Phishing seeks to deceive employees into handing over sensitive data or letting their guard down and is one of the most common cybersecurity threats. This article explains what phishing is, the main types of phishing attacks, and how to strengthen your security measures.
Phishing definition
Phishing involves obtaining confidential data via fraudulent messages or website content. Phishers seek to convince targets they are legitimate before using various methods to implant malware and achieve their goals.
How does phishing work?
The word “phishing” gives us a clue about how attackers work. Emerging in the 1990s, phishers started fishing for user credentials and other valuable data. The rise of email and the World Wide Web created new opportunities for cybercriminals (or “phreaks”) to contact and deceive their victims.
Over 30 years later, phishing has grown into an industrial operation. Criminals send 3.4 billion spam emails every day. Meanwhile, Verizon reports that 74% of data breaches start with a human error. With average data breach costs over $5 million, phishers are as prosperous as ever.
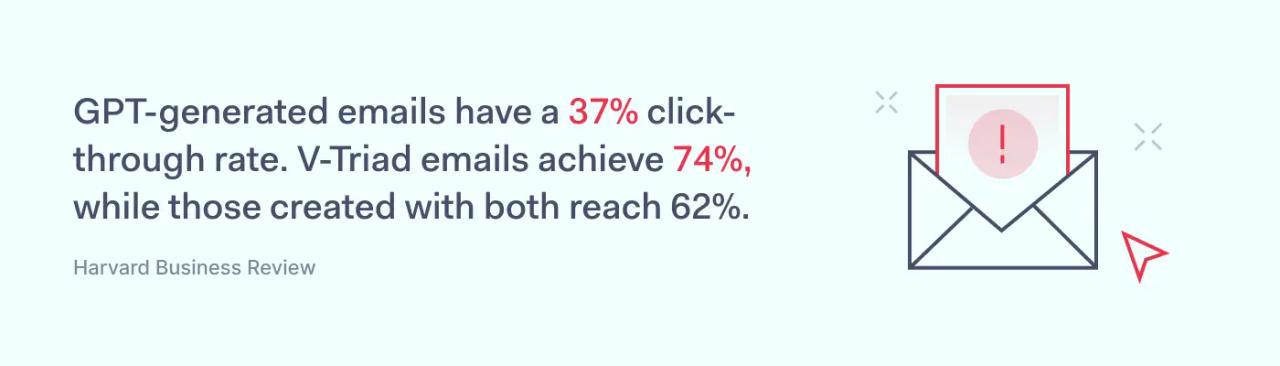
There are many types of phishing attacks. However, every attack has a common theme: cybercriminals pose as trusted contacts, prompting targets to take risky actions.
A trusted contact could be a colleague, a third-party vendor, a reputable corporation, or a government agency. Criminals create content that impersonates legitimate actors. Emails are the most common vector but co-exist with SMS phishing (Smishing), video, and phone-based methods.
Email phishing attacks generally include malicious links in written content or attachments containing malware payloads. Links direct targets toward fake websites, where attackers can harvest details or implant malware.
Successful phishers use social engineering techniques to craft persuasive messages. Attackers comprehensively research their targets, leveraging data available on the dark web to tailor their content.
AI-based tools are also changing how social engineers operate. AI tools can use data sets to generate believable scripts or even deepfake videos. As a result, attacks will become harder to detect.
Even alert, security-conscious individuals can fall for phishing tactics. Every employee is a potential data breach risk.
Types of phishing
Cutting the risk posed by phishing attacks starts with an awareness of how phishers work. Security teams can implement countermeasures to detect common methods, train staff, and respond to breaches when they occur.

Common phishing types include:
Phishing emails
Email phishing is the most common and familiar form of phishing. In this attack type, threat actors send phishing emails containing malicious links or attachments. Recipients may click links or download files without checking their legitimacy. Urgent or credible messages often trick them.
Attackers tend to imitate companies that are known to their targets. For example, Microsoft was the most imitated company in 2024, followed by Apple and LinkedIn. Attackers also frequently use consumer brands like Adidas and retailers like Amazon when targeting private individuals.
Spear phishing
Spear phishing refers to attacks against individuals or specific businesses. Phishers prepare spear phishing attacks by researching their targets. They create the illusion of legitimacy via personalized messages.
For example, attackers may learn from stolen data that an employee orders parcels from Amazon. They could use this information to send a fake failed delivery notification to the individual's work email address.
Attackers targeting companies build profiles of partner vendors and software solutions their target uses. They use that information to pose as maintenance providers, send fake security updates, or advise password resets.
SMS phishing (Smishing)
An SMS phishing attack uses text messages to send targeted content. Attackers may ask recipients to click links, download apps, or make phone calls to phishing centers.
This phishing type often succeeds due to the limitations of mobile devices. Smartphones make it harder for users to view embedded links and learn information about the sender. Attackers can shorten links to make detection harder.
Smishing is not a niche attack type. Around 75% of companies reported SMS phishing in 2023 as attackers branched out from traditional email tactics.
Pharming and page hijacks
Pharming attacks use fake websites to capture their targets. Victims click on links to legitimate websites. Cache poisoning then redirects users to fake websites that resemble the original. Users may enter credentials at these websites, unaware they have been redirected.
Page hijacks are also a form of phishing attack. In these attacks, criminals use cross-site scripting (XSS) to redirect search engine traffic to fake websites. High search rankings make websites appear legitimate, although they may contain malicious material.
Clone phishing
This is a sophisticated form of email phishing that requires prior access to confidential systems. Attackers copy emails received in the past by their targets. These phishing emails appear legitimate, but phishers have replaced previously legitimate links or files.
Cloning is often a secondary attack technique. Attackers gain access to network assets. They can then pose as colleagues or authorized users.
Voice phishing
Not all phishing attack types rely on text. Voice phishing (or vishing) uses Voice over IP or standard phone calls to fool targets and extract information.
Most vishing attacks start with users receiving notifications about compromised account credentials. Attackers inform targets they must reset credentials via telephone or VoIP connections. When they call, attackers use their privileged position to extract confidential information.
Voice phishing via phone has existed for decades. The technique continues at a high level, with around 70% of companies reporting vishing attacks annually.
Whaling
Whales are high-value individuals, often in the C-Suite tier at target companies.
Attackers know successful whaling attacks generally deliver higher rewards. Executives have greater access to resources and network privileges. They can do more harm if they fall victim to phishing attacks.
Executives also generate larger data footprints on the web. Attackers can research their roles, past, and affiliations. Skilled phishers can use personal information to pose as recruiters, consultants, or even friends of their targets.
For example, whaling attacks frequently issue commands from CEOs or CFOs to make payments. With skillful preparation, targets see the request as legitimate—even if cyber criminals eventually benefit.
How can you guard against phishing attacks?
The best practices below will help you protect against phishers. For more details, check out our in-depth guide about how to prevent phishing attacks.
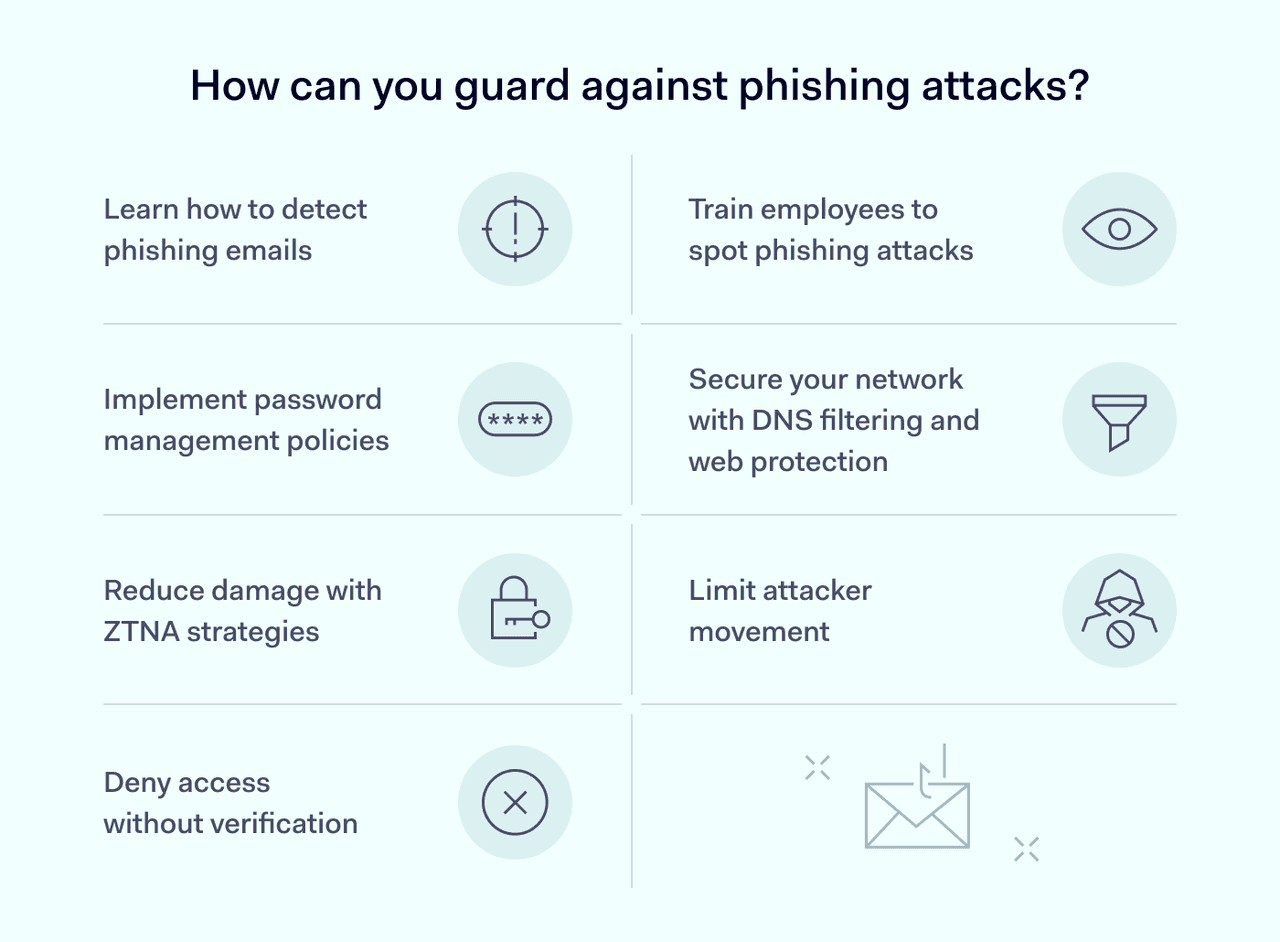
Learn how to detect phishing emails
Firstly, it's important to know the hallmarks of phishing emails. Phishing content usually contains flaws and signposts that betray its origins. Spotting those clues is essential. Common evidence includes:
- Errors in spelling sub-domains and URLs. Hover the cursor over the sender and embedded links to detect any suspicious text alterations.
- Suspicious sender addresses. Legitimate companies have standard email addresses. They won't use Gmail or other email providers to ask for confidential information.
- Urgency of tone. Phishers want recipients to act. They adopt an urgent style to create anxiety and prompt a rapid response. Legitimate companies tend to use more measured approaches.
- Requests for personal information. Legitimate businesses rarely send emails asking for financial data or login credentials.
- Lack of professionalism. Many phishers do not speak English as their first language. Their emails often contain grammatical or spelling errors.
Train employees to spot phishing attacks
Phishing awareness training is essential for all employees. Training should include ways to spot suspicious emails and procedures for verifying emails if employees have doubts. Run workshops and regularly use digital testing to check employee knowledge.
Put in place robust password management policies
Password policies should require regular password changes and enforce strong passwords for all login portals. These policies cut the risk attached to credentials theft. Ideally, stolen credentials should be out of date when attackers seek to use them.
Secure your network with access controls
Phishers generally seek credentials so they can gain access to confidential resources.
Stop phishing attempts before they start. Use DNS filtering by category to block malicious websites. Web protection stops users from visiting harmful sites used by attackers. These measures prevent stolen credentials and malware delivery.
If phishing succeeds, Zero Trust Network Access (ZTNA) strategies reduce damage. Multi-factor authentication (MFA) asks for one-time passwords or biometrics, making attacks harder. Access controls limit user privileges, restricting attackers' movement across the network.
ZTNA policies help verify identities before granting access. Without verification, users are denied. Network segmentation adds extra protection by isolating sensitive resources. This limits exposure even if attackers breach the network.
