Cloud computing enables new opportunities for businesses willing to make the transition. However, at the same time, cloud computing presents many challenges that must be addressed. Cloud security is always a shared responsibility, so each involved party must know its role.
In this article, we present the biggest cloud security issues. This information should help you better understand the cybersecurity risks associated with cloud computing.
How secure is the cloud?
Questions about cloud security threats are a valid concern, as all your sensitive data is held outside of your company premises. However, in most cases, data will be much safer when stored in the cloud than kept on the user's device.
Usually, cloud data is stored in an encrypted form, meaning that anyone needing data access needs a digital key. Not to mention that the data itself is stored across a large fleet of servers with multiple backups. This is done to protect the information in case of a server malfunction or a cyberattack.
Cloud security risks and threats
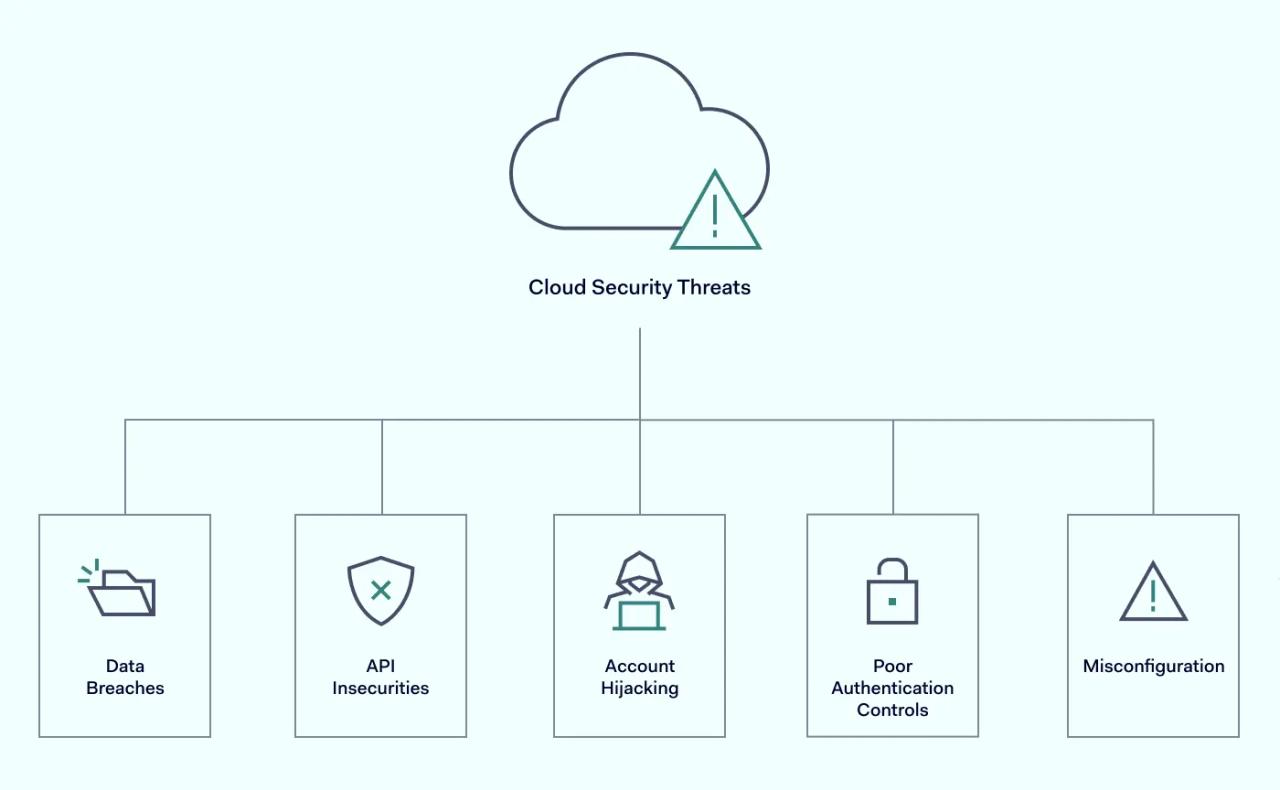
While the cloud is much safer than device storage, it's important to note that no security system is uncrackable. A broad spectrum of cybersecurity risks applies to cloud infrastructure that could compromise your data.
1. External data breaches
Most business owners view data loss as their biggest cloud security concern. Leaking financial or customer data threatens customer trust, which can cause long-lasting revenue loss. As the security responsibilities are shared between a cloud service provider and a client, there's always a risk of failure to secure the network properly. The servers should also be properly equipped to withstand DDoS attacks.
2. Misconfigurations
Cloud infrastructure is very complex, so there's a real risk of missing something when setting it up. Organizations risk misconfiguring their access systems when scaling up or scaling down their operations. Missing important updates or overlooking existing infrastructure shortcomings may also contribute to critical misconfigurations.
3. Poor authentication controls
Your data is as secure as strong is the weakest component within its chain. If the only thing that your employees need is a username and a password, this is something that could be easily exploited. Generally, the rule is to protect sensitive assets with a corresponding level of authentication mechanisms. The more sensitive the data, the more authentication layers it should have.
4. Account hijacking via phishing
Hackers don't need to penetrate your internal networks when the data is hosted in the cloud. This means that hijacking your administrator's account and posing as one could be enough to gain direct access to the cloud-hosted data. It requires less effort to pull off than bypassing various cybersecurity defenses that could be deployed internally.
5. API insecurities
Growing Application Programming Interface (API) usage creates an opportunity for hackers looking for an opening into the network. This area must be thoroughly checked for vulnerabilities, poor coding practices, lack of authentication, and insufficient authorization. These and other similar oversights can help hackers gain access to the system.
6. Insider threats
Even if external hackers are kept at bay, rogue or malicious insiders pose a real risk if they have access to sensitive data and systems. Insider threats can come from employees or third-party contractors and involve data theft, sabotage, fraud, and more. Strong access controls and monitoring are needed to mitigate this threat.
7. Data loss or leakage
When data is moved to the cloud, there is a risk it may inadvertently be shared too broadly if access policies are misconfigured. Even accidental deletion poses a risk if proper backups are not in place. Strict classification and access policies are needed to prevent unauthorized data exposure.
8. Denial of service attacks
As cloud infrastructure relies on constant online connectivity, it is susceptible to DDoS attacks which attempt to overload servers and resources with traffic. Protection against these threats requires strategies like traffic filtering, mitigation services, and redundancies.
9. Infrastructure vulnerabilities
Despite best efforts, newly discovered software or hardware vulnerabilities may still affect cloud platforms. Providers need responsive processes to patch flaws, and customers need diligence in applying updates. Continuous monitoring assists with rapidly identifying and fixing issues.
Cloud security vulnerabilities
Cloud vulnerabilities are a sensitive subject because cloud services are used for development, analytics, machine learning, and other tasks. There are multiple weak points that hackers will check first when attempting to penetrate a network. Here's the list of the top cloud vulnerabilities.
1. Open S3 bucket
An Amazon S3 bucket is a public cloud storage resource used within Amazon Web Services. Buckets are similar to folders as they consist of data and descriptive metadata. According to various reports, poorly configured S3 buckets contribute to a significant portion of cloud security data breaches. Some of the companies that were recently affected by these misconfigurations that resulted in a data breach were Netflix and Capital One. This allowed some of the private buckets to be accessible to anyone interested. Therefore, when using cloud services, it's critical to implement proper access rules.
2. Incomplete data deletion
One of the trickiest parts of cloud data management is data deletion. On the one hand, it's a process that should be done irreversibly. On the other hand, an administrator must ensure that there are no backups left.
In cases when multiple tenants are sharing the infrastructure, data should be deleted without the possibility of retrieving it. It's not enough to wipe the hard drive and hope for the best. The data should be overwritten with blank tables and then deleted again.
As for the data backups, this requires full visibility of where they are kept. There shouldn't be any unsupervised copies lying in the cloud as, over time, this data could find its way to hackers. That said, in most cases, data deletion must follow the cloud provider's procedures, so it will likely be a joint effort. Although some cloud service providers may have different requirements.
3. Lambda command injection
Lambda function is an AWS computing service that allows running code without provisioning or managing servers. It can execute code when needed, ranging from a few daily requests to thousands per second. The service model allows using this tool per the computed time only. It's a convenient tool that tests any application or backend service.
As the user function is serverless, this greatly increases the potential attack surface. The function can be launched from various events like database changes, code modifications, notifications, and other events. This means that a hacker can try to inject an unexpected event into the vulnerable function, which is then passed down to the OS-level application. It's potentially devastating to the stored data as the hacker could obtain direct access to the cloud using this vulnerability.
4. Failure of separation among multiple tenants
The multitenancy model helps drive costs low — multiple customers are using the same software instance, which is installed on multiple servers. User data and resources are located in the same computing cloud, controlled and distinguished by various unique identifiers. Naturally, the risks associated with this model arise from the shared model itself, as the used computer hardware is the same for multiple clients.
Data isolation is paramount in such scenarios as multitenancy would, by definition, be one of the best attack vectors at a hacker's disposal. Not to mention that successfully breaching one of the tenants makes it easier to infiltrate co-residents within the cloud. Since the only boundary between them is individual user IDs, this gives plenty of leverage for malicious individuals.
5. Server-Side Request Forgery (SSRF)
SSRF vulnerabilities occur when an application exposes internal endpoints or resources that should not be directly accessible. For example, an attacker could craft requests that get the server to connect to internal systems and expose sensitive data which is then returned to the attacker. This can give an attacker insight into the cloud infrastructure setup and potentially access to other systems. Careful input validation is needed to prevent SSRF.
6. Lateral movement
Once a bad actor has gained any level of access to a cloud system, they may be able to move laterally or “hop” from one instance or service to another to expand their reach. With privileges, they could access compute resources like containers or VMs, unauthorized systems with insecure configurations, backup instances for data extraction, and more. Compartmentalization and least privilege access models are key to containing lateral movement. Monitoring for anomalous account activity also helps.
Summary
While cloud computing is an incredible opportunity for most businesses to reorganize their infrastructure flexibly, this doesn't come without a price. While, by default, cloud security provides much more safety than locally hosted data, there's much that an organization should keep in consideration when setting it up.
Like most systems, cloud computing isn't without its weak points. The majority of data breaches result from misconfigurations and poor authentication controls. It's important to emphasize that cloud security isn't given. The high status of security has to be maintained.
Then, there are quite many vulnerabilities that a hacker could exploit when planning an attack on your cloud. Network administrators should be in the loop about the latest developments regarding S3 bucket exploits and be very cautious regarding the deletion of backups and other data. Only by timely addressing various cloud risks can it be possible to create a secure model that helps businesses achieve their goals.