A VPN (or a Virtual Private Network is a technology initially developed to serve businesses. Its primary function was to provide secure, cheap, and flexible solutions to protect corporate networks. It made work tools and data accessible to the employees and restricted access to everyone else.
Rather than relying on expensive hardware to set up closed-off networks, a VPN connection uses the open internet to safely transfer data via an encrypted tunnel. Since the internet is public by design, encryption serves as a deterrent for rogue agents lurking in the same environment.
VPN technology is not complex, but there are many VPN setups and tunneling protocols from which to choose. All of this can get very technical, so here's a quick rundown of which types of VPN and tunneling protocols are right for your business.
Key takeaways
- Decide between remote access and site-to-site VPN by network setup and user needs.
- Remote access suits individual connections, while site-to-site connects entire networks.
- Focus on secure VPN protocols like WireGuard, L2TP/IPsec, and OpenVPN for better encryption.
- Two VPN types:
- Site-to-site VPN
- Remote access VPN
- VPN protocols:
- IPSec
- L2TP
- PPTP
- SSL and TLS
- OpenVPN
- SSH
- WireGuard (NordLynx)
Different types of VPNs and when to use them?
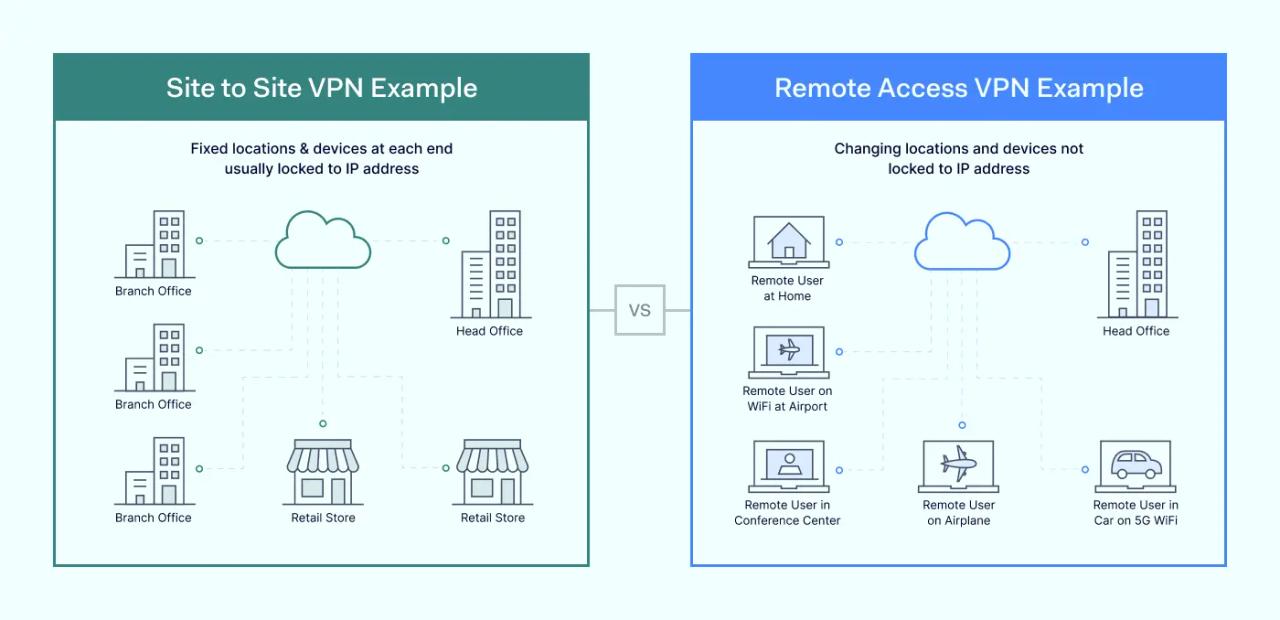
Remote Access VPN
Remote access VPN is a temporary encrypted connection between the business's data center and the user's device. It becomes active only when the user enables it. Otherwise, it doesn't have a permanent link. Businesses primarily use this type to securely access the applications and data in a central hub via a VPN tunnel. You can think of it as a VPN connection making a secure pathway from your device to access sensitive documents or company materials on the other end.
The main drawback of this method is that the applications you're using are hosted from the main headquarters now very rarely. Most organizations adopt software as services (SaaS) solutions — universally hosted somewhere else, using enormous data centers. Therefore, setting remote access VPN up might not be the most practical solution as in those cases, the data would be going from users' device to the central hub, to the data center and back. So not only this could introduce severe bottlenecks and degrade network performance.
Although, this solution can be good when you need it for specific self-hosted applications or very classified documents that you don't want hosting elsewhere. Though, it's worth noting that you should plan depending on the number of users accessing them. The more of them you'll have, the more capable hardware you'll need.
Site-to-site VPN
Site-to-site VPN is a permanent connection between multiple offices to create a unified network that is always on. It needs separately configuring for both networks, and it works best for cases when you have multiple remote sites. It can be configured on-premises routers or on firewalls.
This solution won't help you much if your users want to connect from home. Administrators usually don't allow connections from networks they have no control of for safety reasons. Essentially, they're sacrificing accessibility in favor of security.
On the upside, it's one of the cheapest methods to merge separate networks into a single intranet. Every single device can function as if it's on the same local area network facilitating data exchanges and making it closed off from snooping attempts from the outside.
Choosing the right VPN type for your business
Choosing the right VPN depends on your network and how users access resources. A remote access VPN works well for businesses with employees who need secure, temporary access to a central network. It’s ideal for accessing internal tools, sensitive files, or specific applications from anywhere. However, it can create bottlenecks when connecting to cloud services.
Site-to-site VPN is better for businesses with multiple offices that need a unified, permanent network. It allows all devices at different locations to act as if on the same local network. It ensures secure data transfer between sites but lacks flexibility for remote users. Tailor either option to your infrastructure and users' needs.
Most common VPN protocols
VPNs are using tunneling protocols that act as rules for sending the data. It provides detailed instructions on packaging the data and what checks to perform when it reaches its destination. These different methods directly affect the process speed and security. Here are the most popular ones.
Internet Protocol Security (IPSec)
IPSec is a VPN tunneling protocol that secures data exchange by enforcing session authentication and data packet encryption. It is twofold encryption — the encrypted message sits in the data packet, which is further encrypted again. IPSec protocol combines with other protocols for added security and frequently utilizes Site-to-site VPN setups due to its high compatibility.
Layer 2 Tunneling Protocol (L2TP)
L2TP works by generating a secure tunnel between two L2TP connection points. Once established, it uses an additional tunneling protocol to encrypt the sent data, i.e., IPSec. L2TP's complex architecture helps to ensure high security of the exchanged data. It's another popular choice for Site-to-site setups, especially when higher security is needed.
Point–to–Point Tunneling Protocol (PPTP)
PPTP is another tunneling protocol that creates a tunnel with a PPTP cipher. However, since the creation of the cipher in the '90s, the computing power has increased exponentially. Brute-forcing the cipher wouldn't take too long to crack it to reveal the exchanged data. For this reason, technology rarely uses this cipher — a replacement containing more secure tunneling protocols with more advanced encryption is preferable.
SSL and TLS
Secure Socket Layer and Transport Layer Security protocols are the same standard that encrypts HTTPS web pages. That way, the web browser acts as the client, and user access is limited to specific applications rather than the entire network. Since almost all browsers come equipped with SSL and TLS connections, no additional software is usually required. Usually, remote access VPNs use SSL/TLS.
OpenVPN
OpenVPN is an open-source enhancement of the SSL/TLS framework with additional cryptographic algorithms to make your encrypted tunnel even safer. It's the go-to tunneling protocol for its high security and efficiency. Though, compatibility and setup can be a bit hit or miss as you won't be able to install it natively on many devices to form router to router VPN networks. So, the performance may vary.
It comes in User Datagram Protocol (UDP) or Transmission Control Protocol (TCP) versions. UDP is faster because it uses fewer data checks, while TCP is slower but better protects data integrity. As a whole, OpenVPN is a well-rounded and secure tunneling protocol and is popular for both remote access and site-to-site virtual private network uses.
Secure Shell (SSH)
Like the other option, SSH generates an encrypted connection and allows port forwarding to remote machines via a secured channel. It is useful for accessing your office desktop via your laptop at home. While it does add additional flexibility, SSH channels should always be under close supervision to provide a direct entry point for breach. That's why it's a better fit only in remote access setups.
Wireguard
The most recent widely available tunneling protocol is less complex but much more efficient and safer than IPSec and OpenVPN. It relies on highly streamlined code to squeeze the best possible performance with a minimal margin of error. While it still is in the early adoption stage, you could find offices using Site-to-site connections based on Wireguard. There even are proprietary WireGuard implementations like NordLynx.
Which VPN protocol is the best for your business?
IPSec | L2TP | PPTP | SSL/TLS | OpenVPN | SSH | WireGurad |
|---|---|---|---|---|---|---|
Secure | Secure | Fast | Widely used | Highly configurable | Allows port forwarding | Highly secure |
Flexible | Widely available | Built-in client | Maintains data integrity | Open source | Supports key-based authentication | Open source |
Widely supported | Easy to set up | Easy to set up | Required for compliance | Highly secure | Enables secure file transfer | Lightweight design |
A VPN protocol should be the last thing off the list that you should be choosing. First, you should choose what kind of setup you should be using : remote access or site-to-site. It should narrow down your list of options. Though, it's worth noting that neither remote access nor site-to-site are the only possibilities to set up an Internet-based VPN.
After carefully considering your business needs and setup method , you can start l ooking into your network needs. Look into your risk model, what traffic load you would expect, what data you want to make available, and whom. The clearer the picture, the easier it will be to drive the setup cost down and pick the right tunneling protocol for your specific case.
As a rule of thumb, Wireguard, L2TP, SSL/TLS, and OpenVPN will be the safest options for remote access setups. The best VPN protocols can depend entirely on your hardware from site-to-site perspective. I.e., if you're already using routers that natively support OpenVPN, it might make more sense to use them rather than throwing them out to get ones that can handle Wireguard.
FAQ
What is the primary difference between remote access VPN and site-to-site VPN?
Remote access VPN connects individual users to a remote network, while site-to-site VPN connects two entire networks together.
Why should businesses monitor SSH channels?
Businesses should monitor SSH channels closely to ensure security, detect unauthorized access, and maintain the integrity of data and systems.
Which VPN protocols are recommended for remote access setups?
Recommended VPN protocols for remote access setups are: OpenVPN, L2TP/IPsec, and IKEv2/IPsec.