Increasing digitalization pushes large and small organizations to secure their network environments. To achieve this, network access control (NAC) is a crucial component, ensuring these networks' continued safety and reliability.
Adopting appropriate technological solutions is the only way to be prepared to face evolving cyber threats. Therefore, in this article, we'll detail network access control functions and highlight why they hold significant importance in today's digital landscape.
Network access control definition
Network access control (NAC) is a security approach restricting access to private networks and sensitive resources. It enforces policies on endpoints to ensure that only authorized and compliant users and devices are allowed to enter the network.
By improving cybersecurity and compliance, NAC protects businesses from malware, ransomware, and unauthorized access to sensitive data. These solutions offer total network visibility, instant user profiling, guest networking management, internal access management, and network management.
Common use cases of NAC include:
- Managing bring-your-own-device (BYOD) work arrangements.
- Safe collaboration.
- Incident response.
- Handling IoT devices.
Implementation varies but typically involves mapping endpoint devices, creating a network access control list, determining user permissions, setting up required technology, and maintaining systems for updates. The types of NAC solutions include pre- and post-admission, each with a specific focus and benefits.
Why is network access control important (NAC)?
Network access control solutions enhance the overall security posture of the network by establishing access policies. This allows the introduction of verification and authorization of user identities and their devices, preventing unauthorized access. As companies try to avoid cybersecurity incidents, granular network control helps maintain user base accountability.
As risk mitigation is one of the main functions of cybersecurity, network access control serves as a cornerstone for a company-wide data security strategy. Overall, network access security offers a robust and proactive approach to network security, providing organizations with better visibility and control which helps to keep potential cyber threats at bay.
What are the main advantages of network access control solutions?
Since network access controls provide enhanced security controls, context-aware access and network-level enforcement makes the solution perfectly suited when mitigating threats and protecting network resources.
Increased network visibility
The expansion of remote working, bring your own device, third-party collaborations, and IoT connectivity poses severe problems for network managers. The proliferation of devices and users is hard to map and monitor, making complete network visibility challenging. NAC solutions solve this issue by mapping every device that connects to a network infrastructure and implementing policies covering every authorized user.
Improved cybersecurity
The threat of cyberattacks grows constantly. Corporate resources are exposed to malware, ransomware, and DDoS attacks, while hackers continuously seek access to sensitive data they can sell on the dark web. NAC solutions minimize these threats by excluding unauthorized or suspicious actors and limiting users' ability to achieve network access.
More effective compliance
Regulators are becoming stricter about how companies protect client information, especially concerning payment and personal information. Companies with solid records of compliance with security regulations benefit from a trust dividend and reduce the risk of losses associated with data theft. NAC solutions can assist both tasks by following gold-standard security compliance across all network endpoints.
How does network access control work?
NAC solutions establish which devices and users can connect to wired and wireless networks. Security teams devise a protocol that forms the basis of authorization policies, and specialist software applies those protocols every time a connection request is received.
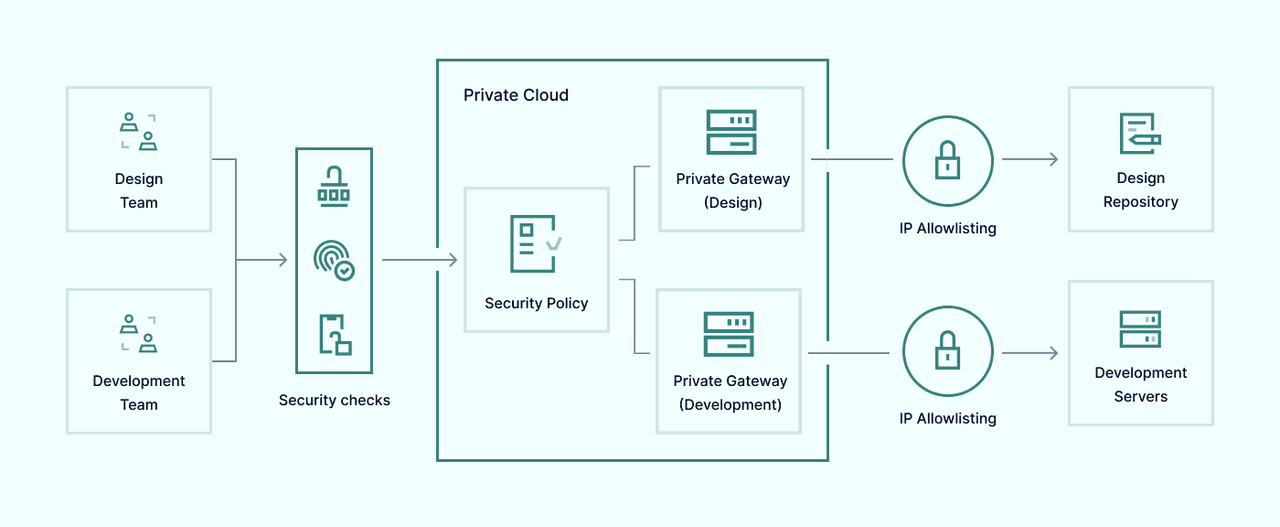
NAC systems refer to third-party authentication services when they receive access requests and establish user permissions. The system authenticates users and creates secure connections that resemble classic virtual private network traffic tunnels.
NAC tools may also determine which resources are available to corporate network users. Security policies can set out different access tiers dependent upon user roles, and NAC software can make it impossible for users to move outside their allotted permissions.
This architecture provides several capabilities for network managers, making threat management much more manageable.
Capabilities of network access control
As network access control ensures authorized access to network resources, it secures against unauthorized user access. This provides a range of capabilities to enforce network security policies, authenticate and authorize users, and monitor and control network activity.
Total network visibility
NAC implementations make networks more legible for corporate network managers. Security teams can map out what devices are connected and the contours of the network perimeter. They can identify threats and launch mitigation actions based on this information before they cause any damage.
Instant user profiling
When users request remote access to NAC portals, the system immediately checks their credentials. NAC software can exclude unknown devices and individuals by comparing this data with centrally held resources.
Guest networking management
Network access control solutions also allow companies to admit guest users securely with limited network access. Secure guest access allows collaboration with partners and contractors while lowering security threats within a corporate network.
Internal access management
When corporate networks grant user access, NAC tools determine what they can do. Sensitive resources like client databases can be kept off-limits to unauthorized users. Malicious actors will also struggle to move laterally throughout networks, limiting the dangers of malware attacks.
Network management
Sometimes, NAC tools can assist with network management tasks such as load balancing and resource allocation. Updating admission policies also encourages regular protocol monitoring, prompting security teams to update access strategies.
What are the major NAC use cases?
Network access control is useful in various use cases, enhancing network visibility, enforcing security policies, and protecting against unauthorized access. Here are some of its common use cases.
Managing BYOD work arrangements
Remote working, mobile devices, and bring-your-own-device practices have become more common in recent years. That's good news for flexible working and collaboration, but it potentially leads to expanded threat surfaces and network management issues. NAC allows security teams to log BYOD authorizations and only authenticated devices to access resources.
Safe collaboration with corporate partners
Working with contractors, guests, and external partners is a regular part of modern work. But network security problems can arise when you bring in third parties to access corporate resources. NAC solutions work around this by authorizing third parties seeking access to your data, allowing efficient collaboration without posing undue risks.
Incident response
When cyberattacks happen, NAC can spring into action. Companies can set up NAC applications to deliver threat response data to third-party security partners, facilitating immediate mitigation measures. Any endpoints affected by attacks can be neutralized and quarantined, and lateral movement throughout networks can be restricted.
Handling IoT devices and systems
The internet of things has become a vital tool for companies in diverse sectors. IoT devices like automated equipment, sensors, smart grids, and even IoT-connected vehicle fleets are featured. NAC solutions can connect large numbers of IoT devices securely and systematically, ensuring that no rogue devices are left unmapped — this also applies to the proliferation of medical devices connected to the IoT. Flows of sensitive data can be regulated and protected via adaptive NAC solutions.
Security compliance
NAC solution is also a valuable tool to ensure compliance with relevant cybersecurity regulations. Network security policies can be integrated into GDPR or HIPAA compliance plans, proving that networks meet external standards.
What are the main types of network access control?
There are many NAC solution packages and almost infinite ways to configure them. However, it helps to simplify things by dividing them into two major types.
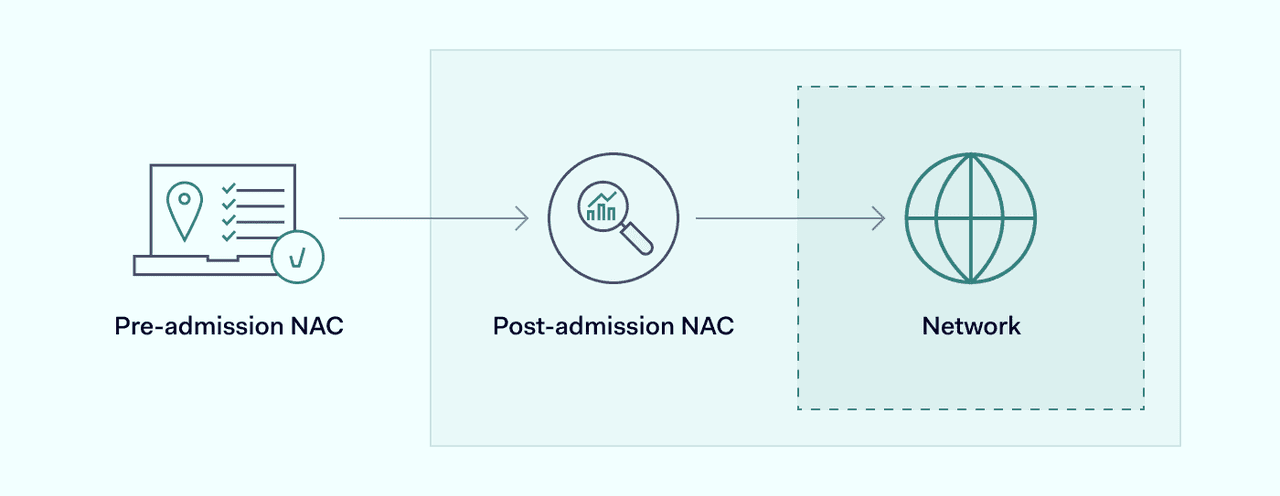
Pre-admission
Pre-admission NAC technology assesses, authenticates, and admits users when they seek to connect with corporate networks. Everything happens before users obtain access. This system stores user credentials on secure databases, and access protocols specify requirements that devices need to meet before entry is permitted. Third-party authentication services are generally also used to provide extra assurance via MFA.
Post-admission
Post-admission NAC is a little different. In this case, pre-admission authentication may remain. However, post-admission network security infrastructure monitors what users can do once they access corporate resources. Internal firewalls segregate network resources, while security protocols ensure users only access data corresponding to their privileges. When endpoints try to breach those privileges, post-admission NAC systems will shut them down and deny access.
How to implement NAC solutions
The benefits of installing a network access control are clear, but how should companies implement it?
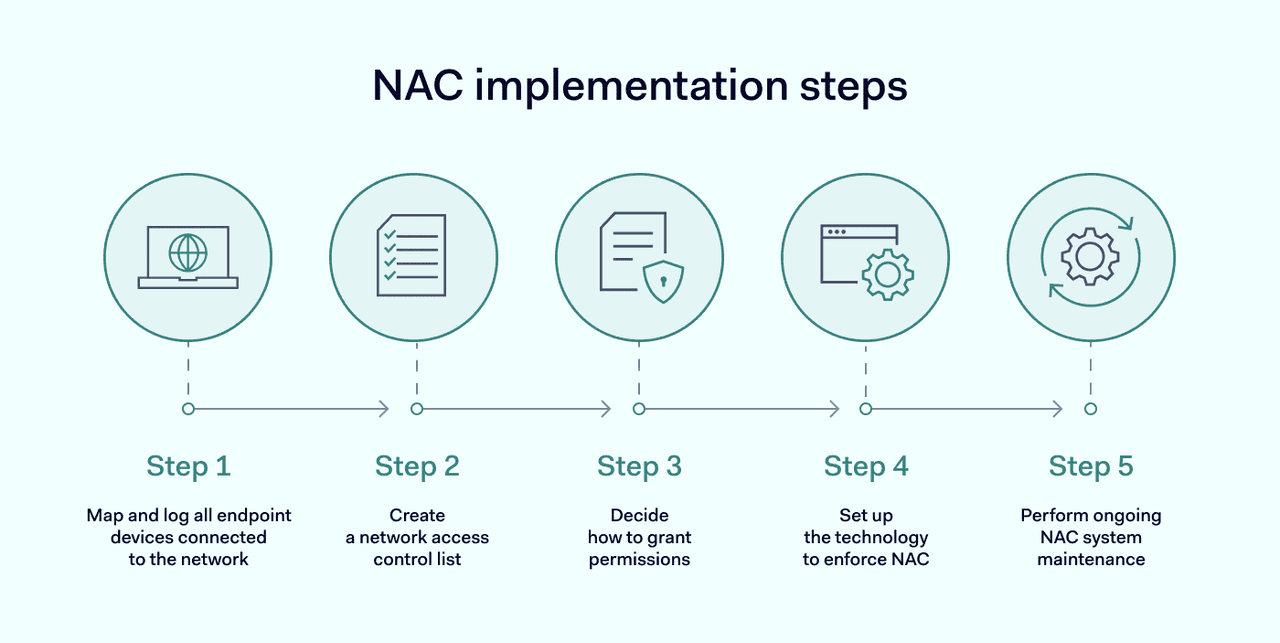
Methods vary depending on the contours of each network, the number of IoT, medical devices and third-party gadgets involved, the budget of the company, and the decision to choose pre-admission, post-admission, or hybrid network security solutions. But some basic steps are common to most NAC applications.
- Security teams should map and log all endpoint devices connected to the network. Carry out a comprehensive survey of network edges, considering IoT devices, employee devices like laptops, and centralized equipment.
- Security teams need to create a network access control list. This list includes details of all authorized users, along with their permitted access level. Start by recording all user identities on a central database. Using the existing network directory is usually a sound basis for this stage.
- Decide how to grant permissions to authorized users. It makes sense to establish permissions by role instead of individually to save time and simplify the process. Try to apply the principle of least privilege (PYOP) wherever possible. PYOP means allowing users to access what they need while limiting everything else.
- Set up the technology required to implement your access control list. Test the access portal to ensure that relevant users can obtain access and that systems exclude unauthorized users.
- Create and maintain systems to update the NAC system as required. Access control lists will change as corporate network layouts change. Applications will need regular updates to ensure that antivirus, access control, and encryption technologies are up to date.
Following these steps should allow companies to create secure network access systems with network admission control. But it isn't usually wise or necessary to do so alone. Many NAC providers can supply expertise and technology to develop customized network security solutions with recommended security policies.
