Effective network security solutions must detect and mitigate threats before they escalate into network downtime or data breaches. Intrusion detection and prevention solutions (IDPS) meet these two critical needs by monitoring traffic and automating responses.
This article explores what IDPS solutions are and how they work, before offering some best practices to ensure a successful implementation.
What is an IDPS?
An intrusion detection and prevention system (IDPS) is a security solution that monitors traffic, detects threats, and automatically implements mitigation actions. IDPS contrasts with intrusion detection systems (IDS), which lack automated response features.
How does an IDPS work?
Intrusion detection and prevention solutions monitor network traffic in real-time to detect and mitigate threats. As the name suggests, IDPS has two critical functions: detection and prevention.
Detection refers to identifying cyber threats and malicious behavior.
IDPS uses two main techniques to identify threats. Anomaly-based detection tracks deviations from behavioral baselines that suggest active cyberattacks. Signature-based detection compares network activity patterns with known malware attack signatures drawn from threat intelligence databases.
Prevention refers to the mitigation actions following a positive threat detection.
Intrusion detection and prevention systems analyze traffic and automatically apply network security measures. Actions could include connection resets, dropping malicious data packets, or locking user accounts. IDPS solutions may also escalate serious threats for triage and in-person analysis by security teams.
Benefits of an IDPS
IDPS solutions bring many potential benefits for users.
- Real-time monitoring: Security teams benefit from real-time in-line threat detection, enabling rapid identification of cyberattacks.
- Automated prevention measures: Automated threat responses block malware and exploit attacks, limiting the scope for data theft or network damage.
- Proactive cybersecurity: Automation also saves time. Security professionals can concentrate on targeted actions such as threat hunting or analyzing intelligence feeds. In this way, passive IDPS solutions facilitate proactive cybersecurity strategies by removing the need for repetitive manual tasks.
- Improved compliance: IDPS solutions also have compliance benefits. Companies can log incidents and mitigation actions after identifying suspicious network activity. This enables businesses to take "reasonable steps" to secure data: a core compliance requirement of HIPAA and PCI-DSS regulations.
- Defense-in-depth: IDPS also has advantages compared to IDS solutions. Where IDS solutions identify threats, IDPS prevents attacks. This adds an extra layer to defense-in-depth strategies.
Types of IDPS
IDPS is not a one-size-fits-all solution. There are many types of intrusion detection and prevention systems, and organizations need a solution to suit their circumstances.
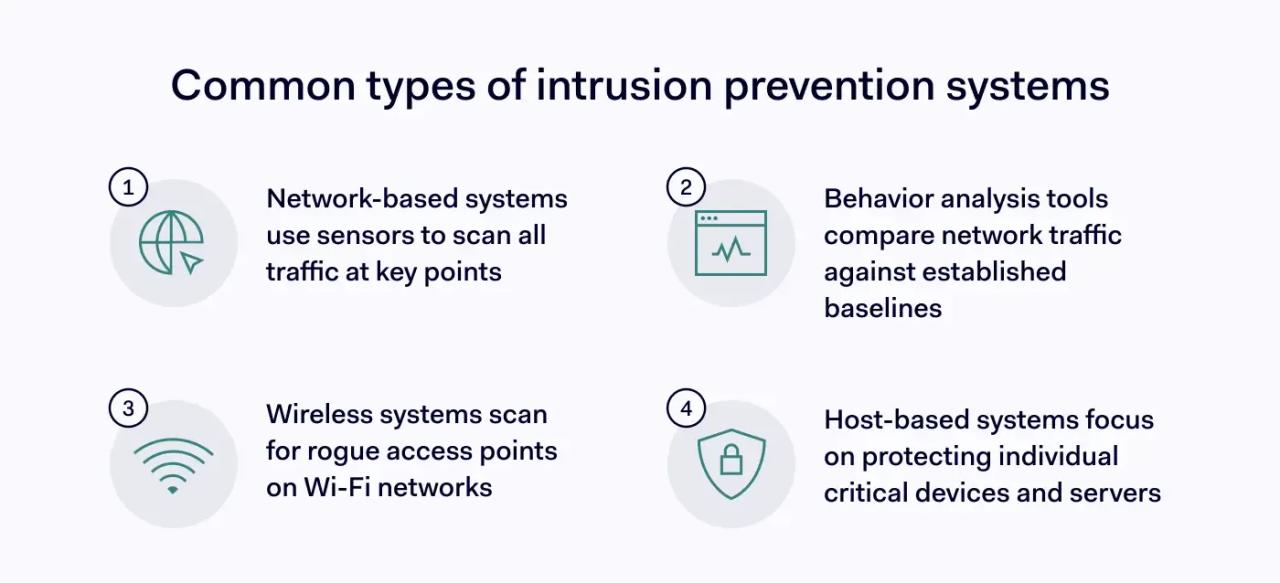
Common IDPS types to consider include:
Network-based IDPS (NIPS)
These IDPS solutions deploy in-line sensors at strategic points across a company's network infrastructure. Sensor locations are chosen to capture and scan all network traffic. For example, technicians may deploy NIPS sensors on routers, switches, remote access points, or behind network firewalls.
Standard NIPS systems use centralized detection tools that compare network traffic patterns with a pre-defined activity database. Security tools correlate real-time traffic against definitions of malicious behavior or malware signatures. If they discover a match, automated prevention systems fix vulnerabilities, remove threats, and alert security teams.
Network behavior analysis tools (NBA)
NBA is a variety of network-based IDPS that actively scans for suspicious activity patterns. Scanning tools compare traffic with acceptable baselines. Baselines may be static and manually maintained, although machine learning can also dynamically adjust baselines to reflect network conditions.
NBA is a particularly effective tool for preventing denial-of-service (DoS) attacks. IDPS solutions immediately detect traffic patterns associated with DoS incidents. Systems that assess incidents individually are often slower to detect DoS attacks, leading to reactive security tactics.
Wireless intrusion prevention systems (WIPS)
WIPS IDPS systems are designed to protect wireless networks. These IDPS solutions scan wireless radio frequencies for rogue access points or unauthorized device connections linked to evil twin attacks. Companies can deploy secure wireless systems, enabling flexible on-site and remote work.
Host-based IDPS
Host-based IDPS solutions protect individual devices that require additional cybersecurity measures. For example, healthcare companies may use host-based IDPS to protect servers that contain sensitive private health information. Protecting network gateways is another common use case.
Host-based IDPS monitors traffic on the host device, data integrity, active processes, and application activity. Solutions detect suspicious TCP/IP traffic and operating system activity.
IDPS techniques
IDPS protects wireless networks, individual hosts, or entire network environments. However, what techniques do IDPS solutions use to detect and prevent threats?
Critical IDPS techniques on the detection side include:
Signature-based detection
Signature-based IDPS correlates network traffic with known malware signatures. In this case, a signature is a consistent pattern of activity that is unique to a specific threat. Signatures often identify malware agents, but also refer to exploits and credential stuffing attacks.
Monitoring tools detect signature matches in real-time. When they make an identification, IDPS systems apply automated responses or deliver alerts to security teams.
Signature-matching is effective at detecting known threats. However, it cannot defend networks against new or evolving threats that are not stored in signature databases.
Anomaly-based detection
Anomaly detection looks for unusual patterns of behavior. Detection tools compare samples of network traffic with established baselines. Baselines record network conditions that apply if malicious activity is not present.
Deviations from baselines trigger automated responses and alerts. For example, IDPS systems may detect traffic spikes, failed login attempts, or protocol anomalies.
Anomaly detection detects novel threats, but can deliver large quantities of false positives. AI-based detection systems may solve this problem, allowing instant detection of novel and advanced threats.
Protocol-based detection
Protocol-based threat detection applies protocols or policies to network traffic. For example, security officers may define a protocol as "verifying all transfers of this file format" or "preventing access from [x] location."
Detection tools enforce policies and block violations. This is a simplified detection solution, but it helps when implementing network-wide security policies.
Techniques to prevent and mitigate threats include:
Alerts
IDPS tools detect anomalies and deliver alerts to relevant security personnel. Sophisticated detection systems triage incidents and determine whether to raise alerts or administer automated responses.
Automated blocking
Prevention systems respond to incidents by blocking traffic. For example, many failed logins may be linked to a single IP address. In this case, the system blocks that IP address to protect against unauthorized intrusions.
Security environment changes
If necessary, prevention systems alter network settings to block threats. For example, IDPS solutions may change firewall settings to regulate traffic flows or request additional authentication factors to access resources affected by security incidents.
Sanitizing traffic
Security tools automatically filter email traffic and remove suspected phishing content, or prevent access to malicious websites. This sanitization can also strip malicious scripts from web pages or remove harmful attachments from incoming files. By cleaning the data in transit, the IDPS neutralizes the threat before it can execute on the target system.
Best practices for implementing IDPS
IDPS is a powerful suite of detection and prevention tools. However, companies must implement intrusion detection and prevention tools strategically to suit their network requirements. Use the best practices below to guide your deployment strategy:
- Map your network to position sensors: Detection tools must cover all network gateways and critical assets. Map your network environment and strategically place sensors at servers, gateways, or databases.
- Take care to establish accurate baselines: Don't take shortcuts when generating activity baselines. Use extended learning periods to obtain high-quality data. This vastly improves the accuracy of threat detection systems.
- Use context-specific rules: Detection and prevention solutions may come with pre-defined rule or policy sets. Disable irrelevant rules to suit your operational context and ensure streamlined threat management.
- Integrate with other security tools: Detection and prevention tools should integrate seamlessly with SIEM, data loss prevention, antivirus, and threat intelligence solutions.
- Regularly audit your IDPS implementation: Security solutions require periodic maintenance audits to verify performance and make improvements. Remember to update signatures regularly and apply software patches when available.
- Go beyond passive detection and response: Leverage IDPS to enable proactive threat hunting. Use deep packet inspection and data collection functions to explore indicators of compromise (IoC) and combine IDPS outputs with global intelligence feeds.
Defend in depth with intrusion detection and prevention solutions
IDPS solutions combine real-time threat monitoring and automated mitigation. Signature and anomaly analysis work alongside proactive prevention to provide a critical layer of defense. When strategically implemented and integrated, IDPS protects network integrity, aids compliance, and enables a proactive security posture.
