Securing protected health information (PHI) is a priority for all healthcare companies. This article will explore how cybersecurity relates to healthcare organizations. We will learn about critical cybersecurity threats and challenges faced by security teams of healthcare companies. We will also discuss how to use compliance frameworks and best practices to achieve cybersecurity goals.
Key takeaways
- Cybersecurity is a critical concern in the healthcare industry. Hundreds of large-scale data breaches occur annually, affecting millions of patient records. Organizations must take action to prevent data loss and ensure patient privacy.
- Common cybersecurity threats for healthcare bodies include ransomware attacks, phishing, credential theft, insider sabotage, and web application attacks.
- Companies can consult cybersecurity frameworks to understand their legal obligations. Compliance with HIPAA rules limits cybersecurity risks and insulates healthcare organizations against financial penalties.
- Cybersecurity challenges for the healthcare sector include protecting data and ensuring privacy. Organizations must shift from legacy systems to secure alternatives. But they must consider security when using the latest medical technology.
- Organizations can meet cybersecurity requirements with training programs, risk assessments, and security controls. Follow best practices to create secure data storage and operational systems.
Why is cybersecurity important in the healthcare industry?
Cybersecurity is critical in the healthcare industry because it protects patient confidentiality and reduces the risk of data breaches. A robust cybersecurity strategy also enables healthcare organizations to comply with relevant regulations.
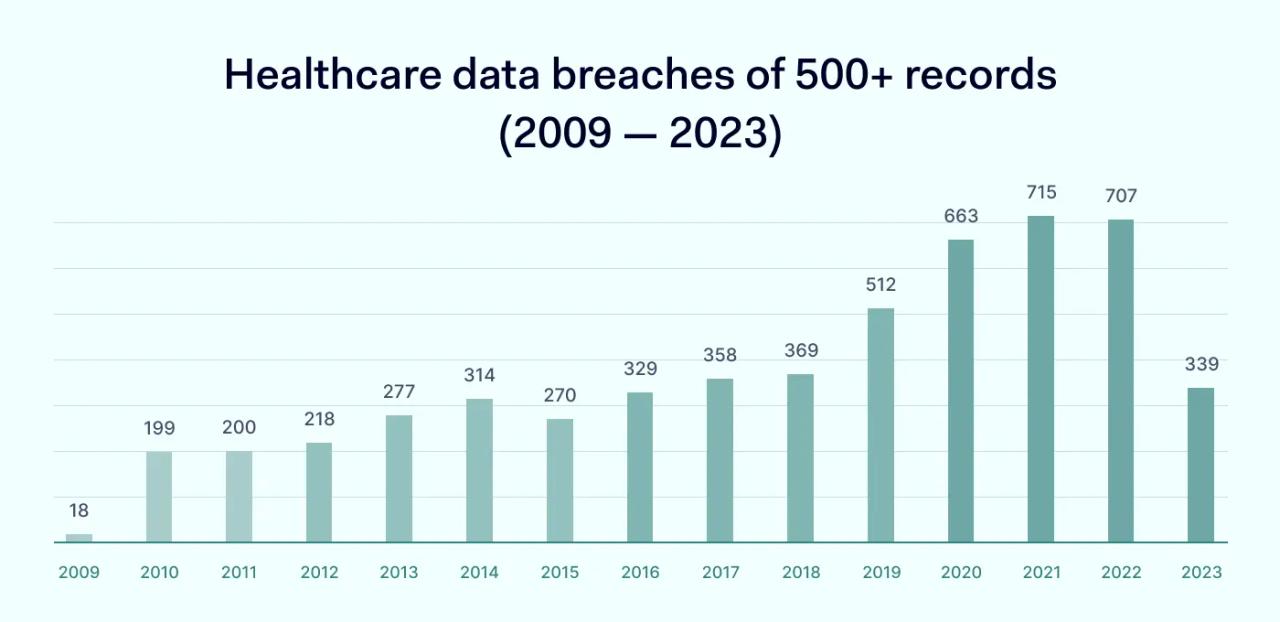
Most of these incidents involve hackers breaching network defenses to steal protected health information. In most cases, hackers gain access months before detection. Effective cybersecurity detects these attacks before they lead to massive data exposure. This minimizes the risk of regulatory fines, builds customer trust, and keeps operations running smoothly.
How the healthcare industry has become a prime target for cyberattackers
Every year the Office for Civil Rights (OCR) handles over 800 data breach investigations in the healthcare sector. The industry is constantly under assault from external attackers. But what is driving this cybersecurity trend?
The answer partly lies in technology. Recent years have seen an acceleration in the digitization of Electronic Health Records (EHRs). IoT devices generate more EHR every day. And electronic protected health information held by healthcare organizations constantly becomes more detailed. As patient records become more revealing, their value rises for attackers.
The use of third-party associates in the healthcare industry is also rising. App developers, security partners, cloud infrastructure providers, and IT vendors work closely with healthcare organizations. Their services are essential to delivering advanced health services. But the poor information security practices of associates could allow attackers access to patient data.
Healthcare organizations also struggle to keep pace with security developments. A covered entity may not allocate sufficient resources to security teams. Staff training could lag behind the activities of phishers. And organizations can fail to update technology, creating security vulnerabilities.
Main healthcare stakeholders
Healthcare cybersecurity strategies consider the role of stakeholders within the information ecosystem. Stakeholders are individuals who handle patient data or enable access to patient databases. And each one plays a role in protecting confidential data.
Patients
Cybersecurity aims to protect patient data, but patients themselves can sometimes put data at risk. Healthcare customers should be aware of how to communicate securely with clinical professionals.
Providers should inform patients about safeguarding confidential data in public and digital settings. For instance, companies may require using encrypted channels when organizing telehealth consultations.
Clinical professionals
Healthcare professionals are responsible for protecting patient confidentiality. Employees should receive and understand corporate cybersecurity policies. Workers should know how to handle data safely, rules about disclosure limits, and the penalties for breaching security policies.
Employees must also be free to report cybersecurity concerns. In a healthy organizational culture, professionals can raise concerns confidentially without fear of consequences. Workers must know who to contact with security issues. And their concerns should be fed into cybersecurity strategies.
Executives
C-level officers have a critical supervisory role in the cybersecurity landscape. Chief Information Security Officers (CISOs) manage and promote cybersecurity within the organization. Executive buy-in is vital to successful security strategies. And only proactive work by the CISO can ensure this happens.
C-level employees have additional cybersecurity responsibilities. Individuals at the executive level generally possess extensive privileges. Attackers obtaining executive-level credentials may gain wide-ranging network access. This makes extra phishing (or whaling) training for executives vital. Security teams should also minimize the allocation of administrative privileges where possible.
Business associates
Suppliers and vendors are also critical stakeholders in healthcare organizations. Cybersecurity policies must consider all business associates that deal with the organization. This includes cleaning companies and even HVAC suppliers.
Vendors store sensitive information about healthcare companies. Attackers can leverage this information when mounting phishing attacks. So, it’s vital to assess every third party and choose suppliers with robust security records.
Cybersecurity challenges in the healthcare industry
Healthcare organizations tend to face similar cybersecurity challenges. Security strategies are needed to deal with these challenges when protecting patient data.
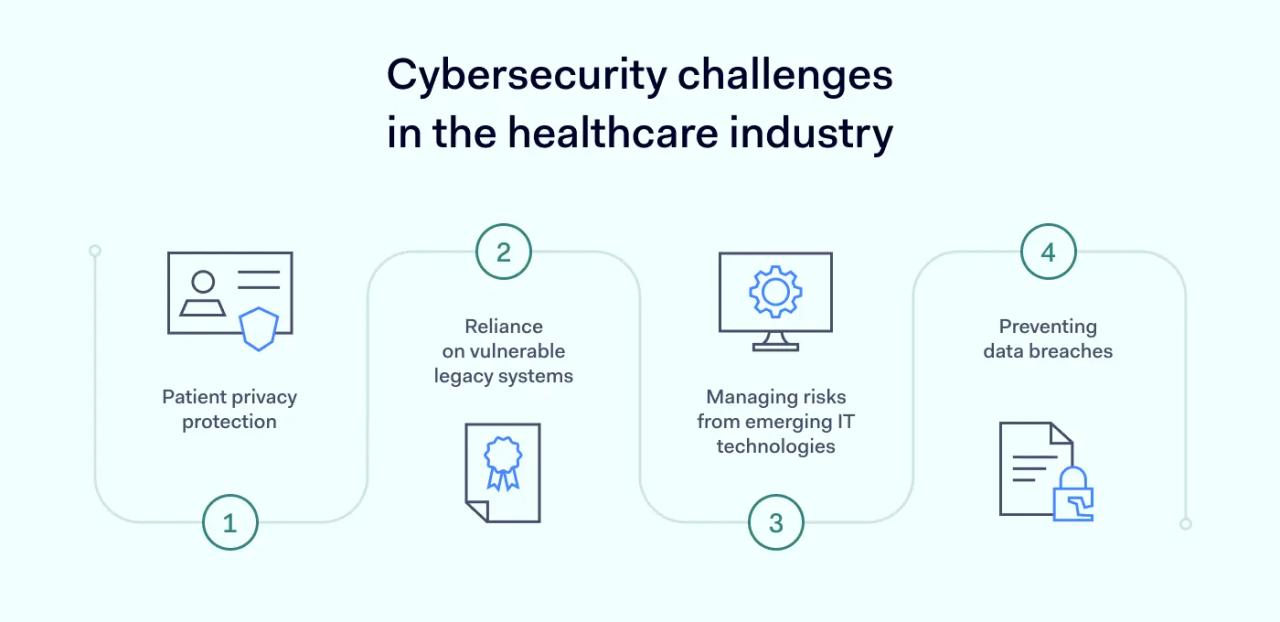
Patient privacy protection
Meeting global privacy requirements can be challenging for healthcare providers, with various legal frameworks and compliance rules.
The Health Insurance Portability and Accountability Act (HIPAA) includes strict privacy requirements for every covered entity. This includes restrictions on data sharing, the need to obtain patient consent to share data, and huge fines for companies that expose Protected Health Information (PHI).
Privacy requirements are even tighter for companies that operate in the European Union. In Europe, the General Data Protection Regulation (GDPR) requires user consent and complete transparency regarding health records. Privacy breaches carry heavy fines.
Companies operating in Canada must comply with the Electronic Documents Act (PIPEDA). PIPEDA protects PHI data. However, compared with HIPAA, businesses must guard a broader range of personal data.
Avoiding reliance on vulnerable legacy systems
Legacy systems are older technologies that lack support from their original suppliers. In healthcare settings, they can become a cybersecurity nightmare.
Unsupported apps are not updated to reflect current security threats. Their codebase does not evolve to prevent exploits. As a result, web portals gradually become more vulnerable to injection or scripting attacks.
Unfortunately, healthcare companies often rely on legacy systems in their everyday operations. There are good reasons for this. Sometimes, the cost of transitioning to modern technology is too high. Medical devices might rely on older firmware that IT teams cannot change. To save money, organizations can retain technology that once passed compliance tests.
Security teams need to make the case for change. They must persuade executives to invest in new systems and upskill employees to use them safely. And they need to make the case before cyber-attacks occur.
Managing risks from emerging IT technologies
New IT products can also create cybersecurity risks. For example, almost 50 percent of physicians use telehealth systems to meet patients. However, video-based consultations can open the door to attackers.
Telehealth involves using smart devices to record patient data and communicate with professionals. But cybersecurity experts have found that these devices may not be secure. Criminals could intercept data flows or hijack feeds. The theft of smart devices could also compromise data security.
Trends within healthcare suggest that interconnected IoT devices will soon become commonplace. While delivering major benefits for patients, this also creates a systemic risk. Attackers can use single devices to access entire healthcare databases or IoT networks. Security teams need to factor this into their planning.
Preventing data breaches
Security breaches are toxic for healthcare organizations. They incur regulatory penalties, damage trust, and can even lead to criminal prosecutions under the HIPAA Security Rule. Cybersecurity teams must understand potential attack vectors and implement controls to keep data safe. But this is not simple.
Hackers can pose as legitimate healthcare organizations and extract personal information from professionals or patients. Network users can implant malware by clicking a single malicious link. Insiders can also use their credentials to steal and sell patient data.
Security teams must encrypt data and tightly control access. They must implement firewalls and filter unauthorized users. Security awareness training should enforce secure practices within the workforce. Whistle-blowing policies should provide timely alerts when internal threats arise.
At the same time, cybersecurity teams need plans to document and report data exposure. Under the HIPAA Breach Notification Rule, companies have 60 days to inform patients and HHS. If they miss the deadline, they will incur a violation penalty.
Cybersecurity threats faced by healthcare organizations
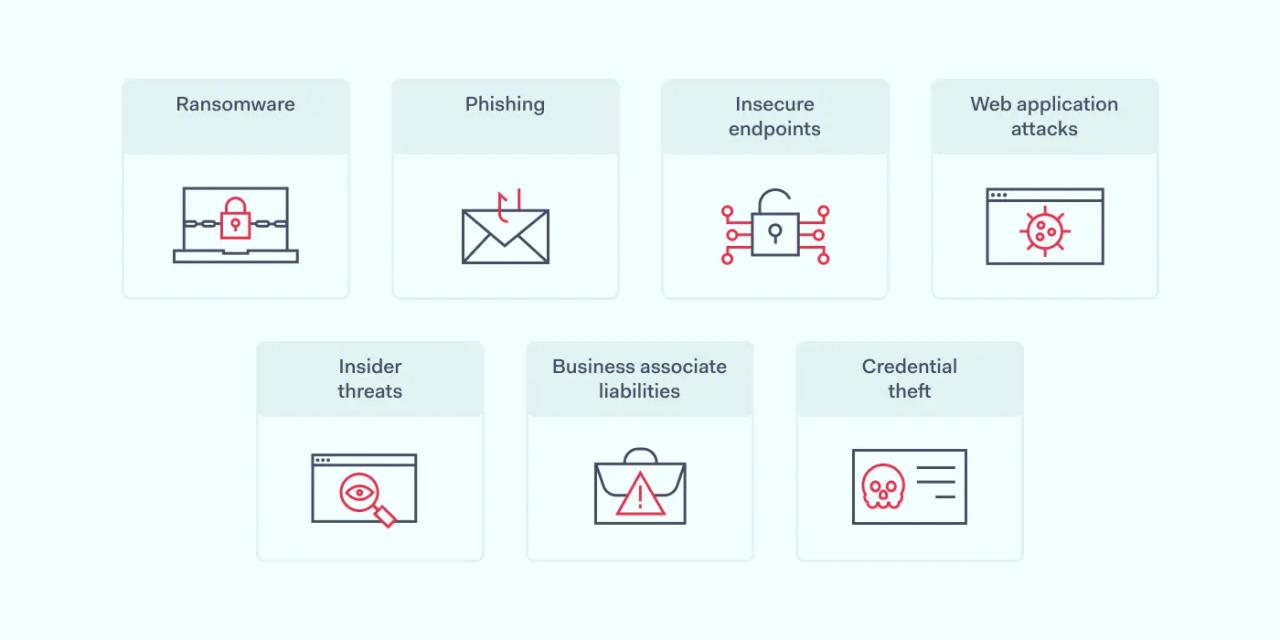
Ransomware
Ransomware locks down IT systems and demands a financial ransom from victims. Hospitals are common victims. For example, Hollywood Presbyterian Hospital in California paid $17,000 after attackers exploited outdated JBoss servers to implant a ransomware agent.
Phishing
Physicians or administrators may fall victim to phishing emails that pretend to be from Federal agencies or associates. Phishers use this route to implant spyware that stays resident on healthcare networks, passively collecting data for months or years. Phishers can also persuade victims to provide private information, which they use to gain network access.
Insecure endpoints
Insecure endpoints can also allow access to malicious outsiders. For example, many clinical organizations rely on medical devices linked to the Internet-of-Things. Remote sensors and communication tools become vectors for attackers if they lack cybersecurity protection.
Web application attacks
Web applications like health insurance portals and hospital inventory management systems pose security risks. If developers code applications incorrectly, attackers can use exploits and code injection to gain access to app backends.
Credential theft
Attackers may steal credentials and use them to access patient databases. Remote workers may leak credentials when using insecure WiFi networks. Employees may lose devices or fall victim to theft. Or companies could send credentials to incorrect recipients.
Business associates
Some attackers target business associates of larger healthcare organizations. Associates are third-party organizations that work alongside insurers or clinical facilities. But partner organizations sometimes fail to audit third parties to verify their security processes.
Poor security is a problem because business associates regularly handle patient data. They may also allow access to the networks of their partners. And if attackers steal credentials, they can pose as legitimate associates.
Insider threats
Internal employees are often the most dangerous cybersecurity threat of all. Disgruntled workers can access databases and extract patient records, often without risk of detection. Former workers may also retain access and use their old credentials to sell patient data.
Understanding the legal frameworks for healthcare cybersecurity
Organizations can use compliance frameworks to align cybersecurity systems with regulatory requirements.
HHS has created a series of framework documents to accompany HIPAA and related legislation. These documents should guide companies as they mitigate cybersecurity risks and protect patient data. And they are designed to simplify critical security challenges.
Companies can also attend industry events to learn about compliance strategies. For example, the HIMSS Global Health Conference brings together industry experts to discuss regulatory challenges and IT opportunities.
Privacy and data security frameworks
Healthcare companies should start with “Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients.”
Prepared by HHS, this document provides guidance related to the HIPAA Security Rule and is regularly updated to include the latest security recommendations. It explains the five most pressing healthcare-related cybersecurity threats. And it provides a set of best practices for healthcare providers when securing their networks.
The National Institute for Standards in Technology (NIST) also provides framework documents for healthcare companies. NIST Special Publication 800-66 Revision 1 provides a thorough grounding in meeting Security Rule obligations.
Malware protection frameworks
HHS also publishes frameworks to help healthcare providers block malware. The agency’s Cybersecurity Guidance Materials section hosts practical guides about designing anti-malware systems that meet HIPAA rules. This library includes a concise Cybersecurity Checklist to guide compliance strategies.
NIST also provides documents specifically relating to ransomware attacks. For example, Ransomware Risk Management: A Cybersecurity Framework Profile applies to healthcare companies. It assists planners when risk-assessing ransomware attacks and recommends mitigation measures to block attack vectors.
Healthcare cybersecurity best practices
Healthcare companies should refer to compliance frameworks when protecting patient data and neutralizing cybersecurity threats. However, it helps to simplify this guidance into a set of healthcare cybersecurity best practices.
Following these best practices will help you secure patient records, safeguard privacy, and minimize data breach risks.
Carry out risk assessments for cybersecurity threats
Risk assessments provide a foundation for successful cybersecurity strategies. Assess each potential threat based on the following:
- The probability of the threat
- The potential consequences of attacks
- The cost of mitigation
- Regulatory implications of taking action or not taking action
Prioritize risks and focus attention on risks with the highest priority classification. Cybersecurity professionals should revisit risk assessments at least twice every year and add any new threats as they emerge.
Put in place security controls
Mitigate critical risks with the appropriate security controls. Security teams should apply controls according to a defense-in-depth strategy. If perimeter controls fail, fall-back systems should compensate and add an extra line of defense for critical data.
Fundamental security controls for healthcare organizations include:
- Encryption of PHI at rest and in transit
- Firewalls to protect sensitive data
- Access controls to enable legitimate access but block all other users
- Multi-factor authentication for all network users
- Threat detection tools, including anti-virus and ant-malware scanners
- Audit logs to record user activity and data integrity
- Patch management to update vulnerable apps and devices
- Virtual Private Network (VPN) coverage for remote connections
- Physical controls for data centers and other storage locations
Security teams should audit security systems to ensure controls function as designed. Carry out penetration testing at regular intervals. Record scan results and actions taken in response.
Create an incident response plan
Even with the best healthcare cybersecurity solutions, attackers may get through. Companies need incident response plans to cope with security breaches. These plans should:
- Identify and neutralize threats
- Assess data integrity and identify data exposure
- Report any regulatory breaches as soon as possible
- Restore system operations and use data backups to protect critical assets
- Learn from incidents and improve security practices in the future
Provide cybersecurity training for employees
Train staff to follow secure practices when accessing and handling patient data. Include modules on how to spot and avoid phishing emails. Cover the importance of strong passwords and security issues relating to accidental disclosure.
Communicate the organization’s data security and privacy policies during training events. And assess staff members to ensure they are fully aware of cybersecurity rules.
Carry out vendor assessments
Healthcare regulations require organizations to sign Business Associate Agreements with third parties. Classify each third-party relationship as a cybersecurity risk and audit this risk at regular intervals.
When commissioning external services, assess the cybersecurity background of each vendor. Ensure vendors have adequate safeguards for data security. Check HHS records for past penalties or disciplinary action.
Disclaimer: This article is for informational purposes only and not legal advice. Use it at your own risk and consider consulting a licensed professional for legal matters. Content may not be up-to-date or applicable to your jurisdiction and is subject to change without notice.