Zero Trust methodology requires authenticating every user trying to get into the organization’s network. The Zero Trust architecture assumes no internal perimeter is safe and carefully oversees the network’s access permissions. The process is made possible by following the core principles of Zero Trust security.
Key takeaways
- Zero Trust security assumes that no network is inherently safe and requires authentication for every user and connection.
- Traditional perimeter-based security is becoming increasingly outdated due to increasing IoT devices and insider threats, with Zero Trust architecture offering a more dynamic solution.
- To enhance security, Zero Trust limits employee access to only necessary resources, thus minimizing potential breaches by applying least privilege access.
- The Zero Trust model uses automation for efficient authentication and response, and dynamic policies tailored to organizational risks.
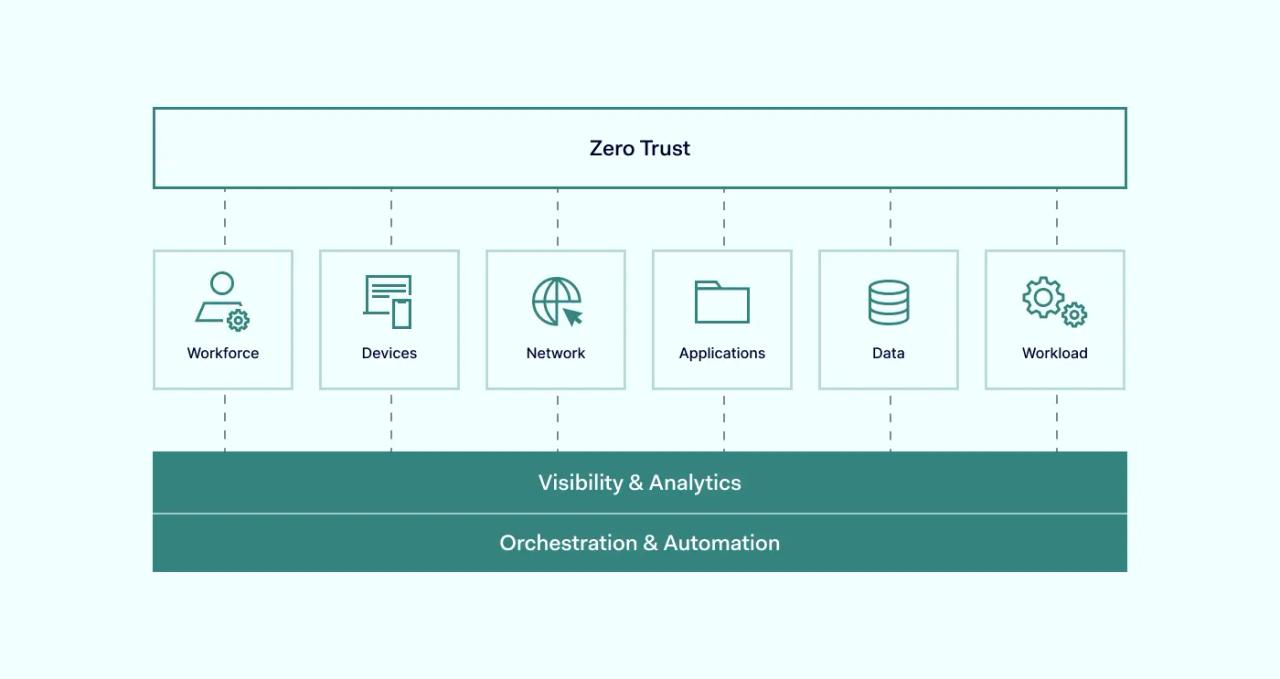
- Key pillars of Zero Trust include workforce, device, workload, network, data security, visibility and analytics, and automation and orchestration.
- Zero Trust is a comprehensive framework guiding IT security, not just a product or specific protocol.
The Zero Trust approach
The Zero Trust method responds to current IT security challenges when users connect from on-premises and outside. It facilitates network management when its scope is too huge to trust connections that passed a single layer of authentication. This is where Zero Trust architecture truly excels—working wonders for remote employees’ authorization and controlling access to hybrid cloud environments.
For this reason, its gaining traction and is set to replace traditional perimeter-based security models in organizations. These were used to protect the devices and users directly connected to the organization’s LAN, considering it protected from external threats. However, the rise of IoT devices over which network administrators have little to no control and the rising dangers of insider threats changed the cybersecurity landscape. Zero Trust solves this problem by denying every connection unless it’s verified and reauthorized.
However, just denying everyone is an oversimplification. Transitioning to the Zero Trust security model is a multi-level process that requires thorough planning. Zero Trust fundamentals should also be considered against the backdrop of a real business network.
What are the core principles of Zero Trust?
Zero Trust principles were outlined in NIST (National Institute of Standards and Technology) Special Publication 800-207. It’s widely accepted as the most neutral and adaptable standard for any organization that wants to increase its cybersecurity status.
Here are the main principles that the publication outlined.
Continuous verification
The zero Trust approach discards the idea of safe internal and unsafe external networks. All networks must be considered untrustworthy regardless of their location, as threats could be lurking in all of them. The focus should shift to the connections themselves and find ways how each could be verified before granting access.
Therefore, the Zero Trust approach requires inspecting every incoming connection and asking for authorization. That way, your employees may have to authenticate more frequently, protecting the enterprise from more threats. While it is a less conventional approach, the price of a data breach is too high to compromise your cybersecurity.
Limit the blast radius
The assumption that your employees are one of the main threats to your cybersecurity is one component of the Zero Trust method. Employee data mismanagement is a serious risk that can bypass even your cutting-edge cybersecurity measures. It’s also very easy to overlook due to the huge scope of internal data and the number of employees, especially in large organizations.
For this reason, Zero Trust recommends granting only limited access to every employee. Using least privilege access, employees should only be given access to the resources needed for their job. This limits employees’ privileges, but it also contains the damage that could be caused if their credentials were exposed.
Automate context collection and response
Zero Trust encourages security streamlining and can be made more effective by automatizations. User-approved log-ins aren’t a viable option if every user needs to be authenticated and reauthorized. This can be automated by analyzing specific connection traits as an additional precaution. If the user connects from a different location and its device’s ID doesn’t match, it can be automatically detected.
However, detection is only half the battle. Upon identifying an anomaly, the system must respond swiftly—denying access and alerting IT administrators. Automated responses help maintain network integrity, allowing human intervention only for more complex cases. Organizations should choose the best ZTNA solutions to automate responses quickly and accurately.
Resource-centric protection
Zero Trust shifts away from the traditional method of network segmentation to focus on safeguarding individual resources. Rather than assuming that all devices within a specific network zone are trustworthy, each asset, service, workflow, and account must be independently secured and verified.
This principle is crucial in today's interconnected environments, where resources may exist across various locations and platforms, such as cloud environments. The goal is to ensure that security policies follow the resource wherever it goes, protecting it from unauthorized access and potential threats, regardless of its network environment. By treating every resource as vulnerable, organizations can enhance protection and minimize risks.
Device and user authentication
In the Zero Trust model, continuous device and user authentication is essential to prevent unauthorized access. This principle recognizes that traditional security models, which rely on network location or physical presence to determine trust, are no longer sufficient. With the rise of remote work, BYOD (bring-your-own-device) policies, and cloud-based services, device and user authentication must be consistently applied, regardless of where a user connects from.
Each session requires validation to ensure that credentials and devices are secure. By employing rigorous and continuous verification, Zero Trust eliminates any assumption of implicit trust, providing a stronger defense against potential breaches and compromised credentials.
Implement dynamic policies
Automation and authentication requirements have to be built on a solid foundation of well-defined security policies. These policies serve as the blueprint for your cybersecurity strategy, providing a clear overview of how security measures will be implemented and managed.
To determine how much flexibility or strictness your policies should have, you must assess the risks specific to your organization. For instance, if you handle sensitive, regulated data, you'll need to introduce stricter controls. The industry you operate in can also play a major role in shaping these policies. Careful evaluation of these factors will help tailor Zero Trust security to your company’s unique needs.
Foundational pillars of Zero Trust Security
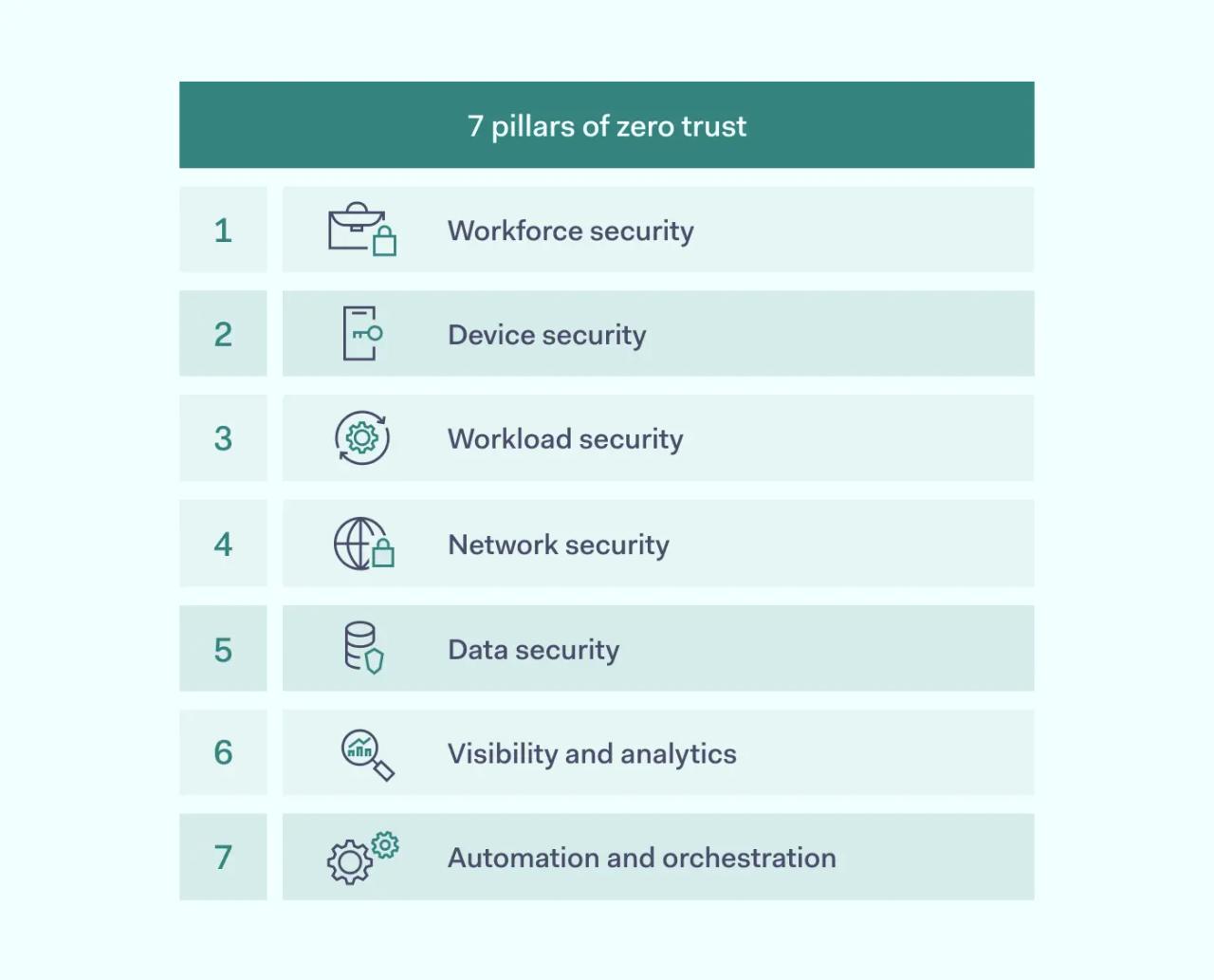
It’s important to realize that Zero Trust isn’t a product or a detailed outline of how your cybersecurity should be set up. Zero Trust is a concept that describes how IT network components in an organization should be treated. The framework is composed of a combination of practices that increase the organization’s cybersecurity.
Workforce security
Zero Trust aims to increase internal workforce security via authentication and access control. Each user that accesses the network has to be verified by the standard set by a security policy. This guarantees minimal access conditions and checks for any suspicious data that could pose a risk to the organization if such a connection is allowed. It’s a method to limit the surface area for cyber attacks.
Device security
A well-rounded organization’s security is impossible without strong device security. Allowing unsupervised or unauthorized devices inside your network is playing with fire. Thorough identification and authorization should be applied in all cases to prevent unsecured device access.
Workload security
All work-related IT inventory, from hardware devices to software applications, constitutes the backbone of most modern businesses. Therefore, security is one of the most important aspects of each used IT asset. As unauthorized data collection and tampering are significant threats, workload security is one of the most fundamental Zero Trust pillars.
Network security
As the data leaves users’ devices and is exchanged online, its security is one of the main aspects of adopting the Zero Trust framework. Microsegmentation of an organization’s internal data helps to set clear boundaries and seals sensitive resources from unauthorized access.
Data security
An organization’s data should be classified to know how much sensitive data an organization oversees. The access policies should be adjusted so that only those needing access for their job role could access the most sensitive documents. However, the files should always be stored securely — using encryption while the data is transferred and stored.
Visibility and analytics
Monitoring is a central component of IT security maintenance. It’s a part of the cybersecurity setup that ensures access control and segmentation rules are followed. Some of these policies’ regulations can be automated if predetermined parameters are set. The end goal is to increase network visibility without leaving any unsupervised endpoints.
Automation and orchestration
A network administrator should be able to control organizations’ connectivity from a single dashboard. The point is to have a centralized control hub from which cloud storage and access can be managed.
Zero Trust Security with NordLayer
NordLayer provides Security Service Edge, part of the Secure Access Service Edge framework. The service is founded on the Zero Trust principles, it helps small to medium businesses jump into better cybersecurity.
Ensuring secure remote access from an off-site location and with a strong emphasis on strict authentication and authorization, NordLayer is a powerful cybersecurity addition. As the service is fully cloud-based, it can completely be controlled from the web dashboard without the need for any hardware deployment.
As with all software-only services, NordLayer offers outstanding scalability options. The only deployment actions needed are accepting an invite link from the email and an easy-to-use application download.
Get in touch with our team and discover more about our approach that could improve your organization’s cybersecurity.