ISO 27001 is the most commonly used framework when building an information security management system. To become fully compliant, companies must pass an ISO 27001 certification audit. This process can be demanding and complex. Knowing what the audit process entails is of critical importance.
This article introduces the ISO 27001 audit process. We will examine why ISO 27001 audits matter, how they work, and how organizations can prepare. The result will be a thorough grounding in ISO 2700 certification, enabling readers to align their systems with ISO requirements.
Key takeaways
- ISO 27001 is a leading international framework for information security management. Achieving ISO 27001 compliance requires external certification audits and internal audits.
- ISO 27001 certification enhances data security, builds trust, and helps achieve regulatory compliance. It promotes a strong security culture, improves organizational confidence, and emphasizes continuous improvement.
- The certification process involves internal and external audits. Internal audits prepare for certification by assessing risks and implementing mitigation actions. External audits by ISO-accredited certification bodies verify that organizations have achieved ISO 27001 compliance.
- Organizations can prepare for an ISO audit by understanding their ISMS and comparing it to ISO benchmarks. Compliance teams can update policies, implement controls, and provide staff training. Internal audits can check that the organization is ready for certification.
- ISO 27001 compliance requires regular surveillance audits and recertification every three years. Failing ISO audits can result in decertification, making building a culture of continuous compliance essential.
What is an ISO 27001 audit?
An ISO 27001 audit assesses whether an organization's information security systems meet ISO standards. This assessment compares existing security controls and policies with ISO best practices. Auditing identifies vulnerabilities in business processes and recommends corrective actions to ensure regulatory compliance.
ISO 27001-compliant organizations must carry out regular internal audits and submit to external audit exercises. Successful external audits allow the organization to attain ISO 27001 certification. However, to retain this status, companies must constantly check their information security posture and make any necessary changes.
What are the benefits of ISO 27001?
ISO 27001 certification has many benefits. The certification process is demanding and complex, but these benefits often outweigh those challenges.

For example, ISO 27001 compliant organizations benefit from:
- Robust information security. The International Organization for Standardization (ISO) defines global best practices for information security. Companies that pass an ISO 27001 audit program have state-of-the-art technical controls, staff training processes, and internal policies. They are well-placed to safeguard sensitive data and prevent damaging data leaks.
- Greater trust from customers and partners. Companies that fail to secure confidential data quickly lose the trust of their customers and stakeholders. ISO 27001 certification signals that a company takes security seriously. Cutting data breach risks also builds trust over the long term.
- Enhanced regulatory compliance. Companies worldwide must comply with data security regulations. ISO 27001 certification and recertification audits allow organizations to maintain compliance. Organizations can update security systems to comply with GDPR, HIPAA, or PCI-DSS rules. And compliance minimizes the risk of financial penalties.
- A stronger security culture. ISO 27001 recommends training employees to create an internal security culture. The internal audit process requires participation from all departments and senior officers. Systematic training communicates security practices to all staff members.
- Confidence and organizational knowledge. Companies that pass an ISO 27001 audit know that their security management systems are robust and dependable. They can focus on achieving core business goals instead of fire-fighting security or privacy issues.
- Continuous improvement. ISO 27001 compliance is an ongoing process. Compliance does not end with the initial audit report. Companies must carry out periodic audits and arrange annual visits from external auditors. They must assess residual risk and address any problems that emerge. There is no room for complacency or organizational laziness.
ISO 27001 audit types
The ISO 27001 certification process involves two types of audits. Compliant companies must schedule regular internal audits to identify risks and take corrective actions. External audit exercises must also verify that organizations meet ISO standards.
Internal audit
Under Clause 9.2 of ISO 27001, organizations must complete regular internal audits to assess their information security management system.
Compliant organizations need an audit plan specifying audit frequencies, methodologies, and who has auditing responsibilities. External certification is not possible without a formal internal audit program, so this is not an optional extra.
A specialist internal team should execute internal audits. Team members should have ISO 27001 training, although external contractors can assist.
Generally speaking, the internal auditor will:
- Carry out a documentation review. Auditors must check all internal policies to ensure they align with ISO standards.
- Assess security controls to ensure they comply with ISO 27001 best practices.
- Carry out a sampling review of ISMS functionality. Sampling assesses how well the ISMS performs when handling everyday tasks. It identifies whether security gaps exist.
- Complete an ISO risk assessment and gap analysis. This procedure lists core information security risks and recommends corrective actions to achieve ISO standards.
- Oversee improvement projects until technical and administrative aspects of the organization's ISMS meet ISO 27001 standards.
Companies should document audit findings in a central repository. The audit report should be available for external auditors. Its recommendations should feed into continuous compliance management. This includes periodic surveillance audits to double-check compliance with ISO 27001 standards.
External audit
Companies cannot achieve ISO 27001 certification without passing an external audit by an ISO-accredited certification body. Certification bodies are independent organizations that verify ISO 27001 compliance and charge for their services. There are four core types of ISO 27001 external audit.
ISMS design reviews
Reviews take place before the main Certification Audit. External specialists visit organizations to assess the scope and quality of their ISMS. Auditors from the certification body check procedures, controls, and policies. They verify whether the ISMS matches ISO requirements and identify gaps where further action is needed.
Certification audits
Certification audits verify that the organization meets ISO 27001 standards as a whole. During a certification audit, assessors execute field reviews and extensive testing of operational processes. They determine whether the ISMS meets the 118 requirements listed under Annex A of ISO 27001. If so, the external audit team awards a full certification.
Surveillance audits
Certification is not an endpoint. It starts an ongoing ISO 27001 audit process that ensures continuing compliance.
Compliant organizations must pass regular surveillance audits carried out by the certification body. These audits assess core operational aspects of the ISMS. Assessors test how the ISMS performs against ISO benchmarks. They can revoke ISO certification if the organization does not take prompt corrective action.
Recertification audits
ISO 27001-compliant organizations complete recertification audits every three years. This ISO 27001 audit replicates the initial certification audit. Companies prove their ISMS meets ISO standards and reflects changes to ISO guidance since the last audit exercise.
External and internal audit processes work together to maintain ISO 27001 compliance. Companies must use periodic internal audits to prepare for external certification and surveillance audits. Otherwise, they risk losing their certified status.
Stages of a typical ISO 27001 audit
ISO 27001 audit processes vary between sectors and organizations. However, under the ISO framework, two broad stages are common to all certification audit processes.

Stage 1: the ISMS design review
The ISMS design review is stage 1 in the external certification audit process. The design review is not a learning exercise to help companies build a compliant ISMS. It rigorously assesses an existing ISMS to establish its ISO 27001 compliance status.
Preparing for the stage 1 ISMS design review is critical. Core tasks for internal audit teams include:
- Risk assessment and scoping. Compliance teams assess security risks and determine the scope of the ISMS. They document critical risks and define mitigation actions in a risk treatment plan. They also record the basis for decisions to avoid or downgrade risks.
- Assessing the ISMS. Internal teams analyze the organization's ISMS and take action to ensure that it meets ISO 27001 standards. The actions should cover policies, procedures, and technical controls to secure data.
- External ISMS audit. After the internal audit, external specialists determine whether the ISMS meets ISO 27001 requirements. A stage 1 audit report documents the organization's compliance status. This report may enable the organization to move to stage 2 immediately. However, further corrective actions or training may also be necessary before proceeding.
Stage 2: field review and certification audit
Organizations decide whether to pursue full certification after the internal audit and ISMS review. If they choose to proceed, stage 2 involves a comprehensive field review of their information security management.
The design review focuses on documentation review tasks and procedures. The field review verifies that the organization is implementing essential policies and procedures.
Auditors use random sampling to assess the status of controls, data handling systems, policies, and employee training. They compare operational systems to the standards defined by ISO 27001 Annex A, and document divergences from security best practices.
Auditors interview managers and random staff members. They also check internal audit logs to ensure the organization has a continuous compliance policy.
Stage 2 generates a certification audit report. This report certifies ISO 27001 compliance. This certification lasts for three years.
Who should carry out ISO 27001 audits?
Experts with ISO 27001 experience must always carry out external and internal ISO 27001 audits.
Internal audit teams should receive additional ISO training to raise their knowledge levels. Without this expertise, auditors will make mistakes and create compliance gaps. Auditing errors complicate the certification process and can lead to complete failure.
Internal teams should also be independent to avoid conflicts of interest. Auditors cannot be responsible for managing the ISMS. As a result, many companies bring in external contractors to manage the pre-certification internal audit.
External accreditation bodies approve auditors to work on their behalf. These audit professionals should have relevant credentials. For example, they may have completed the ISO 27001 Lead Auditor course. Audited companies should request proof of qualifications, as low-quality external assessments can be costly.
How to prepare for an ISO 27001 certification audit
Systematic preparation is essential when applying for ISO 27001 certification. In general, the following process will help organizations get ready for a formal ISO 27001 audit procedure.
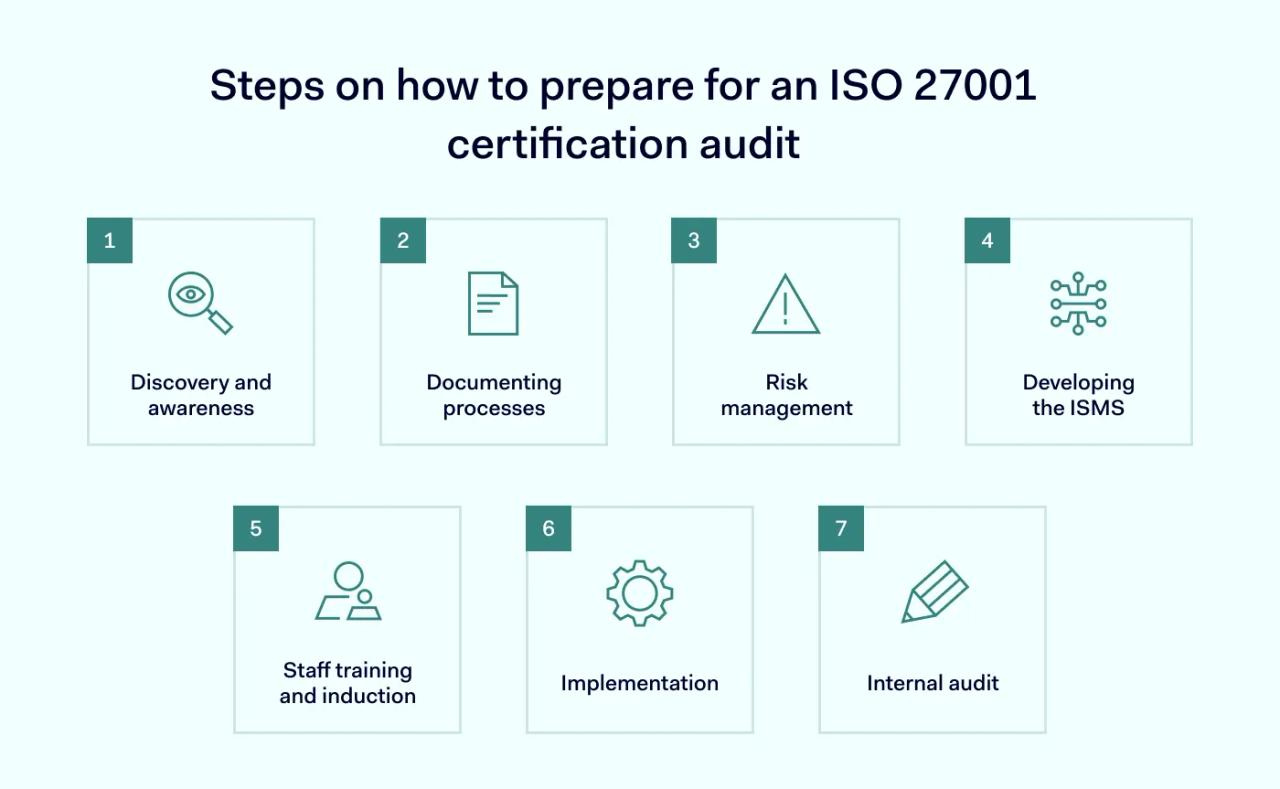
1. Discovery and awareness
The first preparation stage is understanding your existing ISMS. ISO 27001 audit teams must record all interested parties alongside data collection and storage operations. Discovering the data security context allows you to understand the scope of the ISMS. In other words, teams know the areas covered by policies, processes, and controls.
2. Documenting processes
ISO 27001 requires compliant organizations to maintain several core documents. These essential documents include:
- A definition of the scope of the ISMS
- An organization-wide information security policy
- ISO 27001 risk assessments
- A central risk register and risk treatment plans
- A Statement of Applicability that defines how the organization applies Annex A controls
Organizations should store these documents in an accessible central repository. The project manager and security officers should approve the final documents. Personnel teams should also add this documentation to training processes.
3. Risk management
Audit teams must assess critical security risks. The core role of the ISMS is to identify, assess, and mitigate these risks. Risk management teams should classify risks according to their probability and potential harm. They should also create risk treatment plans for each risk. These plans should document risk management strategies, and companies should update them throughout the ISO 27001 audit process.
4. Developing the ISMS
ISMS development brings together the elements of ISO 27001 in a single strategic plan. This plan ensures that the organization has covered relevant Annex A security controls. Components of the ISMS should include:
- Scope. Defining the boundaries of the ISMS and what it protects. Inventory all assets and classify high-risk data.
- Risk assessment. Understanding data security risks and defining mitigation measures.
- Policy development. Creating an overall security policy to safeguard critical data.
- Security controls. Applying access controls, encryption, firewalls, and other relevant controls.
- Governance. Creating leadership roles to manage the ISMS. Assigning security responsibilities throughout the organization.
- Training. Ensuring that all employees and other stakeholders receive security training.
- Incident response. Creating procedures to respond, mitigate, and report data security incidents.
5. Staff training and induction
Clause 6.3 of ISO 27001 Annex A requires companies to provide "suitable instruction" in information and data security. Training requirements are quite vague, but certification audits require evidence that the organization seeks to strengthen awareness of security best practices.
Complying with ISO 27001 also requires formalized induction processes. These processes familiarize employees with the ISMS. They should educate staff about data security basics, organizational policies, and compliance responsibilities.
6. Implementation
ISMS development teams must work closely with internal security professionals to implement the strategic plan. Remember that the certification audit will assess how closely documented policies match real-world operations. It is essential to carefully implement every aspect of the ISMS to ensure that paper recommendations become real-world processes.
7. Internal audit
Internal audits verify that the organization meets ISO 27001 security standards. This part of the process should be carried out by independent individuals not involved in day-to-day information security duties.
The internal audit has two general areas of focus:
- Ensuring policies and procedures are operational and meet ISO 27001 requirements (as discussed above).
- Checking that the organization can monitor ISO 27001 compliance. This includes periodic surveillance audits by objective teams. Compliance teams should share audit reports with senior managers. The organization should document all internal audits.
At this stage, the organization should be ready for a certification audit. Its ISMS should meet Annex A requirements. There should be a dynamic risk management and security culture. The organization should also be ready to deliver continuous improvement in line with ISO guidelines.
How often should you perform an ISO 27001 audit?
ISO 27001 guidelines require organizations to have a plan for regular audits. However, no single schedule applies to all compliant bodies. Each organization must decide how frequently to audit its ISMS to balance costs and continuous compliance.
ISO 27001 is a risk-based standard. This means that organizations handling high-risk data should audit their systems two or three times every year. By contrast, annual audits are sufficient for smaller businesses with a simple ISMS.
Other factors that increase the need for audits include previous compliance violations or failed audits and changes to the organization's risk landscape. One-off ISO 27001 audits may also be needed when an organization changes dramatically, for instance, if two companies merge their data processing systems.
Generally speaking, annual audits are the bare minimum. Regardless of internal policies, compliant companies must apply for recertification audits every three years.
Time required for completion of ISO 27001 audit
The length of internal ISO 27001 audits depends on the complexity of the ISMS and the organization's compliance status. Auditing simple data processing environments can take as little as a few days. However, auditing large corporations can take weeks or months.
Internal audits will take longer if the ISMS is flawed. For example, audit teams may need to build training programs, implement technical controls, and create a new risk management strategy. If the company already has a robust data security culture, project teams can complete these tasks fairly quickly.
External audits take between two and three months. Stage 1 tends to take about a month to create ISMS documentation. Stage 2 is slightly longer, requiring an in-depth assessment of controls and processes. Generally, the process from internal preparation to completing the external certification audit takes between 4 and 6 months.
Consequences of failing an ISO 27001 Audit
What happens if companies don't prepare properly for an ISO 27001 audit?
If companies fail an external certification audit, auditors will issue a non-conformity report (NCP) detailing the reasons for non-certification. When the organization addresses these issues, it can re-apply for certification.
The situation is more complicated if companies fail surveillance audits. In this case, external auditors will issue an NCP as part of the audit report. The NCP should outline reasons for failure and provide a deadline for corrective action.
The audited organization then needs to create an action plan to correct the situation. This plan details concrete steps to restore ISMS compliance and should work within the timescales provided by the external auditor.
When audits uncover significant failures, re-auditing is essential. This fresh audit will focus on areas for improvement and the quality of the organization's response. If assessors perceive an inadequate response, companies can completely lose their ISO 27001 certification.
Disclaimer: This article is for informational purposes only and not legal advice. Use it at your own risk and consider consulting a licensed professional for legal matters. Content may not be up-to-date or applicable to your jurisdiction and is subject to change without notice.
