Cyber-attacks are rising, and modern networks are becoming more complex. Traditional security models no longer work effectively. As threats grow more advanced, 63% of organizations have already adopted a Zero Trust strategy, according to a 2024 Gartner report. This article explores the key Zero Trust pillars, showing how it protects access, reduces risks, and strengthens security for organizations.
What is Zero Trust security?
The traditional “castle and moat” network protection model focuses on securing the network’s perimeter, like walls around a castle. Anyone inside the network is trusted without further checks, much like those inside the castle walls. However, this approach leaves systems vulnerable if an attacker gets through the defenses.
Zero Trust security changes how access to resources is managed. Instead of using the traditional “castle and moat” model, Zero Trust framework assumes no one—user or device—should be trusted by default.
In the Zero Trust model, the system checks every access attempt. A user gets access based on calculated risks, which change depending on user behavior or the sensitivity of the data.
It's like verifying someone's identity at every door in a building, not just at the entrance. This helps limit the movement of attackers within the network if a breach happens.
The 7 pillars of Zero Trust architecture
Zero Trust architecture relies on key elements called pillars. In 2024, the National Security Agency (NSA) released guidance on these pillars for the National Security System (NSS), Department of Defense (DoD), Defense Industrial Base (DIB), and other organizations. The report advises organizations to use this framework to reduce risks and quickly detect and respond to cyber threats.

1. User pillar
Cyber-attacks often target weak points in identity and access control. The 2015 Office of Personnel Management data breach and the 2021 Colonial Pipeline attack both showed these gaps. In these cases, multi-factor authentication (MFA) wasn't fully used, and the user aspect was compromised.
The user pillar strengthens identity and access management to stop these kinds of threats. Here's how:
- Identity management creates and protects digital identities. Some useful steps for organizations are:
- Keep a list of all employees, especially those with special access
- Use one main identity system to avoid mistakes
- Remove access for employees who change jobs or leave
- Credential management keeps passwords and keys safe and up to date:
- Give passwords based on each employee’s job, like different keys for different areas
- Track all passwords; make sure to remove ones that are unsafe or old
- Use MFA to make breaking into accounts harder
- Access management controls who can reach certain areas, allowing access only to the right people:
- Apply least privilege access so employees only get what they need
- Check and remove unnecessary access regularly
- Set access for short times, only when needed
In short, identity management begins by making an accurate list of all users, including people and non-person entities. Credential management adds MFA and handles giving, using, and removing credentials linked to company users. Access management limits access so employees only get what they need.
2. Device pillar
The device pillar ensures all devices trying to access a system are secure. Devices need to be identified, checked, and given permission based on a risk calculation. Only devices that follow security rules get full access. If a device doesn’t meet the rules, it gets limited or no access.

Key parts of the device pillar include:
- Device inventory. List all devices, keep the inventory updated, and block unapproved devices
- Device detection and compliance. Ensure each device follows security policies on connection
- Device authorization. Allow only compliant devices with real-time threat monitoring
- Remote access protection. Set access rules for secure remote access
- Automated vulnerability management. Identify and update weak points to reduce risks
- Centralized device management. Control and secure all devices, including remote ones
- Endpoint threat detection. Find and fix device issues linked to network security.
This will ensure that security tools are in place to protect devices within a Zero Trust architecture.
3. Network and environment pillar
An example: In 2013, an American retail company faced a major data breach because it lacked proper network segmentation. Attackers got the login details of a heating, ventilation, and air conditioning (HVAC) company that worked for several store locations. The HVAC company had access to the retail company’s network to monitor energy and temperature.
The attackers used these credentials to install malware in the point-of-sale systems and stole data from about 40 million debit and credit cards. While the HVAC company needed network access, the breach could have been avoided with better network segmentation and access control.
Traditional network security focuses on building defenses around the network. However, once inside, users, apps, and devices often have access to many resources. If a user is hacked, attackers can reach important systems.
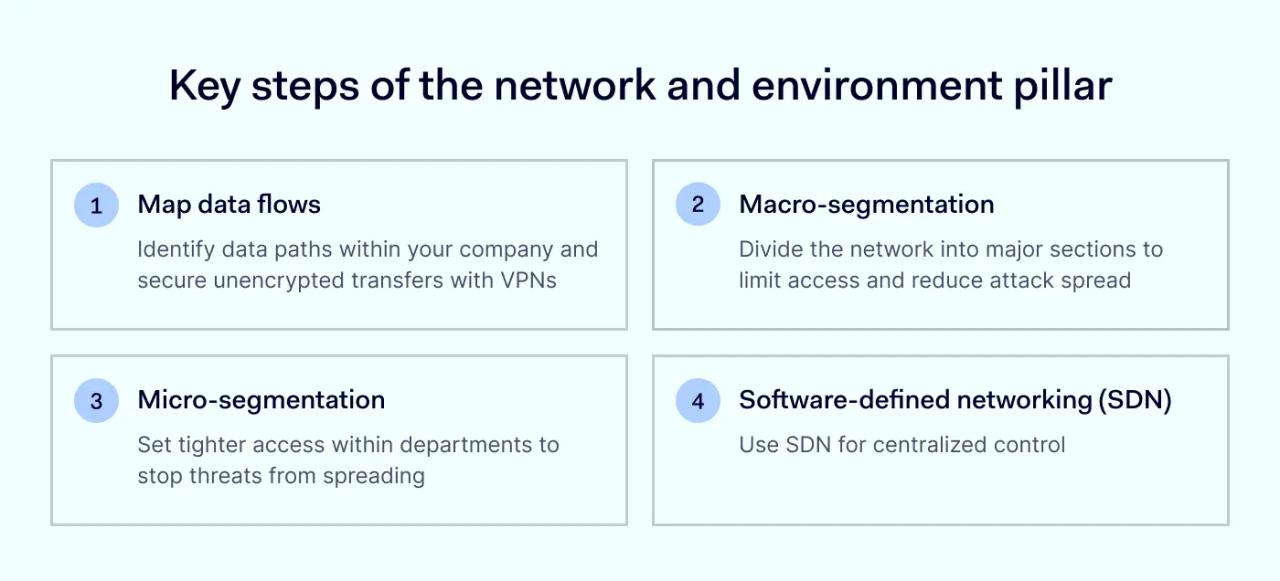
To protect networks, the NSA recommends following these steps:
- Map data flows. Identify data paths within your company and secure unencrypted transfers with VPNs
- Macro-segmentation. Divide the network into major sections to limit access and reduce attack spread
- Micro-segmentation. Set tighter access within departments to stop threats from spreading
- Software-defined networking (SDN). Use SDN for centralized control
These steps, based on Zero Trust principles, help reduce risks. To ensure a strong Zero Trust Architecture, focus on access control, network segmentation, and security tools.
4. Data pillar
The Zero Trust security model protects data through cataloging, labeling, and encryption. Constant checks keep data secure.
The NSA suggests a solid data plan to reduce breaches and spot problems fast:
- Data catalog and risk. Identify and list data types, then check risks of exposure or loss
- Data governance. Control who can use data and follow security policies
- Data labels. Tag data to improve control and awareness
- Data monitoring. Track who accesses data and how it’s used
- Data encryption and rights management. Encrypt data by tag and use Digital Rights Management (DRM) to block unauthorized actions
- Data loss prevention (DLP). Use DLP tools to stop unapproved data use or sharing
- Data access control. Limit access based on data type and user role
5. Application and workload pillar
The application and workload pillar secures applications by limiting access to what’s essential. It uses the least privilege principle. Security from other pillars of Zero Trust framework prevents unauthorized access or changes. This protects applications and workloads in on-premises and cloud environments.
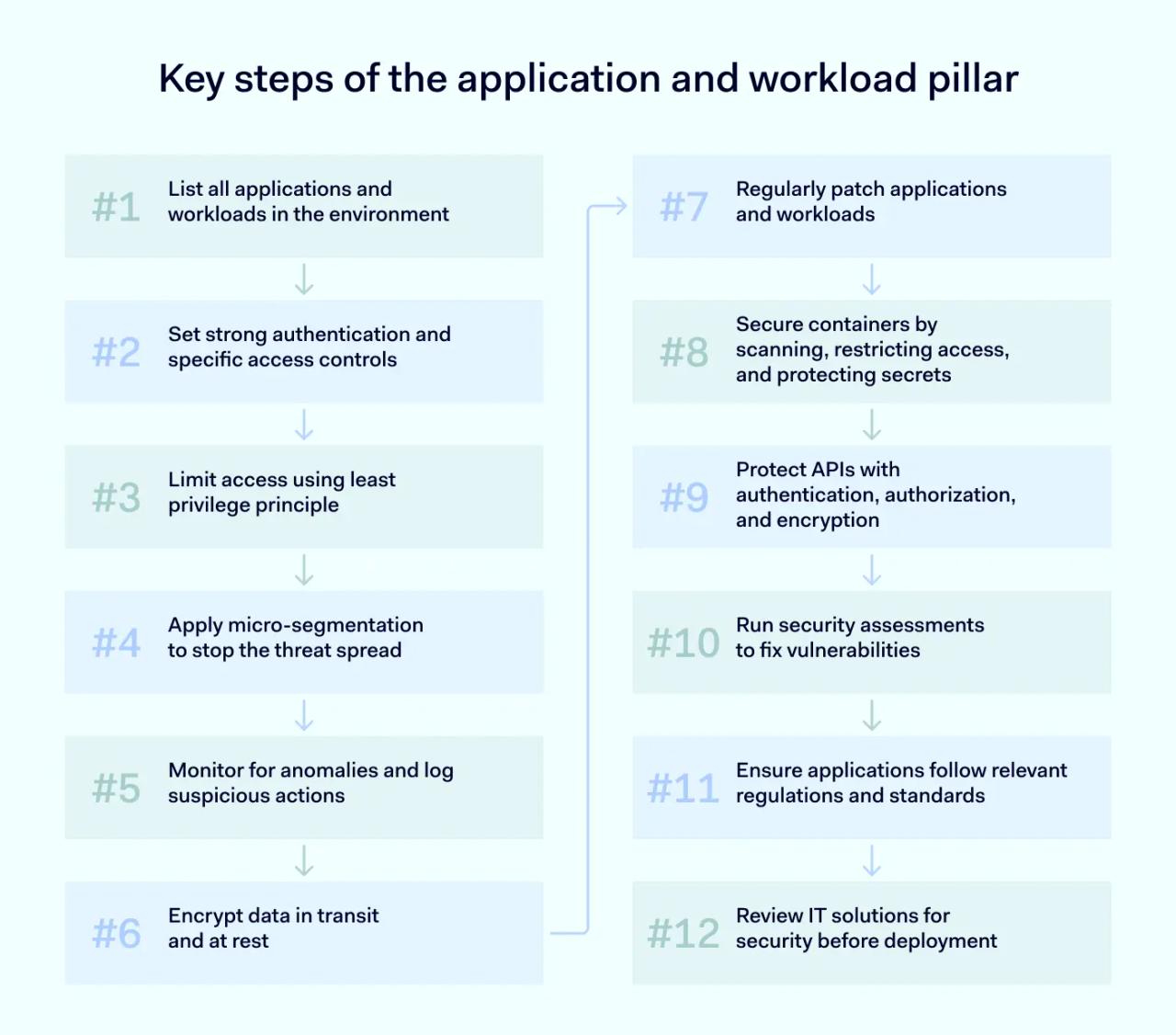
Here are the key steps to secure applications and workloads with Zero Trust security model:
- List all applications and workloads in the environment
- Set strong authentication and specific access controls
- Limit access using least privilege principle
- Apply micro-segmentation to stop the threat spread
- Monitor for anomalies and log suspicious actions
- Encrypt data in transit and at rest
- Regularly patch applications and workloads
- Secure containers by scanning, restricting access, and protecting secrets
- Protect APIs with authentication, authorization, and encryption
- Run security assessments to fix vulnerabilities
- Ensure applications follow relevant regulations and standards
- Review IT solutions for security before deployment
6. Visibility and analytics pillar
The visibility and analytics pillar in Zero Trust framework improves threat detection and security decisions. It monitors real-time network activity, collecting health, status, and behavior data across components. Logs from other pillars provide deeper insights.
This pillar allows faster threat response, investigation, and compliance by giving a full view of network activity.
Key parts of the visibility and analytics pillar:
- Log activity. Collect important logs from devices, apps, and data sources in one place
- Centralized Security Information and Event Management (SIEM). Gather, analyze, and alert on security data using dashboards and plans
- Security analytics. Check asset risks using setup info, weaknesses, and threat data
- User and entity behavior analytics (UEBA). Spot unusual user behavior with AI across many logs
- Threat intelligence. Use outside threat data for early detection
- Dynamic policies. Apply smart policies with AI, live data, and automatic updates
7. Automation and orchestration pillar
The automation and orchestration pillar makes quick, rule-based actions possible across the company. It applies security and operational tasks automatically. Tools like Security Orchestration, Automation, and Response (SOAR) and SIEM work together to manage security across all systems. Consistent security rules in Zero Trust help keep control and speed up responses to threats.
Key steps:
- Policy orchestration with decision points. Guide access decisions, with points gathering data and actions applied based on it. Separating these functions in Zero Trust makes the system more flexible and secure.
- Automating critical tasks. Reduces human error and speeds up tasks like setting up new users and approving access. RPA handles repetitive jobs, while AI runs constant risk checks and automated actions.
- AI-driven analysis. Finds threats fast by studying data, creating baselines, and automating responses. Human checks keep AI systems accurate and trustworthy.
- Machine learning insights. Spots unusual patterns in security events, user actions, and network traffic. Regular testing and human review keep models precise.
- SOAR integration. Automates security steps, speeds up incident response, and strengthens defenses by collecting data and coordinating tasks.
- Standardized data exchange. Boosts communication between systems by using common formats and APIs, improving compatibility across cloud and security tools.
- Coordinated security operations. Security Operations Centers (SOCs) use automation to collect data and handle threats smoothly. Regular updates to incident plans help reduce breach impact and keep business running smoothly.
Zero Trust pillars for business
For large enterprises, adopting the Zero Trust model is essential for a secure environment. By 2026, 10% of large companies to have a fully developed Zero Trust system. This is a huge increase from less than 1% at the beginning of 2023.
For companies of any size, following the key Zero Trust pillars helps protect critical data and systems from new cyber threats. Any organization might divide its network into sections so that only approved users can access specific areas, and only after strict security checks. This lowers the chance of insider threats or attackers moving through the system unnoticed.
Zero Trust framework addresses the real security problems that businesses face today. As more companies adopt its principles, the key parts of the Zero Trust model will become central to successful security strategies.
Companies should adopt Zero Trust pillars to stay protected as breaches become more common and costly. It will not only strengthen defenses but also make businesses more agile. With the right approach, security becomes a benefit, not a barrier, to growth.