Picture this: a coworker saves sensitive data on a personal device. They don’t mean harm, but that decision opens the door for cyber threats. Insider threats are real and more common than you think. Negligence or bad intentions can lead to data breaches or downtime. Let’s break down what insider threats are and how to manage them.
Insider threat definition
Insider threats are security risks that come from within organizations. They occur when trusted individuals misuse their access to steal or damage confidential data. These threats can result in cyber-attacks, data breaches, or other serious risks. Attackers may include employees, former staff, or third-party providers with privileged access.
Many factors lie behind insider threat attacks. Staff could be angry at their employer, seek financial gain, or have political intentions. Sometimes, employees work for governments, rival companies, or even terrorist organizations.
In every case, a trusted network user with authorized access becomes a significant network security threat. As a result, security counter-measures focus on limiting user privileges, training staff, and managing user accounts to prevent access when employees leave organizations.
Types of insider threats
Companies can only prevent insider threat attacks if they understand the most common varieties. Insider attacks emerge from many sources. Any of the varieties below could affect your organization, and mitigation plans are vital.

Deliberate threats
In these incidents, threat actors intentionally commit cyber crimes against their employer or business partner. These threats are often related to conflicts or disputes within the workplace. For example, staff may act when managers overlook them for promotions.
Individual threat actors include collaborators who work directly with external criminals or competitors to steal information. However, employees can work as lone wolves, following personal vendettas without external assistance.
Malicious insider threats
This type of insider threat is slightly different. Outsiders are professional criminals who implant themselves within target organizations, often via standard recruitment processes. Malicious insiders use their positions to inflict damage or steal critical assets for financial gain.
Collusive insider threats
This threat type involves collaboration between malicious insiders and external threats, generally members of criminal groups. Attackers may include technicians, customer service officers, or HR professionals. Combining roles enables attackers to conceal their activity and cause extensive disruption.
Accidental threats
Employees may unintentionally remove sensitive information from network resources. They may expose laptop screens or mobile devices in public, leading to credential theft. Staff could drop physical documents in public places, discuss confidential matters accidentally, or open malicious attachments sent with phishing emails.
Unintentional threats can occur via simple human error. However, individuals may also see themselves above security rules. Arrogant employees may expose data by ignoring proper security practices, underlining the need for training and robust disciplinary procedures.
Third parties
Insider threats can also occur via third-party organizations. For instance, IT maintenance companies or cloud service providers may have access to sensitive data. They may intentionally steal data or expose it to outsiders through lax security measures.
How to detect an insider threat
Insider threat detection is not always easy. Security teams cannot know what employees think about or who they meet outside the workplace. Sometimes, you cannot detect insider threats before they act. Other times, insider threat detection is possible.

Common indicators of a raised insider threat level include:
- Malware spikes. Sudden increases in malware detection can result from insider threats. Employees may click on malicious emails accidentally or deliver malware via external devices. Security teams can trace the source of infections and establish whether internal actors are responsible.
- Unexplained password changes. Internal attackers may access sensitive information by posing as colleagues. When employees report unexplained password changes, check the time and identity of users who requested the change. A malicious insider could be responsible.
- Installation of unauthorized software. Malicious insider threats often leverage externally supplied tools to extract data. Security teams should authorize all software installed on network devices, and any unauthorized installations require investigation.
- Repeated access requests to sensitive data. Malicious insiders may seek access to data beyond their privilege level. Network monitoring tools can track unauthorized requests. An insider threat will often generate a pattern of requests for valuable data.
- Changes to security settings. Always investigate incidents involving changes to firewall, anti-malware, or access management tools. Sophisticated insiders may change settings to escalate their privileges.
- Backdoor vulnerabilities. Attackers can leverage backdoors within existing software or introduce malware agents to create network backdoors. Scan for vulnerable endpoints and regularly update applications to block access.
- Security incidents involving partners. Third parties used by your organization may be involved in cybersecurity incidents. When this happens, all organizations that work with the third party could be exposed to external threats.
- Workplace disputes. The insider threat level tends to rise during periods of conflict within organizations. For example, employees may steal client data when they are made redundant or move to a rival company.
Insider threat examples
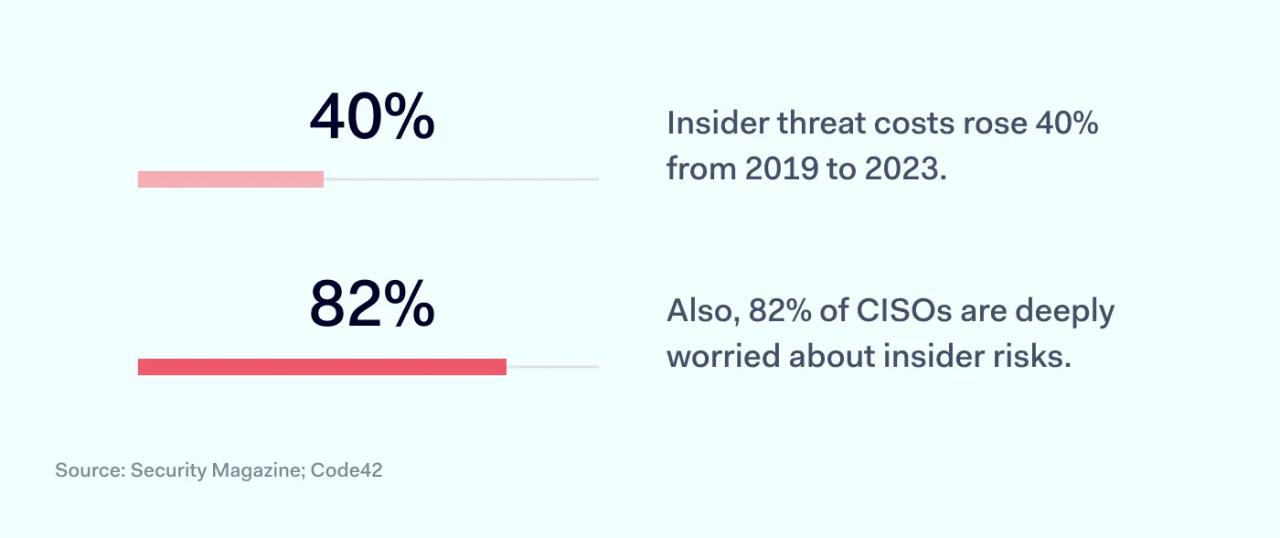
Insider threats are a significant concern for information security teams. Around 60% of data breaches arise from insider activity. The cost of insider threats rose 40% between 2019 and 2023, while 82% of CISOs report being extremely worried about threats from within.
A quick look at three real-world examples shows why security professionals are so worried.
CashApp: Deliberate sabotage by a disgruntled worker
In 2022, the stock trading app CashApp reported the exposure of 8 million customer records, including stock trading histories, portfolios, and customer names. The breach occurred when a departing employee used their privileges to download sensitive data—a great example of why secure offboarding is so important.
Tesla: Blurring the boundary between insider threats and whistleblowing
In 2023, a pair of Tesla employees leaked the personal data of over 100,000 current and former employees to a German newspaper. They also leaked data about crash reports, casting doubt on the automaker's safety record.
In this case, the insider threat appeared to stem from poor whistleblowing processes inside the company. Employees went public to expose dangerous behavior instead of using internal channels.
Boeing: Accidental exposure with potentially huge consequences
In 2017, a Boeing employee was given a seemingly simple spreadsheet task and decided to send the sheet to his wife (who was not on the Boeing payroll) for formatting advice. Unfortunately, the spreadsheet contained the social security numbers of 36,000 company employees in hidden columns.
This incident was not catastrophic. Boeing discovered the breach and notified regulators. However, it's a vivid example of how an accidental act can turn an innocent employee into an insider threat.
What are the risks associated with insider threats?
Companies often focus on malware, credential attacks, or man-in-the-middle attacks, but insider threats pose a similarly significant risk to cybersecurity and financial health. Policies to mitigate internal network security threats are critically important for several reasons:
Firstly, insider threat attacks bring significant security risks. Insiders may infect network devices with malware, leading to data extraction, ransomware attacks, or performance issues. Attackers may delete or corrupt data or risk identity theft for fellow workers and customers.
Insider attacks bring a business risk, too. Employees often remove sensitive information about clients or products. They may sell this data to competitors or take information to rival businesses and use it to steal customers.
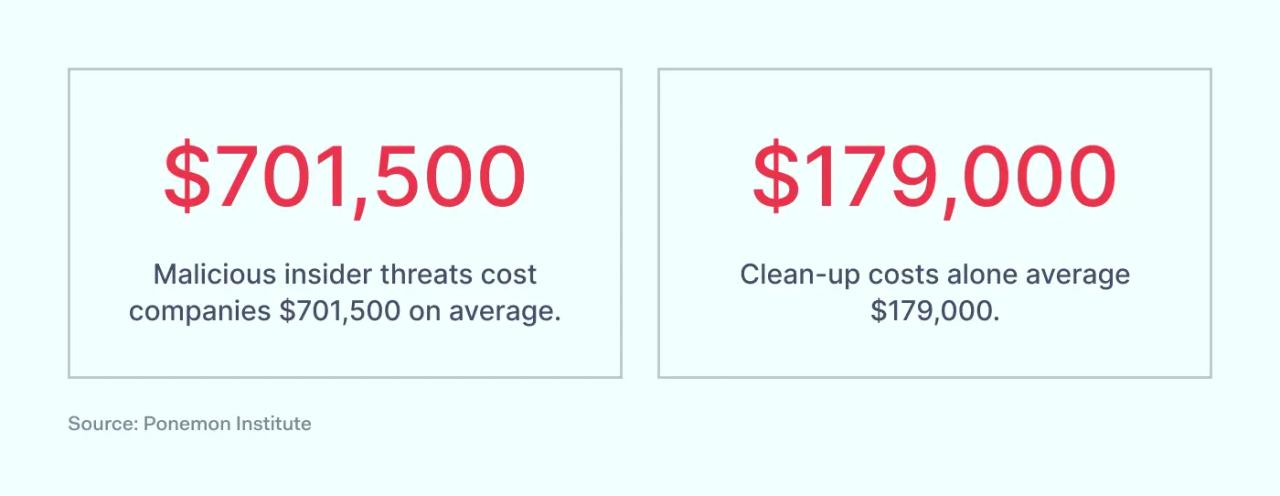
There is also a financial risk. Insider threats are expensive. On average, malicious insider threat incidents cost companies $701,500. Clean-up costs alone for insider threats average $179,000. These numbers do not include regulatory risk, which can magnify the cost exponentially.
Insider threats also carry a reputational risk. Customers avoid businesses that expose data. Potential employees may choose not to join organizations affected by malicious insiders or whistleblowing incidents.
How to protect against insider threats
Insider threats differ from other cybersecurity risks as they come from trusted individuals with authorized access. Unlike malware, these threats involve intentional or accidental human actions. Controlling how employees or third parties operate is often harder than removing Trojans or worms. However, there are ways to prevent insider attacks.
Implement insider threat detection
Companies can detect insider attacks by monitoring user activity and data access patterns.
- Failed access requests to confidential data may signal an insider threat.
- Changes to normal user activity can trigger alerts and prompt security staff to investigate.
- Device checks may identify logins from unusual locations. For instance, ex-employees may access networks from their home without doing so in the past.
NordLayer helps monitor and control network access to protect resources. The Device Posture Security tool checks all access requests, allowing only approved devices. It alerts security teams if ex-employees or third parties use personal devices to connect. It also detects unusual activity, like connections from unexpected locations.
Activity monitoring tools track connections to Virtual Private Gateways, helping spot suspicious behavior, such as access outside business hours.
Respond to incidents with investigations
Ensure rapid responses when network monitoring tools deliver insider threat alerts. Even brief delays can compromise security, giving malicious actors time to extract data.
Thoroughly investigate users connected to alerts, verifying their credentials and privileges. If necessary, request information about their access patterns and network activity. Users should be able to provide justifications for accessing sensitive data. If not, launch disciplinary processes.
Manage access to limit user privileges
Insider threats leverage authorized access to steal data or damage networks. Companies must limit authorized access to individuals with legitimate business reasons. Systems should revoke privileges when employees leave and de-escalate temporary administrative privileges.
NordLayer can help you achieve better network access control. Tools like Cloud Firewall and Device Posture Security support implementing Access Control Lists (ACL). These tools let security teams segment network access rights to limit exposure. Users get access to necessary resources while restricted from other sensitive assets. This reduces the risk of malicious insiders causing damage.
Train staff to keep data secure
Finally, security training can prevent many unintentional insider threats. Ensure staff know how to identify phishing emails and fake websites. Explain the meaning of secure data handling and ways to prevent data exposure. Test employees regularly to refresh their knowledge and general awareness.
Companies cannot completely avoid insider threats. Sometimes, disputes are unavoidable, and accidents happen. However, every organization should practice robust risk management and use security measures to cut insider risks.
