A proxy firewall is the most secure type of firewall barrier for on-premises networks. Like proxy servers, it separates internal network assets from the internet. Like traditional firewalls, proxy firewalls filter traffic to exclude cyber threats. They can also block website access if needed.
Proxies have some critical advantages, but also some potential drawbacks. This article will explain how proxy firewalls work, and how they contribute to network security.
Definition of a proxy firewall
Proxy firewalls are network security appliances that sit between local servers and the external internet. Also known as application or gateway firewalls, they operate at the application layer of the OSI model (layer 7). Proxy firewalls monitor outgoing and incoming packet traffic, apply security filters, and block malicious threats.
Proxy servers create a gap between servers and external clients. They change the identity of local data packets before they leave the network. Because they lack direct connections, they process traffic before it comes into contact with devices on the internal network.
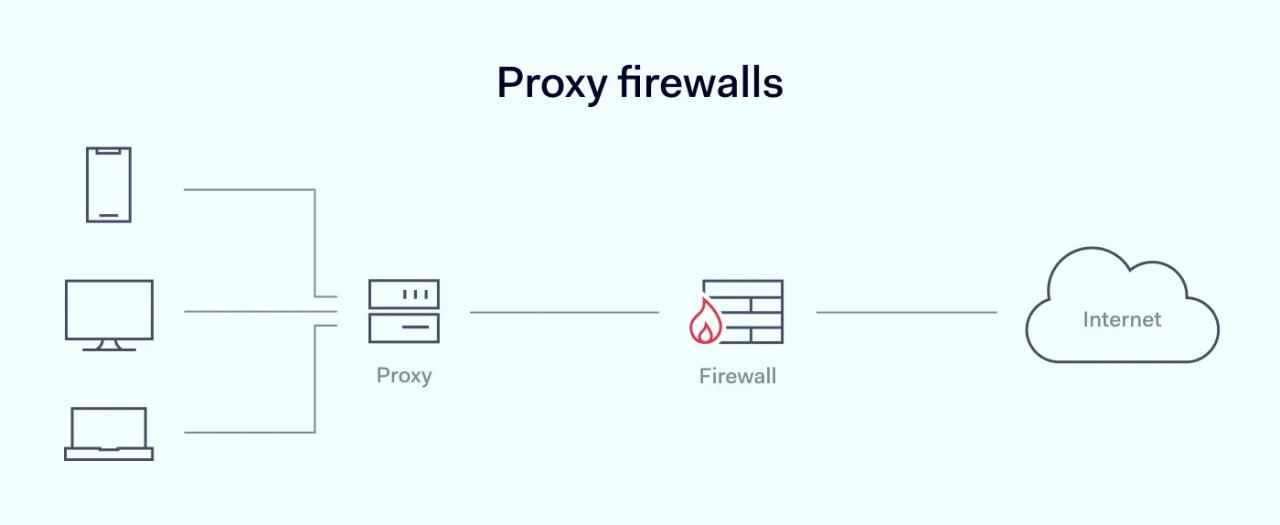
Proxy server firewall caches store incoming traffic. This allows proxy servers to log and inspect data in-depth.
Not all proxy services are firewalls. Proxy firewall systems are a specific variety of proxies. Proxies on their own deliver some security by anonymizing IP address data. But they do not filter traffic or inspect packets to discover advanced threats.
Components of proxy firewall
Proxy firewall devices include two components: a proxy and a firewall.
- Proxies. Proxy servers function as intermediaries between external and internal networks. They anonymize users' IP addresses and control the web content available to local network devices.
- Firewalls. Firewalls filter network traffic and analyze packet data to determine its legitimacy. They also validate requests for network access if data passes pre-defined security tests.
Importance of proxy firewalls in cybersecurity
Proxy firewalls play a critical role in many cybersecurity settings. They are the only type of firewall without direct connections between local infrastructure and the wider internet. Other firewall types integrate filtering and threat detection within network devices, which can raise security risks and lead to network breaches.
Proxy firewalls also provide application-level filtering. This helps security teams manage user activity on individual applications and websites. Firewalls can inspect application protocol traffic to detect malware, data extraction, and suspicious access requests.
Brief overview of the history of proxy firewalls
Proxies are not new components of network security system architecture. Proxy servers helped to build the internet. Caching data enabled servers to move data rapidly and efficiently.
Firewalls in the 1990s often relied on proxy systems. However, stateful firewalls challenged proxies with greater speed and adaptability. As a result, stateful architecture became routine in operating system firewalls. But proxies did not disappear.
Today, businesses still use proxy firewalls to apply application-level controls and filter traffic. A proxy firewall protects critical data more effectively than other on-premises systems. Despite cost and speed issues, proxies still give managers plenty of options for controlling web access and guarding assets.
How does a proxy firewall work?
Proxy firewall tools work at OSI Layer 7, or the application layer. They are separate security appliances with their own IP address.
Proxies do not filter the flow of traffic entering and leaving the internal network. Instead, they mirror local devices. Essentially, the proxy firewall creates a mirror image of applications for the duration of a session. Filtering occurs within this mirror image, separating local and external networks.
Traffic inspection techniques used by proxy firewalls resemble packet filtering firewalls. However, proxies usually go further than assessing external packet data. Proxy firewalls also inspect packet contents via deep packet inspection. This reduces the risk of unauthorized network intrusion.
Proxies work by intercepting access requests by local users. They do so by intervening in the acknowledgment processes of network protocols.
For example, internal network users may request a TCP/IP connection. The proxy firewall uses SYN-ACK signals to connect to both external servers and local clients. All traffic sent or received by local users must pass through the proxy before the network connection is validated.
Proxy firewalls intercept other critical network protocols. For instance, they can intercept Simple Mail Transfer Protocol (SMTP) traffic. This makes it possible to track and block email traffic across a network connection.
Proxies can also mirror File Transfer Protocol (FTP) transfers or Hypertext Transfer Protocol (HTTP) traffic. For instance, a proxy firewall example could include filtering HTTP traffic to create granular web controls.
Role of a proxy firewall in network security
Proxy firewalls are generally deployed on bastion hosts in network environments. Bastions are devices in the network that have the highest attack potential. They are critical points of failure that need in-depth protection against network intrusion. Proxies provide this protection.
The most common use for a proxy firewall is as an application firewall. The firewall functions alongside network applications and tracks traffic at the application layer. When applications make access or transfer requests, the firewall creates a secure mirror. This mirror reproduces the application as if it is running on network resources.
The proxy will then validate and authorize transfers from the specified application. This could include common protocols like HTTP, FTP, and SMTP. In all cases, the proxy separates local and external hosts – making connections much more secure.
Additionally, the proxy firewall can filter Domain Name System (DNS) requests. This contributes to system security by blocking or allowing access to web content. Security teams can block malicious sites, reducing the risk of network breaches.
Types of proxy firewalls
There are three main proxy firewall types: forward proxies, reverse proxies, and transparent proxies.
Forward proxy firewall
Forward proxies are the most common deployment of proxy firewalls. In this setup, proxies lie between local servers and the external internet. Traffic must pass through the proxy server before entering the network. Traffic may be cached on the proxy, helping to manage network loads and improve proxy firewall speeds.
Reverse proxy firewall
Reverse proxy firewalls switch this arrangement around. In this case, the proxy gateway firewall lies between web content servers and the internet. The firewall filters traffic leaving content servers as it passes to private networks. This allows proxy server owners to control what data leaves their servers, and what data private users receive.
Reverse proxies help manage web traffic loads. Content server owners can cache data on the proxy server. Users can quickly access content they regularly access without making requests to the content server.
Transparent proxy firewall
Transparent proxies (or forced firewalls) are virtually invisible to users. They can operate as forward or reverse firewalls, depending on network requirements. This type of proxy is hard to detect because it does not change request or response formats. As far as users are concerned, traffic flows as normal.
Transparent proxies allow companies to censor certain content from external websites. Security teams can also monitor user activity without risk of detection.
Difference between a proxy firewall and a traditional firewall
- Traditional firewalls apply security controls to traffic flows across the network perimeter. Proxy server firewalls create a space between internal and external networks. There is no direct contact between internal and external traffic.
- Proxies create mirrored connections. Traditional firewalls do not. As a result, traditional firewalls cannot anonymize traffic. Assets inside the network are easier to discover from the outside.
- Standard firewalls operate on the transport and network OSI layers (layers 3 and 4). Proxy firewall appliances work at the application layer (layer 7).
- Proxy gateway firewalls filter different protocols. Users can set up a proxy server to filter application traffic from FTP servers. Proxies could also be used to filter SMTP traffic from a company's email servers.
- Proxy servers include cache storage. Traditional firewalls lack this ability. Caches mean that the proxy server can deliver extensive logging capabilities. Firewalls store activity data for audits and analysis. Caches also give proxy server users more options for managing traffic on the network.
Advantages of using a proxy firewall
Choosing a proxy firewall over a traditional firewall has many advantages. Benefits include:
Better security
Proxies are generally thought to be the safest type of firewall. There is no direct connection between internal assets and external actors. Attackers must breach the proxy firewall before traversing an external network connection. Proxies also scramble IP addresses, making it harder to identify network devices.
Most proxies couple separation with enhanced traffic filtering. Deep Packet Inspection checks each incoming packet and detects unauthorized users. This is more reliable than simply filtering packet headers.
Auditing and logging
Proxy gateways don't just examine data packets. They can also log information in dedicated caches. Firewalls can log information about network addresses, destination ports, source IP addresses, and much more.
Secure threat analysis
The proxy server acts as a secure zone between internal networks and the public internet. This enables security teams to analyze threats in a safe environment. They can test the strength of security policies and quarantine potential threats without compromising network resources.
Greater traffic control
With a firewall proxy, companies can apply granular traffic controls. Proxy filters apply specific security policies to different applications. They can apply varying privilege levels to users or roles. And logging abilities make it easier to track user behavior.
Proxies also manage network traffic. Managers can cache web pages to reduce network congestion. Web filtering can block sites like Facebook, encouraging employees to work more productively.
Disadvantages of a proxy firewall
Performance impact
Proxy firewalls can slow down network performance. They intercept and inspect all traffic at the application layer, which introduces latency that affects user experience. This can be a major drawback for businesses that rely on real-time applications or high-speed data transfers.
Complexity of management
Managing proxy firewalls can be complex and time-consuming. They require careful configuration and ongoing maintenance to filter traffic effectively without disrupting legitimate activity. This complexity can increase the workload for IT teams and require specialized knowledge, which leads to higher operational costs.
Scalability issues
Scaling proxy firewalls as a business grows can be challenging. They may struggle to handle increased traffic volumes, which leads to performance bottlenecks. Integrating proxy firewalls into large or distributed network environments can also be difficult, making it harder to maintain consistent security policies across all locations.
Single point of failure
Proxy firewalls can become a single point of failure within a network. If the proxy server goes down, it can disrupt access to all network resources protected by the firewall. It is crucial to implement robust redundancy and failover mechanisms, which can add to the complexity and cost of deployment.
Choosing the right proxy firewall solution
Proxy firewalls could be the best way to restrict access to your network environment. However, choosing the right network security system demands careful planning, and proxies may not be the right option for your network architecture.
For example, proxies suit organizations with large local workforces. They work well in schools or universities where traffic filtering is important. However, remote access firewalls will be a better fit for companies with large remote workforces. Cloud firewalls will work better if companies rely on SaaS applications.
Choosing a proxy firewall solution
If you do decide to commission a proxy solution some challenges to think about include:
- Ease of use. Proxies can be complex to set up. Users may turn off poorly calibrated proxy gateways that limit internet access. And proxies that aren't user-friendly can become unusable at scale.
- Speed. Choose a fast proxy with smart traffic management. Proxies always reduce network speeds to some degree. Poorly engineered solutions create network bottlenecks and worsen cyber threats like DDoS attacks.
- Redundancy. Proxies are a single point of failure, and failure can lead to downtime or security nightmares. Think about combining proxies with other security systems to ensure coverage at all times.
- Cost. Proxy-based firewalls tend to be expensive. Only consider putting in place proxy solutions if there is a proven business case.