Secure Access Service Edge (SASE) is divided into two sections: security and networking. Secure Service Edge (SSE) covers the security side of the equation.
SSE features tools suited to guarding cloud assets and dynamic network perimeters. It complements Secure Access Service Edge networking features such as SD-WAN.
SSE offers a way to secure software-as-a-service (SaaS) and infrastructure-as-a-service (IaaS) assets. Setups vary depending on network architecture. Solutions generally have several components in common. These components form the basis for flexible cloud security.
Security Service Edge definition
Security Service Edge (SSE) is a cybersecurity framework designed to provide secure access to web services and applications. It brings together different security measures, like secure web gateways (SWG), cloud access security brokers (CASB), and zero-trust network access (ZTNA), to keep data and users safe in the cloud. SSE helps businesses set the same security rules for everyone, ensuring data protection no matter where they are.
Imagine it as a dedicated security team that not only checks IDs but also makes sure every part of the building is secure. This is especially helpful for cloud environments, where traditional security perimeters no longer apply. In the cloud, data and applications are accessible from anywhere, so it's important to protect them at every point where people can access them.
Key takeaways
- Security Service Edge (SSE) is a cybersecurity framework designed to ensure safe access to web-based services and applications.
- Its key strengths are zero-trust principles, regulation of cloud service interactions, and internet traffic filtering for improved security and access control.
- SSE reduces risks, enhances threat monitoring, provides secure access globally, protects data, cuts costs, scales easily, and manages digital transition risks, which is beneficial for cloud-transforming or remote-managing companies.
- SSE challenges include integrating with current security tools, updating security policies, managing team dynamics, and ensuring compatibility with communication tools.
- SSE is ideal for basic cloud access and web interface security, while SASE is better for those deeply reliant on Software-as-a-Service (SaaS) or Infrastructure-as-a-Service (IaaS).
- Compared to the broader SASE, which combines security and networking for cloud transitions, SSE focuses solely on security.
- SSE's flexibility allows for easy incorporation into existing networks without the full implementation of SASE, which gives a straightforward solution for better security.
SSE core capabilities
SSE has started a new chapter in network security. It offers a safer and more flexible way for users, devices, and cloud services to interact. Instead of the old approach where one solution was supposed to fit everyone, SSE introduces personalized security. Here, we'll explore how SSE's core features play a vital role in improving digital security.
1. Zero Trust Network Access (ZTNA)
Zero Trust Network Access is a security approach based on the idea “never trust, always verify”. ZTNA setups guard cloud and on-premises assets via context and identity-based access control. These controls exclude unauthorized users and permit privileged users to access essential resources.
In the context of SSE, Zero Trust creates a dynamic network perimeter. Systems detect all connected devices and users. SSE Software monitors access requests and applies security policies consistently at every endpoint. No traffic passes through the network or associated cloud services without proper authentication.
2. Cloud Access Security Broker (CASB)
Cloud Access Security Brokers regulate interactions between cloud-based SaaS applications and other resources. This includes internal corporate networks, remote devices, and the wider internet.
Cloud Access Security Brokers detect SaaS applications. Security teams can then manage these apps via a centralized dashboard. CASBs allow instant data location across all SaaS apps. This contributes to robust data protection. They may also feature User Entity and Behavior Analytics tools. These tools enable traffic monitoring at even greater levels of depth.
3. Secure Web Gateway (SWG)
Secure Web Gateways act as an interface with the external internet. They can apply to remote workstations, office resources, and cloud assets. The SWG integrates security policies on access control and identification. It also blocks unauthorized access requests at the source.
Policy enforcement uses web visibility and URL filtering to stop malicious content. Access controls regulate access to social media platforms or sites hosting inappropriate content. SWGs also track data transfers across the web boundary. This ensures that confidential data remains inside network perimeters.
4. Firewall-as-a-Service
Firewall-as-a-Service (FWaaS) is a key element in SSE, offering network protection from the cloud. It stands out from traditional firewalls because it provides adaptable security that responds immediately to threats and is not limited by location. This flexibility is essential in an environment where users need access from various locations.
FWaaS upholds the Zero Trust model, which ensures the verification of all connections and boosts security for both cloud and on-premise environments. It integrates well with other SSE elements like CASB and SWG, creating a thorough and efficient security system.
5. Additional security features
In addition to ZTNA, CASB, and SWG, SSE includes several vital security features.
- Data Loss Prevention (DLP) tools are essential as they monitor and protect sensitive information, preventing unauthorized data exits from the network.
- Remote Browser Isolation (RBI) serves a crucial function by creating safe zones for web browsing, which greatly reduces web-based threats.
- Secure Email Gateways (SEGs) filter emails, catching phishing attempts, spam, and malware before they reach users.
- Identity and Access Management (IAM) systems enhance security by managing who has access to which resources, requiring strict authentication and authorization.
Together, these features play a key role in strengthening SSE's defenses against various cyber threats.
What is the difference between SASE and SSE?
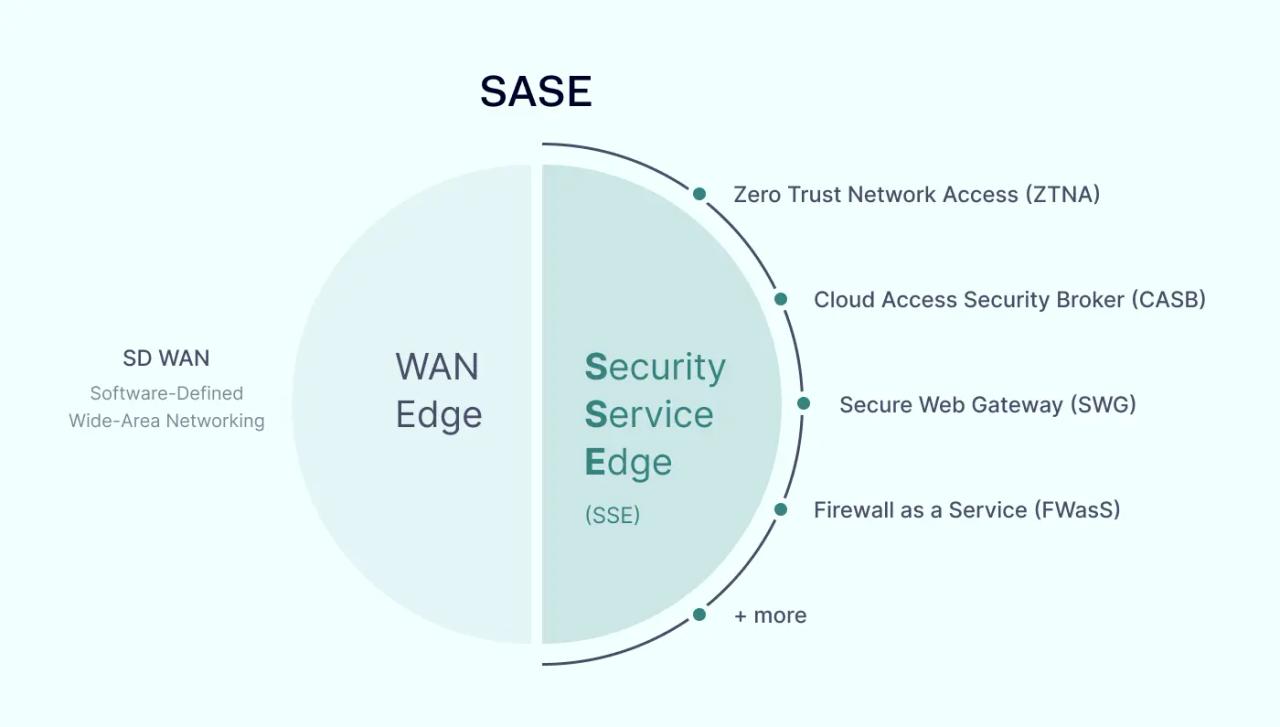
SASE and SSE are similar but far from identical. SASE is a comprehensive package of cloud-hosted tools covering both security and networking. First described by Gartner in 2019, the SASE framework is a popular way to secure cloud resources.
SASE facilitates seamless transitions from on-premises to cloud or hybrid solutions. On the networking side, this involves Software-Defined Wide Area Networking (SD-WAN) edge infrastructure. SD-WAN allows remote workers easy access to cloud resources. It also avoids centralized data routing and associated traffic bottlenecks.
SSE is the security counterpart to SD-WAN edge infrastructure. It provides a layer of threat protection and access management. These functions guard the networking aspect of SASE implementations.
As with SD-WAN, SSE security capabilities take the form of cloud services. Direct connections between central network nodes and remote users are minimal. Everything flows via a distributed network of PoPs and creates direct-to-cloud connections.
Companies can add SSE to networks outside full-blown SASE implementations. SD-WAN architecture is not necessary to achieve edge security for both internal networks and cloud resources. SSE protects cloud resources alongside legacy network technology. Compared to SASE, it represents a lower-cost option for many network managers with similar security features.
Understanding SSE benefits and use cases
SSE offers multiple benefits for companies making cloud-based digital transformations, providing a viable resolution to many core challenges that organizations face as they shift to remote working and SaaS. Critical benefits include:
1. Risk reduction via simplified endpoint security
Networks are becoming ever more complex. SaaS and IaaS combine with remote work and on-premises assets. This causes problems for legacy security solutions. Fixed perimeters, VPNs, and simple access management cannot deliver security for cloud resources.
SSE offers a solution. Centralized dashboards identify and track SaaS assets. Secure Web Gateways govern access. Automated security policy delivery provides device and software updates. The result is far fewer (if any) security gaps and complete network visibility.
2. Advanced threat monitoring
Security Service Edge includes various data and threat protection tools. These tools prevent and neutralize critical network security threats. They also allow security teams to implement ZTNA security principles.
Under Zero Trust Network Access, all users operate within defined network segments. Users are tightly confined and have limited ability to disrupt or damage assets. Encryption and masking conceal network apps from the wider web. This reduces visibility to attackers. SSE also monitors user identity and activity in real time. This generates alerts and valuable insights from security data.
SSE includes security tools like inline encryption, web filtering, and malware detection. When combined, they present a formidable suite of protective measures.
3. Efficient, secure access to resources worldwide
SASE and SSE work together to ensure secure global remote access to cloud resources, websites, and internal networks. Secure Web Gateways are accessible from any remote working device or location. Security policies apply instantly when remote access requests arrive. This includes authentication, device and identity discovery, and privileges management.
SSE also mixes security with efficiency. Distributed architecture guarantees minimal latency. There is no need for access requests and user traffic to pass through central data centers. Instead, security inspection occurs when the user connects with cloud resources.
Virtual Private Networks (VPNs) are not necessary with SSE. Removing VPN coverage eliminates another source of latency. There is no need to patch VPN tools regularly. The risk of poor staff adherence to VPN policies is also reduced.
4. Reliable and flexible data protection
DLP tools identify and classify sensitive data. This covers cloud infrastructure and traditional network resources. Personally Identifiable Information (PIP) or customer credit details are easy to track and locate, helping guard against data breaches. Companies can also protect data to meet regulations such as HIPAA and PCI-DSS.
5. Network consolidation to reduce costs
Security Service Edge supports cloud-based services. Consolidation restricts the need to source solutions from many vendors. Central control panels make day-to-day security monitoring much easier.
Teams can disseminate security policies across all connected devices. Automation ensures regular security policy delivery. The result is in-depth security tracking and robust protection without increasing resource usage.
6. Easy to scale cloud security
SSE allows companies to expand networks without compromising edge security, illustrating an SSE use case where managers can add new cloud infrastructure via the central administration panel. This automatically detects services and delivers security policies. There is little risk of cloud apps going unnoticed. Security applies dynamically as the network perimeter changes.
The same applies to changes in user communities. With SSE, workforces can switch from on-premises to work-from-home or hybrid solutions. New branches can connect securely with virtualized corporate assets. Third parties can collaborate safely, and onboarding new hires is smooth and secure.
7. Risk management during digital transitions
Security Service Edge serves as a transitional security solution. It offers flexible network security for companies putting in place SD-WAN or similar tools.
With SSE, companies can manage security risks, consolidate resources, and launch cloud transformations.
SSE challenges: what you need to know
Security Service Edge is an effective security solution for cloud-reliant organizations. It's also ideal for managing large communities of remote workers.
Even so, implementing Secure Service Edge technology can present several challenges. These challenges tend not to be critical obstacles to deployment. However, they must be featured in the planning process when organizing SSE roll-outs.
- Some businesses rely on tens or even hundreds of existing security solutions. These tools range from firewalls and anti-malware scanners to rights management systems. To work effectively, SSE must replace the functions of existing tools. However, IT teams need to avoid security gaps during the transition process.
- Security policies must be re-formulated to reflect changing realities. Policies need to enable centralized security management via SSE control planes. This can be a challenge when implementing SSE alongside legacy security tools.
- Some SSE roll-outs experience friction between networking and security professionals. Transitioning to cloud-based security tools depends on collaboration between these core personnel groups. Project managers must handle any disagreements sensitively.
- SSE can cause problems with voice-over-IP and collaboration tools. Pure Security Service Edge implementations often serve these traffic types poorly. In those cases, networks may need SD-WAN capabilities to function effectively.
When do you need SASE, and when is SSE sufficient?
As we noted earlier, Secure Access Service Edge and Security Service Edge are different. In some cases, SSE alone will deliver the security protection companies need. In other situations, a combination of SD-WAN and SSE tools will be a more sensible solution.
Generally, companies with existing SD-WAN deployments will not benefit from SASE. In that case, Security Service Edge will be a suitable complement to SD-WAN networking. It provides the security protection that cloud infrastructure requires.
Some companies must secure web interfaces and have limited reliance on cloud security. SSE could be a good fit in those instances. SWG offers dependable protection against malicious web traffic. It also provides robust controls to govern user behavior.
SASE will probably be preferable if companies rely on SaaS or IaaS in core operations. SASE represents a simplified, overarching security solution to accommodate many cloud services. SD-WAN integration allows network managers to streamline traffic. Security Service Edge features add security to the network edge.
SSE can also be a staging post on the route to a full SASE deployment. It creates a secure layer around cloud resources. This makes it easier for IT teams to manage complex digital transformation processes.
SSE: secure edge protection without radical network changes
Security Service Edge is a suite of security technologies optimized for SaaS settings. It features a mix of Zero Trust Network Access, Secure Web Gateways, and Cloud Access Security Brokering.
SSE guards dynamic network edges subject to constant change. This suits companies transitioning to SaaS resources and remote work. In some cases, SSE combines with SD-WAN to form full SASE configurations. But it can also function as a separate edge security solution. For more information, explore SSE solutions at the NordLayer website.