With remote teams, scattered cloud resources, and staff frequently stepping into new responsibilities, relying on manual processes to manage who has access to what is nearly impossible. It can slow operations and create major security gaps when permissions aren't updated promptly or are mishandled.
So, what businesses truly need is a dynamic security model that continuously verifies access and adapts automatically as conditions change. That's why more and more companies are turning to policy-based access control.
Policy-based access control defined
Policy-based access control (PBAC) is an access control strategy that combines role-based access privileges and object attributes. Access to network resources is documented and controlled via established policies.
PBAC determines user privileges based on business roles but also allows administrators to secure resources via granular attribute-based controls. This makes it a flexible alternative to pure role-based access controls and attribute-based controls.
This article will introduce policy-based access systems. We will learn:
- How PBAC works and implementation strategies.
- PBAC's benefits and the challenges associated with its use.
- How PBAC compares with other access strategies.
How does policy-based access control work?
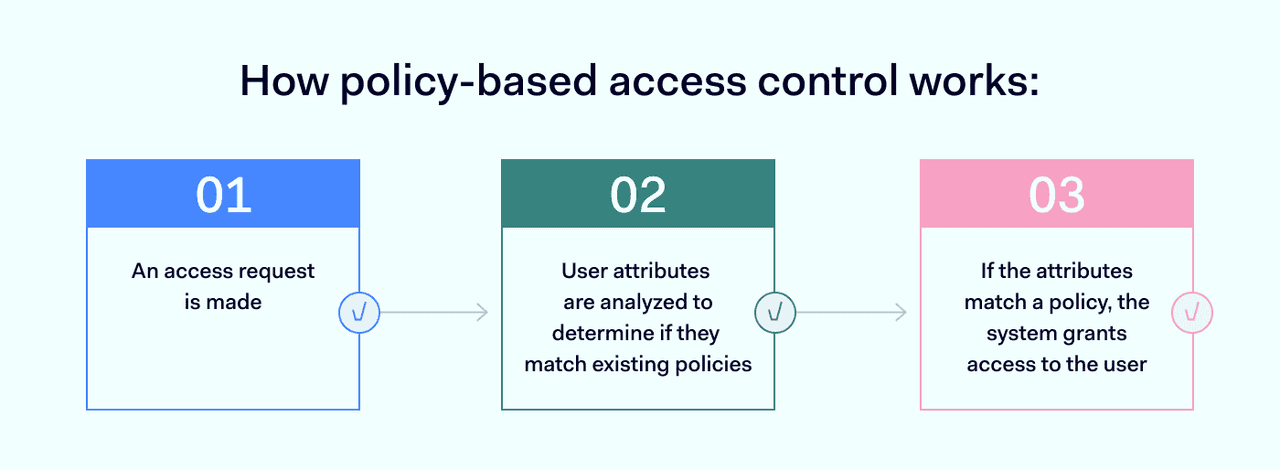
The process usually involves three main phases:
- Access request is made: A user (or system) attempts to access a resource.
- User attributes are analyzed: The system evaluates the attributes associated with the user, the resource, the action being attempted, and/or the environment (such as time of day or location) to determine if they align with the rules defined in existing policies.
- Access is granted: If the combination of attributes matches the criteria specified in one of the existing policies, the system grants the user access to the requested resource.
Key components of PBAC
Policy-based access control relies on several key components to manage access securely and intelligently. The first and foundational component is policies, which define who can access what resources, when, and under what conditions. Next are the attributes, which provide factual information about users, the requested resources, and the overall environment.
When an access request is initiated, the Policy Decision Point (PDP) acts as the core logic engine. It evaluates the attributes against the established policies in real time to determine whether access should be granted, denied, or limited. Closely connected is the Policy Enforcement Point (PEP), which immediately applies the PDP's decision, controlling access accordingly.
Finally, there are contextual inputs such as user identity, device, location, IP address, time of request, and environmental risk indicators. They inform the process, allowing PBAC to adapt access dynamically to each situation.
Role-based profiles and attribute-based policies
PBAC brings two different access control concepts together: role-based privileges and attribute-based policies.
Role-based profiles
Network users have a profile linked to their business role. Roles have different privileges to access, read, write, and transfer data.
Attribute-based policies
Policies are coded in XACML but represented as text descriptions. Attributes are aspects of apps or data that affect user access. Profiles can be simple or more complex. Administrators can use them to control access according to identity, location, time, and many other attributes.
Attributes are at the core of PBAC. Policy-based access technologies use a range of properties to determine access to documents, databases, or applications. Examples of attributes include:
- Subject attributes - information about the user accessing resources. This could include name, department, job role, or project membership.
- Object attributes - information about the app or file. This could include the file type, size, and location.
- Action attributes - information about allowable actions for specific subjects. This could include commands like read, delete, write, transfer, or copy.
- Environment attributes - contextual information about how users can access the resource. This could include time of access, geographical location, or device type.
Administrators can link together these attributes in logical policies for each role and resource. Beneath the hood, policies apply Boolean logic to determine access. Users see a clear description of who can access the resource and the conditions under which access is permitted.
Benefits of policy-based access control
Benefits of policy-based access control include:
- Improved security: Managing access can be extremely detailed. Granular controls allow companies to customize data security strategies. Small subsets of users can change or delete high-value information. But the same data can be viewable to larger communities.
- Centralized management: Security teams can manage policies centrally and distribute them to all users and resources. Central policy databases make it easy to change access strategies. They also make auditing access systems simpler.
- Scalability: Flexible access policies change rapidly as user communities expand or new apps come online. Companies can grow smoothly while extending access controls.
Challenges of policy-based access control
Challenges associated with policy-based access controls include:
- Policy complexity: PBAC can become complex when applied over many locations and IT systems. Administrators must ensure every user has the correct privileges. This requires careful planning.
- Resistance to change: Changing policies can be difficult. Major changes affect user access for large numbers of employees. Administrators often choose workarounds instead of strategic policy updates.
- Training and awareness: Employees need to know what policies are in operation. Poorly worded policies confuse users. This can lead to a security breakdown if employees seek alternative access routes when they are not granted access.
How to implement PBAC?
Implementing PBAC effectively requires careful planning, a thorough understanding of organizational needs, and a step-by-step approach that balances security with usability.
- Model user roles and application usage: Identify all roles in the organization and the applications they need. Understanding how users interact with systems ensures policies are relevant, practical, and aligned with operational needs.
- Define privileges for each role: Assign permissions based on the principle of least privilege. Only give users access necessary for their tasks, reducing the risk of accidental or unauthorized access to sensitive resources.
- Add granular policy controls: Layer detailed rules like time restrictions, device checks, or activity limits. Granular policies allow for more precise management of access and can enforce organization-wide security standards without overly restricting legitimate workflows.
- Incorporate contextual attributes: Consider factors like location, device type, or network security. For example, require VPN or multi-factor authentication for remote employees to protect against potential vulnerabilities.
- Engage employees: Involve users to understand how policies affect their daily work and identify any practical challenges they face. Gathering feedback from employees helps refine access rules and highlight hidden workflow needs.
- Implement gradually and monitor continuously: Roll out policies in stages, starting with critical systems and roles, and gradually expand coverage across the organization. Track access patterns and adjust policies over time, ensuring they remain effective against emerging threats without overcomplicating access management.
PBAC use cases
PBAC is most effective where organizations need to protect sensitive data while allowing flexible working.
The healthcare industry is a good example. PBAC systems allow health providers to separate different clinics or departments. Specialists in a radiography department may have access to patient scans. But the system can deny access to records in other clinical areas.
Healthcare policies can be very specific. Access control policies could state that physicians "can access patient records within working hours, providing records are related to the professional's area of specialty". This helps to safeguard privacy and meet HIPAA requirements.
Banks or insurers may also use a PBAC system in their security model. For instance, branch employees may have "access to client financial information in their branch" but not to the bank's wider client databases.
PBAC helps financial organizations meet compliance regulations. It is also a sound risk management measure that limits the risk of data breaches and other information security incidents.
Is PBAC the same as ABAC?
PBAC and attribute-based access control (ABAC) are very similar approaches to controlling access. Both security models regulate access with object and user attributes. They are both highly flexible and easy to use. But there is one important difference.
- Policy-based access control describes access rules in text-based policies.
- Attribute-based access control applies controls in logical code. These attributes are not expressed as policies, and here less intelligible to network users.
PBAC is more visible to administrative teams and departmental managers. The use of plain text makes it easier to share policies and discuss access requirements. This also makes it easier to make changes and train employees to use access systems securely.
PBAC vs. role-based access control (RBAC)
Policy-based access control and ABAC are alternatives to role-based access controls.
RBAC
Creates policies for each organizational role. Every role has specific access permissions. Users can gain access to resources they need. But a well-designed role-based access control system will restrict access to all other network assets.
PBAC
Uses role-based profiles. But it combines roles with contextual attribute-based controls. RBAC applies broad restrictions with little flexibility. PBAC allows administrators to create granular access systems that reach down to individual files.
Policy-based access control models combine the functions of role-based and attribute-based controls. Plain text policies set access requirements for network resources. These policies apply to roles or authorized users. They can feature granular controls based on time, location, and user actions.
