Role-Based Access Control (RBAC) is a security model that manages who can access your company's critical resources. It operates on a simple but effective principle: access is determined by an employee's role. This role, tied to seniority, responsibilities, and job description, dictates a user's privileges.
Now, what does it mean in practice? RBAC allows employees to access only the resources they need for their jobs, restricting them from other sensitive data. This approach protects data and cuts down the workload for administrators. This article explores the types of RBAC, how it works, and its pros and cons.
Role-based access control (RBAC) definition
Role-based access (RBAC) is a type of access control model that gives employees access only to critical resources and systems based on their roles. In RBAC systems, every network user has a role that determines the user's privileges and is tied to their seniority, responsibilities, and job descriptions.
Access can be permanent and last as long as the employee remains in their role, or it can be granted temporarily for specific projects. For example, if someone joins a short-term project, RBAC can grant them the access they need for just that period without compromising security.
Ultimately, RBAC ensures employees have access to the resources essential for their duties connected to their role, while other data or applications remain restricted. This method has two key benefits. One is that it protects sensitive data by denying access without user permission. Second, it also reduces the workload on administrators, who do not need to manage individual access profiles.
Types of role-based access control
What is RBAC, and how does it work? To start with, there are many forms of role-based access control.
The simplest versions feature role-based profiles. However, access technologies can be more complex, with advanced solutions including permission auditing and separation of duties.
There is no one-size-fits-all implementation. Organizations need to find a form that fits their needs. Here are the main types of RBAC for users to consider:
Core RBAC
Core role-based access control is the most basic variety of RBAC. In core RBAC, access systems must include three "core" technologies. These technologies enable organizations to apply simple role-based controls across their networks.
- Profile management. Role-based profiles set user permissions associated with each role. These permissions make sure users can only access the resources they need.
- Role authorization. When users enter the organization, they must be assigned the correct roles. The RBAC system must authorize each user in their role and apply the right privileges for every user access request.
- Privileges authorization. Core RBAC authorizes privileges according to user roles. Authorization can be simple or granular, depending on the needs of the organization.
Hierarchical RBAC
The second main form of RBAC adds more depth to role-based access systems. This access control method allows administrators to create role hierarchies within their organization.
The role hierarchy defines the relationship between different users. Users at the top of the pyramid have extensive privileges, but privileges become more limited as users become less senior.
For example, the Head of Finance may have access to all financial records. However, individual staff members may have limited access to the accounts they manage.
Constrained RBAC
This form of role-based access control adds separation of duties to the access management mix. Separation of duties is a principle that reduces users' power to carry out important actions. For instance, a physician may require a sign-off from a compliance officer before transferring patient records.
Constrained RBAC guards against network attacks launched by single users. It reduces the risk of human error and solves conflicts of interest that can lead to security issues.
Symmetric RBAC
This form of RBAC adds another key feature to role-based access control: permission-role reviews. Symmetric access controls allow permissions to be reassigned as employees leave the organization or change positions.
Auditing existing permissions boosts the security of RBAC systems. Terminated employees can retain permissions despite leaving the organization, and employees moving between positions can acquire excessive privileges. Regularly assessing the scope of permissions solves these problems.
How does RBAC work?
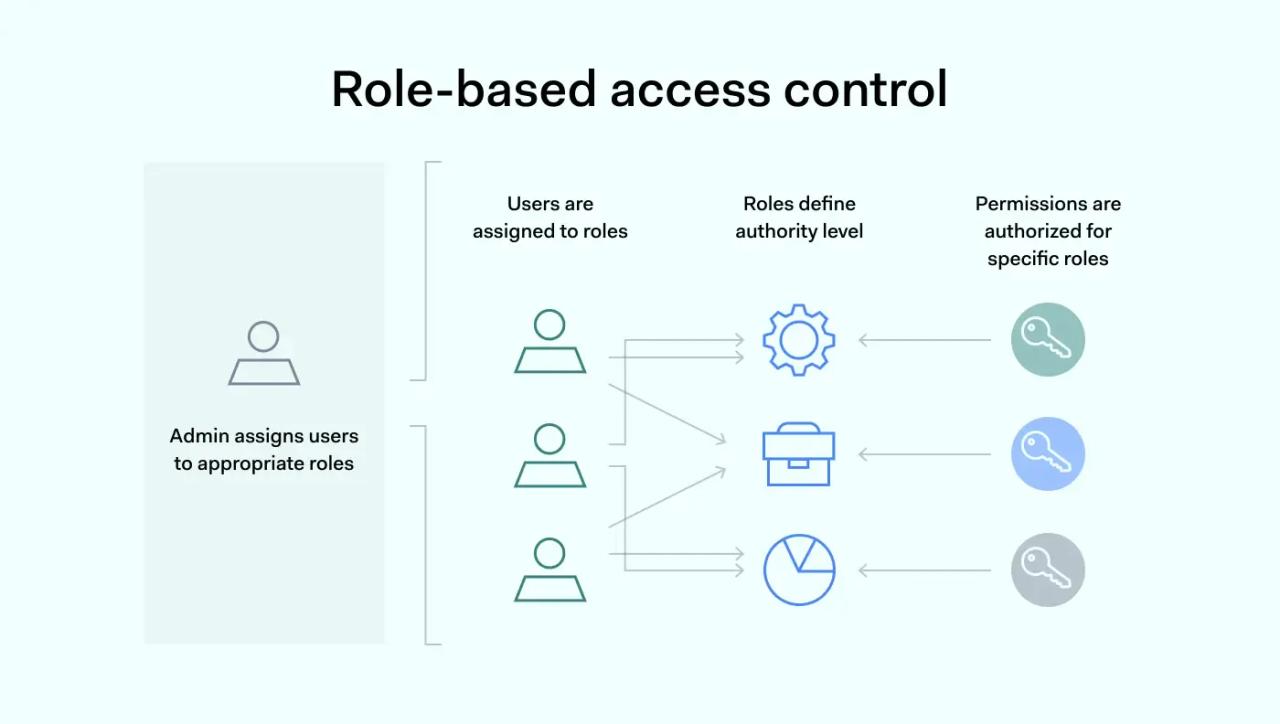
RBAC works by matching user roles to network permissions. There are three rules, provided by the National Institute of Standards and Technology (NIST), that RBAC is based on:
- Assigning roles: First, admins assign a user one or more roles. By being an active member of a specific role or group, the user automatically gains all the access permissions associated with it.
- Authorizing roles: Each user needs authorization for a specific role or roles assigned to them.
- Authorizing permission: Once users get authorization to take on a role, they receive permissions or privileges tied to that role. This way, the role has only the minimum access necessary, following the principle of least privilege.
When users connect to network resources, the RBAC system decides whether to grant access. If the user has the right role-based privileges, they can use resources. If not, controls will deny access.
User access can be applied permanently, or admins can escalate privileges temporarily.
RBAC alternatives
Access based on roles does not usually work alone. Other access technologies complement RBAC to make security systems more powerful.
1. Attribute-based access control
Applying fine-grained access controls can be difficult with RBAC alone. Attribute-based access controls (ABAC) can provide a solution.
ABAC manages access based on object or user attributes. This allows for granular controls on critical databases or apps. For example, financial companies can enable employees to access cardholder data within office hours and limit connections to approved devices.
RBAC vs. ABAC is not necessarily a binary choice. Attribute-based access control may be a useful complement to role-based systems.
2. Access control lists (ACLs)
ACLs are lists of authorized users attached to network objects or devices. Users on the access control list can access the associated resource. If not, they are denied access.
Admins can configure ACLs for specific routers, switches, VPNs, or databases. They function efficiently and provide a basic level of access control.
Organizations rarely rely on ACLs to manage access. Maintaining huge numbers of control lists across network environments can be problematic. However, they add extra security in certain situations and work with role groups if desired.
Admins can use ACLs to make RBAC more precise. An example could be providing members of a single development team access to a specific codebase. ACLs can exclude all other users with a DevOps role, but grant access to project members.
Advantages of role-based access control
RBAC is not a silver bullet for achieving network security. But using roles to manage access is an innovative approach for many reasons:
Security
With RBAC, users can only access resources linked to their professional role. Minimizing unnecessary access reduces the scope for malicious actors to steal credentials or mount phishing attacks. As a result, it should be harder for attackers to access confidential data. RBAC also implements separation of duties. This reduces the risk posed by overpowered users.
Efficiency
RBAC reduces the amount of work required to maintain network access controls. Administrators can add new hires to relevant role groups, and employees then assume the permissions attached to those roles. There is no need to create individual profiles and manage privileges for each user or object.
Scalability
Roles can change, and organizations evolve. RBAC systems allow administrators to amend role-based privileges and apply changes globally. Changes can extend automatically across network assets, reducing the risk of security gaps.
Compliance
Role-based access control (RBAC) helps organizations comply with relevant regulations, such as HIPAA. Healthcare companies often restrict access to patient records by creating roles for different clinical areas. RBAC also makes it easier to audit access requests and user activity.
Disadvantages of role-based access control
Organizations often fail to realize the benefits of role-based access control. That's because RBAC can be challenging to implement and is not always the most suitable solution. Important limitations of role-based access include:
Defining roles
What is a role? Do individual users fit naturally into groups with similar privileges? Sometimes, this is the case. Businesses are complex, and roles don't always match the privileges users require. Security teams may struggle to create meaningful role groups, which results in poor performance and user experience. Without clear role definitions, users can accumulate access rights they should not have, which is a big security risk.
Rigidity
RBAC scales well if roles are constant. However, it can be an inflexible access control solution. Roles can change as organizations evolve, and requirements shift as new apps and devices are added to the network. Role groups may lag, causing serious problems.
Complexity
Role-based access control seeks to simplify network access systems. However, in larger organizations, RBAC can lead to greater complexity. Admins may add more roles to address user complaints. Users may acquire many roles as their positions change or they join new projects. The result is what is known as "role explosion." Administering access becomes chaotic, compromising network security.
Role-based access control (RBAC) record types
Role-based access control (RBAC) defines how users access resources. The model uses different record types to manage and enforce access rules, ensuring security and compliance.
Below are the main RBAC record types.
- Access Group defines the application, default portal, and assigned access roles for a user group. Every user belongs to at least one access group, which determines their permissions.
- The role maintains all access records linked to a role. An access role name aggregates permissions but doesn't configure access control directly.
- The Access Deny record explicitly denies access under specific conditions. If both exist for the same role and class, it overrides any permissions granted by an ARO.
- Access of Role to Object (ARO) forms the core of RBAC. It defines actions a role can perform on instances of a class and links to a unique role and class combination.
- Classes represent collections of objects available to other classes or instances. The class decides whether users can open, modify, save, delete, or report on class instances.
- Privilege links an access role to a protected rule. It acts as a token, allowing only privileged users to perform specific actions tied to that rule.
- Rule is the building block that defines application behavior. Privileges restrict access to specific rule functions, ensuring only authorized users can interact with them.
Rules requiring privileges include activities, attachment categories, correspondence, data pages, flows, flow actions, parse structured rules, and report definitions. These rules control access to various functions within the application
Examples of role-based access control
Businesses and public organizations widely use RBAC. It works best if organizations have clearly defined positions and hierarchies. RBAC functions well in settings where responsibilities and group memberships are stable, but it struggles in more fluid, dynamic environments.
Let's explore some use cases to help you understand how RBAC works in practice.
Managing insurance or financial sales departments
In banking and insurance, sales positions need access to customer records to build relationships and sell products. However, employees should also have access rights to their co-workers' records. Lower-level employees should not be able to delete records without approval. RBAC makes it easy to create suitable access controls.
Separating healthcare competencies
Clinics use role-based access management to control access to confidential patient information. Receptionists and billing teams may need access to some client data and the ability to edit payment details. However, information about treatments and medical issues should be limited to clinicians. Clinicians may also lack the ability to see records from other departments without permission from someone at the same seniority level.
Community centers and sports teams
RBAC can also be used to manage community organizations. For instance, consider a local community sports hub. Admins may need access to workstations and the ability to authorize payments. Coaches or tutors may need access to club members' records and physical access to sports equipment. Payers or parents may need access to sports facilities but nothing else.
Roles make it simple to give everyone the access they need. If necessary, they can be encoded onto pass cards.
Access to digital networks and physical settings
Applied properly, role-based access control is an effective part of a cybersecurity strategy. But implementing RBAC is not always simple. Administrators must carefully design roles that suit the organization. They must assign the right permissions, review role-based privileges, and regularly update access policies.
Best practices for RBA
RBAC's practices ensure robust, adaptable, and secure access management. Here's a summary of how to implement RBAC:
- Engage key stakeholders. Communicate RBAC plans with department managers. Collaboration ensures clear role definitions.
- Develop an access control strategy. Define your goals, such as protecting critical assets and ensuring future scalability.
- Identify challenges. Address issues like inconsistent authentication methods, regulatory requirements, or managing remote users.
- Map access control: Create a detailed list of assets needing access control, including on-premises and cloud resources.
- Group users into role groups. Create role groups with similar access needs. Strive for simplicity but ensure functionality.
- Apply the least privilege principle. Assign only necessary access rights. Collect accurate data to prevent unauthorized access.
- Manage the RBAC system efficiently. Set policies for audits, role assignments, and compliance checks. Assign responsibilities clearly.
- Implement the RBAC gradually. Start with one department, address issues, and then expand. Expect adjustments and feedback.
Additionally, you can regularly review roles, gather feedback, and adjust them for organizational changes. Monitor suspicious access requests to identify vulnerabilities or phishing attempts and establish transparent privilege escalation processes, logging all temporary changes.
When RBAC grows complex, incorporating attribute-based access control (ABAC) or access control lists (ACLs) enhances security.
