ISO 27001 is a popular framework that guides companies when creating an Information Security Management System (ISMS). ISO 27001 is a risk-based standard that suggests controls and policies to assess and address information security risks. In this context, risk management a critical compliance task. This article will explain how to execute information security risk assessments that meet ISO standards.
Key takeaways
- The ISO 27001 framework emphasizes a risk-based approach. It provides controls and policies to address information security risks with a high probability or impact rating.
- ISO 27001 primarily addresses risks related to data exposure, cyber-attacks, personnel-related threats, natural disasters, system failures, physical theft, sabotage, and regulatory violations.
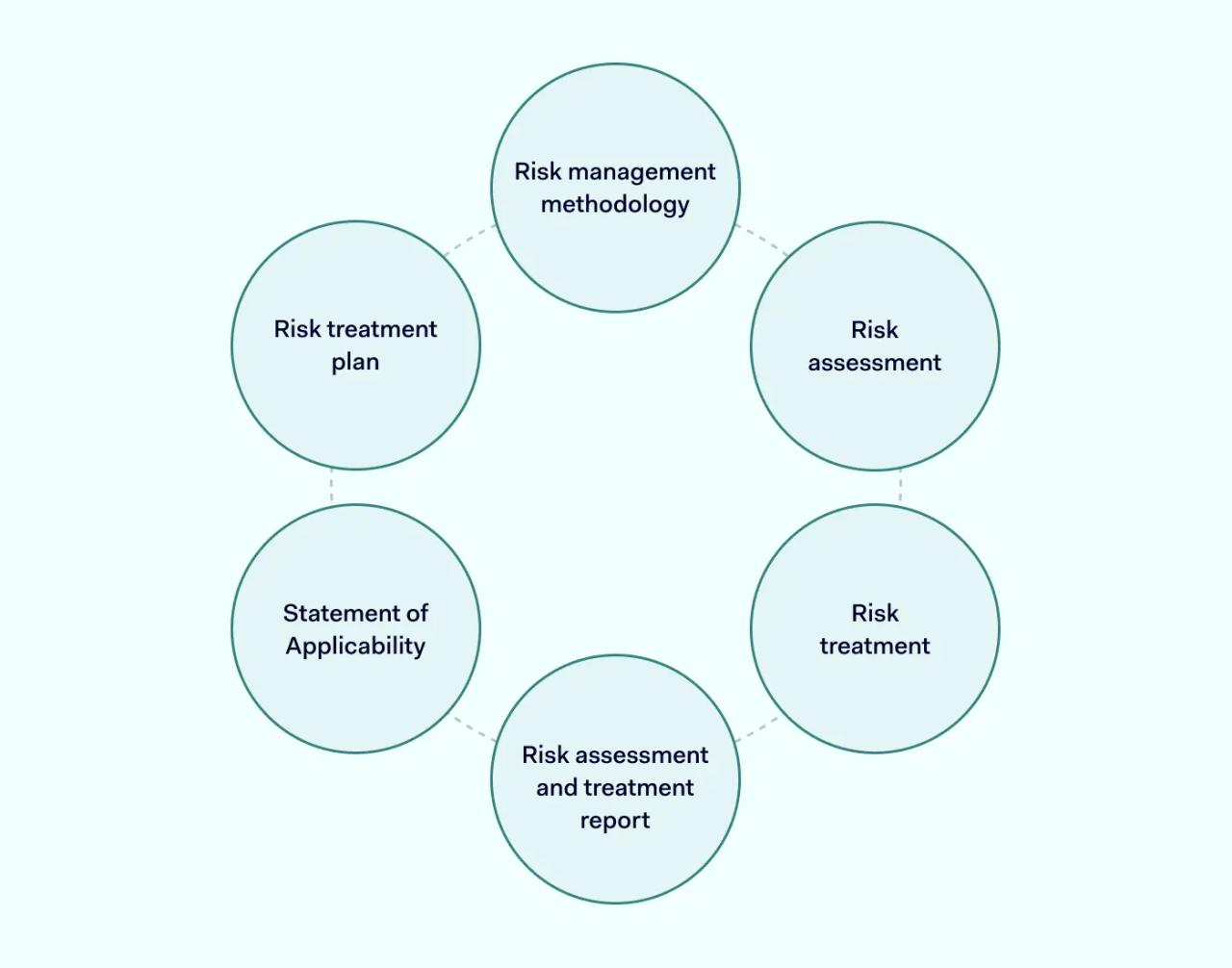
- Compliance with ISO 27001 requires a comprehensive risk assessment framework. This framework includes identifying, classifying, treating, and monitoring information security risks.
- Risk assessors must choose a risk management approach and identify critical risks. They must analyze risks according to probability and severity and prioritize risks using a risk matrix. Assessors must create a risk treatment plan, document risk ownership, and conclude with a risk assessment report.
- Small and medium-sized organizations can optimize their risk management by investing in gap analysis, adopting a measured approach to risk assessment, and consulting documentation experts.
Main ISO 27001 risks
Before discussing risk assessment and management methods, it is useful to understand what type of risks ISO 27001 addresses. ISO 27001 is an information security standard. Typical information security risks include:
- Data exposure due to unauthorized access
- Malware and other forms of cyber-attack
- Personnel-related security threats such as social engineering (phishing)
- Theft of encryption keys or password data
- Natural disasters and other emergencies that affect data security
- Compromised data availability due to device or system failure
- Physical theft of assets containing sensitive data
- Sabotage by competitors
- IT security risks associated with non-compliant third parties (vendor risks)
- Compliance risks like GDPR or HIPAA violations
Understanding risk management and why it matters
ISO 27001 compliance requires a plan to treat risks appropriately. The best way to achieve this is via a comprehensive risk assessment framework. Risk management involves assessing, classifying, treating, and monitoring information security risks.
Risk assessment and classification determine which risks apply to the information security environment. Compliance teams identify relevant risks and classify them according to a) how likely the risk is to materialize and b) the potential harm this would cause to information security.
Classification is valuable because it creates a risk hierarchy. ISO 27001 risk assessment teams know which risks require greater focus. Assessors can downgrade or even ignore some threats. High-risk threats should become a core part of the ISO implementation strategy.
Risk treatment follows assessment and classification. Compliance experts decide which ISO 27001 controls apply to each risk. This process typically cross-references identified risks with the controls listed in Annex A of ISO 27001.
After creating a risk treatment plan, ISO 27001 project teams implement controls. An internal audit checks that these controls are in place and functional. Periodic surveillance audits ensure a continuous risk management process.
What is an ISO 27001 risk assessment?
An ISO 27001 risk assessment is a risk management tool that addresses information security vulnerabilities and threats. As with all risk assessments, ISO 27001 management plans must identify and classify risks. However, risk managers must concentrate on risks addressed by Annex A controls.

Core elements of an ISO 27001 risk assessment include:
- A focus on confidentiality, privacy, data integrity, and availability.
- Measures to prevent unauthorized access to confidential data.
- Enabling continuous compliance and improvement of the ISMS. Considering risks that affect auditing and continuous risk analysis.
- Asset-centered risk analysis. Assessments focus on information assets to determine their value and risk priority.
- Consideration of information security compliance risks. For example, penalties relating to disclosing patient data.
- Ensuring documentation practices meet ISO 27001 requirements.
ISO 27001 requirements for conducting a risk assessment
Organizations must follow certain best practices when carrying out ISO 27001 risk assessments. Most importantly, ISO 27001 risk management requires documentation.
Before starting the process, organizations should create a Risk Assessment Methodology. This document explains the risk assessment process. It demonstrates to external auditors that the organization understands risk assessment and follows ISO standards.
The risk methodology should be clear and easily understood. But it must also be comprehensive. Organizations should include the following five sections:
- Methods to identify risks to critical information. This must cover risks to data integrity, availability, and confidentiality.
- Information about risk ownership. Who is responsible for managing risks, and how is this decided?
- Risk criteria are used to classify threats and determine high-priority actions.
- How the organization determines the potential harm caused by each risk and the probability of this harm occurring.
- Criteria for acceptable risk that does not require corrective action.
Use this methodology as the basis for the risk management process. Share the methodology with relevant stakeholders, including any individuals designated as risk owners. And make the document available to internal and external audit teams.
Steps to a successful ISO 27001 risk assessment
Effective risk assessment is a critical part of the ISO 27001 compliance process. Companies that don't accurately assess risks cannot apply the correct controls. The certification auditor will look for missing controls. If they detect unaddressed risks, they will almost certainly deny certification.
However, following the steps outlined below makes it easier to detect and mitigate the risks that matter.
1. Choose a risk management approach
ISO 27001 risk assessment teams must choose a method that suits their organization. There are two possible approaches: quantitative risk assessment and qualitative risk assessment.
Qualitative assessment
Qualitative risk assessment uses hypothetical scenarios to model potential risks. Teams assess the impact and probability of risks without reliance on numerical metrics. Assessors designate risk probabilities and impacts in general terms as "low", "medium", or "high".
This approach is fine when assessment teams have strong knowledge of the risk assessment environment. Qualitative methods are usually faster and simpler, allowing the ISO 27001 process to move forward more quickly.
Quantitative assessment
Quantitative risk assessment uses data to determine the probability and impact of risks. Assessors may use mathematical tools to model risks, and these tools tend to deliver precise metrics for identified risks.
For example, assessment teams may need to generate precise data about the cost of compliance. Quantitative methods allow ISO 27001 risk assessment teams to build a robust case for additional resources.
Quantitative assessment makes sense when relevant data is freely available. It also applies to high-risk contexts where accurate risk assessment is critically important.
Whatever methodology you choose, remember to include it in the risk assessment methodology document.
2. Identify critical risks
The next stage is identifying risks relating to your information security environment. Make an inventory of information assets. Classify these assets to determine those with the highest risk profile. Assess each asset to identify vulnerabilities and threats.
It's important to remember that ISO 27001 risk assessment must consider risks to confidentiality, integrity, and availability. Risk identification processes should divide each asset assessment into three parts. That way, you can ensure that you cover each core risk area.
3. Analyze risks
At this stage, you should have a register of risks associated with information assets. The next challenge is assessing each risk. There are two parts to this section of the ISO 27001 risk assessment: probability and severity.
Probability refers to how likely the risk affects your information security systems. Your risk treatment plan cannot possibly mitigate every risk. Give each risk a probability rating between 1-3, and concentrate on the most likely events.
Severity refers to what happens when the risk materializes. There are many ways to think about severity. The risk might have a financial impact in terms of lost revenue, theft, or increased costs. It could affect brand reputation and customer trust. The risk could have an operational impact, damaging the company's capacity to serve customers.
It sometimes makes sense to assign more than one impact score for each risk. For example, exposing credit card data via cybersecurity failures can lead to compliance penalties and brand damage. Score each risk impact from 1 to 3 and record this alongside the probability rating.
4. Evaluate and prioritize risk
Now, you should have a risk register with scores for probability and severity. The next step in the risk assessment process is prioritization.
Risk priority should be a simple task. The most critical risks are those with a high probability of occurring and a high severity rating. These risks seriously threaten information assets. They require urgent corrective action.
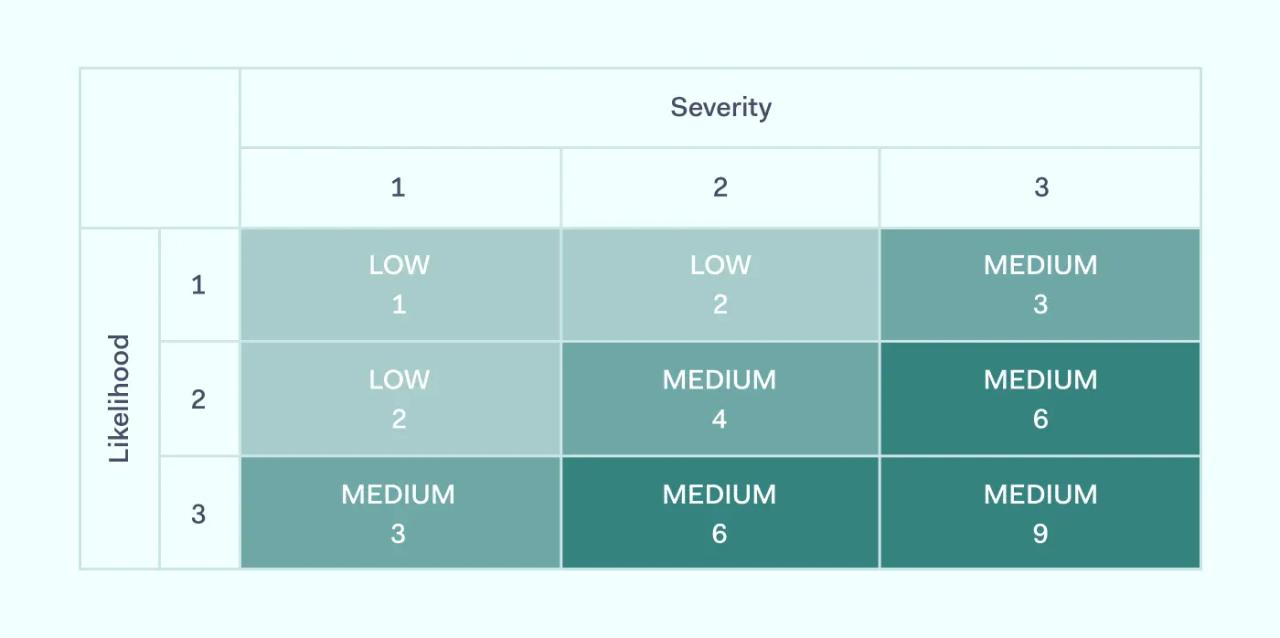
The best way to evaluate risks is via a risk matrix. This table features severity on the X-axis and probability on the Y-axis. Both axes run from 1 to 3. The cells of the graph have numerical values, which double as you pass along the axes.
The matrix assigns a numerical risk level for each risk. For instance, a risk with a severity value of 2 and a probability value of 3 would have a risk level of 6.
5. Create a risk treatment plan
Risk treatment plans are documents that combine risk matrix scores with corrective actions. Every ISO 27001 risk management process must generate a risk treatment plan for external audit teams to consult.
Under ISO 27001, mitigation actions must employ security controls recommended in Annex A of the ISO framework. This document recommends 93 controls, including technical methods, policies, and procedures.
Organizations should document the controls they adopt in a statement of applicability. This statement complements the risk treatment plan and explains the role of each control in protecting the ISMS.
Not every risk requires mitigation actions. The risk treatment plan should document whether to:
- Mitigate the risk with appropriate controls
- Avoid risks by changing the information security environment to render the risk irrelevant
- Transfer risks to a third party (for instance, by purchasing insurance)
- Accept risks due to the high cost of mitigation
Explaining the rationale for risk evaluations is extremely important. For example, valid risk acceptance criteria may be unclear. Organizations must have a clear justification whenever they choose not to implement ISO 27001 controls.
6. Establish risk owners
This step is technically part of the risk treatment plan, but ownership deserves special consideration. Risk owners are individuals who are responsible for executing corrective actions. They also monitor risks and notify compliance teams of any issues.
Organizations should provide additional training to risk owners without specialist ISO 27001 expertise. All risk managers should have communication channels to discuss aspects of ISO 27001 compliance.
7. Create a risk report and arrange an internal audit
The final step in the ISO 27001 risk assessment process is creating a risk assessment report. This report attests that the assessment is complete.
This report aims to provide auditors with proof that the organization has assessed ISO 27001-related risks and has a compliant risk assessment program. It combines the methodology document and the risk treatment plan, along with any other risk evaluations.
The risk report also considers the residual risk that remains despite implementing ISO-compliant controls. Note these risks and assure auditors that teams will monitor them in the future.
At this point, the organization should have an ISO 27001-compliant information security risk management system. Now is the time to schedule an internal audit and verify that information security processes are compliant. After that, the organization can move to formal ISO 27001 certification.
Risk assessment for small and medium-sized organizations
An ISO 27001 certification auditor costs between $10,000 and $50,000. That's a significant burden for small and medium-sized companies. Costs rise even higher when audits fail and the process resets.
A robust ISO 27001 risk assessment process cuts the risk of failure and makes ISO compliance more affordable. Small and medium-sized organizations can also follow these best practices to optimize their risk management techniques.
- Invest in gap analysis. Gap analysis by external specialists identifies discrepancies between existing ISMS and ISO recommendations. The benefits of gap assessments usually outweigh the costs, as smaller businesses generally don't have the knowledge to assess ISMS risks.
- Consider the benefits of ISO 27001 certification. Small organizations should balance the benefits and costs of ISO 27001 before proceeding. And there are plenty of upsides. Compliant companies find it easier to work as suppliers for partners. Customers trust ISO-certified vendors. ISO certification can also replace some audit requirements, lowering the long-term cost of managing security risks.
- Don't go overboard when assessing risks. Take a measured approach to the ISO 27001 risk assessment process. Only implement controls that address real-world risks. Companies can transfer, avoid, or accept many risks. Just remember to document the reason for not applying controls.
- Consult experts to manage documentation. Documentation is a common pain point for SMEs during the ISO 27001 process. If possible, bring in an external expert to audit your ISMS documentation, including risk assessment processes and ISO requirements like the Statement of Applicability.
ISO 27001 risk assessment examples
All ISO 27001 information security risk assessments are different. However, this table provides a general summary of how a risk assessment entry should look:
Risk 1. Data exposure by unauthorized access to IT assets
- Vulnerability. Absent or poorly configured access controls. Inadequate staff training. Lack of access management policies. Poor enforcement of password security.
- Risk score (1-10). 7
- Corrective actions. Strong password policies. Access management and authentication systems that block unauthorized access. Additional training to enforce access and password policies.
Risk 2. Physical theft of information assets
- Vulnerability. Inadequate physical access controls and surveillance systems.
- Risk score (1-10). 5
- Corrective actions. Installation of access control technologies and cameras. Alarms to secure sensitive data storage centers.
Risk assessments may include additional fields. For example, you may add a field providing space to explain risk scores or decisions to designate acceptable risks. However, the format above is fine for most assessment scenarios.
How to mitigate ISO 27001 risks
An integrated risk assessment identifies risks and documents treatment actions. Every identified risk must have some form of risk treatment. The ISO 27001 system recommends three potential treatment types.
Firstly, compliance teams may introduce new rules or policies to the ISMS. Annex A policies range from access control to risk ownership and developing secure systems.
The second option is implementing technical security controls. Examples could include adding data backup centers, installing firewalls, or updating threat detection software.
Compliance teams can also make changes to organizational structures. For example, the organization may need updated chains of command to manage incident responses. A Data Protection Officer may also be required.
Mitigation measures should always conform to Annex A of ISO 27001. For individual risks, more than one mitigation action may be needed.
Make risk assessment central to your ISO 27001 strategy
ISO 27001 risk assessments allow companies to reach the highest data security and compliance levels. Risk assessment outcomes vary between organizations. However, as we have seen, the assessment process is relatively consistent. Follow the steps above to mitigate critical security risks and align your information systems with ISO best practices.
Disclaimer: This article is for informational purposes only and not legal advice. Use it at your own risk and consider consulting a licensed professional for legal matters. Content may not be up-to-date or applicable to your jurisdiction and is subject to change without notice.
