Zero Trust Edge (ZTE) is a virtual network that uses Zero Trust Network Access (ZTNA) to connect and authenticate remote users. The model relies on cloud-based security solutions to reorganize IT infrastructure in a more modern and secure fashion.
ZTE networks are accessible from anywhere, providing a flexible solution for a scattered workforce without compromising your organization’s security. ZTE consolidates cloud-delivered and managed security capabilities with network functionalities.
Zero Trust Edge principles
As outlined by the Forrester report, ZTE brings together networking and security, closely following the Zero Trust framework. Essentially, any ZTE setup should have two fundamental principles.
Cloud-based network and security management
A common problem that enterprises face when introducing cybersecurity solutions is their fragmentation. Separate tools come with their own policies, and creating a shared basis between them isn’t easy. Misconfigurations and security policy differences could leave gaps that could be exploited in cyberattacks.
ZTE provides a single set of configurations that are applied across all connected endpoints via cloud management. This allows easier and consolidated administration for networking, firewall, and other functionalities. Configurations can be adjusted in real-time and from a single dashboard. Choosing reputable ZTNA vendors can further enhance the reliability of configuration management.
Cloud-based monitoring and analysis
Fragmentation as a drawback is also significant in terms of monitoring. It’s easy to lose key insights when each networking and security monitoring tool works independently.
ZTE bridges the gap between networking and security and provides much better supervision of all infrastructure components. By leveraging cloud computing to analyze large data sets, ZTE brings the entire network under a single dome of surveillance. This gives much more data to work with, generating better insights to draw meaningful conclusions.
What are the benefits of Zero Trust Edge (ZTE)?
ZTE provides a systemic approach when solving modern businesses’ cybersecurity challenges. The combination of cloud security and networking can be incredibly beneficial to organizations in several ways.
1. Facilitation of cybersecurity transformation
ZTE can be a gateway for various security and networking services. Some may require cloud infrastructure, while others can be deployed on-premises. It’s a holistic solution that can evolve and expand by adding other functionalities like software-defined WAN (SD-WAN), secure web gateway (SWG), etc.
2. Streamlining of the company’s cybersecurity infrastructure
The adoption of ZTE consolidates many cybersecurity tools into a single and unified solution. This allows easier monitoring, analysis, and response to various cybersecurity threats. Maintenance of one such system is much easier than managing several different ones that might have compatibility issues.
3. Hybrid workplace security
By enforcing consistent and coordinated security policies, ZTE unifies its rules across all connection sources. As remote employees are connecting from unmanaged networks, it applies the same standard of due diligence that it would apply if they were connecting from the office. The unified level of security contributes to workplace flexibility and facilitates risk management.
4. Cuts business expenses
By design, ZTE is cloud-based and heavily focused on automation. This frees the IT staff from mundane tasks and allows them to focus on the anomalies detected by the network monitoring tools. In addition, the ability to easily upscale or downscale ZTE networks means that businesses are never wasting resources and are paying only for what they currently use.
5. Eliminates data backhauling
One of the problems associated with traditional VPN setups was backhauling remote workers’ traffic through corporate networks. This was done for security inspection before passing it through to its destination. Meanwhile, ZTE setups rely on cloud on-ramps providing good connectivity and security inspection worldwide. This ensures much better performance and doesn’t clog up internal bandwidth.
The ZTE model heavily relies on the Zero Trust approach, thoroughly inspecting each connection. This also lowers the risks of being caught off guard due to strict authentication procedures.
How does ZTE work?
While ZTE outlines some ground principles on how it has to be set up, it allows modifications. For instance, some of its components can be cloud-hosted, and others can be set up as an edge-hosted security stack.
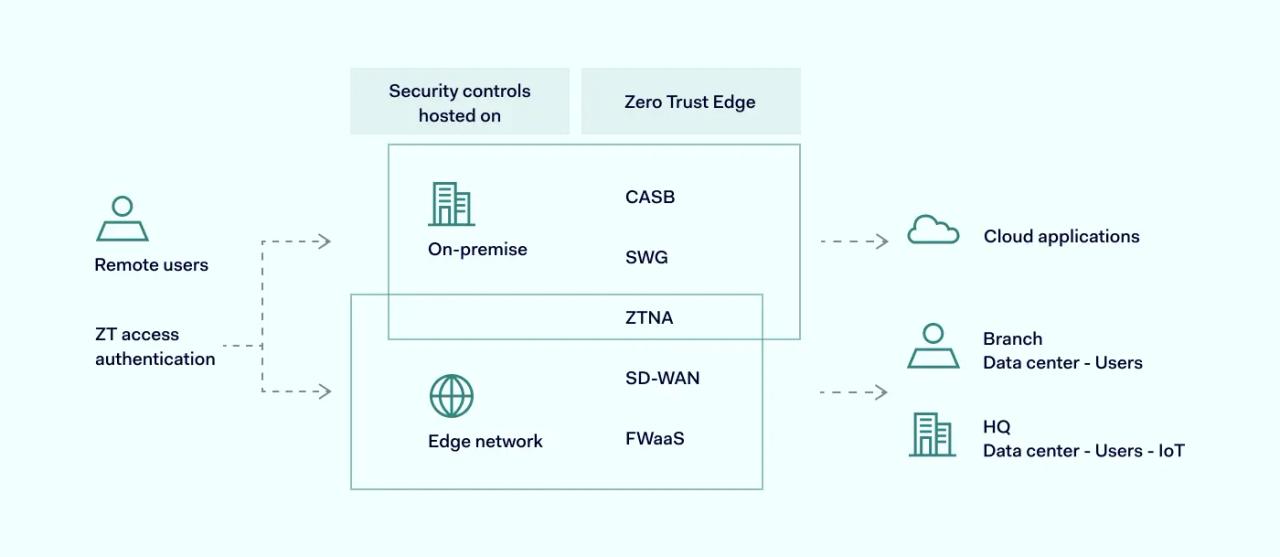
Depending on the use cases and bandwidth capabilities, ZTE can be set up in three following ways:
1. Cloud-delivered ZTE service
In this setup, ZTE is a fully cloud-based and vendor-operated network-as-a-service (NaaS) product. Users connect to distributed points of presence (POPs) and are allowed into the service provider’s infrastructure. This is one of the most popular ZTE delivery methods.
2. ZTE as part of the WAN service
Many WAN service providers have started bundling the service with ZTE capabilities. The clients are getting an all-in-one SD-WAN package expanded with ZTE functionalities. The drawback of this option is that on-premise setups will be less flexible compared to cloud-native systems. Conversely, SD-WAN and ZTE combinations are separate entities, requiring thorough policy configurations across two services. In a way, this invalidates a consolidated ZTE service’s benefits.
3. Self-made ZTE
Creating your own ZTE system from the ground up might also be an option. Though, this method is viable only to large-scale enterprises with infrastructure already in place that could be leveraged. POPs, firewalls, and other components will have to be deployed by the organization itself. This is the most expensive and time-consuming approach, but it does give the most customizability of all the options.
ZTE challenges
ZTE can be regarded as a traditional network security approach disruptor. Naturally, transition to this new framework inherently means dealing with some challenges. This is especially complicated as, traditionally, network security has been done differently. Here are the potential pain points when transitioning to the ZTE framework:
Legacy applications and services
Software built on older standards and non-web protocols won’t be as easy to integrate into the ZTE environment. Depending on the used hardware, it may not always have modern counterparts and can’t be updated. ZTE is the most compatible with modern software that supports identity federation.
Legacy hardware
Some critical infrastructure components might be relying on legacy hardware. Transitioning to ZTE isn’t easy as this would require a total revamp of the infrastructure. In addition, legacy hardware might not have the capabilities to support ZTE. This requires reevaluations of the used operational technologies and IoT devices.
Capacity
The business should consider the network capacity before considering ZTE implementation. Some workarounds will have to be found if it’s at its limits. In some cases, the enterprise will have to migrate to cloud-based infrastructure and then focus on adding other security features. This can be an annoying complication that makes the transition to ZTE more difficult.
ZTE and SASE
Secure Access Service Edge or SASE is considered a convergence of SD-WAN and other network security services in a collective cloud-based offering. In essence, this sounds very similar to ZTE, which also consolidates network functionality with cloud-delivered security capabilities.
The difference is that ZTE emphasizes the Zero Trust approach aiming to create Zero-Trust-as-a-Service beyond access controls. It provides continuous control of the organization’s network infrastructure. This can be understood as a much more specific SASE model.
It remains to be said that both SASE and ZTE use similar principles to enable remote work without drastically increasing risks. As the Internet is one of the biggest attack surfaces in the world, ZTE takes a much stricter approach to protect against potential threats.