One of the most recent cybersecurity trends is Zero Trust. It’s a modern cybersecurity concept stating that threats should be expected from the inside and the outside of the organization. It’s another way of saying you should trust nothing but verify everything. This approach is most prominent in cloud data security but is also gaining traction in endpoint security.
The trickiest part of this equation is that the endpoints are never in the same place for long. This also includes potentially harmful environments, i.e., public hotspots, not to mention homes with several connected IoT devices. This makes Zero Trust architecture for endpoints a critical issue that needs addressing. Here’s how remote employees (and their endpoints) could be secured within the Zero Trust security framework.
Key takeaways
- Endpoint protection keeps devices like laptops and smartphones safe by using cloud technology, which is more effective than older security methods.
- When we use Zero Trust with endpoint security, we make sure to check every user and device before allowing access. This makes our defenses much stronger against various threats.
- By combining Zero Trust and endpoint protection, we make it easier for people to access what they need, lighten the load on our IT teams with automation, and get a better picture of all the devices on our network.
- Adopting this combined approach helps our organization save on cybersecurity expenses and manage things more easily, especially for remote teams. It also helps us follow data protection rules more easily and keep our data safer.
- Opting for a Zero Trust strategy in endpoint security modernizes our defenses, making security management easier and more cost-effective while ensuring our data is well protected. This prepares us better for any future security challenges we might face.
What is endpoint protection?
Endpoint protection relates to the security mechanisms designed to secure devices like laptops, smartphones, and other mobile devices. Essentially, the endpoints’ security is the layer with which users interact directly. Endpoint security systems deployed on the cloud enforce the protection mechanisms themselves.
It’s a night and day difference from the cybersecurity solutions that used to be installed on the endpoints themselves, like antiviruses. Not only did this prove to be a resource hog slowing down the device, but it also heavily depended on pushed updates. The security solution is remotely delivered to every connected device with cloud delivery with endpoint security systems. It’s a much more effective solution against aggressive malware types.
The general rule is that your network will remain secure if your endpoints are protected. Endpoints are the first frontline threat actors will test as they have large attack surfaces and can be severely under-protected. Weak passwords and loose user authentication mechanisms harm an organization’s security.
Modern endpoint protection systems are highly automatized structures capable of monitoring, detecting, and containing various malicious processes. This is ensured by always-online requirements, constantly exchanging device posture with the cloud, and checking for risks.
How Zero Trust works alongside endpoint security
One of the biggest mistakes an organization could make when implementing the Zero Trust security model is believing that the transition to cloud infrastructure will be enough. While cloud security is important, a holistic approach works best when ensuring security is level across the board.
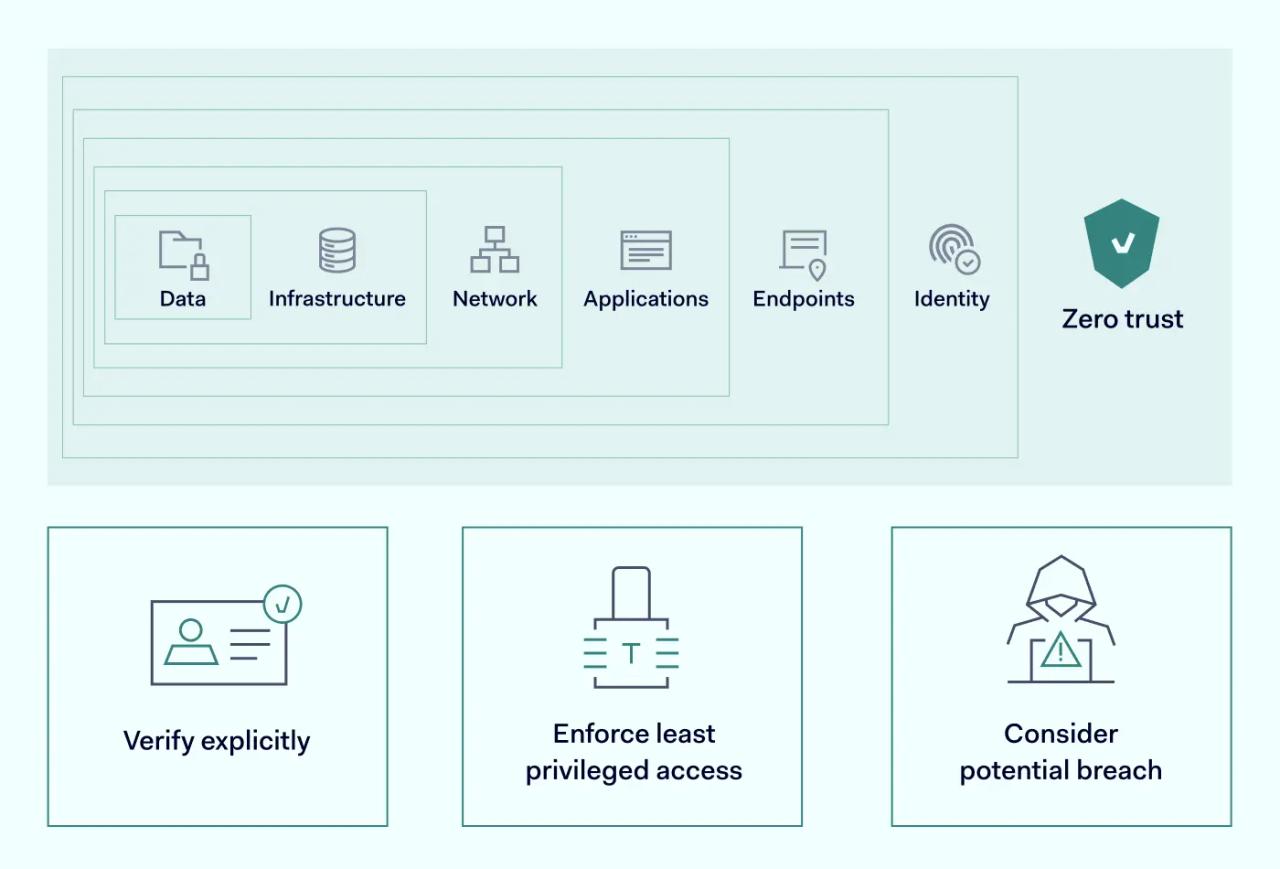
Only focusing on the cloud could mean leaving endpoints unprotected. Therefore, endpoint protection should be one of the key elements of a security strategy. One of the best practices is using various cybersecurity technologies and mechanisms to create several layers of barriers. Endpoint protection should be regarded as one of those barriers that should be secured the most.
Zero Trust as a philosophy should still stand at the forefront of any of your decisions-security wise. This central concept should tie every used technology into a secure ecosystem. Most of its responsibility will depend on your provider selection, especially if you’re building your security model on their framework. Security vendors apply emphases differently, so you should research how it could benefit your unique business case beforehand.
Benefits of an integrated approach: Zero Trust for endpoint
Endpoints are one of the trickiest IT assets to protect. In addition, they also contribute the most to your attack surface size. As your organization’s weakest link, you should make no compromises for their security. An integrated approach between the Zero Trust security model and endpoint protection could be an optimal solution in this case.
Its application would require verifying every device on the network, including guest devices and other devices that employees use to access work materials. The bottom line is that your Zero Trust policy should cover them even if the company doesn’t manage its ownership. This aspect is especially important for an organization implementing bring-your-device policies.
Here’s how interconnecting Zero Trust with the endpoint may address these problems.
1. Unified endpoint access system
Juxtaposing different systems in the periphery of the Zero Trust setup might make things more complicated rather than adopting the same structure across the board. Zero Trust comes with Identity Access Management, meaning that the same user identity needs to be authenticated once to obtain navigation around the network. If your user has permission, they will be able to access everything they should be allowed to access without needlessly passing repeated checks. This streamlines the security, which also benefits the fluidity of your workspace workflow.
2. Helpful management automatizations
As one of the essential Zero Trust components is an extensive monitoring mechanism, this lifts a burden from the shoulders of the IT staff. The system checks the network in real time, looking for signs of issues. It also provides instant alerts to the network administrators who only have to respond to already identified suspicious behaviors rather than find them manually.
The responses to the user’s requests are also streamlined by using the Zero Trust systems. IT administrators don’t need to jump back and forth on help desk requests when users forget their passwords or have issues with application access.
3. Better network assets overview
Zero Trust fundamentals require higher visibility of all devices on the network, including endpoints. Its implementation will need mapping the network itself, cataloging all organization-managed devices, etc.
This should be a much more insightful method, providing more data than conventional endpoint management systems that can’t see everything. On top of that, automated detection and response mechanisms quickly alert if the system spots something odd. That way, complete visibility is combined with better endpoint protection without excluding them from the equation.
4. Cybersecurity solutions consolidation
As the Zero Trust approach can be applied to endpoint management, it helps to drive expenses down. Using a single system for cybersecurity orchestration allows you to free yourself from providers offering a single function. So not only is it cheaper, but it’s also easier to supervise even when your teams are remote.
5. Easier regulatory compliance and higher data security
Since Zero Trust is set on data protection, unauthorized access is very hard. This helps with endpoint security, as well. Following the Zero Trust model, the most sensitive data is never stored on the endpoints. However, access from endpoints has to meet security policies to be allowed, creating a safer ecosystem that is more suited to device protection.
This also makes it easier to stay in line with compliance requirements, as you only need to ensure it’s properly secured in the cloud. Access can be set up with various dynamic controls based on the implemented security policies. They can be set up per user or team without reengineering the whole setup.
Summary
Adopting the Zero Trust model for endpoint security is a smart move for any organization looking to boost its cybersecurity. This method makes things smoother for users, makes managing simpler, helps us see more clearly, cuts down on expenses, and ensures we're following rules properly. It strengthens our defenses and prepares us well for any cybersecurity challenges that might come our way. It's a good answer to today's security concerns.