You might be surprised how many data breaches are caused by weak or stolen credentials. That’s where a solid access control policy comes in. It’s an official rulebook that keeps your sensitive data from falling into the wrong hands, whether from outside attacks or internal slip-ups.
What is an access control policy?
An access control policy is a set of rules that define access control systems. With an access control policy in place, administrators can allow users to access the resources they need and limit access to unauthorized users. This security model protects sensitive data from external and insider attacks.
Types of access control policies
Access control policies help manage who can access different resources in an organization. There are several types, each with unique features. Knowing these helps you choose the right approach to secure data and resources. Here are the four main types:
1. Mandatory Access Control (MAC)
Mandatory Access Control (MAC) is a strict policy in which a central authority controls access rights. Administrators decide which users can access specific resources, and users cannot change these permissions. This ensures a high level of security. MAC is often used in government and military settings where protecting classified information is critical. It prevents unauthorized users from accessing sensitive data.
2. Discretionary Access Control (DAC)
Discretionary Access Control (DAC) is a flexible policy in which the resource owner decides who can access it. Users can grant or revoke access rights to others. While DAC is easy to implement and offers flexibility, it can be less secure. The risk comes from users potentially giving access without proper oversight. DAC is commonly used in environments where ease of use and flexibility are more important than strict security.
3. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) assigns permissions based on user roles within the organization. Each role has specific access rights, and users are assigned roles based on their job functions. For example, an HR manager may access employee records while a developer accesses the code repository. RBAC simplifies management by assigning roles instead of individual permissions. It is widely used in businesses because it aligns access rights with job responsibilities, ensuring users access only what they need.
4. Rule-Based Access Control
Rule-Based Access Control sets access permissions based on rules made by the administrator. These rules determine access rights based on conditions like time of day, IP address, or type of device used. For example, access might be limited to business hours or specific locations. This type of control helps create dynamic and context-aware access policies. It adds flexibility and security by adapting to different scenarios.
What do access control policies manage?
An organization's access control policy manages how users interact with digital and physical assets.
There are two basic types of access control systems. Both should be part of your access control policy:
- Logical access control policies cover access to servers, databases, and applications.
- Physical access policies deal with entry points such as card readers or locks.
Logical access policies have three main components:
- Authentication identifies users by requesting credentials. Organizations generally rely on multi-factor authentication to defend sensitive data. This requires more than one authentication factor before access can be allowed.
- Authorization provisions users with access rights. A robust access control policy limits access rights to resources that users require. Privileges can be allocated individually. But it is more efficient to link roles to access rights.
- Auditing enables administrators to verify that users have the correct privileges. Audits check for over-privileged system administrator privileges or shared accounts. And they remove unused accounts before external attackers can compromise them.
What should you include in an access control policy?
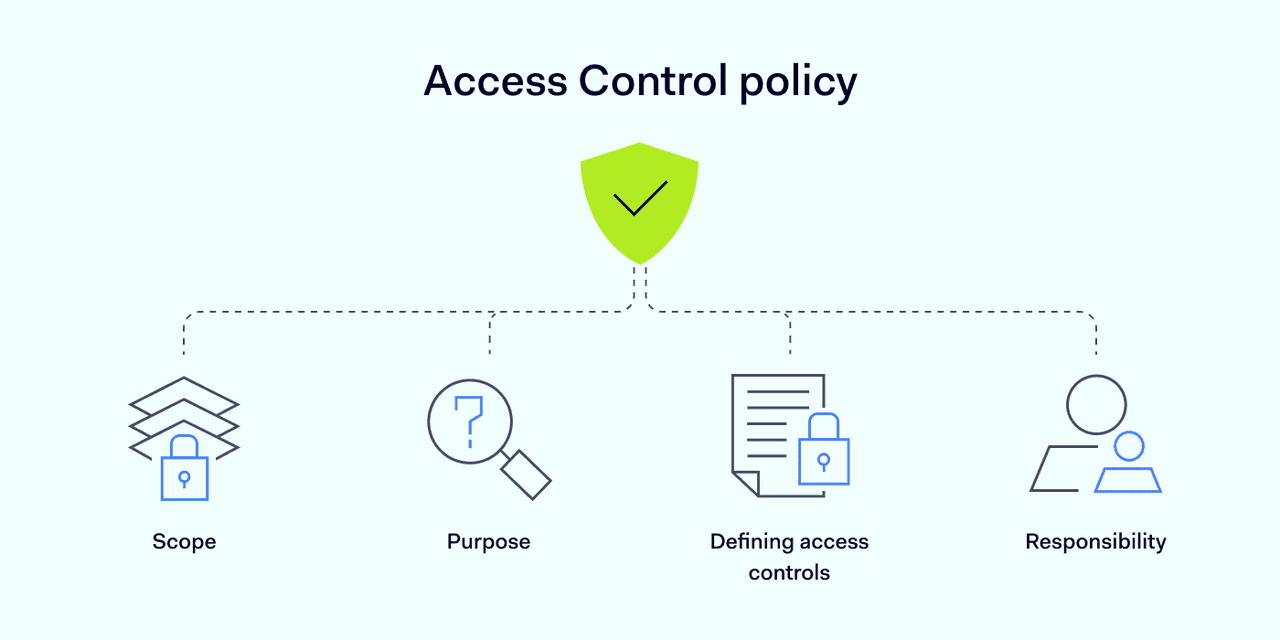
Access control policies vary, but a good access control policy template will always have a few common elements.
1. Scope
Scope refers to the systems and users covered by the access control policy. There are three important areas to include here:
Different classes of user
For instance, an insurance company might need to consider sales teams, developers, HR, customers, and even third-party maintenance services. Each category has its own access rights and requirements. The access control policy should clearly define these rights.
Protecting specific assets
The policy should assign each resource a priority level and apply appropriate controls. A good rule is to prioritize assets that fall under relevant data protection regulations.
When and where access controls apply
For instance, the access control model might block remote access from public Wi-Fi. Or the device policy may prohibit the use of private computers.
- EXAMPLE: "This policy applies to all employees, third-party contractors, policyholders, and vendors who connect to [Insurance Company] applications, servers, or any network devices that can hold or transmit information specified in the [Insurance Company] Data Protection Policy. Servers and applications processing client financial information are classified as "high security" and require additional authentication before allowing access."
2. Purpose
The second section of your access control policy template should explain why access controls are needed.
Controls should align with business goals. They should defend critical data and systems. The policy should define how access controls achieve these aims.
Poorly understood controls cause conflict between employees and IT managers. Without a clear mission statement, it's impossible to assess whether controls are effective. So, security teams should write this section carefully and consult stakeholders to suit their needs.
- EXAMPLE: "The access control policy seeks to minimize access to client and company information. It aims to prevent unauthorized access and use of sensitive information, in line with PCI-DSS regulations and [Insurance Company] security policies. The policy seeks to balance access control and availability, ensuring smooth operation of network assets."
3. Responsibility
This section defines who owns and operates the access control policy.
Ownership refers to whoever creates and audits the policy. This individual is usually a Security Officer. They take responsibility for protecting high-value assets, and ensuring roles and privileges are properly allocated.
Operators of the access control policy (people handling day-to-day access management) are not the same as the policy owners. The policy should define who implements access controls and deals with day-to-day maintenance. In practice, this will usually be the responsibility of IT administrators.
This section should also explain the separation of duties. This principle ensures that single users cannot make global changes to an organization's access systems. Instead, they must seek approval from a third party before making important administrative changes.
- EXAMPLE: "The Chief Security Officer is the ultimate owner of the Access Control Policy. Any changes to access controls require the approval of the CSO or a relevant departmental manager. This includes user additions and deletions, along with amendments to an individual's access rights. Administrators will apply the principle of least privilege and ensure that users only have access to essential resources."
4. Defining access controls
This section is the most detailed part of an access control policy, getting into the nuts and bolts of your access management system. The policy should list the core elements of the organization's access management system. Details may vary, but elements include:
- The principle of least privilege. Under POLP, users can access the resources they need but nothing more. Use this as the foundation for assigning access privileges and creating user roles.
- Roles or attribute-based controls. This section describes the access control system. This could be a role-based access control model (RBAC) where privileges are linked to user roles. If so, list user roles and explain how the system assigns permissions. Include any additional controls for the most sensitive data.
- User credentials. The password policy defines a "secure password" and explains how to make password changes. Include warnings about shared passwords and the need to change defaults. If relevant, add information about multi-factor authentication requirements such as one-time passwords or biometrics.
- Account management. Explains how user accounts will be managed, including how to create and remove accounts. It may include information about audit schedules and event logging, as well as notes about shared accounts and third-party authorization of admin privileges. The digital access policy may mention automated provisioning and off-boarding if these tools are in use.
- Physical controls. A list of physical access controls and the assets they protect. The physical access control policy may include defense in depth for servers handling sensitive information. Weaker physical controls could apply to office settings.
- Remote access. If applicable, include rules about how the remote workforce can safely connect to network resources. This may include the use of Virtual Private Networks or authentication hardware to verify identities.
This PDF template is a good example of how to define an access control system. Apply the format to your environment, using the themes above as a guide.
How to implement access control best practices

Following these best practices will make it easier to create effective access policies:
1. Match roles and access rights on a need-to-know basis
Create roles that reflect the makeup of your organization. Provision of privileges for each role that allows employees to carry out their professional tasks. Adopt a need-to-know approach, assigning minimal privileges starting from the bottom up. Avoid granting wide network access if possible.
2. Create temporary and permanent access privileges
Assess whether users require long or short-term access rights. Third parties may require access to a protected system for a short period. However, full-time employees usually need ongoing access. Make sure temporary privileges are time-limited. Revoke access when the period elapses.
3. Add extra defenses for confidential information
Resources such as patient records need robust protection. In these cases, administrators can combine RBAC with attributed-based controls. Exclude users making suspicious access requests or accessing from insecure locations. And add extra authentication factors for the most important data.
4. Communicate policies and train users
Network users must completely understand the access control policy. Make your security policy freely available. Schedule training sessions to explain how controls work. Put in place support services to assist employees and change access profiles if needed.
5. Use automation to make access management easier
Manual access management (tracking controls and maintaining user profiles) can be time-consuming and prone to human error. Automation tools make authentication more efficient, while automated policy provision and off-boarding remove unused accounts. That way, admins can focus on critical security tasks and protect high-value information.
Conclusion
Access control policies are an essential security tool. Clear and comprehensive policies protect data, streamline access management tasks, and make life harder for malicious actors. Leverage the best practices above and use our access control policy template to create a policy that suits your requirements. The result will be better risk management, robust compliance, and enhanced data protection.
