Identity and Access Management (IAM) is like a trusted gatekeeper. It ensures that the right users get access to the resources exactly when needed. A solid IAM setup, vital for modern businesses, minimizes the risk of data breaches and puts up a good fight against cyber attackers.
However, to function properly, IAM systems need maintenance. That's where IAM assessments come into play. This article will break down what assessments are, their importance, and the steps to implement them.
Key takeaways
- Understanding Identity and Access Management (IAM) assessments is the first step toward a robust defense and protection of your organization's data.
- IAM assessments evaluate access control and authorization processes. It identifies gaps and provides a roadmap for enhanced security.
- A well-executed IAM assessment is your strategic guide toward achieving IAM maturity: it prioritizes critical tasks, promotes best practices, and enhances data security throughout the organization.
- Cyber threats are ever-evolving, and IAM systems can become disordered over time. Regular assessments are crucial for staying ahead of potential breaches.
- Evaluating who has access, what needs protection, where users connect, when they access resources, and how IAM systems perform fortifies your organization's security
What is an IAM assessment?
An IAM assessment seeks to evaluate access control and authorization processes. The assessment considers governance, security, and identity management issues. It identifies any gaps or areas of improvement. And it provides a roadmap for better IAM practices in the future.
The core aims of an IAM assessment include:
- Clearly explaining access management best practices.
- Making IAM solutions more effective across the entire organization.
- Controlling all aspects of IAM strategy. This includes remote access, legacy systems, cloud, and on-premises assets.
- Ensuring data protection is as robust as possible.
- posture and makes you compliant.
Why does your business need an IAM assessment?
IAM assessments are necessary because data is constantly under threat. Credential theft and unauthorized access are the major sources of data breaches. Poor access management policies provide an open door for hackers.
Over time, IAM systems tend to become disordered and outdated. Attack vectors evolve every week. Hackers may compromise the credentials of privileged accounts. Network identities can change, creating new ways to access confidential data.
IAM assessment benefits
A well-executed IAM assessment delivers various critical benefits for your security posture. These benefits go beyond just improving access control and include the following:
- Managing the strategic direction to achieve IAM maturity. Assessing IAM solutions allows companies to understand how network access works and how to counter urgent risks.
- Prioritizing critical tasks. Not all assets or users have the same risk profile. A good IAM assessment establishes priority tasks to protect sensitive data.
- Spreading good IAM practices across the entire organization. Assessments generate policies that are disseminated to all stakeholders. This drives security improvements in all areas.
- Assessments detect security weaknesses and areas to address. Vulnerabilities can appear at any time. Only regular IAM assessment processes can detect poorly secured entry points or over-privileged users.
- Better security for data. Access control is the first step in guarding confidential data.
- Change management. IAM can be used to grant permissions to change managers, who, in turn, make sure that only legit IT infrastructure changes can take place.
- Compliance benefits also flow from a solid IAM assessment. Assessments improve security controls and generate evidence to prove compliance.
IAM assessment phases
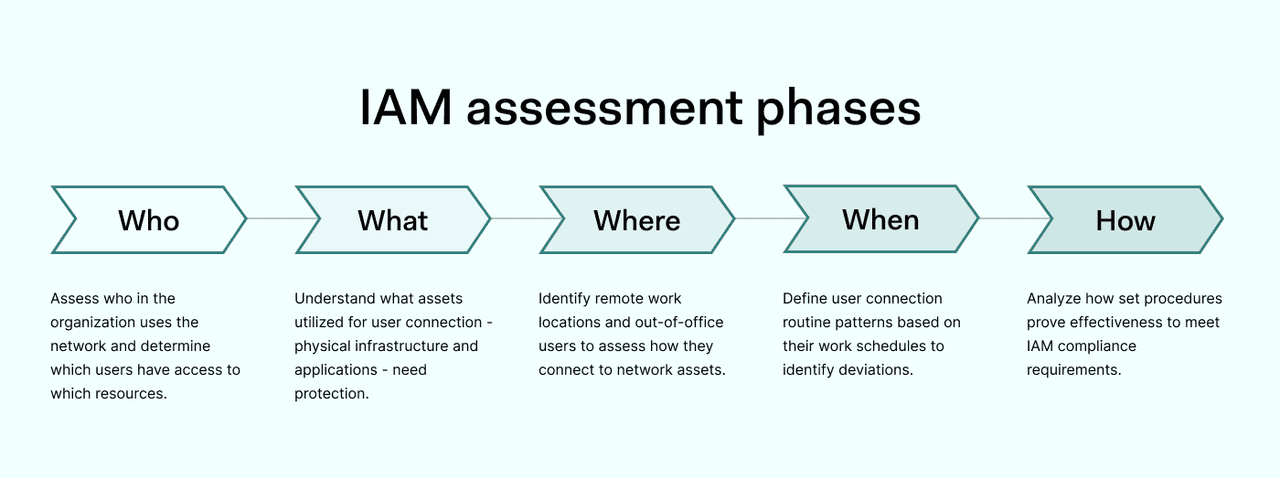
The IAM assessment process can be divided into five separate areas: who, what, when, where, and how. Let’s quickly explore how the five sections work.
IAM assessment: who
Assessors must determine which users have access to which resources. Knowing who is using the network is the first stage in understanding how to secure data and applications. This task is not simple and requires careful analysis of the organization’s network environment.
The term “user” includes employees (with both regular and privileged access). But it can also encompass IoT devices, service accounts, third-party partners, applications, and even clients. Every user has their own profile. This details the resources they require and the privileges needed to access them.
IAM assessment: what
The second part of assessing IAM solutions is understanding what assets need protection. What physical infrastructure or applications are users connecting to?
Document what these resources are, but also how they are used. This allows assessors to discover patterns of use. They can also map assets to uncover security gaps – such as over-privileged accounts with excessive access to private client data.
The “what” phase also includes current IAM tools and other elements of your security posture. Assessment teams must establish whether legacy systems deliver robust security and how they can be improved.
Time also needs to feature in this section of the assessment. Will the mix of applications change in the future, and will expansion create new access control risks?
IAM assessment: where
This section of the assessment covers how users connect to network assets. This is important because traditional on-premises networking rarely applies in the modern economy. Employees routinely connect remotely from home or public access points. Remote connections to cloud portals may also bypass existing IAM controls.
IAM assessment teams must identify remote work locations and out-of-office identities. If they know “where” users are, security teams can apply appropriate access controls and user privileges.
IAM assessment: when
Understanding when users connect to network assets is another critical part of assessing an IAM program. Users tend to have consistent usage patterns reflecting their working schedules. This creates a digital fingerprint. If usage patterns change, this may provide evidence of illegitimate access.
IAM assessment: how
The fifth aspect of assessing IAM involves analyzing the composition and effectiveness of existing identity and access management systems. In other words, “how” companies meet their IAM compliance requirements.
Assessments should consider how current technology is meeting IAM requirements. But they also need to consider future investments. Will IAM systems continue to meet business goals? Can improvement actions deliver better security?
Strategy also comes into this part of the process. Assessors need to make sure security policies reflect existing IAM systems. They need to ensure policies, technology, and procedures match compliance aims. If not, new policies and action plans are required.
Identity and Access Management audit checklist
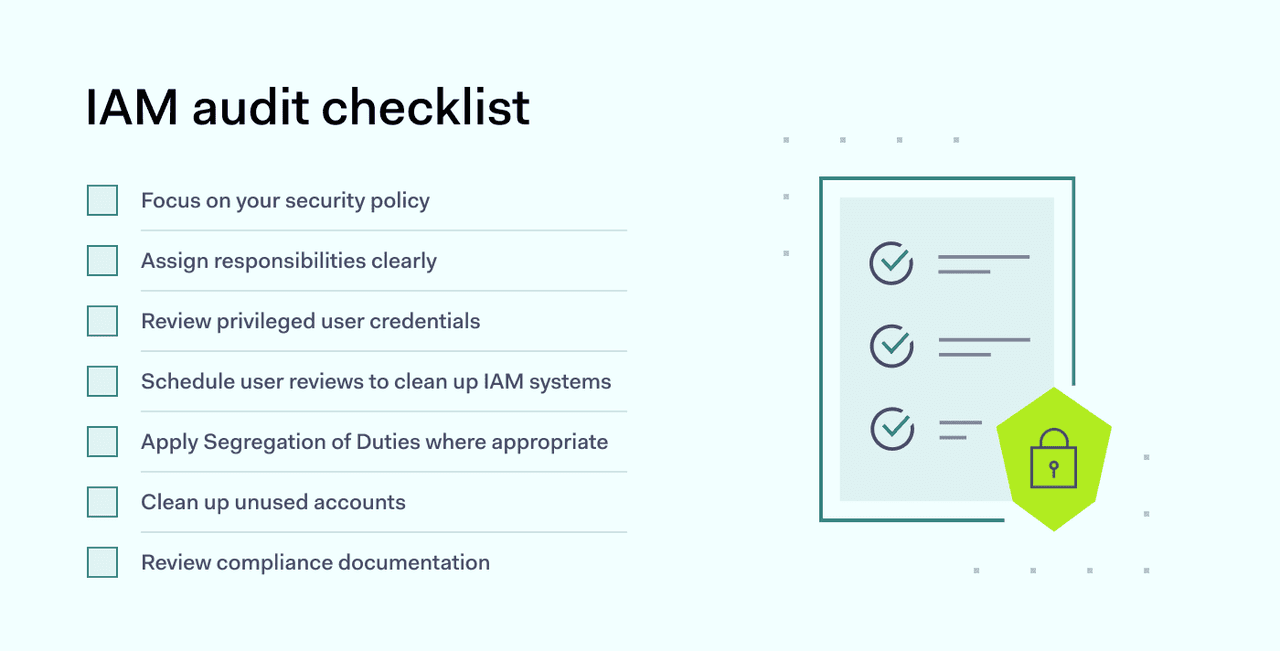
Covering every area is important when you carry out an identity and access management assessment. This brief audit checklist provides a useful guide to ensure comprehensive coverage:
1. Focus on your security policy
Use the assessment to revisit and improve your security policy. Your IAM security policy should reflect current technology or any IAM systems you intend to implement. It delivers formal procedures to manage identities and secure your network assets. And it should make responding to security incidents much easier.
2. Assign responsibilities clearly
Clearly define who is responsible for aspects of identity and access management. This might include:
- Managing federated identities
- Offboarding accounts
- Checking admin privileges
- Quality-checking data governance.
3. Review privileged user credentials
Cut the number of accounts with privileged access. These accounts are the most urgent security risk, allowing users the greatest freedom within the network. Where possible, assign elevated privileges temporarily.
4. Schedule user reviews to clean up IAM systems
Review all accounts to avoid over-provisioning. Apply the “principle of least privilege” wherever possible. Create a user review schedule to continually assess user profiles. Maintain better security by keeping privileges at a safe level.
5. Apply segmentation of duties where appropriate
No single user should have total control over security measures such as authentication, assigning user privileges, and off-boarding accounts. Divide roles to add secondary approvals. This may compromise efficiency, but segregating duties will make security much tighter.
6. Clean up unused accounts
Deleting expired accounts is a crucial part of access management. Automate the removal of accounts when employees leave roles or posts within the organization. Check for any generic accounts created during testing processes.
7. Review compliance documentation
Double-check your IAM policies and cross-reference with relevant compliance frameworks. Make sure there is an audit trail of user activity and security changes. Provide simple evidence of compliance for annual audits and avoid any areas of confusion.
Ensure the integrity of your IAM system
Maintaining an up-to-date IAM system is one of the most important business objectives. Companies need to create relevant security policies and formal processes. They must constantly check user privileges and avoid exposing sensitive data. Obsolete accounts must be removed. Roles should be segregated to avoid excessive power residing with one individual.
A good IAM assessment ensures smooth authentication and authorization. Assessing access management processes is the only way to ensure tight, consistent data security. Assess regularly and assess thoroughly. The result will be fewer data breaches and compliance issues.
