Secure Access Service Edge (SASE) technology is the most effective way to secure cloud-based networks. Blending strong edge protection, identity management, network segmentation, and cloud brokerage, SASE aligns perfectly with the needs of contemporary organizations. This NordLayer explainer will explore how to use SASE and best practices to follow when exploiting its capabilities.
Why is it time to implement SASE?
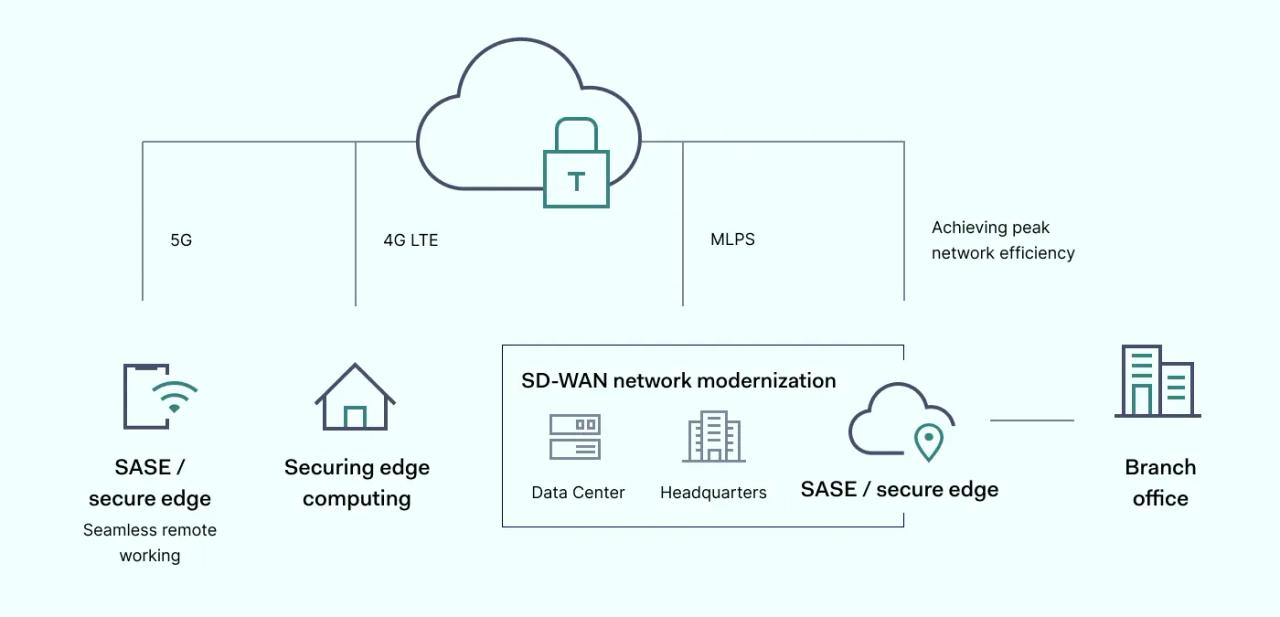
SASE is not a single app. Instead, it is a cloud delivered model with plenty of real-life use cases to secure and optimize modern networks. SASE deployments can solve some pressing challenges that businesses face. Examples include:
1. Boosting security and lowering costs with SD-WAN network modernization
Traditional MPLS networks are a poor fit for companies reliant on multiple cloud applications and large communities of remote workers. Older perimeter-based systems fail to provide sufficient protection for cloud data centers and suffer from inefficient traffic routing. They also result in excess costs relative to agile, SASE-based alternatives.
SASE operates a dynamic SD-WAN perimeter, automatically identifying users at the network edge and separating their traffic from other network resources while they connect to corporate assets. With SD-WAN, users anywhere can securely and efficiently access apps and resources across multi-cloud environments.
Data Loss Prevention (DLP) tools can integrate with SASE, even guarding sensitive data outside the network perimeter. Cloud brokering allows secure access to core resources by concealing SaaS applications from outside observers while Secure Web Gateways and Identity and Access Management (IAM) tools limit access to authenticated users only.
2. Seamless remote working
SASE is the optimal networking solution for geographically distributed workforces. In an age of working from home, remote working, and hybrid solutions, security systems must secure a complex array of endpoints and devices.
With a SASE solution in place, achieving secure access for a remote workforce is simple. IT teams can apply Zero Trust Network Access (ZTNA) principles uniformly, bringing remote work under the same security umbrella as on-premises staff.
SASE does not rely on older VPN technology to encrypt traffic and defend perimeters. Virtual Private Networks tend to struggle as traffic rises, leading to network bottlenecks. They also struggle to scale effectively as user communities grow, and lack lateral threat protection within network boundaries.
SASE adopts a more flexible approach, relying on SD WAN networks, globally dispersed PoPs and local inspection at every edge node. This approach delivers greater threat protection than standard VPNs, while boosting network efficiency.
3. Securing edge computing
The network edge has changed in recent years, encompassing sensors and IoT devices that pose significant challenges to standard wide area network models. Botnet operators have mobilized edge devices to mount global DDoS attacks. They are also difficult to monitor and map using conventional security approaches.
SASE is the ideal alternative for companies dependent on industrial sensors, self-driving vehicles, or accessories such as health monitoring products.
SASE solutions automatically scan and authenticate all edge devices when they connect to the network. IT teams enjoy complete visibility of all connected devices via central admin consoles, and managers can easily extend security policies to each device.
4. Achieving peak network efficiency
SASE use is also a route to optimizing network efficiency in multi-cloud settings. Modern networks often involve multiple cloud vendors and services. Vendor proliferation can create overly complex, inefficient enterprise networks characterized by compromised performance and flawed user experience.
SASE offers a route to improved performance via multiple-point solutions. Distributed PoP exchanges are close to cloud assets and other traffic sources. This setup minimizes the hops required for packet transmission, ensuring almost zero latency between SASE PoPs and crucial cloud applications.
SASE architecture also makes adding new branch locations to corporate networks easy. There is no need to backhaul traffic to central data centers. With SASE, traffic can flow rapidly and safely to globally distributed PoPs. So wherever access is needed, speeds should be superior to older security systems.
5. Making cloud modernization simple
Many businesses have swapped on-premises data centers for cloud alternatives without rationalizing their network architecture. Chaotic digital migrations create needless complexity, and complexity can lead to security risks as IT teams lose control of the threat surface.
SASE use provides an effective way to simplify network security. IT teams can integrate cloud assets and apply security controls via a single admin console. Technicians can monitor threats and respond when needed while networking professionals can assess network performance.
At the same time, technologies such as SWG and Cloud Access Security Brokers (CASB) allow companies to enjoy the benefits of cloud computing while mitigating security risks. Global data flows such as customer transactions or dynamic pricing information can remain confidential without compromising speed. And contractors or employees can access cloud services safely, wherever they are.
6. Streamlining IT management
SASE use also generally contributes to leaner, more efficient network management. Centralized admin consoles and bundled security functions reduce the need for multiple solutions such as VPNs, firewalls, or threat scanning tools.
Multiple solutions increase the time required to update and maintain network infrastructure. SASE reduces maintenance time to an absolute minimum. Everything is centrally located and cloud-native. IT staff can focus on perfecting the security posture and threat monitoring instead of wasting resources on unnecessary tasks.
7. Business scaling without security gaps
Businesses rarely grow steadily. Sometimes spikes in sales or strategic changes can result in rapid expansion, and networking infrastructure may not be able to handle increased traffic or user communities.
SASE provides the best solution for digital businesses as they grow, allowing for totally consistent policy enforcement.
For instance, expanding companies may take on new contractors as partners. In that case, SASE applications can automate new user onboarding. Strong user identity authentication and tracking tools also provide reassurance when onboarding third parties by plugging security gaps before they cause problems.
Distributed PoPs also serve companies as they expand globally, avoiding traffic bottlenecks. And switching cloud service providers is radically simplified when centralized admin consoles are available.
SASE best practices
SASE has a wide range of relevant use cases and offers many benefits relative to traditional network architecture. However, as with all technologies, it must be deployed correctly to achieve optimal results. Here are some best practices that will make transitioning to SASE much easier.
1. Make Zero Trust a guiding principle
Achieve the best possible security posture by combining SASE technologies with Zero Trust approaches. Zero Trust Network Access (ZTNA) rests on the maxim “never trust, always verify.” ZTNA entails identifying and authenticating every user identity and micro-segmenting networks to control user privileges and contain potential threats.
SASE use provides a platform to implement Zero Trust ideas. SWG, CASB, and SD-WAN give IT teams the power to verify every user. Technicians have complete visibility and real-time information about every packet passing through SASE PoPs.
2. Plan the right mix of on-premises and cloud infrastructure
The SASE model applies to data passing to and from cloud applications, but most companies are not cloud-only. Instead, they will need security solutions encompassing both cloud and on-premises infrastructure.
Companies relying on local and remote infrastructure may need to retain on-premises firewall defenses or physical security measures to protect data centers. In these cases, planners need to decide what assets they can safely hold in the cloud and what remains local.
If companies intend to increase remote working or migrate to SaaS in the future, implementing SASE solutions sooner rather than later makes perfect sense.
3. Choose SASE vendors wisely
The benefits of SASE use can evaporate if vendors supply poor quality products lacking full functionality or leave clients without adequate support. Not all SASE dashboards are equal, for example. Some lack real-time threat monitoring or traffic data, while others cannot apply ZTNA basics like Identity Management.
Test software before purchasing to ensure a seamless user experience. And try to avoid building a SASE tech stack from multiple vendors. Some companies may have in-house tools to add to the mix, but the whole idea of SASE is to simplify cloud security. Ideally, a single vendor will supply everything required.
4. Plan smooth, gradual SASE transitions
Implementing any digital changes can be disruptive, and SASE is no exception. Avoid rapid handovers from legacy wide area network models to SD WAN and cloud access security. Instead, plan gradual transitions from the software and hardware currently in use.
Execute any migration from on-premises hardware to cloud alternatives with care and allot sufficient time for secure migrations. Test constantly to ensure data remains secure and employee workflows are not impaired. And explain every transitional step to core stakeholders to avoid disputes and confusion.
5. Create detailed inventories to understand change
If possible, align SASE migrations with existing hardware life cycles to reduce redundancy costs. To do so, make a complete inventory of existing hardware, making how projects will phase out previous perimeters without compromising security.
This inventory acts as a map to guide SASE transitions and provides the basis for cost-benefit calculations. This information will be invaluable when assessing the short-term costs and longer-term savings associated with SASE implementations.
6. Be prepared to audit and update your cloud security stack
Like any other cybersecurity product,SASE services are subject to constant revision and refinement. Plan to update every element of your security stack as frequently as possible and investigate additional tools when they become available.
Some SASE solutions will work well for a while but fail to accommodate business expansion or the addition of new SaaS apps. Some vendors will lose focus on contemporary threats and leave security weaknesses in their products. Stay aware of the market and audit your setup to ensure that every aspect is best in class.
Modernize cloud operations with SASE network security
As the list of SASE use cases above shows, Secure Access Service Edge technology has an important role to play in securing modern cloud-based networks.
Whether companies are opening branches abroad, switching from an on-premises corporate data center to cloud services, experimenting with edge computing, or serving remote workers, SASE use can help.
SASE deployments should be simple and beneficial, but making the change from traditional enterprise network management can be disruptive. However, if you follow the SASE best practices outlined here you can reap the benefits while avoiding common mistakes.