In today's world, keeping access to important data safe is key. Building a system called Identity and Access Management (IAM) helps businesses do just that. This article will cover the basics, the challenges, and actions to ensure only the right people can get to the data they need.
What is IAM architecture?
IAM architecture is the strategic design of your identity and access management framework. It outlines how policies, technologies, and processes work together. This blueprint ensures users access resources securely and appropriately.
A robust IAM architecture acts as the foundation for your organization's security posture. It systematically connects the right individuals to the correct digital resources. This involves defining how an IAM system will manage identities and enforce access controls. A well-planned architecture aligns your identity management strategy with overall business objectives, ensuring efficient and secure operations.
Key takeaways
Here are the critical points about crafting IAM architecture that we discuss in depth below:
- Identity and Access Management (IAM) gives access to resources and prevents unauthorized connections. These systems can only work with a proper architecture.
- Common challenges you may encounter are poor data integration, legacy systems compatibility, shifting to hybrid or remote work, focusing either on the internal or external IAM architecture side, and lack of expertise and training.
- Your IAM strategy should cover every asset and user role.
- Consider efficiency. Avoid duplicate and unnecessary features, and automate the processes when possible.
- To choose the right IAM architecture, build an app portfolio, visualize connections, understand identity federation, and assess automation and authentication methods.
- Start by understanding your application portfolio and creating a logical user directory. Then, separate the company and customer IAM infrastructure. Finally, assign role-based access controls (RBAC) for employees and add MFA controls for local and remote users.
Why does your business need IAM?
Modern businesses need a well-thought-out IAM architecture to protect confidential data. Companies routinely handle financial and personal customer information. Network assets store vast amounts of operational data. Vulnerable workloads require constant protection from an effective IAM system.
IAM guards critical assets with strong access controls and privilege management. Authentication systems demand several factors before allowing entry. Authorization tools assign strict permissions to every user.
As a result, IAM strengthens the perimeter and limits internal freedom if attackers gain access. This also includes robust privileged access management for sensitive accounts.
Companies should take an architectural approach to identity management. IAM architecture involves planning access systems to suit business needs. IAM must cover all user types, applications, data resources, and network infrastructure. Careful design ensures that Identity and Access Management covers every critical area.
Potential challenges faced during IAM deployment
Implementing IAM can be complex, and knowing the potential obstacles is important. Common challenges encountered during the IAM architecture process include:
- Diversity and poor data integration: Security teams may encounter hybrid cloud and on-premises infrastructure. Application portfolios may also be highly diverse. Planners must collect all relevant data about user communities, applications, and platforms.
- Compatibility with legacy solutions: Architects must avoid conflicts with existing systems when adding new access control rules. This requires significant planning and investment in pre-implementation preparation.
- Changing work patterns: Companies may shift to remote work or hybrid work arrangements. Device communities using SSO portals can become diverse and complex to manage.
- Organizational confusion: Implementing IAM architecture is a major investment and a deep process of technical change. IT teams may understand the scope of the changes required, but communicate the project goals poorly to business managers. Stakeholders must be on the same page and aware of the project goals.
- Too inward-looking projects: Corporate IAM architecture has two sides: the internal and the external. The external aspect deals with third parties and customer accounts. The internal one is concerned with staff and network control. Planners may neglect one at the expense of the other, resulting in an imbalanced IAM architecture.
- Poor knowledge and training: Identity and Access Management is a dynamic process. It requires constant maintenance and IT expertise. Companies may need to pay more attention to training and awareness, creating a skills deficit. Over time, access controls can become less effective. Workforces also tend to revert to insecure habits, making the IAM framework less efficient.
What to consider before implementing IAM architecture
Planning IAM architecture is critically important. Organizations must create a strategy that maps out core goals and challenges. This plan will guide project teams. It ensures that the finished Identity and Access Management solution is:
- Comprehensive. Covering every identity provider, connected asset, and user role within the organization.
- Consistent. Applying standard forms of authentication and authorization across the whole enterprise. Using Single Sign-on (SSO) to bring all access requests together and ensure consistent policy enforcement.
- Efficient. Avoiding duplication and unnecessary features. Designed to make life simple for users and administrators, leveraging automation where possible.
Planners must consider a range of questions when designing IAM architecture. Core issues to consider include:
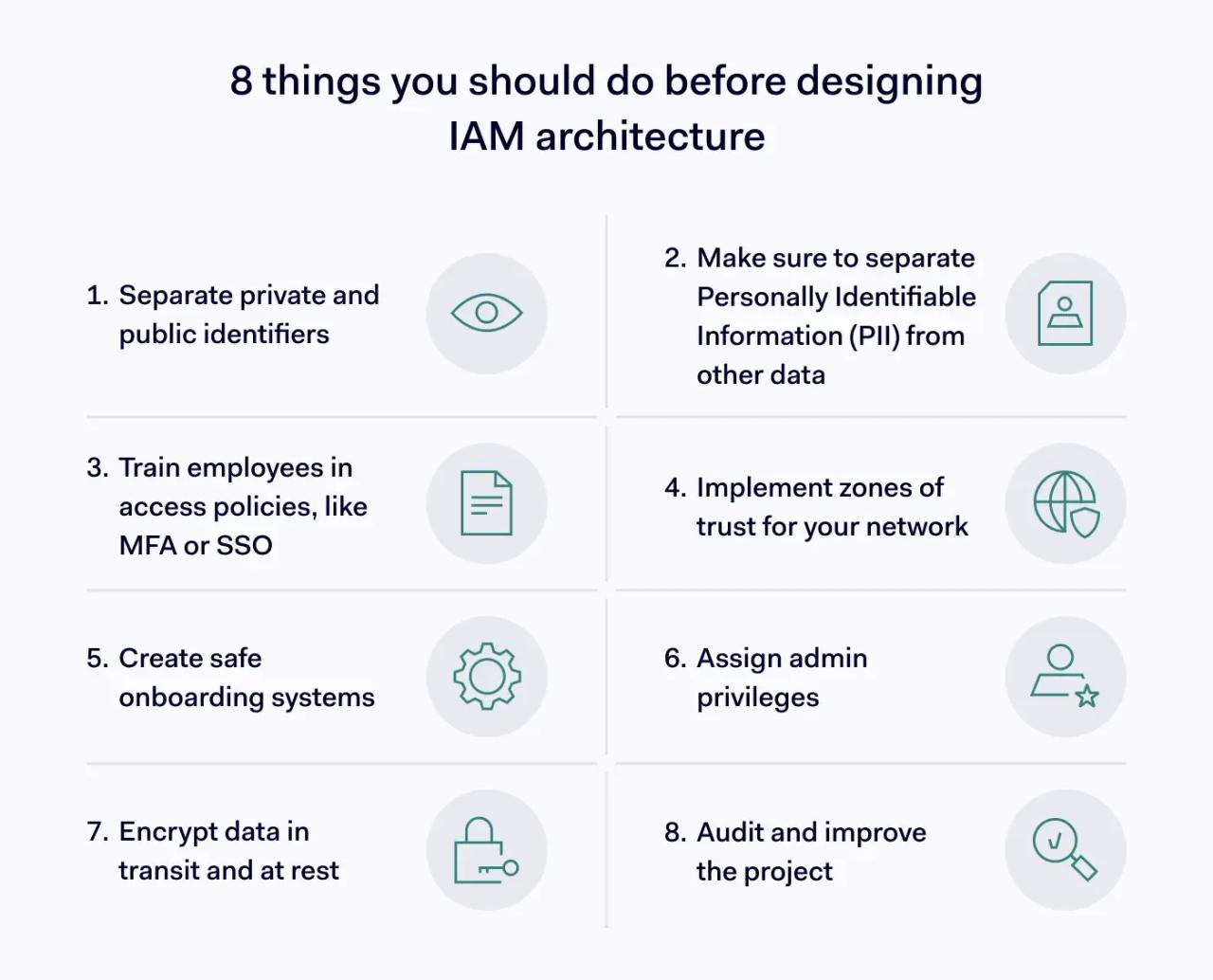
1. Separating private and public identifiers
Public identifiers are less sensitive personal information. They may appear on public-facing profiles or directories. Private identifiers are used in authorization and MFA processes. These require additional security protection because they verify identity. Separating these two identity data types is crucial for security and privacy compliance.
2. Defining and protecting Personally Identifiable Information (PII)
Personally Identifiable Information (PII) is highly confidential identity data. It includes details like social security numbers or financial records. PII requires exceptional protection for compliance reasons and to prevent identity theft. It must be clearly defined and separated from other corporate data within your IAM system.
3. Training employees in access policies
Controls like multi-factor authentication (MFA) and SSO must become everyday practices. Employees must know how to use identity systems correctly. They also need to understand how to manage and change their identification data securely. Users must also know and follow corporate password management policies to maintain security.
4. Implementing zones of trust
Network segmentation allows planners to create secure zones. These zones group resources according to their risk and regulatory value. You can then apply specific controls to minimize the risk of external attack. This helps contain potential breaches within smaller, manageable areas of the network.
5. Creating safe onboarding systems
IAM architecture may feature self-onboarding for customers. This is distinct from employee onboarding processes. These are two different ways to create digital identities. They must be separate systems. This ensures that low-privilege individuals, like customers, cannot access internal network resources or sensitive company data.
6. Assigning admin privileges
Privileged accounts grant access to critical infrastructure components. This includes servers, firewalls, and sensitive data stores. However, every over-privileged user identity is a critical security risk. Planners need to minimize these admin-level accounts. Effective privileged access management also involves developing strong security controls around high-value assets.
7. Encrypting data
IAM best practices advise security teams to encrypt data. This applies to data in transit and at rest. Planners must ensure all PII is encrypted effectively. It's also vital that encryption keys are securely stored and managed. This prevents unauthorized access even if the data is compromised.
8. Auditing and improving the project
IAM architecture projects will inevitably face obstacles or new requirements. Make auditing a regular component of your risk management strategy. Audits can identify areas of weakness in your IAM system. They may also discover new elements to add to your access management solutions, ensuring ongoing improvement.
Choosing the right IAM architecture for your business
Selecting the right IAM tools is an essential part of access management. It requires understanding what needs to be protected, who uses network resources, and how users connect to applications and data. This is key for effective identity management.
- Build an application portfolio for the organization. This is a list of applications and services users need to access. All must be brought under the access control umbrella, including third-party service providers.
- Create a map of application connections. Visualize how users interact with cloud environments. This includes SaaS apps, CRM solutions, and messaging services. Connect cloud-based and locally hosted assets.
- How do apps and services link together? Network architecture may feature multiple identity management systems. These can include SAML, HTML, or OpenID Connect. Gain a solid understanding of how identity federation works on all connected resources.
- Who is the IAM solution for? Are customer IDs part of the challenge? Or is the solution purely designed for managing identity profiles on an internal network? Clearly define the scope for your identity management efforts.
- Assess the potential for automation. Ideally, users will have maximum freedom to manage their access settings. This reduces the workload on admins. Automation can also make onboarding and offboarding more efficient. This reduces the risk posed by dormant accounts.
- What kind of authentication works best? Identity and Access Management requires enhanced authentication, usually via MFA. However, there are various forms of multifactor authentication. Choose a method that suits your workforce and security needs, balancing usability and protection.
After answering these questions, planners should have a realistic picture of the project’s scope and goals. They can commission a technical solution to create an effective IAM environment with that information.
How to create an IAM architecture?
How can you handle the challenge of designing IAM architecture? Following these simple steps will provide a solid foundation for a successful implementation.

1. Understand your application portfolio
First, list all applications and services that need to be secured by your IAM. Then, map the connections between these resources. It's also important to identify the standards used to manage identities on each service. For example, various apps might use OpenID Connect or SAML to federate identities across different platforms.
2. Create a logical user directory
Companies often use many user directories across on-premises and Cloud environments. Your goal is to bring employee directories together, ideally under a single sign-on (SSO) system. This consolidation will make policy enforcement consistent across the organization. It also enhances visibility into user access and identity data.
3. Separate customer and corporate IAM infrastructure
Customer portals require specific IAM solutions tailored to external users. Therefore, you must separate employee and customer access methods. Provide sufficient flexibility for customers to manage their identities. At the same time, ensure robust protection for their PII and other sensitive identity data. This distinction is vital for security.

4. Assign role-based access controls (RBAC) for employees
Use your consolidated user directory to create logical roles based on job functions. Assign sufficient privileges for workers to access the apps and data they need for their tasks. Crucially, follow the principle of least privilege. This keeps permissions to the minimum necessary, reducing potential attack surfaces and improving overall identity management.
5. Create authentication systems at the SSO level
Integrate appropriate MFA controls directly into your SSO solution. This applies to both remote and local users to ensure consistent security. You should also consider implementing MFA for customer access. This is especially important if users are providing or managing sensitive data through your portals.
Why a strategic IAM architecture matters
Taking an architecture approach is the only reliable way to create robust access controls. IAM is a complex challenge. Practices like improvisation or buying simple off-the-shelf products won’t work for comprehensive security. A well-defined IAM system is crucial.
Security teams must plan their IAM implementation carefully. This guarantees consistent policy enforcement across the board. They must include every identity and application, leaving no security vulnerabilities. This systematic approach forms the core of effective privileged access management and general user access.
Follow best practices and apply access control rules that fit your organizational needs. With the correct strategy, companies can defend data and connect users with the resources they need. With a strategic approach that includes advanced tools like NordLayer's IAM solutions, you can effectively defend your organization’s data and provide users with secure access to necessary resources.
