Rule-based access control definition
Rule-based access control (RuBAC) is an access control system that allows user access to network resources according to pre-defined rules.
In rule-based systems, administrators define the conditions users must meet before gaining access. The access management system compares information about the user to a rules database. If they meet the conditions, they can use apps, move files, or view records. If not, the system restricts user permissions.
This article will introduce rule-based access systems. We will look at:
- How rule-based access works
- The pros and cons of rule-based network access
- Use cases for rule-based access-control-models
- Implementing rule-based access controls
- How rule-based access compares with alternative access methods
Why is rule-based access control important?
Controlling user access is a critical security challenge. Without robust access controls, companies expose sensitive data to external attackers. Expensive data breaches or ransomware attacks can result.
Why should organizations use rule-based methods to control access? The main reason is that rules allow companies to set precise conditions for access.
Administrators can target high-value data with additional barriers. They can limit access to authorized users and exclude users without a legitimate need to access resources.
Rules are reliable and consistent. If administrators set the correct rules in their access systems, there is much less scope for human error.
The use of rule-based access also has major compliance benefits. Organizations can track access requests and demonstrate the existence of strong controls for relevant assets.
How does rule-based access control work?
Rule-based access systems compare user credentials to rules databases. These databases include sets of rules that are connected to network assets. Each app or protected database requires a set of access conditions.
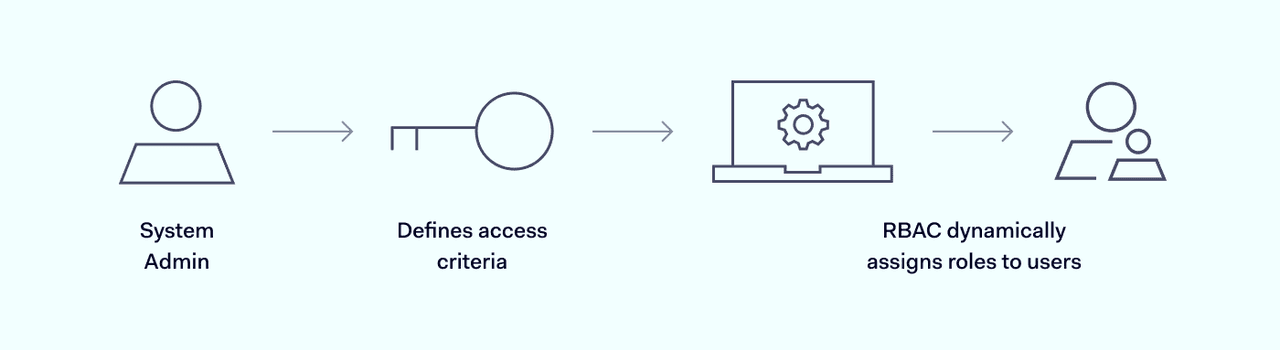
If users satisfy conditions defined in the database, the system allows access. If not, the system denies access or requests additional credentials to prove users are who they claim to be.
Rules-based systems differ from role-based access controls because they use attributes to define rules. Attributes are facts about individuals who seek access to network resources. Attribute-based access control can use many user attributes, including:
- Time. Admins can allow access to apps or databases at specific times of day. For example, data may be unavailable outside office hours. Or companies may limit access to trading data before markets open.
- Location. Companies can restrict access to their premises, or agreed remote work locations. In some cases, organizations might limit access from certain regions.
- Role and seniority. Access controls assess the role of each user in the organizational structure. They then deliver privileges appropriate for that position. For instance, C-suite employees may require broad access to resources. But marketing teams or HR officers may only have access to relevant databases.
- User activity. Advanced rules-based controls track and analyze user activity. The system may deny access to users behaving erratically. This can protect networks against account hijacking.
Rule-based access control can also be static or dynamic. Static controlsremain the same until admins make changes to the rules database. Dynamic controls adapt to different conditions. An example could be access denial after multiple failed logins.
Benefits of rule-based access control
Benefits of rule-based access control systems include:
- Granular controls. Rule-based access control is very precise. Administrators can define rules based on many attributes. For example, client databases could be blocked at certain times of day or made accessible to specific roles. Admins can even allow certain IP addresses or track user activity, This level of granularity is not possible with purely role-based access controls.
- Improved security. Granularity promotes better data security. Admins can target rules at the most sensitive network assets. This offers extremely robust security when combined with technologies like multi-factor authentication (MFA).
- Administrative efficiency. Rule-based access control is extremely efficient. Once the rules database is in place, there is no need to assign privileges manually. The system automatically allows access if users meet pre-defined conditions. This also reduces the scope for human error.
Challenges of rule-based access control
Rule-based access control has some important drawbacks. Challenges for implementing this type of access control include:
- Setting up rules-based access systems. Configuring a rules-based access system can be complicated. IT teams must build a comprehensive rules database. This includes rules that enable access to every network asset. This can be a lengthy process. By contrast, setting up role-based controls is much simpler.
- Ensuring configurations are ready for deployment. Setup must be accompanied by testing and quality assurance. Security teams must eliminate mistakes before the system goes live. Testing is essential to make sure access controls deliver real-world benefits.
- Adapting and expanding rule sets. Rule-based access systems sometimes struggle to adapt when access needs evolve. Changing rules may require complex alterations to rule databases, especially if nested rules are employed. Some systems also include more than one set of rules. For example, a company could split its access controls across different branches. In this case, admins need to change attributes in each location to ensure consistency. RuBAC also struggles to scale efficiently. Adding apps or devices can become burdensome as organizations grow.
- Handling computing demands. Rule-based access control can also be technically demanding. Processing large quantities of rule-based requests places high demands on network infrastructure. This can be a problem if organizations rely on older hardware. Diminished network performance may result.
- Auditing and testing access processes. Auditing access controls can be difficult with purely rule-based systems. Tracking the activity and privileges of individual users is difficult. Admins may also allow rule exceptions for specific users. Recording and rolling back exceptions can be problematic, resulting in messy auditing procedures.
- User experience problems. Sometimes, users are denied access even though blocked resources fall within their role. This happens because rules are not sensitive to the needs of individuals. They apply globally and inflexibly. But role-based access control alternatives are built around the needs of users and may result in a better user experience.
When to use rule-based access controls
Rule-based access controls make sense when speed, security, and efficiency are important.
RuBAC systems process large numbers of access requests relatively easily. They just need to compare user attributes with rule databases. If the system detects a match, it allows access. This is less complex than handling roles or individual profiles and also eliminates sources of human error.
RuBAC is ideal for protecting critical apps or data. Rule-based controls assure regulators that organizations take data protection seriously. And they give network admins maximum flexibility when managing access.
However, rule or attribute-based access controls don't usually work alone. They are often used in combination with role-based access control. For example, organizations could incorporate rule-based controls into their security setup if:
- They need to control access to critical data or apps.
- Companies are responding to threat intelligence and need targeted access control.
- Work groups move overseas or remote work becomes more common.
- The threat surface changes temporarily, making existing access systems unsafe.
Rule-based access control implementation steps
Implementing rule-based access controls requires careful planning. Systems vary in terms of the attributes they use. But implementation processes tend to include the following steps:
1. Understand network access rules
Planners must determine specific rules for apps and network access points. And they also need to specify general rules that apply network-wide. Prioritize high-value data and resources. Deal with high-risk assets separately, and add extra controls where needed.
2. Model the threat environment
Think about potential weak points and network threats. Controls should guard against critical threats and harden defenses where those threats are most urgent.
3. Create a relevant rules database
Rules should reflect your organizational structure and be tightly focused on security. Check access control rules regularly to ensure they continue to meet security requirements.
4. Test access systems to avoid conflicts
Test the access control system thoroughly. Avoid any blockages that prevent authorized resource use. Check for conflicts with role-based access controls or other access management tools.
5. Create clear access control policies
Policies inform users about how the access control system works and why they are in place. Include instructions about how to use access controls and penalties for misuse. Include details about how to solve access problems if they arise.
6. Audit and improve access systems
Schedule audits to check that rules are relevant and functional. Log data in a way that meets compliance needs. And be prepared to change rule databases as your organization evolves.
Rule-based access control vs role-based access control
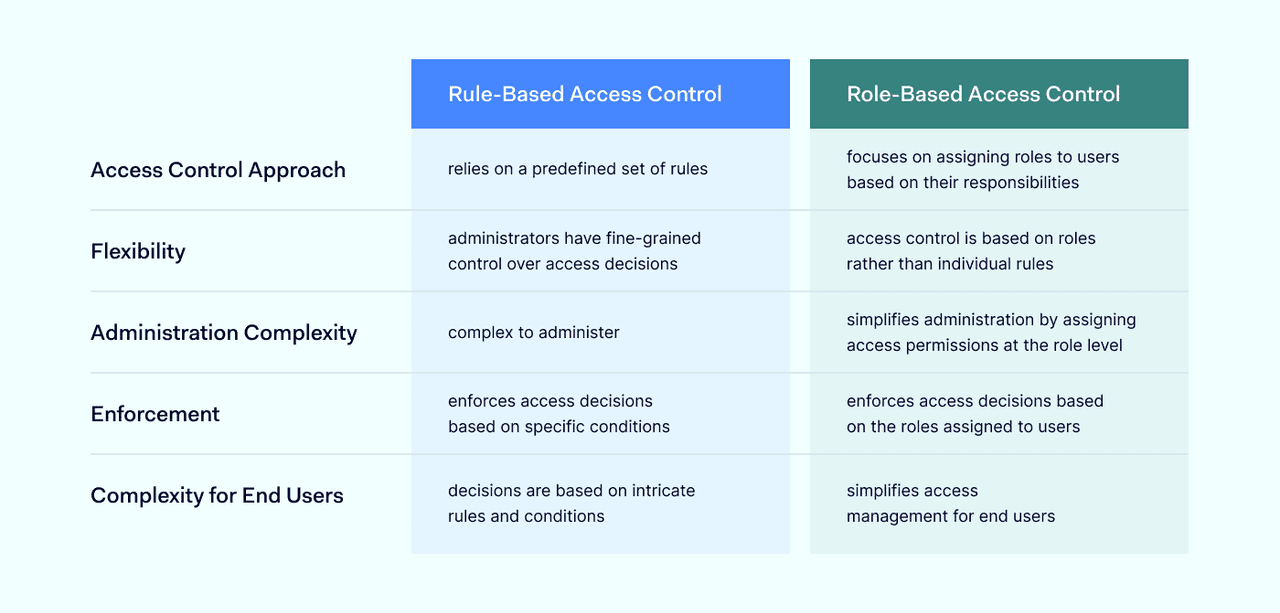
RuBAC and role-based access control systems are not mutually exclusive. However, planners often have to choose between the two paradigms when creating access management systems. And there are important differences between rule and role-based access controls:
Rule-based access control
- Uses mandatory access controls created by administrators. Controls are based on rules that use attributes to determine network access. Rules cover all roles in the organization.
- Controls seek to prevent unauthorized access to network resources. Access levels are not associated with individual users. This makes it hard to implement Zero Trust access policies.
- Covers network assets in granular detail. Denying access to individual data sets, code bases, or apps is simple.
- Less vulnerable to credential theft. Admins can add attributes like location, IP address, or time. This adds extra security protection for vulnerable data.
- Lengthy implementation process. Admins must connect each resource to relevant attributes. Extensive testing is required to check that the right rules are in place.
- On-boarding users is simple. There is no need to assign user privileges. The priority is ensuring user attributes are visible to access control systems.
- Rules apply passively in the background and there is no risk of role explosion. Admins must ensure rules remain relevant as network needs change.
- Maintenance is complex. Changing rules can affect large numbers of users. System administrators can make errors that create huge security vulnerabilities.
Role-based access control
- Uses mandatory access controls created by administrators. Controls are based on roles. Roles are assigned to users based on their position in the organizational structure.
- Controls provide a set of privileges for each role. This makes it easier to implement the principle-of-least-privilege.
- Relatively imprecise. Controls apply broadly. Implementing granular controls for resources may require the addition of ABAC systems.
- Vulnerable to credential theft. Malicious users with credentials can access resources if they pass authentication gateways.
- Requires less work to set up. Admins create roles as needed, and can automate privileges management to reduce the workload.
- Admins must consider which role fits each user. This consumes more time than on-boarding with RuBAC systems.
- Roles can be imprecise. This can lead to role explosion as users request greater access levels, making security controls less effective.
- Maintenance is relatively simple. Admins change privileges linked to each role. Changing one role does not affect other user positions.
Conclusion
Rule-based access control restricts or allows access based on user or object attributes.
With RuBAC, administrators can limit access according to location, time of day, IP address, and organizational role. This provides maximum flexibility. But RuBAC can also be hard to set up and maintain. This makes it important to carefully compare RuBAC with alternatives such as role-based access control.
