PCI-DSS (Payment Card Industry Data Security Standards) is the most important set of standards in the credit card processing industry.
Overseen by the world's largest credit card companies, these regulations seek to protect cardholder data and prevent digital fraud. All online vendors must achieve PCI-DSS compliance if they want to avoid penalties and minimize the risk of data breaches.
This article will explain the 12 core PCI-DSS requirements. We will explain how to integrate these requirements into security setups. And we will also explore a few important challenges organizations face as they seek to become PCI-DSS compliant.
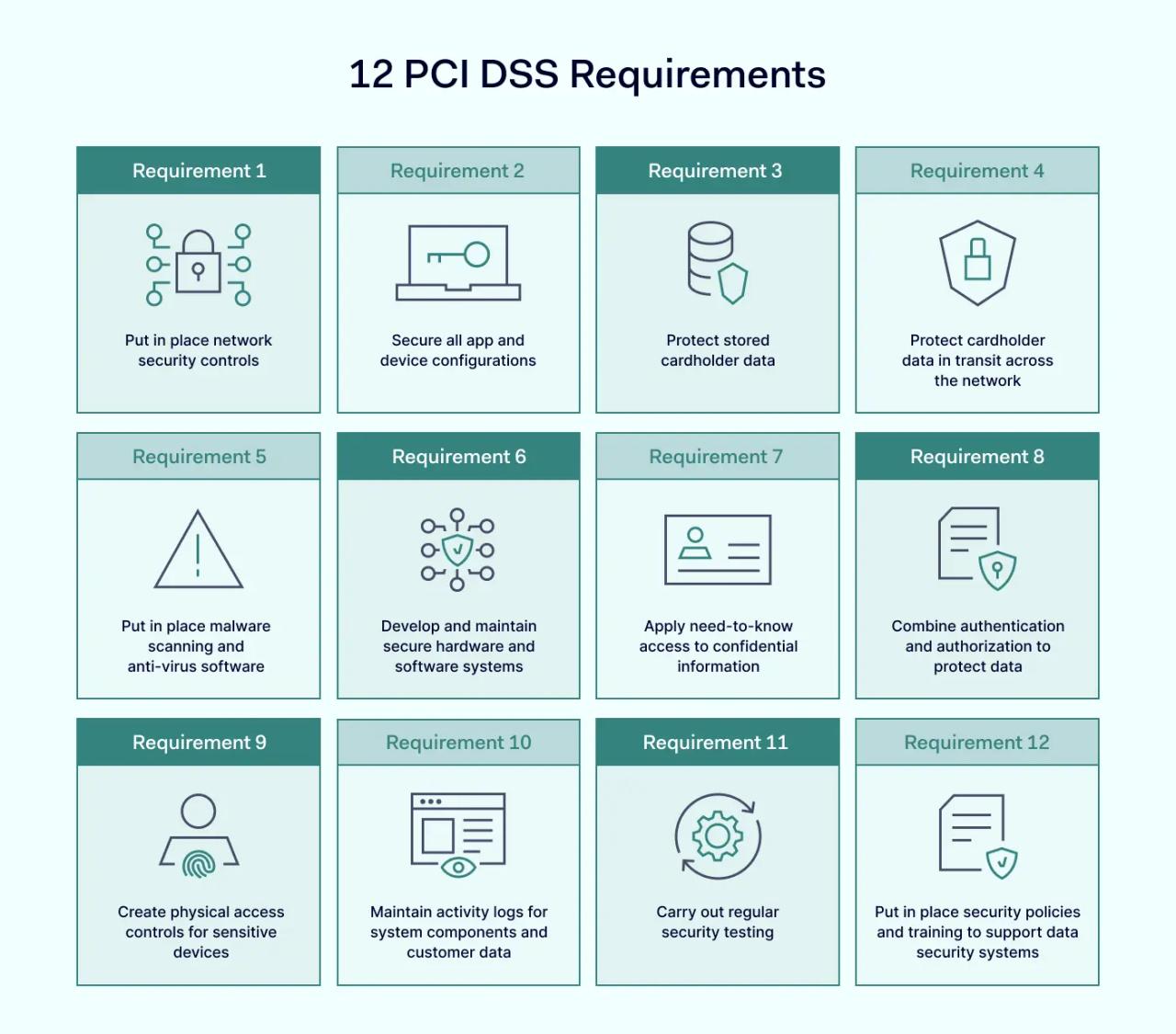
The 12 PCI DSS requirements
- Building secure systems
- Protecting cardholder data
- Managing network vulnerabilities
- Access controls and authentication to restrict access
- Logging and testing network assets
- Information security policies
These categories provide a good foundation for compliance projects. But IT teams need to consider all 12 requirements individually. So let's run through these requirements and explain how to become PCI-compliant.
Requirement 1: Put in place network security controls
Installing and maintaining a secure firewall is one of the most important PCI-DSS compliance requirements . Firewalls protect stored cardholder data by filtering incoming and outgoing network traffic. They also block unknown users, while next-generation firewalls (NGFWs) actively block malware and scan for suspicious behavior.
Firewall configuration is critically important. Security teams must configure their firewall to protect the CDE while allowing access to authorized users. Firewall rules should be documented and clearly explained. And access should be standardized across all network entry points. There should be no unprotected routes into the CDE.
Data flow diagrams help to model connections between user devices, external servers, and the CDE. Companies need to know exactly how cardholder information flows between users and data centers. This information makes it possible to put in place targeted controls that protect confidential data.
Requirement 2: Secure all app and device configurations
PCI-DSS advises against retaining vendor default settings on system components. This extends to servers, routers, hardware firewalls, and all applications used on the network. Retaining vendor defaults exposes an otherwise secure network to external attacks. Always change default security parameters like passwords or user names to secure alternatives.
Document actions to harden third-party devices and applications. And cover every asset in your network inventory. For example, hardening applies to point-of-sale devices, WEP keys, operating systems, and CRM systems. Protect and reconfigure anything connected to the CDE.
Requirement 3: Protect stored cardholder data
Protecting cardholder data is the core aim of the PCI-DSS regulations. And the regulations provide a set of recommendations about how to achieve robust data security.
Organizations should encrypt all stored customer data using 256-bit encryption standards. IT teams should also create secure storage systems for encryption keys.
Some customer data such as Primary Account Numbers (PANs) is generally unencrypted. In these cases, organizations should truncate numbers and apply masking to make PANs inaccessible without authorization.
Companies should also have clear policies about deleting unnecessary customer data. Set time limits for data deletion and minimize the amount of confidential data at rest on servers.
Requirement 4: Protect cardholder data in transit across the network
PCI-DSS rules also include recommendations about how to transmit cardholder data securely. Data in transit is vulnerable to interception attacks, both from active hackers and passive resident malware. So strong data controls are essential.
Security teams should encrypt transmission of cardholder data , wherever it travels . And use the latest version of transfer protocols such as TLS. Put in place rules prohibiting unencrypted transmission of confidential data via email. And force email users to encrypt transmission of protected data.
Companies should be aware of data flows. Systems must log transfers of payment card data, including details about the time of transmission and the user identity.
Requirement 5: Put in place malware scanning and anti-virus software
Malware attacks are the most common vector for data breaches. Under PCI-DSS regulations, companies must have robust defenses to prevent intrusion by malware and other malicious software.
Organizations must install antivirus software to guard the CDE. Antivirus software should be capable of neutralizing emerging threats. And it is essential to regularly update security tools. Attackers rapidly exploit blind spots in anti-malware software. So automate patch updates and include updates in your routine data security audits.
Check that antivirus software protects all relevant devices. This includes on-premises servers and routers, along with cloud storage containers and apps that handle credit card data. It is also important to protect remote devices. Devices connecting to the CDE must employ up-to-date malware protection.
Requirement 6: Develop and maintain secure hardware and software systems
PCI-DSS-compliant organizations must put in place processes to develop secure systems. Data security should be a critical component of all network planning. This includes developing new applications, adding data containers, and reshaping network infrastructure.
This is a dynamic aspect of PCI-DSS compliance. Companies must demonstrate that they can apply data security rules in changing environments.
Organizations should have the capacity to risk assess their CDE and its components. This includes identifying potential vulnerabilities and selecting the right security controls to neutralize them.
Update management is also important. IT teams should update network assets when possible, including all connected devices. And all changes should be recorded as part of the auditing process.
Requirement 7: Apply need-to-know access to confidential information
Strong access control measures are at the heart of PCI-DSS compliance. Organizations need to protect every piece of stored cardholder data. To do so, they must ensure that data is only accessible to authorized users. And systems should only allow access when necessary.
The best way to achieve this is by applying need-to-know access measures. Users should have tightly defined privileges based on their business role. Role-based access controls should allow access to relevant data. All other data within the CDE should be off-limits without proper authorization.
Regularly assess role-based access profiles. Profiles should allow employees to carry out tasks, but keep all other privileges to a minimum. Administrators should also delete obsolete accounts promptly and record any account deletions for audit purposes.
Requirement 8: Combine authentication and authorization to protect data
Access controls should work with watertight authentication systems to protect sensitive data. PCI-DSS rules require organizations to apply multi-factor authentication (MFA) whenever users seek access to protected information. Users should provide at least two unique identifiers before the system grants access.
User identities should also be unique. Organizations should restrict the use of shared passwords for all network assets. And it should not be possible to access cardholder data via shared accounts. Each user account should have a unique ID. This allows security teams to log user activity and trace actions back to specific users.
Password hygiene is also important. Users should always use strong passwords, and security policies should require regular password changes. Stored passwords must be encrypted and there should be clear policies about requesting changes to authentication credentials.
Requirement 9: Create physical access controls for sensitive devices
PCI-DSS compliance is not just a digital challenge. To be fully PCI-compliant, organizations must also restrict physical access to devices that store or transmit confidential data. This section also includes any paper records containing cardholder information.
Organizations should secure access points to data centers and offices. Only individuals with the right credentials should be able to physically access cardholder data. Keycards and scanning devices are commonly used to restrict physical access to critical network assets.
Companies must also record activity around servers and critical infrastructure. PCI-DSS rules state that organizations must retain video recordings of relevant areas for at least 90 days. The same applies to access logs detailing who has entered restricted areas.
Physical security also involves managing the use of external devices. For instance, any flash drives used by employees should be destroyed after use. And security policies should prohibit the use of unauthorized devices when connecting to the network.
Requirement 10: Maintain activity logs for system components and customer data
PCI-DSS compliance requires continuous network activity monitoring. Organizations must maintain accurate logs of user activity and these logs must cover all access requests. This includes both successful and unsuccessful requests.
Administrators should store logs in a legible format and be able to generate audit reports based on logged data. Reports should include information about access times and the resources that users access. Auditors should be able to use the data to analyze user activity over the past year.
Logging should also record changes to the network's security parameters. For example, if administrators add new rules to the firewall configuration. Any security changes should be noted and available for auditors to consult.
Compliant bodies also need to provide evidence that they have consulted activity logs. Organizations should schedule audits to analyze network vulnerabilities and use the data generated to refine their security posture.
Requirement 11: Carry out regular security testing
Managing evolving threats is another important PCI-DSS compliance requirement. Compliant organizations must maintain secure systems that handle new threats and vulnerabilities. This requires regular, thorough security testing.
Security testing takes various forms depending on the organization's PCI level. Almost all companies must carry out quarterly network scans. Scans must be carried out by an Approved Scanning Vendor (ASV). They use metrics like IP addresses and external domains to detect unauthorized access points.
Organizations should also carry out internal scans to identify network weaknesses. These scans can detect resident malware agents, illegitimate network traffic, and potential software exploits.
Many PCI-compliant companies also need to carry out regular penetration testing. These tests are carried out by third-party partners, and they simulate the most common forms of external attack. The PCI rules generally require annual penetration testing of the organization's CDE.
Requirement 12: Put in place security policies and training to support data security systems
Companies must create information security policies that document their security controls and provide evidence of robust PCI compliance.
Information security policies bring together information about the entire data security environment. They document exactly how systems protect cardholder data. This includes access controls, encryption, physical security, and data sharing. The policy should be delivered to all network users and held in an easily accessible central repository.
The information security policy also provides a basis for employee and third-party training. Compliant organizations must ensure that all network users are aware of data security policies. Administrators should verify and reinforce this knowledge as appropriate.
How to become PCI DSS compliant?
If you accept online credit card payments or store credit card information, you need to be PCI-DSS compliant. This applies to globe-spanning corporations and tiny start-ups. But the process of becoming compliant is relatively uniform across all business types and sizes.
To achieve compliance, organizations need to:
- Determine whether they qualify as a merchant or a service provider under the PCI system.
- Determine their PCI-DSS level. Levels are generally related to the number of annual transactions processed by the organization. Controls and documentation required become more complex as organizations climb the PCI hierarchy.
- Apply relevant PCI-DSS standards. Add controls until the organization complies with the 12 areas of the PCI system, as described above.
- Carry out a Report on Compliance (ROC). This is an assessment of the organization's security controls. Smaller businesses can complete a ROC using internal expertise.
- Execute required network scans and penetration testing to maintain secure systems. Network testing will generally require assistance from a third-party Approved Scanning Vendor.
Compliance isn't a one-time achievement. Organizations must work to retain their PCI accreditation. This entails annual security assessments and quarterly network scanning. Companies should also show evidence of ongoing security management to protect cardholder data. The process is dynamic.
There are also some other details that organizations should be aware of.
- PCI levels for Mastercard and Discovery cards are generally consistent. But American Express and JCB, and Visa operate slightly different classification systems. Consult the PCI website to ensure you find the right level for your organization.
- Visa may also require more assurance from companies that have suffered recent cyber-attacks. In some cases, the credit company may raise affected companies by one level. This can significantly change what is required to achieve compliance.
- Smaller organizations can usually carry out compliance tasks in-house. But external input is required at higher levels. This covers security testing as well as auditing.
- Payment processors may provide third-party assistance for clients. This can be a cost-effective way to put in place the required controls and carry out network testing.
Challenges in achieving PCI DSS compliance
Achieving compliance with PCI-DSS can be difficult. The PCI Security Standards Council demands that organizations protect every customer record. This sounds simple but can entail a huge amount of assessment and technical change.
In some organizations, thousands of users could access a single credit record. Huge amounts of devices might transmit or store confidential data. And existing access management and encryption systems may not meet PCI standards.
Companies also make a series of common errors when designing PCI-DSS-compliant systems. Examples of the most common mistakes include:
1. Neglecting default settings
Almost every vendor-supplied device or app has default settings. And default settings are vulnerable to external attackers. Organizations need to change passwords and IDs as soon as possible. But this can be challenging in large, constantly-changing network environments.
Potential solution : Use automation to deliver alerts about new devices and apps and add vendor settings to regular security audits.
2. Poor network segmentation strategies
Network segmentation separates high-value credit card data from other network assets. Segmentation guards the most sensitive data via firewalls and hardened access controls. This makes life very hard for data thieves and is a core PCI-DSS requirement.
Unfortunately, segmentation strategies can fail to include all cardholder information. Poor-quality scoping leaves access points vulnerable to attackers. That's a huge problem, because one exposed database may be enough to launch devastating attacks.
Potential solution: Use segmentation tools to create secure zones around the CDE. Take care to plan the scope of segmentation strategies. Map out all connections to the CDE, including antivirus tools and patch management systems. Cover all entry points with MFA to restrict access. Use firewall barriers to add extra protection for cardholder data.
3. Misunderstanding PCI-DSS rules
Not all companies that require a PCI-DSS compliance strategy design and implement one. Some businesses assume that their payment systems are out of scope. For instance, if most of their transactions are in-person or handled via phone lines.
This is often incorrect. If your business stores credit card data and transmits that data to a bank or online finance tool – you are within the scope of PCI-DSS regulations.
Other companies fail to understand PCI-DSS levels or mistakenly classify themselves as merchants or service providers. Depending on the nature of the error, this can lead to excessive self-regulation or weakly defended security systems.
Potential solution : Read through the PCI-DSS rules and take time to determine how they relate to your organization. Never make assumptions about your regulatory situation. Consult external experts or contact the PCI if you have any queries.