Securing critical data is a constant battle. Both external actors and disgruntled insiders seek access to valuable data to extract, transfer, and sell. With multiple data exfiltration techniques available, securing information is an ongoing challenge.
This article will explain what data exfiltration is (and what it is not). We will introduce exfiltration techniques and real-life examples before providing practical detection and prevention tips.
Data exfiltration meaning
Data exfiltration is the unauthorized removal of sensitive data from network servers, workstations, or cloud resources. Criminals typically exfiltrate data via cyber-attacks, transferring locally held data to third-party locations for storage or sale on the Dark Web.
However, insider threats can also remove data to sabotage businesses or for their own profit. In all cases, companies need to minimize data exfiltration risks.
Differences between data exfiltration, data leakage, and data breaches
Data exfiltration is part of a wider category of threats related to data security. For instance, you may be familiar with the terms data leakage and data breaches. These terms refer to slightly different cybersecurity concepts, and understanding the differences is critically important.
In simple terms, data exfiltration is a deliberate attempt to obtain confidential data. Data leakage is generally unintentional and results from employee errors and misconfigurations. A data breach refers to the unauthorized access, acquisition, disclosure, exposure, compromise, or loss of control over protected or sensitive data.
The table below summarizes the main differences to put data exfiltration into context:
| Intention | Root cause | Scope | Technique |
|---|---|---|---|---|
Data exfiltration | Always deliberate. | Malicious threat actors. | Intentional data theft. | Targeted cyber-attacks. |
Data leakage | Usually unintentional. | Avoidable data security failures or human error | Accidental data exposure. | Human error/misconfiguration. |
Data breach | Can be deliberate or accidental, depending on context. | Variable. Assessment requires a thorough incident investigation. | All forms of unauthorized transfer of private data. | Variable. |
How does data exfiltration happen?
Data exfiltration incidents have two main causes: external attacks and insider threats. Security strategies should have a dual focus, blocking access attempts from unauthorized outsiders and managing privileges to restrict user access to sensitive data.
Insider threats often happen when security teams assign excessive freedom to trusted users. Employees may become unhappy with their company or seek to profit from confidential client information. Exfiltrating data is relatively simple if the employee has free access to data.
However, insider threats can also be unintentional. For example, healthcare employees may leave a computer screen visible to clinic visitors. Or they may email sensitive data to the wrong contacts. Accidental exposure is commonplace. Without continuous training, it is also difficult to prevent.
External threats are potentially more damaging due to their professional and targeted nature. They tend to follow a similar template.
External attackers infiltrate networks via phishing techniques or credential stuffing attacks. Malware deployed on compromised devices spreads throughout the network, seeking high-value data. This process can occur rapidly or over months or years, until attackers are discovered or have completed their exfiltration actions.
Types of data exfiltration
The process outlined above is simplified. Real-world cyberattackers employ a diverse range of tools and tactics to compromise networks and extract valuable data. Criminals also have many potential targets. All require specialized protective measures. Common types of data exfiltration include:
Phishing or social engineering
Social engineering employs manipulative emails or other means of communication. Attackers trick targets into downloading malware-infected attachments or visiting websites designed to steal credentials.
Clicking on malicious attachments automatically executes malware or ransomware. Malware agents embed themselves on the network, where they seek to escalate their privileges and discover valuable data sources.
Phishing is the most common entry point for data exfiltration attacks. It is not the means of transferring data. Criminals use other techniques to remove data without detection.
Outbound emails
Criminals use legitimate employee accounts to send data via email. These emails appear legitimate on the surface, as they originate from the accounts of actual employees. However, criminals can transfer data as attachments or embedded in the body text.
File transfers
Attackers create secure servers and use the File Transfer Protocol (FTP) to transfer sensitive data. Attackers may exfiltrate over FTP, HTTP, HTTPS, or SMTP. HTTPS can blend with normal web traffic, while SMTP blends with email traffic. Attackers generally use different protocols for data theft and command and control. They also tend to encrypt or obfuscate transfers to evade detection.
DNS data exfiltration
Attackers exploit vulnerabilities in the Domain Name System (DNS) protocol. In this technique, data thieves embed information within outbound DNS packets. Firewalls and other data security systems approve the packets as legitimate traffic. Packets also resolve to servers controlled by the attacker, completing the extraction process.
Cloud storage exfiltration
Criminals exfiltrate data from company networks to cloud locations. For example, they may remove client account data to a private Dropbox account or Google Drive. This technique avoids reliance on external servers that could arouse suspicion. Instead, criminals use reputable services, potentially evading security measures.
Unsafe file sharing tools
Detecting cloud exfiltration is even harder if criminals exploit file-sharing tools used by regular employees. For instance, a project team may no longer operate, but may still retain a Dropbox account. Despite its inactive status, data security tools may approve this account. This makes it the ideal routing point for stolen data.
Uploads to removable storage media
Insider threats often exploit their physical access to network resources. They use USB drives to store data, before physically removing them from company locations. This attack technique only works if networks enable the use of unapproved external devices.
Physical access and removal
The economy may be almost completely digital, but companies should still consider physical exfiltration risks. Insiders can print confidential information or remove paper files. If security teams have lost focus on physical data resources, stealing information is often extremely simple. This highlights the need for complete visibility of sensitive data.
How to detect data exfiltration?
Losing critical data is never desirable. Data breaches lead to reputational damage, the loss of intellectual property, and costly compliance actions. Businesses need to understand how to detect data exfiltration before breaches occur.
Security teams can employ several techniques to identify exfiltration attacks. Detection methods include:
- DNS query monitoring. This technique helps you detect data exfiltration via DNS traffic. Monitoring tools can identify the use of DNS tunneling to break down data into web domain addresses. Tools detect unusual domain names, track high query volumes, and refer to global threat intelligence databases to correlate with known extraction sites.
- Tracking outbound emails. Scanning outbound emails helps detect data extraction via attachments. Monitoring tools detect unusual spikes in data transfers, flag suspicious recipients, and check for mentions of sensitive information (such as PII or social security numbers). Security teams automatically receive alerts, enabling rapid triage and account management.
- Monitoring data access patterns. Data access monitoring establishes a "normal" baseline for access requests and assesses whether deviations represent a data exfiltration risk. For example, a data container may experience transfer requests late at night or from unusual locations.
- Analyzing suspicious user behavior. User Entity Behavior Analytics (UEBA) complements data monitoring. UEBA tools compare user behavior to normal baselines to detect account hijacks or insider threats. Data exfiltration generally involves abnormal activity at the user level. UEBA automatically flags suspicious activity.
- Using Data Loss Prevention (DLP) solutions. DLP solutions take a data-centered approach to preventing data exfiltration. They continuously monitor traffic passing into and from the network (and between local, remote, and cloud resources). Tools look for movement of sensitive information and apply pre-defined policies to enforce acceptable usage.
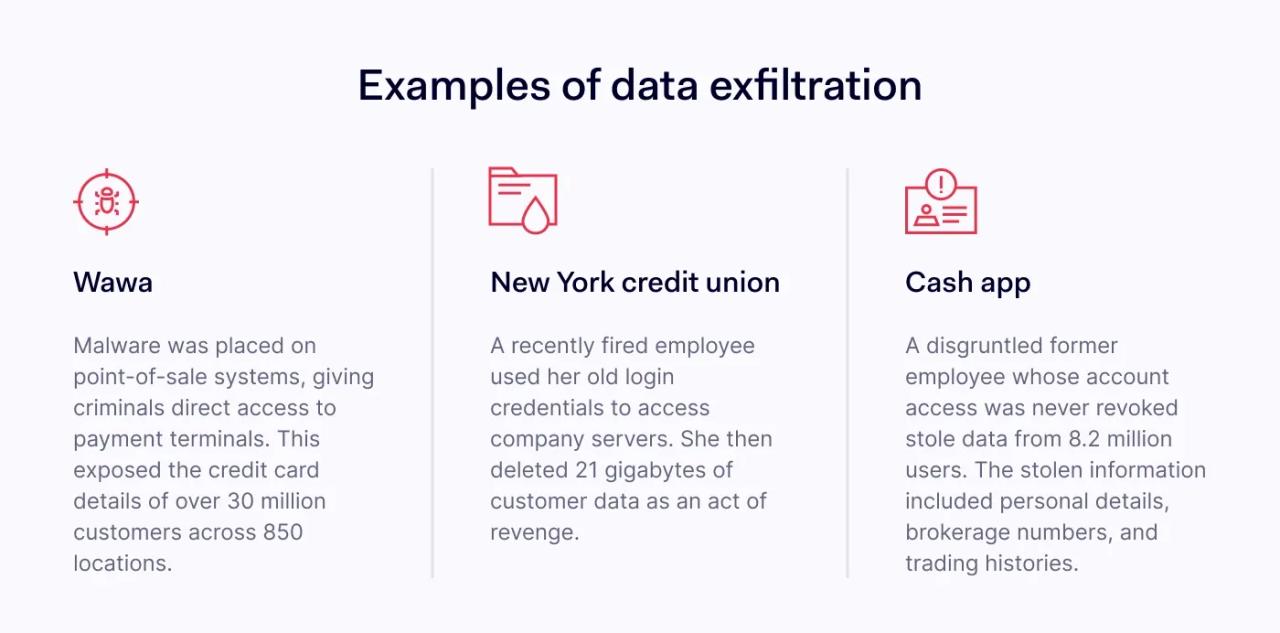
Examples of data exfiltration
Data exfiltration threatens all businesses and should not be taken lightly. As several real-life examples show, data exfiltration can ruin reputations and inflict financial damage.
Wawa: wholesale customer breach from the outside
In 2019, the gas station and convenience store giant Wawa lost data from 850 locations, including over 30 million customer payment details. Criminals infiltrated the company network and were able to embed data exfiltration malware on point-of-sale terminals. This gave them direct access to credit card numbers for over six months.
New York Credit Union: insider data destruction
In 2021, a recently fired employee of the New York Credit Union took revenge on her former employer. Although she no longer worked for the union, Juliana Barile could still gain access to company servers. She exploited her privileges, destroying 21GB of customer data - a classic example of the threat posed by dissatisfied insiders.
Cash App: customer data theft
In 2021, Cash App lost the data of 8.2 million users to a disgruntled employee. Data extended well beyond names, including trading histories, brokerage numbers, and individual holdings.
Apparently, the thief was also a previous employee. As with NYCU, Cash App failed to remove obsolete account privileges, resulting in a crippling data exfiltration attack.
How can you prevent data exfiltration?
Detecting data exfiltration is half the challenge. Companies also need ways to prevent data exfiltration. Prevention requires proactive measures to secure critical data, educate employees, and block unauthorized transfer of sensitive information.
Here are some best practices to achieve these core data protection goals:
Implement robust access controls and user authorization
Data exfiltration relies on the ability to move within networks, search for valuable information, and escalate privileges to enable data transfers. Access controls based on the principle of least privilege cut the risk of lateral movement, complicating the exploration phase of data exfiltration attacks.
Users should only have sufficient privileges to access resources related to their business role, and nothing more. Multi-factor authentication (MFA) should guard sensitive information, and systems should constantly verify identities.
Use adaptive authentication to monitor activity
Authentication should go beyond identifying user accounts. Adaptive authentication tools monitor additional factors such as user locations, device profiles, and access times. Security teams can also strengthen access controls as needed, adding biometrics and token-based systems to guard critical assets.
Update applications to block exploit attacks
Unpatched apps are inherently vulnerable. Apply network-wide patch management policies that promptly update internet-facing applications and firmware. Supplement patch management with vulnerability scanning to detect hidden network weak spots.
Apply strong encryption to data at rest and in transit
Critical data should never be left unencrypted. Robust encryption promotes data protection by rendering exfiltrated data useless to attackers. Criminals and insiders require access to encryption keys to decode data, making successful data exfiltration far harder.
Train employees to cut phishing risks
Most external data exfiltration attacks begin with social engineering campaigns. Cut the risk of malware infections and credential theft by scheduling regular phishing awareness events. Use workshops and testing to assess employee knowledge, and enforce strict email and password hygiene policies.
Put in place tools to detect data exfiltration
The measures above help to prevent data exfiltration. However, data exfiltration by insider threats and skilled cybercriminals remains a background risk. Companies should implement the detection measures discussed above as part of their prevention strategy. Remember: prevention and detection work together.
Secure critical assets with data exfiltration protection
Data exfiltration is the deliberate removal of sensitive information for malicious purposes. All companies face a data exfiltration risk from both insiders and external attackers.
Strategies to detect and prevent data exfiltration are essential. Employee training, access controls, encryption, and patch management aid prevention. Meanwhile, behavioral and network monitoring tools identify exfiltration attempts that evade prevention measures.
