Summary: See how cloud network security helps your team stay secure, work flexibly, and scale your business without the usual tech headaches or risks.
Adopting cloud-based infrastructure requires strong cloud network security to protect your data, apps, and systems.
With effective cloud network security, businesses can scale resources as needed, reduce costs, and better manage risks. It offers a clear view of your security landscape, helping you make informed decisions about future cybersecurity investments.
So, what exactly is cloud network security, and why is it so important? This guide will cover everything you need to know about it and its role in modern businesses.
Cloud network security definition
Cloud network security refers to the technologies, policies, and processes that protect public, private, and hybrid cloud networks from threats and unauthorized access.
How cloud-based network security works
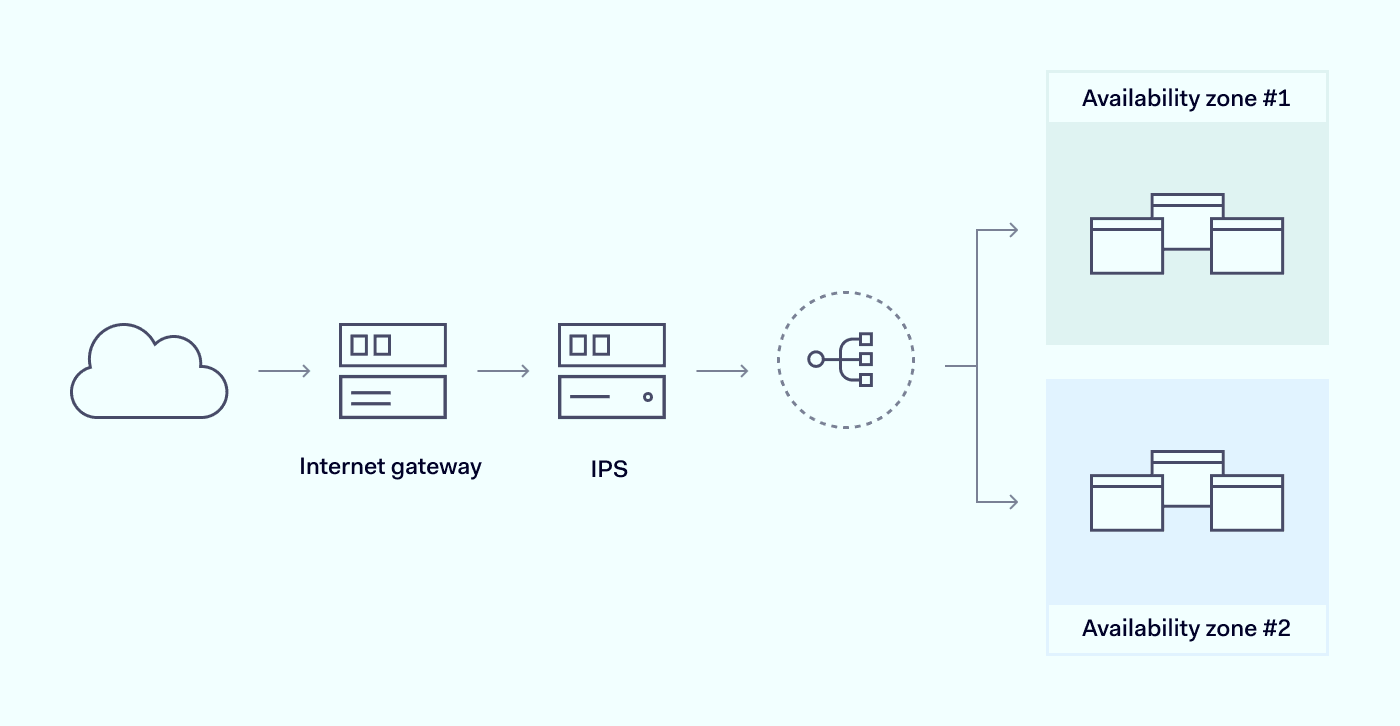
Cloud network security resembles traditional on-premises network security but with important divergences related to defending virtualized environments.
Like on-premises security, cloud network security defends network assets against external threats. Cloud security systems assess access requests and authorize users to access resources. They provide visibility for security managers, including real-time alerts and audit logs. And they neutralize malware and illegitimate data transfers.
Unlike standard security solutions, cloud defenses are not based on-site. Cloud security systems function via software-defined networking tools. Virtual gateways reside in the cloud, where they can protect applications and data from access requests, wherever users may be.
The context: understanding cloud computing
Cloud computing uses virtualized platforms to host applications and store data. The cloud exists as a worldwide network of servers and is accessible via a standard internet connection.
The user’s apps and data reside off-site, removing the need for on-premises hardware. Instead, network resources are “virtualized”. Resources are accessible to the owner or user, but cloud providers host them.
Users can access software-as-a-service (SaaS) apps or build customized cloud deployments via platform-as-a-service (PaaS). In all cases, security is a shared responsibility between users and cloud service providers (CSPs).
Providers must secure the hardware used to host cloud apps or data. Users must protect any data passing through cloud environments. They are also responsible for managing access to cloud assets.
Elements of cloud network security
Cloud network security solutions vary, but could include:
Sanitization: Systems can filter low-level traffic and remove potential threats, without the need for full-scale inspection.
Exploit protection: Protection against known zero-day exploits, with data from the latest threat intelligence.
Traffic inspection: Inspection of SSL/TLS traffic passing through virtualized environments. Analyzes encrypted traffic without compromising speed.
Centralized security administration: Solutions cover all cloud applications and storage assets. They integrate seamlessly with existing resources (including on-premises networks), providing total awareness of network activity.
Segmentation: Cloud network security applies
micro-segmentation to limit user permissions and guard confidential data.
Remote access: Ensures secure access for remote workers and third parties. Users can connect to cloud assets safely from any location.
Automation tools: This includes an automated extension to newly installed cloud services. Automated workflows blend ease of use and security, allowing companies to harness the cloud's potential.
Simple integration: Cloud security tools integrate with legacy applications, operating systems, and third-party security systems.'
Cloud vs. on-premises network security: key differences
When it comes to network security, on-premise systems give businesses full control over their infrastructure, allowing them to implement strict security protocols and have direct oversight of sensitive data. This can lead to more robust, tailored security measures, especially for organizations with strict compliance requirements.
In contrast, cloud network security relies on third-party providers to manage infrastructure, which can reduce direct control but offers scalable, flexible security features. Cloud providers typically offer advanced security measures, like automated updates and 24/7 network monitoring, which can improve overall security management without the need for internal resources.
The following table highlights the main differences between cloud and on-premise network security, specifically focusing on security-related aspects.
| On-premise network security | |
|---|
| Full control over infrastructure and security protocols | Limited control, the provider manages the security infrastructure |
|---|
| Easier to comply with specific industry regulations | Compliance depends on the provider and may require additional effort |
|---|
| Limited scalability, requires additional hardware | Highly scalable, can easily adjust resources as needed |
|---|
| Entirely the organization’s responsibility | Shared responsibility, the provider handles some security measures |
|---|
| Requires internal backup systems and manual recovery plans | Cloud providers often have built-in redundancy and recovery options |
|---|
The key difference lies in control and responsibility. With on-premise, the business is fully responsible for security, while cloud-based solutions shift some of that responsibility to the provider. However, cloud security benefits from continuous innovation and scalability, while on-premises may struggle with adapting to evolving threats quickly due to limited resources.
Ultimately, businesses must weigh their need for control and customization against the flexibility and managed services offered by the cloud.
The importance of cloud network security
The cloud is everywhere in modern life. Businesses, non-profits, and government agencies all rely on cloud infrastructure to deliver services and host workloads. But the rise of the cloud has created new security vulnerabilities. This means that organizations need to rethink their network security policies.
Traditional on-premises networks have a simple security architecture. Central resources are protected by the network perimeter. Endpoints are few in number and easy to monitor. Access patterns and user communities change slowly, if at all. In this context, putting in place firewalls and threat detection systems is relatively simple.
Cloud network security presents a different set of challenges.
In the cloud, there is no standard network perimeter. Users can access cloud gateways anywhere. IT teams rarely manage on-premises resources. Instead, cloud assets are maintained by cloud providers on servers across the world.
A public cloud environment can change rapidly. Employees might spin up new SaaS instances or cloud APIs, or staff could bring new cloud storage containers online to backup data or handle overflows.
Security teams need to maintain awareness, track user activity, and neutralize threats. Organizations need a cloud network security strategy that locks down critical cloud assets while enabling users to use cloud computing.
Cloud network security benefits
Adopting a cloud network security strategy has many advantages. The benefits of retooling your security setup for the cloud include:
Improved data security
The most important benefit of cloud network security is enhanced protection for sensitive data.
Cloud security solutions encrypt data at rest on the cloud. If files are stolen, cybercriminals will not be able to read data easily. Encryption of data in transit also makes it harder to track information flows and launch targeted interception attacks.
Micro-segmentation separates confidential data from the rest of an organization’s cloud network. Data resides in software-defined compartments that are accessible with the right credentials. Cloud security systems can define these segments at a granular level.
Better visibility for administrators
IT teams need visibility to monitor threats and user activity. But legacy security solutions are not well-adapted to discovering cloud apps and tracking activity in a cloud environment.
Cloud-native network security systems bring together all virtualized assets. Admins can monitor network activity in real time via a single pane of glass and automated alerts deliver information about potential threats before they become critical.
Simplified cloud policy management
Security policies should reflect the security needs of network owners and be delivered to all users. However, delivering security policies consistently in cloud settings is a complex task. Unified cloud network security systems solve this problem.
IT teams can automatically deliver updated security policies to endpoints. Cloud-native solutions also make it easier to offer policies across hybrid or multi-cloud environments.
Threat analysis and neutralization
Cloud resources are vulnerable to data breach attacks. Compromised remote access devices, phishing emails, and credential theft are common entry methods. Cloud-native security controls are the only effective response.
Robust security systems detect, contain, and neutralize malicious threats before they cause damage.
Cloud network security uses threat intelligence to counter the latest threats. Intrusion detection systems guard cloud gateways and scan network traffic. Anti-bot scanners also track emerging DDoS attacks. This prevents downtime from traffic flood attacks.
Security automation
Automation allows IT teams to work efficiently and securely. Users can automatically extend access controls and threat detection to new cloud resources. There is no need for lengthy manual configuration processes. New services receive instant coverage, limiting the risk of human error.
Cloud network security challenges
Cloud network security systems make sense for organizations that manage pure cloud or hybrid networks. But implementing cloud security is not a simple process. Challenges faced by organizations include:
Understanding the shared responsibility model
Under the shared responsibility model, CSPs and users share responsibility for securing cloud resources. Users accept this when they source cloud solutions. However, determining areas of security responsibility can be difficult.
Cloud users must secure apps and data stored on the cloud, manage user access, and monitor external threats.
CSPs are responsible for securing cloud infrastructure. They harden cloud servers to block data thieves or viruses.
This model leaves scope for overlap and confusion. For example, cloud users may rely on their cloud service provider's encryption. As a result, users may not apply encryption for data in transit or use Data Loss Prevention tools.
Define areas of responsibility before activating cloud services. Most SaaS providers build security features into their products, but users always have a role to play, and this varies between different cloud contexts.
Managing dynamic cloud environments
Change is a core feature of cloud deployments. Apps come online constantly, and configurations may change to reflect developing workflows. New users connect from home or abroad; individual employees can connect cloud containers with a few mouse clicks.
Automation can sometimes make this problem worse. For instance, companies may use autoscaling to build cloud deployments quickly. This boosts efficiency and leaves security teams scrambling to catch up.
Cloud network security systems need to adapt to change. Admins must track access requests, respond to alerts, and discover threats if they infiltrate the network infrastructure. This is even harder in hybrid environments that mix on-premises systems with extensive public and private cloud deployments.
Cloud network security best practices
Achieving cloud security can be challenging. But managing cloud security is far from impossible, even for small businesses. Follow these cloud network security best practices and build a security solution that meets your goals:
1. Apply Zero Trust principles
Zero Trust Network Architecture (ZTNA) is a security model that teaches users to trust no one. This is a good rule to apply when securing cloud infrastructure.
Avoid situations where users have global network privileges, and adopt a denial-by-default stance. Require more than one authentication factor when allowing user access. Segment cloud environments to limit east-west movement within the network.
Zero Trust changes the focus of security strategies to meet cloud computing needs. Instead of policing the network edge, admins concentrate on managing identities. This is a good fit for dynamic cloud environments. Deployments may constantly change. But user communities are easier to manage.
2. Lock down interfaces between the cloud and the internet
Internet-facing assets are a critical security risk. Access portals, web forms, and email accounts connect with the wider internet. This makes them common vectors for malware and data theft attacks.
Configure cloud apps to minimize contact with the internet. If necessary, leverage threat protection tools to guard vulnerable points. Web Application Firewalls (WAFs) can deny access to suspicious network traffic. DDoS and intelligent detection systems handle malicious agents that breach the firewall.
Set automated alerts to inform admins about potential risks. When building cloud network security systems, prioritize internet-facing assets. Carry out enhanced risk assessments, log user activity, and test access controls to secure entry points.
3. Use micro-segmentation to protect critical data
Cloud security systems usually include the ability to micro-segment networks. Micro-segmentation lets you guard critical data with an additional layer of protection. This has security benefits while also helping companies comply with relevant data security regulations.
4. Use private cloud solutions to enhance security
Private clouds allow users to communicate and collaborate without creating links to the external internet. This limits the scope for attackers, whether they use email phishing or malware injection.
Build networks that blend private and public cloud tools without compromising security. Determine which workflows require internet access. Switch everything else to private access technology that does not require external IP addresses.
5. Work with partners to establish security responsibilities
The principle of shared responsibility divides security functions between service providers and consumers.
Before commissioning new SaaS or IaaS products, be clear about security responsibilities. Create a security policy for each cloud service explaining your areas of responsibility and the security controls you will use. This should complement your cloud partner’s security policy. There should be no areas of ambiguity.
6. Write and deliver clear cloud security policies
Robust cloud network security rests upon good documentation and organization.
Cloud security policies define the controls used to secure cloud resources. This could include multi-factor authentication, Identity and Access Management, and data encryption. Policies also inform users about their security responsibilities.
Every SaaS app or cloud-hosted database should have a security policy. Store policies centrally. And use automated delivery to ensure that policies are implemented consistently and rapidly.
The role of AI and machine learning in cloud network security
Cloud network security is advancing all the time. And one of the most exciting research areas is the application of Artificial Intelligence to secure cloud environments.
AI harnesses machine learning to assess cloud security threats. Also known as User and Entity Based Analytics (UEBA), this technology scans user activity to detect malicious agents. AI engines compare real-time user behavior to logs of previous activity. In theory, this information helps to authenticate legitimate users and unmask intruders.
However, UEBA faces some challenges before becoming mainstream. For example, AI requires structured data sets and vast amounts of information to function properly. Generating useful data takes time and may also breach privacy regulations.
Attackers will also adapt to the use of machine learning. Expect to see Advanced Persistent Threats (APTs) that gather user activity data and build fake profiles to fool UEBA scanners. If IT teams rely too much on AI, this could become a security threat.
Cloud network security: key takeaways
Legacy security systems were designed for on-premises networking. Next-generation cloud security tools are built into the cloud, operating alongside SaaS apps and cloud infrastructure.
Threat detection systems neutralize malware attacks.
Access management tools block unauthorized users.
Segmentation keeps high-value assets safe behind additional barriers.
Encryption conceals data from external intruders
These features work together to mitigate security risks associated with the cloud. In a world where businesses depend on cloud infrastructure, robust cloud network security is essential.
Looking for a cloud network security solution?
NordLayer will help you build a customized cloud network security architecture. Our products include various cloud-native features to protect data and enable secure collaboration. For example, users benefit from:
Seamless identity management.
Threat blocking tools to analyze network traffic and block cloud threats.
Secure gateways link remote workers to the cloud
Control access with IP allowlisting.
Achieve reliable, comprehensive cloud network security. Get in touch with NordLayer and discuss your options today.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she has dedicated her life to simplifying complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.