Role-based access control allows organizations to connect access privileges to user roles. RBAC makes it easier to manage user permissions and protect sensitive data from unauthorized access. These abilities make it a go-to cybersecurity tool. This article explains how to implement role-based access control, alongside some helpful tips to manage it effectively.
RBAC implementation steps
Setting up role-based access control requires careful planning. Improperly defined role groups can lead to security gaps and user access problems. This neutralizes the benefits of RBAC and may put critical assets at risk.
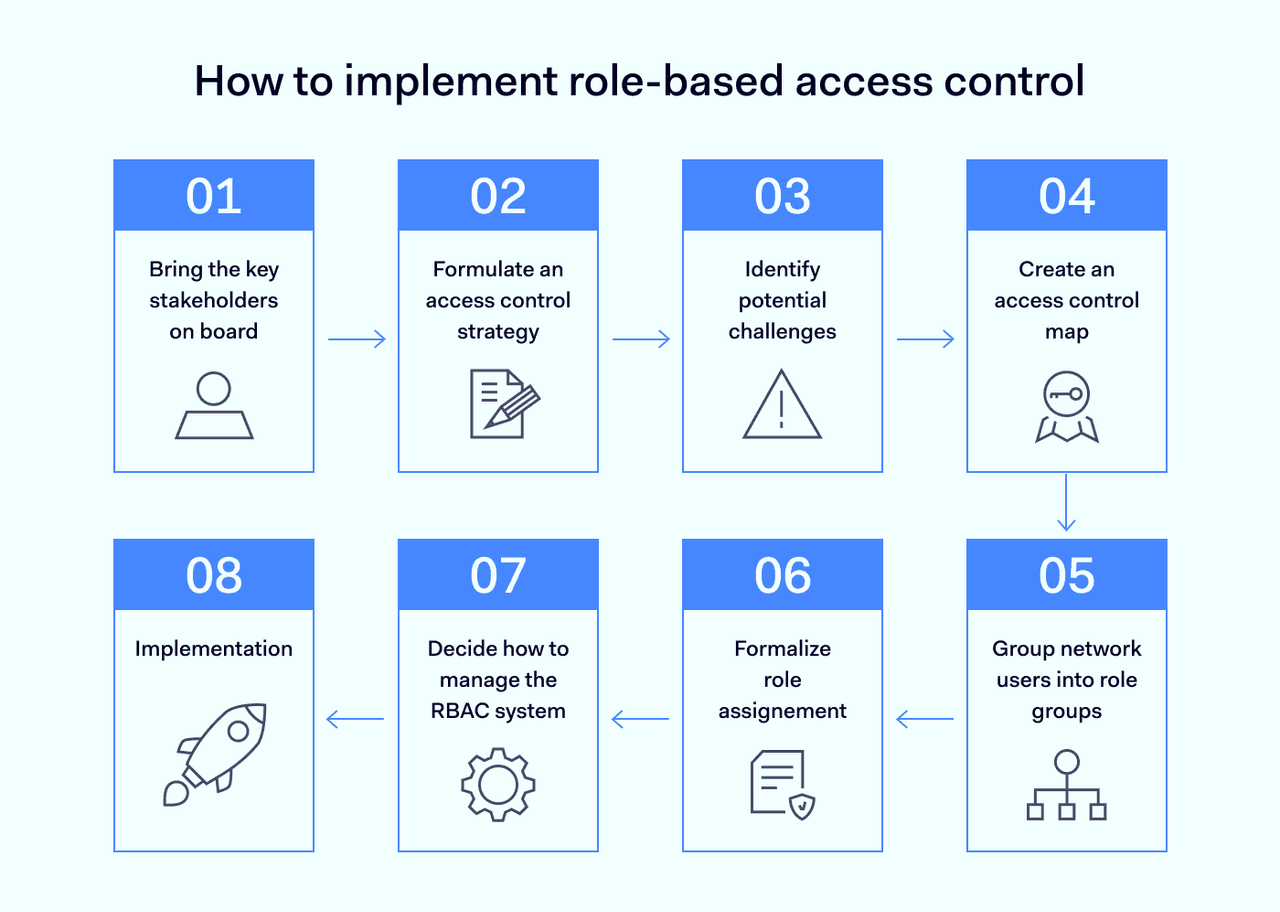
The process below sets out a typical route to a robust access control setup. It provides a good starting point for RBAC implementation.
1. Bring the key stakeholders on board
Every successful RBAC implementation starts with collaboration, not code. Before you even think about permissions or software tools, you need to get all relevant stakeholders in the same room—physically or virtually. This usually means bringing together department heads, IT administrators, security officers, and sometimes compliance specialists.
These people hold the knowledge about which roles exist, what their responsibilities are, and which systems they interact with daily. Without their input, you risk gaps or overlaps in access rights. Think of this stage as building a blueprint before starting construction—everyone needs to agree on the design before work begins.
At this point, you’re not finalizing roles, just ensuring there’s a shared understanding of the goals, benefits, and limitations. Also, establish how feedback will be collected during and after rollout. Good communication early means fewer unpleasant surprises later in the process.
2. Formulate an access control strategy
Once you’ve gathered your stakeholders, the next step is to define a clear, realistic strategy. An RBAC implementation without a strategy is like setting off on a road trip without a map—you might reach your destination, but it will take longer and cost more.
Your strategy should explain how RBAC fits into your wider security framework and business objectives. For example, are you primarily trying to protect sensitive customer data, meet compliance requirements, or reduce administrative overhead?
It’s also worth considering future scalability. If your company plans to expand to multiple regions, acquire other businesses, or adopt more cloud-based tools, your RBAC design should be flexible enough to adapt. Set measurable outcomes, such as reducing access-related helpdesk tickets or simplifying audit preparation. Clear targets ensure you can track whether your RBAC implementation is working as intended.
3. Identify potential challenges
Before going into the technical build, it’s crucial to anticipate and plan for obstacles. Every environment is unique, so the challenges you face when you implement RBAC may not be the same as those in another organization.
Common issues include inconsistent use of multi-factor authentication, a mix of old and new operating systems, or a hybrid workforce that spans office, home, and mobile setups. Each of these factors can make role assignments more complex.
Compliance is another major consideration—if your business operates in regulated industries such as healthcare or finance, your RBAC system must align with strict data protection rules. Mapping these challenges early will help you create realistic timelines and avoid last-minute changes.
4. Create an access control map
An access control map is essentially an inventory of what you need to protect. This step turns vague ideas about “system security” into a concrete list of assets and applications.
Start by documenting every system that stores or processes business-critical data: cloud platforms, on-premises databases, email servers, financial systems, HR portals, and collaboration tools. Include both major assets and smaller tools that only a few teams use.
A thorough map also helps you visualize relationships between users and systems. This makes it easier to group assets into categories and later match them to appropriate roles. Without it, your RBAC implementation risks being incomplete or inconsistent.
5. Group network users into role groups
Grouping users into role groups is where the concept starts to take shape. The principle is simple: people with the same job function should have the same permissions. This reduces the need for one-off access changes, making your system easier to maintain.
Finding the right level of granularity can be tricky. Too few roles, and you risk giving people more access than they need. Too many, and you’ll overcomplicate the system.
A good starting point is to have department managers suggest the roles their teams need. In parallel, IT and security teams can analyze system logs to identify real-world access patterns. This approach ensures your role definitions are both practical and data-driven.
6. Formalize role assignment
This is where planning becomes action. Using the data from earlier steps, define the exact roles in your RBAC system and assign them to users. Apply the “principle of least privilege,” which means giving each role only the permissions necessary to perform its tasks.
For example, a customer support agent may need read-only access to the customer database, while a sales manager may require both read and write access but not deletion rights.
Document your role definitions so administrators know exactly what each role entails. Clear documentation is essential for audits and makes it easier to train new system administrators. A careful, methodical approach at this stage will make it easier to implement RBAC effectively.
7. Decide how to manage the RBAC system
RBAC isn’t a “set it and forget it” system—it requires ongoing governance. Before launch, define how you will maintain and review role definitions.
This should include regular audits to check whether permissions still match job responsibilities. Assign responsibility for RBAC governance to a small, trusted group, and ensure that no single person can approve their own elevated privileges.
If your organization is subject to compliance requirements, integrate audit schedules into your plan. A clear management process ensures your RBAC implementation stays accurate, secure, and efficient over time.
8. Implementation
Now it’s time to go live. Instead of switching every user to the new system at once, roll out RBAC in phases. Start with a single department, monitor results, and address any issues before expanding.
Early feedback is essential—listen to both managers and end users. If people find that their roles don’t give them the tools they need, it’s better to fix those problems now than after full deployment. Expect a brief adjustment period; even the best-planned system may require tweaks once in real-world use. This phased, attentive approach will help you implement RBAC smoothly while keeping user trust high.
Tips on how to manage role-based access control
Robust access control is an essential part of an organization's security posture. But how should RBAC users administer access control systems to ensure integrity, security, and efficiency? Here are some tips that will simplify access management challenges.
Be prepared to make changes
Role-based controls are created at a single point in time. But as time progresses, organizations change. Access controls must change in step with the organization that they serve.
It is important to review roles and privileges regularly. Schedule periodic audit exercises that cover several critical areas:
- Check that roles match the actual needs of users. Users may switch applications, change their organizational structure, or switch to different work locations. All of these shifts can affect the integrity of role-based access controls.
- Establish whether any new controls are needed. For example, a company might implement RBAC before migrating sales data to a cloud-hosted solution. Admins will need to adjust any roles that access data on the new system.
- Ask for feedback from stakeholders. Bring senior managers into the audit process. RBAC works best when all users are engaged and willing to provide information. IT teams cannot operate in a silo as they manage the access system.
Remain vigilant to potential vulnerabilities
RBAC management should be continuous. IT teams need to track suspicious system access requests and patterns of behavior.
For example, a cluster of denied access requests from users in a role group could be evidence of a phishing attack. Or it could be a flaw in the way that role is configured. Constant monitoring can detect the real issue and make any necessary changes.
It helps to log data about requests for security assistance. From time to time, there may be spikes in assistance requests from departments or project teams. Monitor those spikes and use them to fine-tune roles if needed.
Create clear processes for privileges escalation
Sometimes, administrators provide users with temporary privilege escalations. Users may need access rights for short-term projects. A flexible RBAC system can accommodate these adjustments, enabling seamless workflows.
Implementing temporary role changes can be risky. When they grant access administrators should log all escalation requests. They should also track user activity for the duration of the escalation. It is also essential to remove any additional privileges when the user reverts to their original role.
Consider adding ABAC to manage granular security
Controlling access can become harder as RBAC expands. Privileges creep can see users acquiring too many permissions. Roles can overlap as organizations become more complex. And the number of roles can become unmanageable. When this happens, applying additional controls can help.
Attribute-based access control (ABAC) supplements role-based systems. ABAC allows admins to secure assets with contextual or environmental controls. For example, system access to financial records could be limited to employees using MFA within office hours, in a specific location.
Access Control Lists are another option. Administrators can configure ACLs for individual devices or applications. They can be a useful way to control access temporarily.
ABAC and ACLs can compensate for some of RBAC's weaknesses. But it is not a substitute for properly modeling and implementing role-based access architecture.
Conclusion
RBAC is a powerful way for organizations to strengthen their security posture. Role-based controls are simple to manage, prevent unauthorized access, and help organizations comply with security regulations. However, to deliver these benefits RBAC systems must be well-constructed.
Planning, communication, and awareness are the keys to successful implementation. By following the steps outlined in this article and implementing the management tips provided, organizations can protect their data efficiently.
