"I see that Jason actually made the pull request to have WireGuard included in the kernel. Can I just once again state my love for it and hope it gets merged soon? Maybe the code isn't perfect, but I've skimmed it, and compared to the horrors that are OpenVPN and IPSec, it's a work of art." — Linus Torvalds, creator of the Linux kernel, said this about WireGuard in 2018. Since then, WireGuard has gained popularity, with many fans using it as it is and companies building products around it. Let’s look at what WireGuard is.
WireGuard protocol definition
WireGuard is an open-source protocol for creating secure Virtual Private Networks (VPNs). It encrypts data within a Wireguard tunnel using advanced cryptographic methods. Originally built into the Linux kernel in 2020, it is now available for many operating systems.
How does Wireguard work?
The protocol was developed by the sole security researcher, Jason A. Donenfeld, who was experimenting with existing options. As most of them had poor performance and were hard to set up, the natural conclusion was to simplify the whole architecture. Therefore, WireGuard was intended to be a streamlined VPN protocol that could outperform the competition and provide much better network security.
WireGuard VPN protocol strongly relies on various open-source cybersecurity technologies incorporating them into its architecture. As one of the most recently developed VPN protocols, it has all the bleeding edge bells and whistles you would expect from a modern solution.
- WireGuard VPN relies on ChaCha20 for symmetric encryption
- It uses the Poly1305 hash function for authentication
- The protocol applies Curve25519 elliptic curve for the Diffie–Hellman agreement protocol
- SipHash24 and BLAKE2 functions are used for private keys
- The keys are derived using HKDF
That said, there's a wide variety of setups across all WireGuard VPN architecture implementations. What remains constant is that its lean codebase makes it a very high-performing VPN protocol.
In addition, its connectivity handshakes take place each minute instead of the content of exchanged data packets. This means the keys always rotate, ensuring a perfect forward secrecy mechanism.
The keys and handshakes are always updated, renegotiating their status when required. Data packet loss during handshakes is minimized using a separate packet queue per host. This also contributes to the uninterrupted performance of clients.
Pros of WireGuard VPN
Here are the most important advantages of the WireGuard VPN protocol.
High-performance
Fewer code lines help WireGuard VPN to achieve great performance. Due to high-speed cryptographic primitives reaching 1000Mbps and using Linux kernel modules, it provides fast performance and bandwidth. This combination works wonders on portable devices with weaker hardware, obtaining the best possible performance.
Easy to set up
WireGuard VPN is appealing to network administrators because it doesn't require infrastructure based on certificates. WireGuard uses only public keys for identification and encryption, so there's no need to worry about certificate maintenance.
Security
WireGuard VPN protocol uses cryptographic key routing to provide highly secure links between endpoints and VPN servers. For this reason, it's possible to use public encryption keys or industry-standard AES-256 ciphers.
Codebase
Before WireGuard VPN, it was considered normal for tunneling protocols like OpenVPN to use 70,000 lines of codes which could even add up if additional cryptographic libraries are added. WireGuard radically simplified the underlying structure using only 4000 lines of code, which is much easier to troubleshoot.
Platform support
WireGuard isn't exclusively locked to any platforms, which makes it more accessible than some proprietary technologies. Its open source also makes it much more friendly when setting it up on devices that don't support the WireGuard interface natively.
Cons of WireGuard VPN
However, WireGuard has many disadvantages, as well.
Development stage
Being the most recent VPN protocol doesn't come at a price. In this case, while it's available for public and commercial use, there are still many things to iron out before WireGuard reaches maturity. WireGuard VPN protocol has yet to go through several cycles of security audits to be an alternative without any shadows of doubt.
Privacy concerns
WireGuard works by keeping an internal ledger on the VPN servers so that the data packets wouldn't be mixed among its users. In principle, this can severely threaten the user's privacy as this is one of the key vulnerabilities that an intruder could target. For this reason, VPN service providers need to work around this problem with custom solutions.
Used port
The default implementation of WireGuard VPN protocol uses UDP port 51820, something that most competent network administrators will close on public networks for security reasons. The default port used by HTTPS, port 443, which is WireGuard, doesn't support the one left open for general Internet connectivity.
Stability issues
As with most of the experimental software, you can expect a lot of stability issues with WireGuard. There can be strange outages or performance drops, which are common due to the recent rollout. However, as its development progresses, there should be fewer performance hiccups.
Infrastructure requirement
To maximize its security measures, WireGuard will need the infrastructure adapted to function properly. If you're planning to set it up independently, you'll need to look into separate servers and key management systems to make the most out of this VPN protocol.
How can WireGuard be used?
As WireGuard is a tunneling protocol, its use mainly consists of various applications within the VPN ecosystem. Here are the principal use cases for WireGuard.
Remote site connectivity
One of the areas in which WireGuard is starting to be extensively used is connecting internal networks between remote sites using site-to-site configuration. This comes in handy when linking branch offices to HQ or meshing all the networks of globally distributed departments.
This would require setting up a physical WireGuard server at each location and configuring access rules so that only branch network connections would be allowed. In such a setup, the server could be the office's router or a multi-purpose stack that's also used for hosting applications.
The downside of such a setup is that the hacker must only breach one of the connected branches to obtain full access to the entire network. This is extremely dangerous as it allows the hacker to quickly escalate with a direct link to the most sensitive documents.
Remote access
Another potential WireGuard use case is allowing an isolated user access to the internal network remotely, a method also called point-to-site. This requires setting up WireGuard architecture on the same internal network that will be accessed. Although, frequently, the same setup is software-only.
The main benefit of such a setup is that it gives network administrators much better control over who can access specific networks. This becomes especially relevant when internal resources are shared with external contractors or third parties. A layered mechanism helps to keep external connections at a distance from confidential data. Finally, access can be easily revoked without disrupting the system when access is no longer needed.
Establishing a Zero Trust network
While Zero Trust is a much broader subject, one of its practical applications, Zero Trust Network Access (ZTNA), requires a secure communications channel. This is where WireGuard comes in, as it can be used as an underlying technology for setting up secure access.
The whole infrastructure in this use case relies on endpoints equipped with software that could use WireGuard. In addition, only WireGuard connections should be allowed when connecting to the company's servers. This creates a much better-controlled environment in which the device, user identity, and exchange channels are used to achieve the Zero Trust model.
While this is a much more complex method to set up and administer, it's one of the most popular and secure ways to make safe remote access possible. This gives a lot of security to the administrators, who can revoke access anytime.
Technical details of WireGuard Protocol
From a technical point of view, WireGuard is a collection of various freely available solutions compiled into a single implementation. One of its key traits is that all incorporated components are streamlined to fit within 4000 lines of code. For comparison, the likes of IPsec or OpenVPN can stretch those lines up to 600,000 lines. These improvements are direct contributors to high-speed network exchanges that the WireGuard protocol is known for.
A single individual could look at WireGuards code and develop improvements or detect misconfigurations, while the same can't be said about other popular tunneling protocols. In addition, this lean framework shrinks the attack surface with fewer possibilities to find unknown vulnerabilities that the bad actors could exploit.
How can you take advantage of WireGuard with NordLynx?
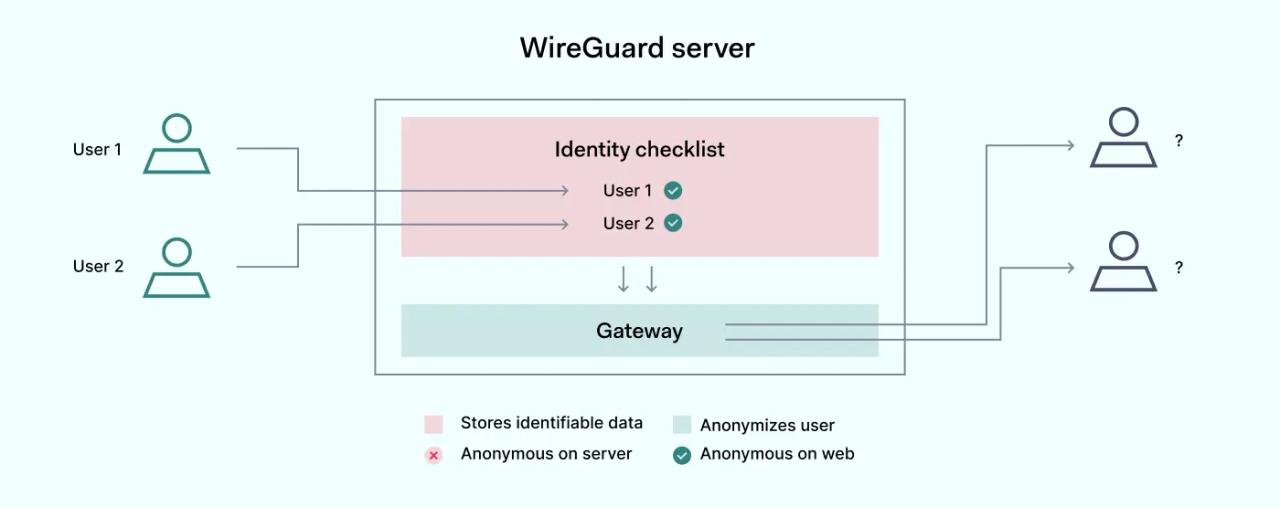
As it was mentioned previously, WireGuard is still in its infancy stage. It can still function as a building block to develop more complex solutions. The general process is taking the source code of WireGuard and developing additional functionalities on top of it. This can combine the best of both worlds: the strong foundation and niche functionalities that could be relevant in highly specific use cases.
NordLynx is a great example of that, using the WireGuard codebase. It's an improvement in maintenance, faster connections, and a stronger security setup than unmodified versions.
NordLynx solves some of the built-in WireGuard flaws by adding more robust security measures. This proprietary VPN protocol uses a double Network Address Translation system. It allows the establishment of a secure NordLynx connection without identifiable data. This means that the ledger can't be exposed or exploited, solving one of the biggest drawbacks of default WireGuard.
Summary
WireGuard is a new-generation VPN protocol that radically streamlines secure communication for its end users and network administrators. Making use of various advanced cybersecurity technologies, it provides unparalleled encryption and crypto-key routing to secure end-to-end network exchanges.
While the VPN protocol is still in its early development stages, it already rivals current tunneling protocols regarding security and lightning-fast internet connection speeds. Due to this reason, WireGuard sees increased use in business contexts as organizations are looking into ways to take advantage of WireGuard's benefits.
Some WireGuard implementations also can be heavily modified to increase the default functionalities, like NordLynx tunneling protocol. Using it can be a key to a more modern cybersecurity setup for businesses of diverse sizes seeking to improve their cybersecurity resilience.