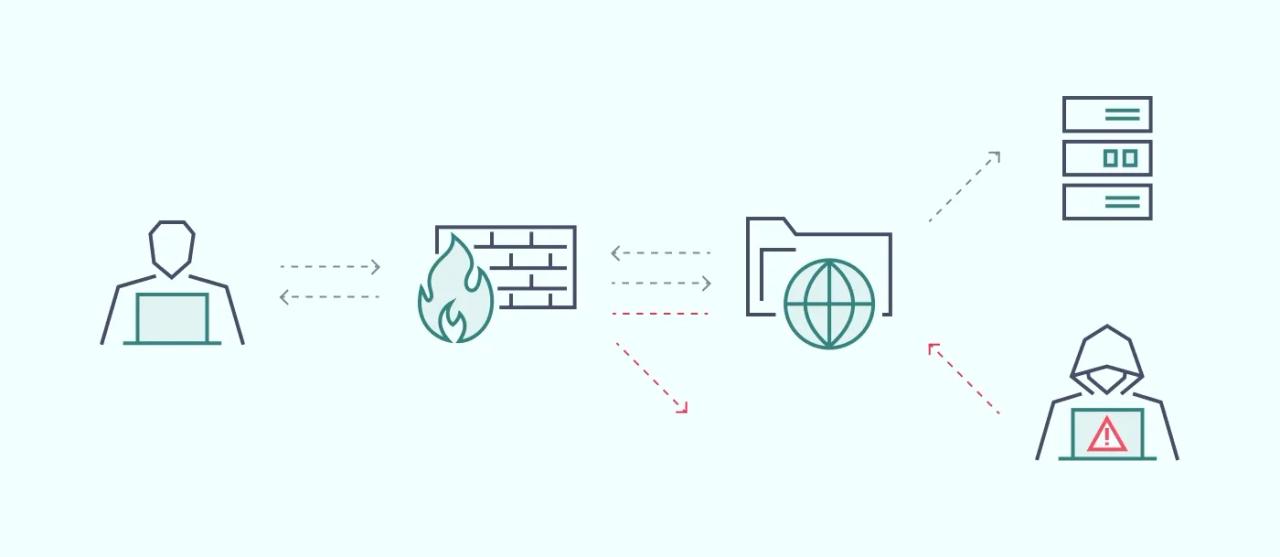
Imagine your network as a busy office building with multiple entry points. Just as a security guard checks IDs at the door, a firewall ensures that only trusted traffic gets in, blocking anything suspicious before it can cause harm.
Firewall definition
A firewall is a computer security system that monitors and controls filtering traffic. The software or hardware unit selectively blocks malicious traffic or allows data packets to pass through, following established security rules.
A firewall is often positioned as a barrier between the public internet and your device or network. It protects networks against various online threats. A firewall is one of the fundamental staples of network security that has always adapted to the changing cybersecurity landscape.
The role of a firewall in network security
Firewalls are used in business and consumer settings to enhance network traffic management and security capabilities. The main use cases of this tool are intercepting incoming malicious packets or creating segmentation within the network. Configuring a firewall according to specific security rules allows network administrators to have additional controls within a network.
Apart from threat defense, firewalls contribute to cybersecurity intelligence by performing logging and auditing functions. The logs can then be analyzed to improve security policies. At the same time, this helps to paint a broader threat landscape that businesses face daily.
Finally, firewalls with added DNS-based filtering can also be used for content filtering, especially when set up within the network and firewall rules. By denying unwanted URLs and IP address ranges, network administrators can deny remote access to various websites.
How does a firewall work
A firewall filters traffic that enters or leaves a network. It acts as a gatekeeper, allowing or blocking data based on pre-set rules. These rules inspect information like the source and destination IP addresses, port numbers, and protocols to decide if the traffic is safe.
For example, if a packet of data is coming from an untrusted network, the firewall will block it to prevent any harm to the network. Firewalls can also detect if the content of the data is harmful, such as identifying malware hidden within the data. This ensures only safe, legitimate traffic can pass through.
Types of firewalls based on the method of operation
Despite the naming, firewalls can have numerous differences that set them apart.
Proxy firewalls
A proxy firewall protects network resources by filtering exchanged application layer packets. Users connect to the gateway (or proxy) between a local network and the public internet. A proxy firewall is set up on the server inspecting outgoing traffic packets and creating a connection to other web servers.
The same process happens in reverse when a web server initiates a connection back to the client, inspecting what is being sent. This eliminates a direct network connection, between the client and the web server, enforcing the established security policies.
One of the biggest flaws of a proxy firewall is when a single proxy server is assigned for multiple users, and sometimes the proxy server can be a bottleneck in terms of efficiency. Exponentially, the processing time at every exchange can take longer with each user. Higher latency is something that network administrators have to take into consideration when contemplating this method.
Stateful inspection firewall
Stateful firewalls keep track of incoming and outgoing traffic and monitor active network connections while analyzing incoming traffic. Operating at network and transport layers within the OSI model, it intercepts packets and derives data for analysis to improve security. All information from previous interactions and events is retained rather than inspecting every incoming data packet, making its operations much faster.
Context is the primary foundation for a stateful inspection firewall for all of its decisions. In practice, a firewall will allow incoming data packets only if certain specific conditions are met. It also applies to ports, as they can be closed unless a connection requires access to a specific port. This stops attack patterns when hackers are scanning for the ports that are left open.
One of the biggest vulnerabilities of a stateful inspection firewall is that it can be manipulated. Some stateful firewalls can attract outside connections with simple actions like viewing a webpage. In addition, they are extremely susceptible to man-in-the-middle and denial-of-service attack types.
Next-generation firewalls (NGFW)
According to Gartner, NGFWs are highly sophisticated network-based firewalls that can be implemented in either software or hardware. This type greatly expands the functionality of network address translation firewalls allowing them to detect and block sophisticated attacks at application, port, and protocol levels.
Some of the advanced NGFW functions include:
- Deep packet inspection (DPI)—looks at packet payloads and checks which applications are accessed by the packets.
- Application awareness—firewalls check which applications are running and which ports they are using. It can neutralize certain types of malware that can aim to terminate a running process and take over its port.
- Identity awareness—allows the firewall to enforce rules based on users' identities.
- Sandboxing—isolates pieces of code from incoming traffic packets executing them in a closed-off environment to ensure that they're not malicious.
In addition, most next generation firewalls integrate at least three basic firewall functionalities like enterprise firewall capabilities, intrusion prevention systems, or application control. This creates a well-rounded mechanism for network security.
Threat-focused NGFW
A threat-focused NGFW goes beyond traditional NGFW capabilities by emphasizing real-time threat detection and response. These firewalls integrate advanced threat intelligence feeds, behavioral analysis, and automated threat mitigation to identify and neutralize emerging risks as they develop.
This allows for rapid adaptation to evolving attack vectors, making them highly effective in environments requiring proactive security measures, especially against sophisticated cyber threats. Unlike standard NGFWs, the threat-focused version excels in not only blocking known threats but also predicting and responding to new ones in real-time.
Web application firewalls (WAF)
WAFs protect network applications by filtering, monitoring, and blocking malicious HTTP traffic. This same firewall technology can protect against cross-site forgeries, cross-site scripts (XSS), file inclusions, SQL injections, and others. In a way, the WAFs mode of operation is similar to a proxy server, with the key difference being that it acts as an intermediary between the web app server and a client.
As such, web application firewalls are deployed in front of a web application shielding it from the rest of the public internet. That way, the server is protected from threats, as everything must first pass WAF. This type of firewall can come in various forms like software, appliance, or delivered as-a-service.
Like other types of firewalls, WAF operates by enforcing security policies. However, a significant advantage of WAFs is that they adjust policies exceptionally fast. This translates into a more agile system that reacts to varying attack vectors faster.
Firewall-as-a-Service (FWaaS)
FWaaS provides cloud-based internet traffic inspection. What is unique about this type of firewall software is that it's delivered exclusively via the cloud. Using FWaaS usually means offloading on-premise data center equipment and shrinking the infrastructure that needs to be maintained.
The deployment of FWaaS is very similar to other cloud-based services. Each customer is assigned a virtual instance of the service, which can be customized from the web interface. More often than not, FWaaS providers offer identical management interfaces that in-house network administrators are already familiar with.
The downsides of such a setup are similar to those of cloud services. For instance, the online delivery model has latency concerns, especially when compared to in-house operations. Finally, there is always a question regarding data privacy, as firewalls are fully outsourced and managed by third-party.
Unified Threat Management (UTM) firewalls
UTM firewalls combine multiple security functions into a single device or service, offering a comprehensive solution for network protection. Along with traditional firewall features, UTM systems provide additional tools like intrusion detection and prevention, antivirus software, VPN support, and content filtering.
This "all-in-one" approach simplifies security management for smaller businesses or organizations that need multiple layers of protection but lack the resources for individual solutions. However, because UTM systems handle many tasks, they can sometimes slow down network performance, especially in larger deployments.
Circuit-level gateway firewall
Circuit-level gateway firewalls operate at the session layer of the OSI model and monitor the TCP handshakes between packets to determine if a session is legitimate. They don’t inspect the content of individual packets, which means they are faster but provide less security detail than application layer firewalls.
These firewalls ensure that the sessions are established according to pre-defined rules but may miss certain types of malicious traffic, such as data payload threats. Circuit-level gateways are typically used to protect networks behind more comprehensive firewalls.
Virtual firewall
A virtual firewall is a security appliance designed specifically for cloud and virtualized environments. Unlike traditional hardware firewalls, virtual firewalls are deployed as software within the cloud infrastructure, allowing them to scale dynamically alongside virtual networks. They filter and monitor traffic, safeguarding virtual machines, applications, and data in both public and private clouds.
Virtual firewalls can be integrated with other security tools, such as a Virtual Private Network (VPN) and intrusion prevention systems (IPS), to provide comprehensive cloud security. Their cloud-native nature makes them essential for modern, decentralized network architectures.
Packet-filtering firewall
A packet-filtering firewall is one of the earliest and simplest forms of network security. It operates at the network layer of the OSI model where the firewall inspects each data packet that passes through the network, deciding whether to allow or block it based on predefined rules. These rules typically focus on information found in the packet header, such as the source and destination IP addresses, port numbers, and protocol type.
While packet filtering firewalls are effective for basic traffic management, they are vulnerable to attacks that manipulate packet contents or sequences, such as certain types of malware or denial-of-service attacks.
Types of firewalls based on delivery method
As was briefly mentioned in the previous section, firewall deployment options can be very different. Here are the main types of firewall delivery methods.
Hardware-based firewalls
Hardware firewalls are self-contained appliances acting as a firewall maintains a secure gateway between devices inside the network perimeter and outside it. As they aren't attached to any host devices, they don't consume as much processing power. Their only function is to enforce security policies.
It's an ideal solution for medium and large companies looking to protect many devices within a defined network perimeter. On the downside, they can be complicated to set up effectively and require higher maintenance.
Software-based firewalls
A software firewall runs on a computer or server with the single task of ensuring network security. Also known as a hardware firewall or a host firewall, it must be installed on each device requiring protection. This means that a portion of the device's processing power needs to be allocated to keep a firewall service operational.
Host-based firewalls provide security for individual devices against viruses and other threats. This advanced threat protection also includes malicious processes running on the host while packet filtering network traffic.
Cloud firewalls
Managed security service providers (MSPs) offer cloud-native firewalls that are hosted in the cloud. While the provider takes responsibility for the technical side, the client must configure the virtual firewall according to their security policies. This approach works best for huge or globally distributed organizations as it eliminates the need to set it up per device.
Evolution of firewalls
The concept of firewalls originated in the 1980s, borrowing the term from physical firewalls used in building construction to prevent the spread of fire. In networking, early firewalls were simple packet filters embedded in routers.
Their function was basic: to block or allow traffic based on predefined rules for IP addresses, ports, and protocols. These first-generation firewalls were limited in their ability to inspect the content of data packets, which meant they couldn’t detect malicious payloads.
- First generation: Packet filtering firewalls (late 1980s). Inspected individual packets and allowed or blocked them based on predefined rules but could not detect malicious content
- Second generation: Stateful firewalls (mid-1990s). Tracked active connections and monitored ongoing communication sessions, offering improved detection of suspicious behavior
- Third generation: Application layer and proxy firewalls (early 2000s). Analyzed traffic at the application layer, providing deeper inspection and more granular control over data exchanges
- Fourth generation: Next-generation firewalls (NGFW) (2010s). Combined traditional firewalls with advanced features like deep packet inspection, intrusion prevention, and application awareness
- Fifth generation: Advanced threat prevention (2017 and beyond). Designed to counter large-scale, multi-vector attacks with technologies like anti-bot systems, malware protection, and sandboxing
Each generation of firewalls has built upon the last, evolving from simple packet filtering to sophisticated systems capable of identifying and stopping modern, complex threats. Today, firewalls are an integral part of an organization's security infrastructure, continuing to adapt as new challenges emerge.
The importance of a firewall
Network traffic, especially when it's coming from the public internet, should always be treated with caution. Therefore, firewalls stand as the first line of defense against various threats.
By keeping unused ports closed and filtering out malicious data packets, firewalls safeguard the security of your network.
More importantly, they're pushing the threats away from the endpoint. That way, the threat can often be shot down before it causes any critical damage to the device. It's also a much more secure method as it's much easier to handle the threat rather than try to get it removed once it breaches your network.
How to use firewall protection
Firewalls are a key part of your cybersecurity strategy, but knowing how to choose, configure, and maintain them is essential for keeping your network secure. Let’s walk through the key steps to ensure you're getting the most out of your firewall protection.
Choosing the right firewall
The first step in using firewall protection is selecting the right type for your needs. The size of your network, the sensitivity of your data, and your security requirements will all play a role in this decision. For small businesses, a basic firewall may suffice, while larger enterprises or companies handling sensitive information may require next-generation firewalls (NGFWs) with more advanced features like deep packet inspection and application control.
Configuring the firewall
Once you've selected a firewall, the next step is configuring it correctly to maximize its effectiveness. This usually involves setting up rules to control which traffic is allowed in and out of your network. Most firewalls come with default security settings, but it’s important to customize these according to your specific network requirements.
Basic setup steps:
- Define your network zones (e.g., internal, external)
- Set access control rules to permit or block traffic based on IP addresses, ports, and protocols
- Enable features like logging to monitor traffic and flag potential threats
- Test the firewall by running simulated attacks to ensure it's blocking malicious traffic
Maintaining the firewall
Firewalls need regular upkeep to remain effective against new and evolving threats. Maintenance tasks include updating the firewall’s software, applying patches, and reviewing the firewall logs. Keeping an eye on these logs is critical, as they can reveal suspicious activity that requires immediate attention.
Maintenance checklist:
- Regularly update the firewall’s firmware and apply security patches
- Review and fine-tune access rules as your network changes
- Schedule routine log reviews to spot potential threats early on
- Back up your firewall configurations in case of failure or upgrade
Advanced firewall features
Modern firewalls often come with advanced features designed to bolster security. For example, many include an IPS that detects and blocks malicious activity in real-time. Features like virtual private networks and sandboxing can add additional layers of protection, especially if your business deals with sensitive data or has remote workers. Advanced features to explore:
- Intrusion Prevention System (IPS): Automatically monitors and stops network threats
- Deep Packet Inspection (DPI): Analyzes data in transit for hidden malicious content
- Application Control: Lets you manage and monitor the use of specific apps on your network
- Sandboxing: Isolates potentially harmful files or code to test them in a secure environment
By choosing the right firewall, configuring it properly, and staying on top of maintenance, you can ensure that your network is well-protected. Don’t forget to explore advanced features for extra security when needed!
Future of next-gen firewalls
Like the remainder of the cybersecurity inventory, the firewall is changing. Even with the developments in next-generation firewalls, the trend is moving towards higher autonomy and remote delivery methods.
It's expected that firewalls will be even more active in the future and better communicate with various other cybersecurity components, creating a more holistic security mechanism. The next logical step would be integration into Security Information and Event Management solutions.
One thing is sure — as firewalls are such a key component of network security, they will remain as one of the fundamental areas of cybersecurity.
Key takeaways
- A firewall is a critical component in any network security device strategy, functioning as a gatekeeper for both internal and external networks.
- Firewalls help enforce cybersecurity policies by monitoring, filtering, and controlling both incoming and outgoing network traffic.
- Different types of firewalls—such as proxy, stateful, next-generation, and web application firewalls—offer layered protection across the OSI model and beyond.
- Advanced solutions like NGFWs and Firewall-as-a-Service (FWaaS) provide deeper visibility, smarter threat detection, and cloud-native deployment models for agile businesses.
- The delivery method—hardware, software, or cloud—should align with the organization’s size, infrastructure, and security requirements.
- Historical evolution and current innovations reflect how network security firewalls have adapted to increasingly complex threats.
- Ultimately, firewall security remains foundational for safeguarding the internal network and ensuring a robust, scalable cybersecurity posture.