Healthcare providers protect patient information, one of the most sensitive data types available. The United States government regulates and enforces stringent guidelines to safeguard the confidentiality and security of health information. The Health Insurance Portability and Accountability Act (HIPAA) is the primary reference document for healthcare providers to protect and manage sensitive customer data.
Even though the regulation applies to every healthcare provider in the US, it’s not easy for businesses to ensure that their practices are HIPAA compliant. Therefore, this HIPAA compliance checklist will guide you through the HIPAA essentials to make your compliance journey easier.
Key takeaways
- HIPAA compliance ensures the protection of sensitive patient information, including electronic PHI (ePHI).
- The HIPAA compliance checklist is crucial for standardization, trust, data security, and easier compliance with other regulations.
- Covered entities, business associates, and subcontractors in healthcare must adhere to HIPAA compliance.
- The HIPAA compliance checklist includes appointing a privacy officer, IT infrastructure checks, and staff training.
- HIPAA policies cover patient rights, electronic PHI security, breach response, and extended responsibility to business associates.
- To succeed in HIPAA compliance, identify sensitive data, implement safeguards, and choose the right network access solution.
To ensure compliance for your medical organization, follow these steps:
- Familiarize yourself with the five rules of HIPAA.
- Identify the rules relevant to your organization.
- Conduct a risk analysis.
- Develop a compliance plan.
- Set up accountability measures.
- Take measures to avoid potential HIPAA violations.
- Follow updates to HIPAA.
- Maintain thorough documentation.
- Promptly report any data breaches.
HIPAA compliance basics
HIPAA compliance ensures that the organization meets all the regulatory requirements imposed by the US federal government for protected health information or PHI. It refers to any information concerning a person's health, healthcare, or payment for their healthcare.
PHI can take many forms, but its digital counterpart is ePHI — electronic Protected Health Information. Since most modern healthcare organizations store patient data digitally, this has become the primary private patient data archiving method.
These types of data fall under HIPAA compliance:
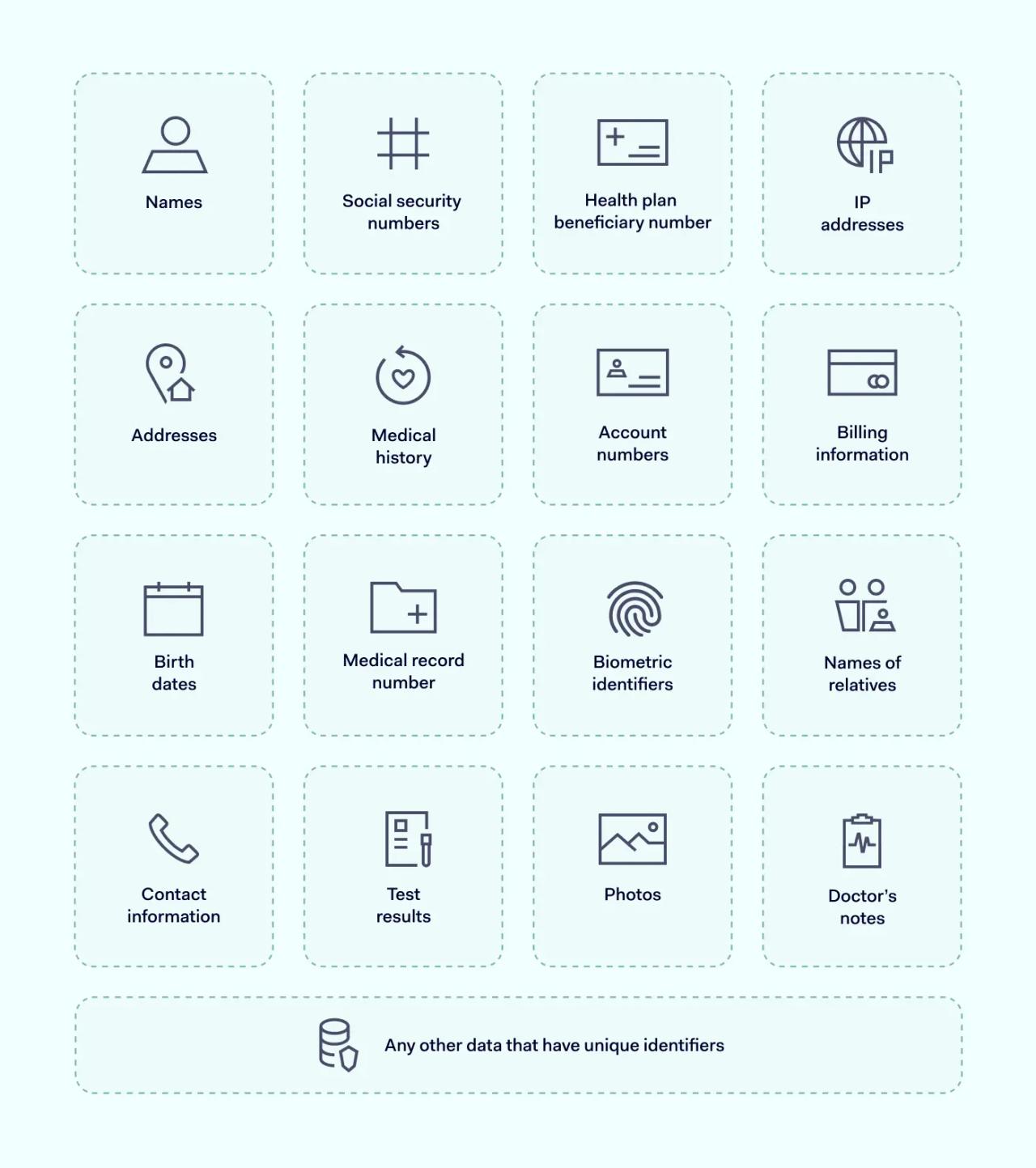
Why is the HIPAA compliance checklist important?
The HIPAA compliance checklist is essential for healthcare organizations and patients. It ensures healthcare providers securely handle sensitive information according to the same rules. For instance, an insurance provider can only access the clinically relevant information concerning a patient's medical history.
HIPAA compliance helps to ensure:
- Standardization. HIPAA encourages the establishment of standard procedures for handling and protecting health information. Simultaneously, it promotes interoperability among different systems and healthcare providers, eliminating unnecessary friction.
- Trust and reputation. Compliance helps build trust with patients, knowing that their data is handled securely. It also enhances the reputation of healthcare providers and associates as reliable entities.
- Easier compliance with other regulatory certificates. Following HIPAA compliance ensures that entities adhere to state and federal regulations and standards. In addition, this helps avoid repercussions for sensitive data leaks and may help improve the organization’s position for other compliance certificates.
- Data security. HIPAA compliance also promotes best cybersecurity practices like data encryption. Not only is this extremely relevant when protecting sensitive health information, but it also helps to improve overall cybersecurity posture.

Who needs to be HIPAA compliant?
Generally, three organization types are subject to their compliance requirements.
Covered entities — are directly involved in creating and transmitting PHI by performing treatment or other procedures and accepting payments for health services. These organizations are subject to a full scope of HIPAA compliance requirements.
Examples: doctors, clinics, psychologists, dentists, pharmacies, and health insurance companies.
Business associates — organizations that handle PHI and obtain it from covered entities but aren't involved in its creation. This type covers many enterprises providing services to the healthcare industry.
Examples: consultants, accounting firms, IT suppliers, and lawyers.
Subcontractors — organizations hired by business associates to help with specific niche roles. Since it also means that they could have some PHI access, meaning that HIPAA regulations apply to them.
Examples: Cloud hosting providers, shredding companies, etc.

HIPAA compliance checklist

Being HIPAA-compliant means covering multiple business areas, which can be a colossal job. To help you get started, we created a short HIPAA compliance checklist.
1. Dedicate responsible personnel
The first step is to appoint a privacy and security officer to oversee the implementation of your HIPAA compliance program and ensure it is efficient. It will also make your organization transparent.
The second step is to develop a written privacy and security policy and code of conduct for everyone in your organization. It's also essential to carefully document all the policies and procedures that the appointed official will enforce.
2. Develop a HIPAA compliance administration plan
Organizations in the healthcare industry should ensure their long-term strategies are aligned with the HIPAA. This involves implementing several crucial rules and guidelines for security awareness training program.
Most HIPAA breaches happen because of unintentional disclosures or negligence. Internal training ensures that all staff members are knowledgeable and competent in managing ePHI. This minimizes the risk of breaches and ensures that the organization operates within the parameters of HIPAA compliance.
3. Make sure your IT infrastructure meets the required standards
PHI or ePHI can't be stored anywhere — it requires secure storage. The protection types fall into two categories: technical and physical.
- Technical safeguards deal with supervising hardware and software of the machine that stores PHI. Logs monitoring to check who accessed what particular data is a good example.
- Physical safeguards govern restrictions on who has access to where PHI is stored. It regulates who has what credentials and how much data is accessible to them.
4. Deploy technologies for PHI handling
According to HIPAA requirements, HIPAA covered entities are responsible for PHI safety. It involves adding technologies to your setup to ensure your security methods aren't easily bypassable. Outdated systems open the door to hackers, so plan for regular security software updates.
The HIPAA Security Rule states that HIPAA covered entities and their business associates must protect PHI at rest and during transmission. One of the security methods is to use technology that encrypts data, monitors authorized users, and blocks unauthorized user access.
5. Evaluate the current risk level
HIPAA, being a federal law, doesn’t mandate official audits nor offers any certification for compliance. Instead, it necessitates organizations to conduct self-assessments, enabling them to identify any breaches or suspicions of violations proactively.
Organizations striving for HIPAA compliance routinely conduct security audits, ensuring that risk analysis is a continuous process. These audits encompass a comprehensive review of all administrative and technical policies. Undertaking periodic checks is essential for maintaining an enduring compliance status.
6. Plan for emergencies
Develop an action plan for responding in case of cyberattacks or security incidents. As the Breach Notification Rule states, all HIPAA-compliant businesses must have specific policies and procedures for handling an unexpected data breach.
The administrative safeguards require a contingency plan. Tailoring it to your organization, location, and policies would be best. It’s the only way to secure the availability, integrity, and security of Protected Health Information. The plan should create a roadmap of actions during an emergency and should include the method of data backup, contacting workforce and business associates.
7. Investigate found violations
An investigation into each report about a found HIPAA violation must provide guidelines and a timeframe for its resolution. Usually, this step will follow after audits, and an organization must resolve each discovered violation before it can be HIPAA-compliant.
As the HIPAA Breach Notification Rule states, an organization should report a breach within 60 days following the date of discovery. Exceeding this time is one of the HIPAA violations. In addition, your business associates must also report attempts or successful unauthorized uses or disclosures of PHI.
8. Document HIPAA activity
Everything related to HIPAA and its actions must be logged, recorded, and stored. Its scope should include everything from the first steps taken to audit evaluations. A good practice is to keep it in one place to make HIPAA compliance policies transparent and valuable in case of a violation.
Remember to keep the documents containing PHI or the policies about PHI for at least six years. The HIPAA documentation includes policies and procedures, all written and electronic communications, and actions requiring records.
9. Find the right security provider
If your organization lacks the resources to manage everything in-house, there are security vendors who specialize in compliance. Such companies can provide software that matches your setup and complies with all HIPAA requirements. However, you must ensure they're trustworthy and won't accidentally leak your data.
10. Get familiar with HIPAA
HIPAA establishes four rules for safeguarding the privacy and security of patient medical information. Each rule provides a framework for the necessary measures required in various fields to achieve compliance. Following these guidelines equips organizations to align their actions to reach compliance.
Non-compliance with HIPAA laws can substantially impact an organization. Therefore, educating staff about these HIPAA rules is imperative. Doing so fortifies the organization’s defenses, ensuring steadfast compliance and safeguarding sensitive data against potential breaches.
HIPAA policies and procedures requirements
Entities covered by HIPAA must comply with various policies and procedures to ensure the confidentiality, integrity, and availability of ePHI. This also means they must be aligned with the main HIPAA rules. Here’s a short explainer of what each of them entails.
Privacy Rule
HIPAA Privacy Rule outlines patients' rights regarding their health information and regulates who can access it. It also defines what information falls under the ePHI classification and its maintenance and transmission channels without endangering data integrity.
Not all of it deals only with digital information. Parts of this Privacy rule also list the required paperwork and consent forms to be filled out by those handling PHI. The timeframe is irrelevant, as it applies to past, present, and upcoming visits, payments, or procedures.
However, there are some exceptions regarding the uses and disclosures of PHI. The HIPAA Minimum Necessary Standard defines these exceptions. For example, when a patient wants to access their medical history or in case of judicial proceedings, a covered entity must share the requested PHI.
Security Rule
HIPAA Security Rule establishes standards for safeguarding information when transmitted or stored electronically. So, while privacy defines procedures for keeping the data confidential, the security rule concerns the technical methods to make it inaccessible to unauthorized individuals.
The Security Rule covers all areas, including physical safeguards, used technologies, administration, and everything else relating to securing the PHI storage devices. Three primary safeguards are:
- Administrative safeguards concern PHI handling policies and procedures, including training all employees on HIPAA regulations and code of conduct and assigning a staff security official. Administrative safeguards also apply to regular security risk assessments to monitor risks and system gaps.
- Physical safeguards are measures that ensure the physical security of PHI. Your organization needs a restricted-access location or facility where you can store all the PHI. It's also essential to implement security systems to prevent intrusion and detection and to control workstations and devices accessing PHI.
- Technical safeguards apply to hardware, software, and other technologies that limit access to ePHI and secure the digital transmission of ePHI. It means implementing access control solutions like encryption, multi-factor authentication, automatic log-off, and audit control.
Breach Notification Rule
As the name implies, the Breach Notification Rule details the course of action in case of a data breach. This rule assumes that no system is 100% hackproof and that it's better to have a detailed plan of what to do in an emergency. It defines how to notify the affected patients and what steps to take to limit the damage.
The steps are as follows:
- Affected individuals' notification plan. Patients whose PHI has been disclosed must receive a written notice about what has happened with their sensitive data.
- Public disclosure plan. In most cases, the affected organization has to issue a public statement in primary news media sources.
- The timeframe is two months. It's imperative by law to disclose data breach findings under 60 days.
- Inform the Secretary of Health. If the incident affects more than 500 people, the report submission timeframe is 60 days. If it affects less than 500 people, the timeframe extends to the end of the year.
Final Rule
It's one of the most recent additions to HIPAA that expands the scope of regulated entities beyond covered entities. The current result means that a covered entity will be held responsible for any potential violations of their business associates and subcontractors. It made it more challenging to blame the partners for raising the safety standards.
To ensure that your organization won't have any problems, aligning internal and external safety standards and risk assessment with compliance procedures is necessary.
Tips for a successful HIPAA compliance plan
As covered entities and their business associates have access to medical records, they must meet HIPAA regulations. All aspects, such as physical and technical data security safeguards, are equally important and should be considered.
Our HIPAA compliance checklist can help you determine the expectations for your organization. To demonstrate HIPAA compliance, you must know where your sensitive data is, how it's classified, who and when can access it, and how to design and implement controls to protect your PHI and monitor all its access.
The path to HIPAA compliance can be long and winding, but choosing the right network access solution can make it easier to achieve it. We sincerely hope that our HIPAA checklist will make reaching compliance easier for your organization.
HIPAA compliance checklist FAQ
Does HIPAA apply outside the U.S.?
HIPAA applies to certain U.S. entities and their business associates, even if operating internationally. While it primarily affects U.S. operations, international entities must comply with it when handling U.S. patients' information, alongside any additional local privacy laws like the EU’s stricter GDPR.
What are HIPAA compliance requirements?
HIPAA-compliant entities are required to evaluate potential risks targeting PHI confidentiality. The key areas are administrative practices, physical security, IT systems security, and crisis recovery plan. After identifying the risks, they must implement an action plan to eliminate them.
What must a HIPAA checklist include?
All HIPAA checklists will rely on the gathered data on all the key areas to evaluate potential risks. Its documentation should act as the basis for HIPAA compliance enforcement detailing specific actions to limit PHI exposure to the public.
How do I know my documentation is sufficient to pass the HIPAA compliance audit?
You can head to the HSS website and download their Audit Protocol. It covers all the areas that should reflect in your HIPAA compliance checklist. However, if you feel this task is beyond your capabilities, consider that many consulting services will cover the paperwork for a fee.
What happens if you fail a HIPAA audit?
The consequences will depend on the severity of the violations. Your audit report should list minor infractions, and often you'll have to provide evidence of the actions taken to protect the data. However, major offenses can make you liable for penalties.
What HIPAA audit focuses on the most?
HIPAA audits address all aspects of HIPAA compliance, covering administrative practices, physical security setup, data breach action plans, and other technical measures to keep PHI safe.
What are the most common HIPAA violations?
Most common HIPAA violations result from the lack of employee awareness and flaws in internal security practices. PHI data could be accidentally shared outside the company even if the top security precautions protect it.
How can NordLayer help?
NordLayer's HIPAA-compliant solutions make it easier to comply with HIPAA requirements without advanced setups or long deployment. Secure every endpoint in your organization, locking down essential apps and databases while keeping user-friendly access. Contact our team and learn how your organization can benefit from the Zero Trust and SSE solutions.
This article has been prepared for general informational purposes and is not legal advice. We hope that you will find the information informative and helpful. However, you should use the information in this article at your own risk and consider seeking advice from a professional counsel licensed in your state or country. The materials presented on this site may not reflect the most current legal developments or the law of the jurisdiction in which you reside. This article may be changed, improved, or updated without notice.
Disclaimer: This article is for informational purposes only and not legal advice. Use it at your own risk and consider consulting a licensed professional for legal matters. Content may not be up-to-date or applicable to your jurisdiction and is subject to change without notice.