core concepts to govern access to network resources.
- Subjects: users or user groups seeking access to resources protected by DAC.
- Object: a system resource such as an application, or a piece of data stored on the network.
DAC relies on subject identification to grant access to objects. Users must supply authentication information that identifies their status before the system allows access. The access control system then decides whether the subject has the rights required to access a specific object.
There are two main types of DAC systems:
- Access control lists (ACLs): an access control list is a document that contains information about authorized users. This allows administrators to set rule-based access control systems for each object. ACLs include user identities and the privileges that each user possesses. They can also be linked to user groups as part of role-based access control systems.
- Capability systems: these decentralized systems do not rely on ACLs. Instead, access is related to the identity of the object being accessed. For example, cryptocurrency owners can access their currency if they possess a private key. Imgur users can edit objects if they have the hidden URL for each image.
Both types are discretionary. Object owners can change ACLs to limit or allow access and expand user privileges. For example, some groups may have writing privileges. Others may only be able to read entries in a database.
Imgur users can allow limited access to files via public links. Cryptocurrencies allow transactions via public keys if the owner agrees.
Benefits of DAC
There are many reasons to choose Discretionary Access Control solutions when restricting access. The main benefits of DAC systems include:
- Flexibility: with DAC users can set permissions for individual objects. Object owners can divide users into groups, creating fine-grained controls over access settings. This is not possible with mandatory access control systems.
- Speed and efficiency: discretionary controls let information flow freely through networks. Users can grant object access with the click of a button. There is no need to create complex user profiles or clearance levels for new hires.
- Low administrative burdens: decentralization means that object owners manage access. Administrators do not need to manage access control profiles for every user, to every resource. Instead, users choose how to access information when they need it.
- Simple policy management: all admins need to do is assign object access privileges to users. With the right ACL management systems, discretionary access technology is extremely simple to use.
These benefits make a discretionary security system appealing when speed and simplicity are priorities. DAC is often a good fit for smaller organizations or companies that deal with little sensitive data.
Challenges of DAC
Despite its benefits, discretionary access control is not without its problems. Here are the main issues to keep in mind.
- Security: most importantly, DAC is recognized as less secure than mandatory access control. Discretionary access can allow attackers to implant malware on target access points. Privilege creep can grant excessive access to users. Users might grant access too broadly. Or they may not understand what they are agreeing to.
- Lack of visibility: decentralization can lead to confusion and poor administrative visibility. Security teams need to know who is accessing sensitive resources. Discretionary controls are hard to monitor and control, leading to security gaps and compliance issues.
- Maintenance: object owners are responsible for maintaining up-to-date and relevant ACLs. As ACLs grow and networks expand, they may become less effective. For instance, an access control list could include access rights for ex-employees. Or it might fail to change with user roles.
- Poor data protection: security best practices suggest using centralized controls to guard the most sensitive data. Discretionary systems cannot provide the assurance organizations need to protect health or financial data.
Discretionary access control examples
DAC is a common feature of everyday life and private network management. Most of us encounter discretionary access systems without even realizing it. Important use cases include:
Social media
Facebook groups are managed via a form of discretionary access control. Group owners can determine who has access to content hosted on each group. Group members generally have a restricted ability to transfer content and share it outside the Facebook platform.
Smartphone apps
When you allow apps to access your smartphone, you are using discretionary access systems. The smartphone owner determines which applications can access functions like the contacts directory or GPS. Users decide when to allow potentially insecure operations.
File system management
Most operating system technologies use a form of DAC to manage files. For example, UNIX file mode allows object owners to set read, view, and write privileges. The same applies to Windows or DOS. Discretionary file controls govern whether users can transfer or edit files. They can hide file attributes such as size or path. And they can deny access privileges without proper authentication.
Collaboration platforms
Productivity tools like Dropbox or Google Docs use DAC to set user access to files. For example, the owner of a Google Document could create an ACL including relevant employees. Some members of the group are given write functions, while others may only be able to view the file. And the owner retains the power to delete the document or close the project.
Crypto wallets
DAC allows access to crypto wallets, providing the user has both private and public keys. But users can also transfer cryptocurrency via the public key. This allows owners to guard their assets and make transactions securely.
Scripts
Scripts are executable files associated with applications like MS Excel. Owners send them to users to carry out specific tasks that are too complex to carry out otherwise. This has some security weaknesses. Insecure scripts can access system files and lead to data breaches. But most modern systems provide discretionary controls and information about the script's source.
Discretionary access control vs. mandatory access control
When constructing access systems, users often face a choice between mandatory and discretionary access control. This table outlines the key differences between the two technologies, which have very different use cases.
| MAC | DAC |
|---|---|---|
Access control enforced by | Administrators and operating system | Administrators and users |
Form of access control policy | Confidentiality levels and clearances | Access-control list with user identities |
Maintenance | Hard | Easy |
Implementation cost | High | Low |
Granularity | Admins adjust clearance manually | Users can assign access rights to any other user |
Security level | High | Low |
Trusted users | Only administrators | All users |
Mandatory controls are used where security and confidentiality are the main concerns. Government organizations use MAC to protect classified data and military secrets. Mandatory access systems let managers create clearance tiers. Users can only access classified data if they have centrally-approved clearance.
Discretionary controls are used where flexibility and customization are important. For instance, smartphone users need the ability to grant some apps the ability to see their contacts directory. But they may want to deny this ability to other services.
Businesses can use discretionary controls to manage projects at a granular level. Managers can assign different access levels to databases, image catalogs, code, and individual apps.
