Payment Card Industry Data Security Standards (PCI-DSS) regulate companies that handle or store cardholder data. These standards are a core concern for most online sellers.
Password hygiene is one of the most important aspects of PCI regulations. Compliant organizations need password policies that meet PCI-DSS requirements. But what does this mean in practice? How can organizations change their policies to achieve compliance?
PCI-DSS 4.0 introduces major changes to compliance, impacting how businesses protect cardholder data. Understanding the updated requirements is crucial to staying compliant and avoiding penalties.
In this article, we will explain the key PCI-DSS 4.0 password requirements and list the actions needed to meet industry regulations. We will also cover important updates, such as password rules and stronger authentication methods.
What is PCI-DSS 4.0?
PCI DSS 4.0 is the latest version of the Payment Card Industry standard, introducing important changes in compliance. This version highlights:
- Greater focus on cloud and service providers
- Expanded requirements covering more areas
- Emphasis on a risk-based approach to security
The compliance deadline was March 31, 2024, with many new rules becoming mandatory by March 2025.
One of the biggest shifts is the introduction of the "Customized Approach," which allows companies more flexibility in meeting security goals. This approach gives businesses the choice to adapt controls based on their needs. Other updates include stronger authentication (like multi-factor), stricter password rules, and better protection against phishing.
Many new requirements are complex and expensive, so companies are given time to comply. If your business handles cardholder data, start planning now for these changes.
Understanding the PCI DSS 4.0 password requirements
Passwords are one of the most important attack vectors for data thieves and other malicious actors. Attackers can steal credentials via brute force attacks or buy leaked passwords online. They can also sometimes use unchanged default passwords to access apps and cardholder data.
There are many security risks connected to passwords. That’s why PCI DSS 4.0 compliance includes a range of requirements to strengthen password usage
Password security is a familiar part of general cybersecurity systems. Achieving compliance with PCI password requirements is not complex. However, compliant organizations need to be thorough. Many steps and measures are involved, and this checklist covers them all.
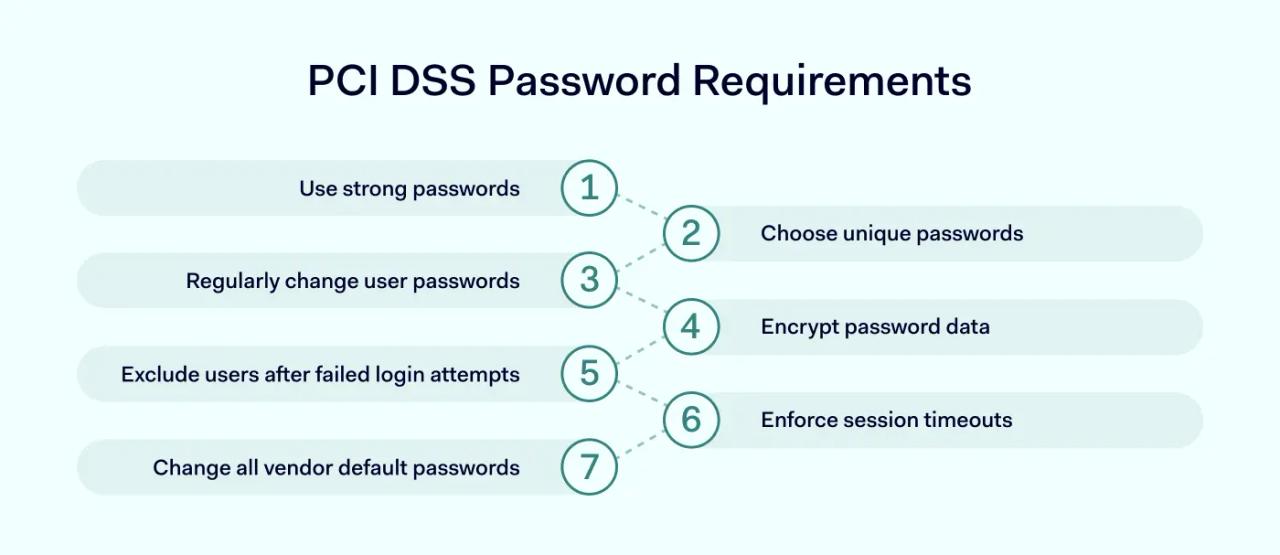
Requirement 1: Use strong passwords
A strong password is almost impossible to guess and is not related to information about the individual user. PCI-DSS 4.0 security standards include a strict set of criteria for strong passwords. And every user on the network needs to fulfill these rules:
- Password length. Passwords should be at least seven characters long. This is a minimum length. Ideally, organizations will demand longer passwords. More than 12 characters are optimal, and going beyond the minimum length is preferable. The more characters in a password, the more computations are needed to carry out brute-force attacks, so extending password lengths makes sense.
- Password complexity refers to using diverse characters to create passwords. Users should not rely on weak passwords made solely from alphabetic characters. Administrators must require a mixture of upper- and lowercase letters. Users should also add at least one number and a special character.
It is important to enforce both complex passwords and diverse characters. Left alone, users often resort to long dictionary words. These terms are generally seen as weak passwords. They are easy to remember but also easy to guess. Blending long and diverse terms solves this problem.
Requirement 2: Choose unique passwords
Passwords should be unique to each user. Users should not share passwords on the same account. Each user must have their ID and password, and breaches of this policy should result in disciplinary action.
Users should not use the same password on different services—even services used in their personal lives. Many people rely on familiar terms to make life simpler, but this is extremely risky. If attackers force credentials on one platform, they can access the user’s logins across all other gateways.
Requirement 3: Regularly change user passwords
Eventually, all passwords are compromised. PCI-DSS 4.0 password requirements solve this problem by demanding regular password changes for every network user.
PCI regulations state that users should change their passwords every 90 days. Administrators should not rely on user initiative to make changes. The 90-day limit should be part of a compliant password policy. Users should receive reminder emails before expiry. Access should be denied if changes are not made within the time limit.
Admins should also prevent recycled passwords. Users may alternate between two passwords for convenience. But this is risky from a security perspective.
Requirement 4: Encrypt password data
Organizations must encrypt all password data at rest on their servers or ensure that cloud service providers encrypt hosted data. Encryption should also apply to password data in transit across network infrastructure. Use 256-bit encryption with no known weaknesses, and use secure storage to restrict access to encryption keys.
Requirement 5: Exclude users after failed login attempts
The password policy should include measures to guard against illegitimate logins. PCI standards state that users should have a maximum of six login attempts.
The system denies access if the user fails to provide the right credentials. The user is then denied access until they change their password via secure channels. Denial of access is preferable to locking users out for specific periods. Users will need to inform administrators of the issue. Admins can then check for potential threats and take necessary action.
It’s also important to ensure that users do not recycle compromised passwords. Users often resort to familiar passwords to make life simpler. But compromised passwords will always represent a security risk. Automate systems that reject previously used passwords and prompt users to choose a new term.
Requirement 6: Enforce session timeouts
Inactive users pose a critical security threat, and PCI standards recognize this. Inactivity could be evidence that employees have left their workstations. If they are working remotely, security teams have no way of knowing whether the device was exposed during their absence.
To achieve PCI compliance, administrators should automatically exclude users after 15 minutes of inactivity. Alerts can inform users if the timeout is approaching, but enforcing timeouts is a good way to minimize data breach risks.
Requirement 7: Change all vendor default passwords
Companies rely on third-party apps and devices within their cardholder data environment. All of these services come with default settings, including passwords. These passwords are usually either publicly available or easy to guess.
Attackers can easily gain access to credit card data if admins fail to change default passwords. Make these changes part of your basic security policies. And enforce unique passwords for all assets.
Are the PCI 4.0 password requirements sufficient to prevent cyber-attacks?
PCI-DSS 4.0 password regulations should not be seen as a comprehensive shield against cyber-attacks. The regulations seek to protect cardholder data and reduce basic data breach risks. But without reinforcement, they leave significant gaps for attackers. Relying on PCI-DSS rules is a risky strategy.
Passwords are also not the only critical cybersecurity issue. Companies need strategies to harden network devices and protect the network edge. Firewalls, threat detection systems, and access management all have roles to play.
Remote access is also an important security risk. Strong passwords cannot eliminate security risks related to remote work. Companies need to use secure gateways and Virtual Private Networks to encrypt traffic. And they also need to train employees to prevent phishing attacks. Password policies are irrelevant if staff compromise network assets by clicking on malicious links.
How can PCI password requirements be enhanced?

Online businesses should take all available actions to minimize data breach risks. PCI-DSS password requirements are useful but insufficient. Various ways can supplement PCI rules, such as adding extra controls to secure sensitive data.
1. Put in place multi-factor authentication (MFA)
MFA and two-factor authentication (2FA) add another set of barriers to unauthorized entry. Both systems require additional credentials before allowing access requests.
There are many ways to design a multi-factor authentication solution. For example, two-factor authentication could include one-time codes delivered via electronic tokens or smartphones. MFA can also leverage biometric factors such as retina and fingerprint scans.
MFA best practices advise against applying authentication factors without careful planning. It’s important to streamline access as much as possible. If the user experience is too complex, users can work around authentication systems via insecure solutions. So weigh up the benefits of MFA vs 2FA and take your business context into account.
Focus on protecting critical parts of the cardholder data environment (CDE). This will meet PCI-DSS requirements and limit the need for time-consuming authentication processes in other parts of the network.
2. Use a secure password manager
Password managers automate many PCI password requirements and make life easier for both administrators and users. A password manager solution will:
- Generate strong and unique terms automatically.
- Ensure that passwords are not recycled.
- Prohibit password sharing between different accounts.
- Store password data securely via encryption.
- Streamline user requests to change passwords or solve access problems.
With a password manager, users can autofill login forms without compromising security. Passwords are not stored locally. They are protected by watertight encryption, preventing wholesale credential theft.
Cutting-edge password managers combine these functions with passkey holders. These secure authentication tokens remove the need for character-based passwords and work well with mobile devices.
3. Use threat intelligence tools to screen leaked passwords
Cyber attackers routinely steal and sell user credentials. However, targeted organizations are not always aware of leaks. This opens the door to attacks via stolen passwords. Attackers can simply hijack existing accounts without users or admins knowing about their activity.
Threat intelligence databases offer a solution. These tools constantly monitor the Dark Web and other markets for stolen credentials. They deliver automated alerts when network users seek to use stolen passwords. And they enforce password changes if they detect a match.
4. Maintain a password blacklist
Users often fall back on basic passwords to streamline access. But this is far too risky from a PCI compliance perspective. Companies should leverage all available tools to eliminate basic passwords from their databases. And blocking commonly used terms is a good place to start.
Password blocklists include the most popular terms (such as “ABC123” or “default,” for example). You can change blocklist settings to add common dictionary words. And you can make blocking context-specific. For instance, you might want to block any terms related to the user’s job role, name, or location
Conclusion: meet PCI password requirements with careful planning
An effective password policy is a critical part of PCI compliance. PCI-DSS regulations require organizations to demand strong, regularly changed passwords. Compliant companies must encrypt password data, manage failed logins, and enforce timeouts for inactive users. And sharing user passwords is completely prohibited.
Multi-factor authentication, password managers, and threat intelligence tools add extra security. They may not be necessary for lower-level PCI compliance, but at higher PCI levels, they are essential.
Putting these measures in place requires planning. The password policy must cover all users, including third parties with CDE access. Administrators also need to assess vendor-supplied apps to remove default passwords.