Cloud solutions provide businesses scalability, cost-efficiency, and flexibility. An increasing number of organizations are integrating these solutions into their products. As a result, attacks on cloud interfaces are also rising. How can you build a strong cloud security architecture?
Key takeaways
- Cloud security architecture is a framework of technologies designed to protect cloud-based systems and data from cyber threats.
- The importance of cloud security architecture lies in its ability to safeguard critical operations and sensitive data as more companies depend on cloud services.
- Components of cloud security architecture include encryption, access management, visibility tools, automation, network segmentation, flexibility and scaling, resilience, stack validation, and compliance. These components work together to secure data and control access.
- Encryption and access management secure data as it moves and rests, and control who can access cloud resources through advanced identity management tools.
- Automation and network segmentation automate security tasks and create secure zones within the cloud to prevent unauthorized access and enhance operational efficiency.
- Cloud security architecture threats include denial-of-service (DoS) attacks, insider attacks, poorly secured cloud hardware, shadow IT, and human error.
- Principles of cloud security architecture focus on confidentiality, availability, and integrity to ensure data is protected, accessible only to authorized users, and accurate at all times.
What is cloud security architecture?
Cloud security architecture is the framework and technologies used to protect data and systems in the cloud. This framework includes a set of security measures that help prevent unauthorized access and data breaches, ensuring that your information remains safe and secure in various cloud environments.
That sounds clear, but in a world of hybrid IaaS, PaaS, and SaaS systems, finding the right cloud security mix is far from simple.
This article will look at the components of cloud security architecture and how these elements apply to cloud security models. The result will be a strong understanding of how to guard cloud assets and balance productivity and cybersecurity.
Why is cloud security architecture important?
Cloud computing security architecture matters for several reasons. Companies rely on cloud services to host workloads and apps or to store data in cloud containers. PaaS systems power eCommerce stores, while some companies have switched their entire IT infrastructure to IaaS systems.
Data at rest on cloud servers or passing from users to the cloud must be secure from external attackers. If not, hackers can access confidential data flows and extract sensitive information. DDoS attacks can cripple company operations.
Security teams must guard cloud assets against insider threats and insecure employee behavior. Weak passwords and poor phishing awareness can instantly compromise cloud assets. Companies need to take into account local data compliance issues to protect cloud data. And they also need to police device security, ensuring every connected device is safe to use.
Users are responsible for cloud security architecture. They cannot leave security to cloud partners or work on an app-by-app basis. Instead, cloud security best practice recommends creating enterprise-wide strategies to cover every cloud security risk.
In other words, companies must build an architecture that protects critical assets. Poor cloud security architecture is a fatal flaw in any business security posture. But what is cloud security architecture in practice? Let's explore how to build that structure and secure cloud resources.
Components of a cloud security architecture
Cloud security architecture is not a one-size-fits-all approach. Cloud implementations vary, with Software-as-a-Service, Platform-as-a-Service, and Infrastructure-as-a-Service all commonly used. Security measures depend on what apps are in use, how companies use cloud apps, and who requires access.
The tools required vary from case to case. However, some key technologies can be found in almost any cloud security strategy:
Encryption
Encryption scrambles data passing between network users and cloud assets. When data encryption operates, attackers cannot read communications or extract valuable information. Data is encrypted end-to-end, from leaving user devices to entering cloud portals. Your cloud provider should encrypt data at rest on their services. Virtual Private Network (VPN) encryption may also apply above network infrastructure. VPNs conceal user identities from external observers. They add another layer of encryption, making data theft even harder.
Access management
Identity and Access Management (IAM) tools control who can access cloud resources. Access control applies at the client end and forms a junction between company networks and cloud applications. IT managers set privileges for each user, determining their access to different cloud assets. IAM may also include multi-factor authentication (MFA) to make access safer.
Visibility tools
Devices connected to the cloud must be visible at all times. Cloud Access Security Brokers (CASBs) provide real-time information and deliver alerts about unusual behavior. Security teams can monitor user activity and data flows to detect threats if they emerge. They can also log user activity for compliance and audit purposes. This enables network managers to improve their cloud security architecture.
Automation
Cloud security management does not require labor-intensive monitoring. Security teams can automate monitoring systems to work in the background. Companies can also automate security policy management and software updates, saving time that could be spent on cybersecurity analysis.
Network segmentation
Segmentation divides cloud applications from other network assets. Segmenting cloud assets creates a zone of trust around each cloud portal. These zones only admit authenticated users and exclude unauthorized actors. Segmentation prevents access to cloud assets for malicious actors if they enter the network through exposed endpoints. Alongside security features like activity tracking and IAM, it provides a foundation for Zero Trust Network Access (ZTNA).
Flexibility and scaling
Cloud security strategies must include scope to expand and adapt as network perimeters change. Security teams must be able to extend security protection when adding new cloud services to the network. User onboarding and off-boarding should suit cloud resources. Workers should have access to core resources when commencing new roles, and automation tools should immediately remove orphaned accounts.
Resilience
Cloud security architecture must include measures to boost cloud system resilience. Firmware underlying cloud deployments must be strong enough to withstand cyberattacks. Companies must be able to restore critical cloud resources as soon as possible when attacks occur. Security teams should also reinforce the boot process to prevent malware infection when booting cloud systems.
Stack validation
Security managers must check every layer of the security stack to validate components. Apps and stored data must remain unchanged during cloud deployments and digital transformations. Data should be protected against unauthorized changes while cloud services are in use.
Compliance
Cloud security architecture fits within the overall context of regulatory compliance. Data security methods should meet relevant national and regional data protection legislation such as GDPR. Strategies should use internationally recognized data security standards as a yardstick. For instance, they might use ISO 27017 (cloud security controls) and ISO 27018 (protecting personally identifiable information).
Cloud security posture management (CSPM) software can help with compliance. CSPM tools compare security configurations with compliance best practices. They highlight any required actions, making it easier to meet regulatory goals.
Cloud security and shared responsibility model
One way to understand cloud security architecture is by dividing the challenge into SaaS, PaaS, and IaaS approaches. Users and cloud providers operate according to the shared responsibility model in all three cases.
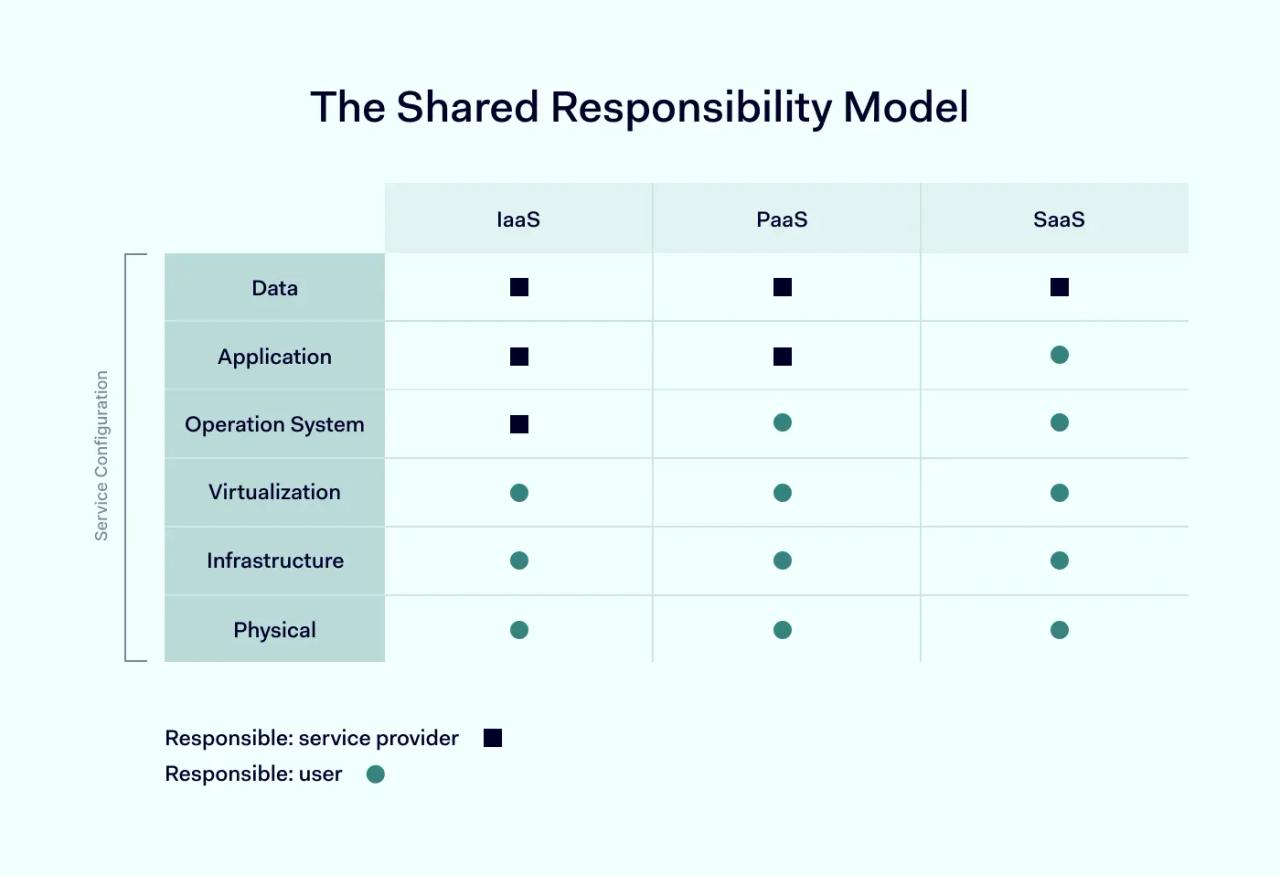
In the shared responsibility model, the cloud service provider is responsible for securing apps – including code, infrastructure, and hardware required to deliver customer services. But this means users are responsible for the data they store on cloud servers. Not all cloud users are aware of what this means.
Infrastructure as a Service (IaaS)
In IaaS solutions like Microsoft Entra ID, customers buy cloud infrastructure from a third-party cloud provider. Companies can add their software and operating systems to this infrastructure. This is a good way to create a customized cloud deployment. In this arrangement, customers are responsible for securing the apps they add to cloud infrastructure. Cloud providers have a relatively small security role.
Platform as a Service (PaaS)
In PaaS solutions, customers buy off-the-shelf platforms that run on ready-built cloud infrastructure. Amazon Web Services, Heroku and SAP Cloud are common examples. In this arrangement, customers must secure applications they run on PaaS platforms. They are responsible for app configuration and managing access. Cloud providers must create secure platforms and play a more active security role than IaaS partners.
Software as a Service (SaaS)
SaaS involves purchasing access to cloud-based applications on a case-by-case basis. Dropbox, Mailchimp, Zoom, and SalesForce are good examples. Companies using SaaS applications are responsible for managing access to those apps. Security teams must authenticate users and exclude malicious actors. Cloud partners are responsible for securing the apps themselves.
Multi-cloud systems
These definitions are simplifications of actually existing security architectures. In reality, most companies operate multi-cloud systems. These systems involve multiple SaaS apps and potentially more than one PaaS solution. In these cases, cloud security architecture must assess security responsibility for each app and manage risk accordingly.
Principles of cloud security architecture
When creating a cloud security model, a sound approach is to build your strategy around core principles. In the context of the cloud, three principles apply - confidentiality, availability, and integrity. All three principles should form part of your cloud security planning.
Confidentiality
Companies should conceal data stored on the cloud from outsiders. Data should only be available to authorized users. Companies should limit access on the basis of trust. Only users with appropriate permissions should be able to access or edit confidential data. Security teams should regularly review permissions for every user.
Availability
Cloud applications and customer services hosted on the cloud should always be available. Security teams need to neutralize threats to availability. DoS attacks are a critical threat in this area, but security staff needs to mitigate any threats capable of taking services offline.
Integrity
Companies need confidence that applications and data function as expected. They also need assurance that apps have not changed without authentication. Users or intruders should not be able to change data and application code without authentication. Tools should track any changes and flag data integrity issues as they arise.
Cloud security architecture threats
It's impossible to build a cloud security architecture without knowing the major cloud security threats. Cloud users must have risk strategies and mitigation measures to handle the most significant cyber threats. Here are some frequently encountered hazards that cloud users need to consider:
Denial-of-Service (DoS) attacks
In denial of service attacks, cyber-criminals direct large amounts of traffic to cloud applications. Eventually, systems are overwhelmed, resulting in application shutdown and network damage. Security tools can screen potential DoS traffic at the network edge and monitor for signs of DoS attacks before they become critical. Cloud partners may also have systems to redirect traffic during DoS assaults.
Insider attacks
Many cloud attacks occur via company insiders. Employees may misuse login credentials or accidentally leak credentials to outside actors. Phishing and poor password security commonly compromise employee accounts. Cloud providers may also harbor insider attackers with access to client data. And poorly secured cloud assets may be vulnerable to governmental or non-official surveillance.
Poorly secured cloud hardware
Cloud partners may use storage hardware located in distant parts of the world. They may also subcontract hardware management to other companies. This can lead to security gaps at the network edge. For instance, third parties may not properly secure physical hardware. This makes life far easier for attackers.
Shadow IT
Security teams may not have complete control over cloud environments. For example, app configurations can change without the knowledge of IT teams. This is a problem commonly associated with DevOps teams. Shadow IT leads to potential security vulnerabilities and makes stack validation processes essential.
Human error
Cloud security can also be affected by simple mistakes. For example, users often misconfigure S3 Storage Buckets, creating an entry point for attackers. Companies may leave security control panels poorly secured. User permissions can become excessively weighted towards user access, not security.
Create a rock-solid cloud security architecture
Cloud computing security architecture is a critical part of modern business management.
Every day vast amounts of data flow through cloud containers and applications. SaaS apps host crucial work meetings and confidential doctor-patient consultations. HR apps manage payrolls and recruitment and sales apps store sensitive financial data. All of these cloud services require security from external threats.
A robust cloud security architecture protects confidentiality. It ensures data integrity, and makes services available to stakeholders. Security strategies must provide a good fit for PaaS, IaaS, and SaaS systems. They also have to account for shared responsibility with cloud partners.
Fortunately, many tools contribute to cloud security setups. Encryption, CASBs, access management consoles, segmentation, activity tracking, VPNs, backups, and disaster recovery tools all have roles to play. Build a strategy that suits your situation.