The marketplace is now dominated by digital transactions, making credit card security one of the most important concerns for online sellers. It also means that companies need to be aware of PCI-DSS security standards. These rules apply to any business that handles cardholder data online. And the penalties for PCI violations can be severe. Over the years, PCI DSS fines have varied widely, depending on the level of non-compliance. For example, British Airways was fined $229 million in 2017 for a breach affecting 500,000 customers. Target agreed to an $18.5 million settlement after a 2013 data breach exposed over 41 million customers' payment information. TJX Companies were fined $40.9 million after exposing more than 94 million customer accounts between 2005 and 2006. Smaller businesses can face PCI DSS fines from $5,000 to $100,000 per month, while larger breaches can result in fines reaching millions of dollars.
This article will explore how PCI-DSS violations work. We will learn about:
- What counts as a PCI-DSS violation
- The most common types of violation
- How PCI compliance is enforced
- Ways to avoid PCI fines
What counts as a PCI-DSS violation?
Put simply, a PCI-DSS violation is an action or failure to act that breaches PCI-DSS regulations.
PCI-DSS is a security framework that defines secure practices for organizations handling cardholder data. The regulations are monitored by the PCI Security Council. Members of the council and acquiring banks levy significant financial penalties for violations.
Violations come in many forms. Companies could store credit card data in an insecure format. Or they may transmit cardholder information without applying encryption. Because of this, regulated organizations need to know the most common violations.
What are the most common PCI violations?
Most PCI violations are not conscious acts such as fraud or data theft. They tend to be examples of negligence. Companies may not even be aware that their data protection systems are not PCI-DSS compliant. But this will not change the outcome of PCI's disciplinary procedures.
In some cases, companies may apply insufficient or outdated security controls. Security practices may decay without regular assessments. And companies can outgrow existing PCI policies, creating new security vulnerabilities.
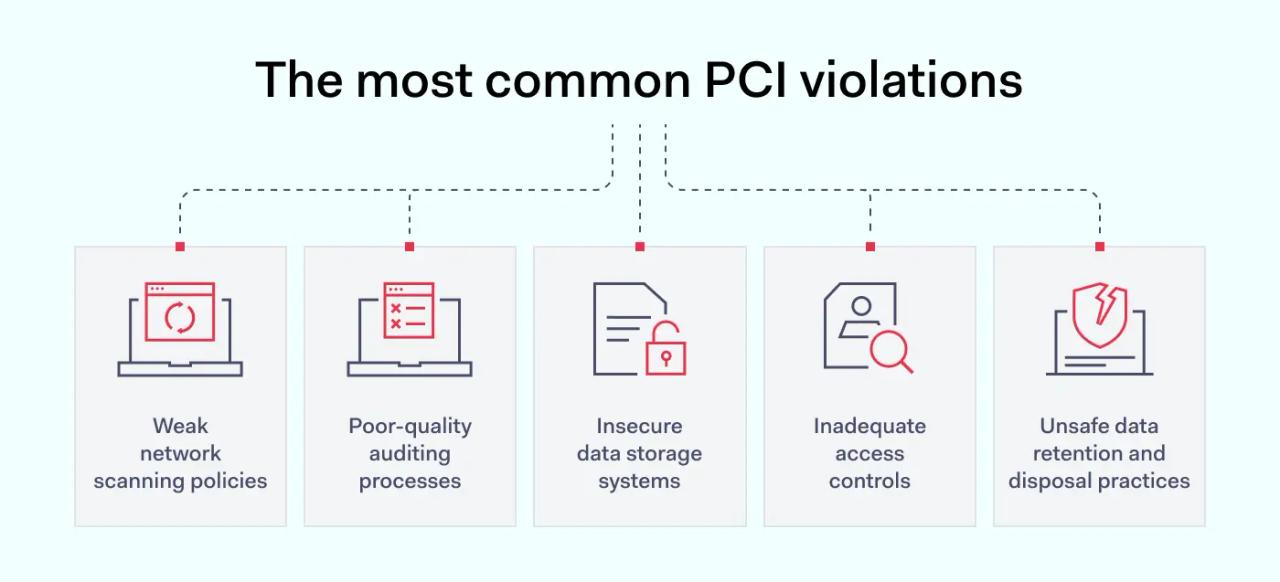
1. Weak network scanning policies
PCI-DSS requires compliant organizations to carry out annual audits and quarterly network scans. This requirement aims to detect security problems and manage emergent threats. But many organizations neglect their audit responsibilities.
Companies may fail to carry out network scans or choose non-compliant scanning methods. PCI-DSS compliance requires that companies use an Approved Scanning Vendor (ASV) four times per year. But time and cost issues can lead to companies cutting back.
Under PCI-DSS companies must also execute internal and external scans. Organizations may check internal systems for unpatched software or encryption problems. But they might fail to carry out penetration scans to test the network perimeter.
2. Poor-quality auditing processes
Auditing is a critical part of PCI-DSS regulations. Organizations must monitor user activity and record network events. They must store audit data securely and protect it against manipulation. And data should be available to use in assessment processes.
Unfortunately, documentation is not always maintained at the required quality level. Documentation may not record timestamps of user access requests. Records might not record administrative changes or the results of network scans.
Moreover, companies can violate PCI-DSS requirements by failing to meet reporting requirements. PCI rules require organizations to submit annual audit records – both in the form of self-assessment questionnaires and full-scale company audits. And they require timely reports about data breaches or other security incidents.
Poor-quality auditing is a serious PCI violation. Without proper record-keeping and data storage, organizations cannot prove compliance. They may also fail to detect security vulnerabilities, creating a cascade of PCI violations.
3. Insecure data storage systems
PCI-DSS compliance requires that cardholder data is encrypted and secure from external attackers. This applies to data at rest on company servers or cloud containers. And it also applies to cardholder data in motion. For example, during credit card transactions data moves from points of sale to central customer databases.
Violations often occur when companies fail to store data securely. Companies should always use strong 256-bit encryption to store cardholder data. And they should ensure that encryption keys are stored securely. Credit card companies will not wait for a massive data breach to act. Any data exposure due to faulty encryption counts as a violation.
Companies may also store excessive amounts of data and fail to delete data promptly. For instance, organizations should not store CVV, PAN, or magnetic stripe data from credit cards. Storing this sensitive data beyond card authorization is a serious violation.
4. Inadequate access controls
PCI-compliant companies should have complete control over who can access the cardholder data environment. Users should only have access to credit card data if they have a business need and possess the correct credentials. Otherwise, systems should deny access. But this is not always the case.
Companies often employ weak access controls that give users too much access to card data. Administrators may escalate user privileges temporarily but forget to restore their original permissions. And users can share login credentials, granting access to resources they should not be able to use.
Weak access controls also raise security breach risks. Hackers will exploit undefended customer data unless blocked by firewall tools and access management systems. This makes it vital to restrict access at all times.
5. Unsafe data retention and disposal practices
Companies need to store cardholder data for business reasons. But PCI-DSS regulations demand that data is deleted when it is not required. And organizations must dispose of customer data safely, without exposing it to data thieves.
Violations occur when companies retain data for long periods (generally beyond one year). They may also fail to delete all personal information from customer databases, or neglect to delete physical records. Security teams should securely shred paper records. And they should safely destroy physical devices holding customer data when they are no longer needed.
What are the PCI-DSS fines and consequences for violation?
It's important to note that PCI fines vary between payment processors. The architecture of PCI security standards gives processors and banks the freedom to set penalties. Various factors influence the scale of PCI compliance fines, including:
- A history of non-compliance. Repeat offendersare likely to suffer greater penalties. But first-time violators may be more fortunate.
- The degree of non-compliance. One compromised customer record is a violation, but is not as severe as losing millions of credit card numbers during a data breach. Fines reflect the severity of the offense.
- Duration of non-compliance. Even if no records have been stolen, leaving data exposed for months will result in a higher penalty than short-term exposure.
- Mitigation efforts. Taking remedial action can sometimes reduce the size of fines. If companies show evidence of mitigating violations, credit processors may reduce the scale of their penalties.
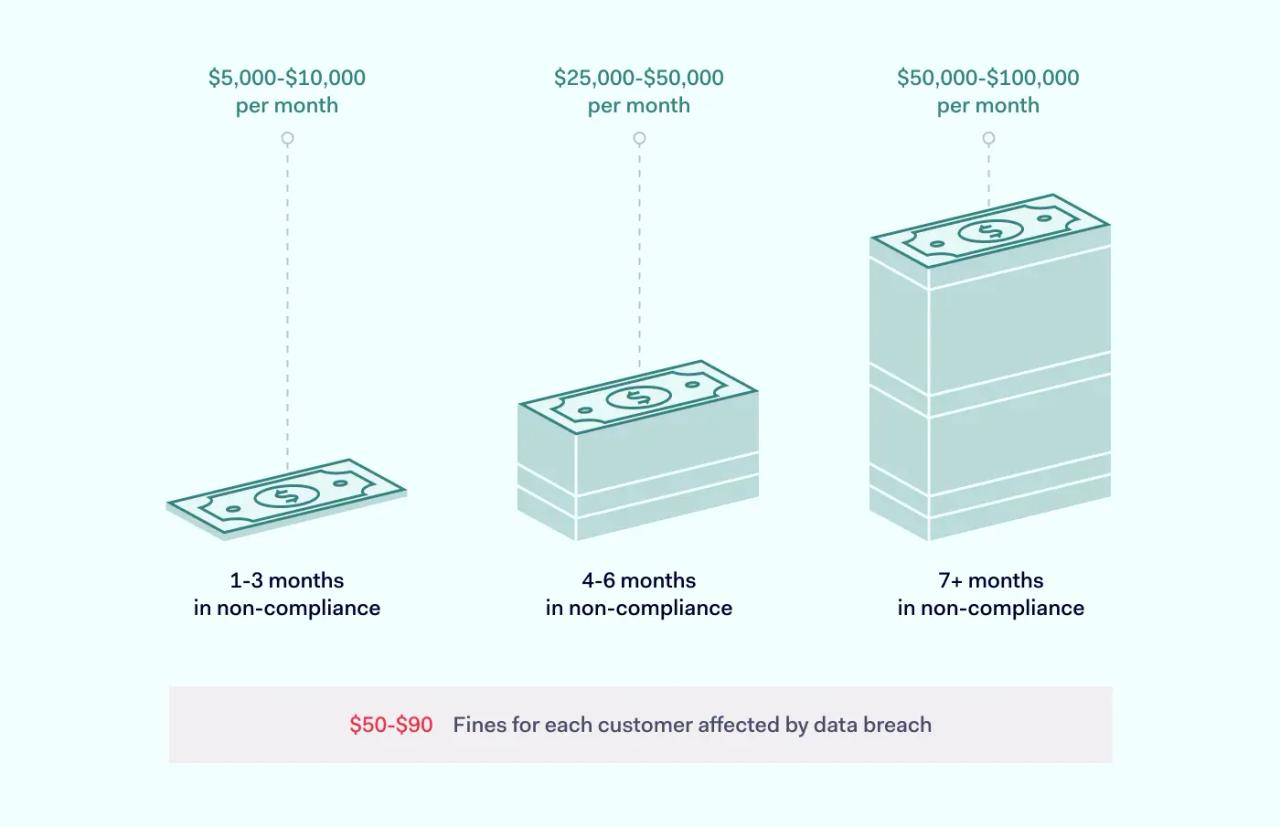
- 1-3 months in non-compliance. Fines of $5,000 per month for low-level PCI organizations. Fines of $10,000 per month for higher volume merchants.
- 4-6 months in non-compliance. Fines of $25,000 per month for low-level PCI organizations. Fines of $50,000 per month for higher volume merchants.
- 7 months and upwards in non-compliance. Fines of $50,000 per month for low-level PCI organizations. Fines of $100,000 per month for higher volume merchants.
It is also possible to receive fines without evidence of non-compliance. Merchants are generally penalized if a data breach occurs. Credit card processors typically fine companies $50-$90 for each exposed customer record during a data breach. Companies may also be suspended from banks or processors temporarily or permanently.
Who enforces PCI-DSS fines?
PCI compliance fines are not enforced by the PCI itself. Instead, enforcement is left to individual PCI members. This includes all of the world's biggest credit card companies, such as Visa, Mastercard, American Express, Discover, and JCB. These companies play a critical role in ensuring cybersecurity in financial services, maintaining trust and data safety across the industry.
PCI penalties are enforced in collaboration with intermediaries that lie between merchants and their payment processors. In practice, this usually involves an acquiring bank. The acquiring bank is responsible for ensuring its customers meet PCI standards.
A merchant's credit card company makes decisions about violations and penalties. For example, Visa may decide that a seller does not protect payment cards with sufficient encryption. In that case, Visa will technically fine the merchant's bank for dealing with a non-compliant business. However, the bank will then pass on the fine to the business in question.
How can organizations avoid PCI penalties?
PCI penalties should be avoided as much as possible. Violations have wider consequences than financial penalties. Non-compliant companies suffer reputational damage and lose the trust of customers. They may be forced to change banks and credit processors. And they will often face a heightened risk of cyber-attacks and data breaches. So taking action is critical.
Companies can consult our PCI-DSS checklist to bring their systems in line with PCI recommendations. But these quick tips will also help you minimize penalty risks and ensure smooth credit processing:
Stay aware of PCI requirements
Research PCI-DSS regulations and make sure you understand what they demand of your company. Schedule regular assessments to check for PCI updates. Regulations change throughout the update cycle, adding new measures that could affect your business.
Match PCI requirements to security controls
Create policies that comply with PCI-DSS rules. Add firewalls, encryption, access management tools, remote access solutions, and threat scanning systems. Every PCI-DSS requirement should be covered by relevant security solutions.
Make auditing a core part of your security strategy
Poor auditing is a common PCI violation. Schedule quarterly network scans by an ASV and penetration scans on (at least) an annual basis. Carry out annual PCI audits to detect and fill any security gaps.
Protect cardholder data
Data security is a critical part of PCI compliance. Map your CDE and apply encryption to all customer data. Remember to encrypt data at rest on local and cloud servers. And apply encryption to data in transit as well. Make sure you have robust incident response processes to deal with data breach incidents. Secure data with updated intrusion detection tools.
Limit access based on employee roles
Access controls protect data from unauthorized actors. Apply the principle of least privilege and tightly limit access to credit card data. Only provide access if users have a business need. And log all access requests for audit purposes.
Remain compliant to avoid PCI violations
PCI-DSS regulations protect credit card data, allowing safe online commerce. All eCommerce operators must be compliant, or they will face significant financial penalties.
Minimize your risk of PCI-DSS fines by improving your data security posture. Create action plans to meet PCI requirements, control access, and use encryption to lock down data. Robust data security is the only reliable way to avoid violations and potentially devastating reputational damage.