Many VPN providers include TLS tunneling in their services. This form of VPN protection uses TLS encryption to lock down the traffic data of browser users. It can also safeguard web-based portals between home workers and on-premises networks.
This glossary article will look at what is TLS security, how TLS VPN services work, and whether TLS provides enough protection in today's cybersecurity environment.
TLS VPN definition
TLS VPN is a security protocol that uses Transport Layer Security (TLS) to create encrypted tunnels between a client and a server. It encrypts the data and confirms the identities of both parties. TLS VPN is often used in secure web browsing and remote access VPNs.
What is TLS VPN?
TLS and SSL is a VPN protocol that replaced the existing Secure Sockets Layer (SSL) protocol in 1999. SSL was the first security protocol to lock down web traffic at the Transport Layer of the OSI networking model (layer 4). However, hackers soon found ways to compromise SSL data encryption. The same has not yet happened to the TLS protocol.
TLS has now reached version 1.3. Like SSL, it operates at the Transport Layer. This makes it useful for protecting traffic data transmitted by web browsers, Voice-over-IP apps, email clients, and messaging apps.
The combination of data authentication and encryption also makes TLS a good fit for VPN services, that protect Layer 4 data.
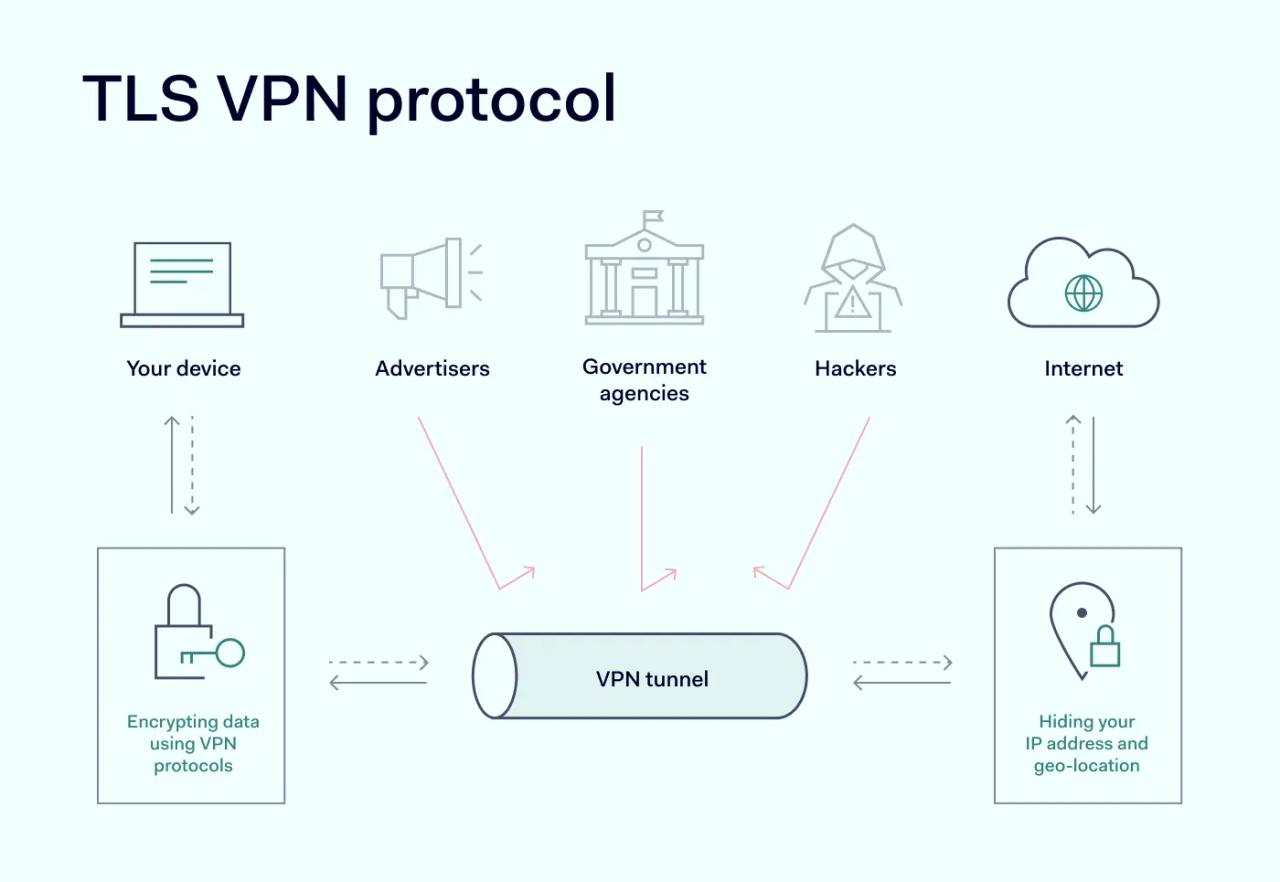
A Virtual Private Network (VPN) is a service that creates a virtual network on top of physical data flows. Data packets move through encrypted tunnels that wrap payloads in unbreakable code. Servers also anonymize user identities, assigning new IP addresses to each packet. This allows users to change their digital location and evade surveillance or cyber criminals.
TLS VPNs are usually clientless. There is no need for separate software to establish connections and control access. This style of VPN also works with HTTP, allowing it to work seamlessly with most modern websites. It functions in the background, adding another cybersecurity barrier for web users.
How does Transport Layer Security (TLS) VPN tunneling work?
TLS VPNs protect data by creating VPN tunnels. These tunnels are connections between two defined devices that encrypt data and authenticate transfers to ensure data integrity. VPN types create tunnels in different ways, and the technique used is as follows:
1. Connection
Firstly, the TLS protocol must establish a connection via a cipher suite negotiation. This informs the client and server involved that the TLS protocol will be used in the data transfer. Browsers can make a direct request, or they can just open a port used by TLS. This is generally port 443.
2. TLS handshake
The second stage in the process is the TLS handshake. This involves exchanging keys between the VPN client and the VPN server using asymmetric Public Key Infrastructure (PKI). Key exchange allows the devices to create a Master Secret that is unique to each transfer. This Master Secret forms the basis of the MAC code, which authenticates the whole process. PKI also creates session keys that are used in symmetric cryptography to hash data as it passes between the two devices.
3. TLS record
When TLS handshake has created the encryption keys, TLS record applies encryption and sends data securely via the TLS tunnel. Record divides the payload into packets and uses digital certificates to authenticate each packet at either end of the transfer. TLS record applies strong encryption to each packet, and processes the transfer via the Transport Control Protocol (TCP).
A TLS handshake applies end-to-end encryption (E2EE). Data in hash form is unreadable to outsiders while in transit. The VPN tunnel ensures that even if sensitive information is intercepted, attackers will not be able to use it. The only weak points are at both ends of the transfer, where data is encrypted or decrypted.
At the same time, the VPN server anonymizes IP address information. Data sent over the web will not be directly linked to the user's device. A good VPN should even hide the websites involved. Instead, external observers see anonymous data packets and can learn very little about the user's online behavior.
Pros and cons of TLS encryption protocol
No data transfer method is flawless. Users have to balance factors like encryption strength, stability, speed, and compatibility. But where does Transport Layer Security stand in this regard? Many TLS benefits make it a viable VPN option, but there are also some cons that users need to know.
Pros
- Well-suited to web applications. One of the biggest TLS advantages is that it works with browser and web portals. All users need is a browser-based client, and clients are often integrated into browsers like Firefox or Chrome. TLS handles encryption for most websites and also uses the HTTPS protocol, which is rarely blocked on public wifi.
- Granular access controls. Administrators can use the TLS protocol to set fine-grained access controls at the web gateway. Security teams can create security policies specifying which websites to filter and the web applications available to each user. Access control can be tailored to every user, every application, and even web objects. This is harder to achieve with alternative VPN styles.
- More efficient server management. Access controls via TLS also have efficiency benefits. For instance, network managers can set uniform access policies for each application at the web gateway. With other VPN styles, managers may need to create access policies for each user at the Operating System level. TLS can also secure gateways to SaaS services – streamlining resource use on application servers.
- Clientless access. SSL/TLS VPNs are embedded into web browsers and web-based apps. Users do not need to purchase, install, and configure separate VPN clients. Any transfers via the web are secured via encryption and users can easily access the services they need. With IPSec, admins need to create policies for each connection. That's not the case with TLS.
- Strong security. TLS 1.2 is classified as highly secure by industry watchdogs and has few known security vulnerabilities. AES 256-bit private key encryption guards against data theft, while certification provides watertight authentication. The result is an encrypted link that ensures data reaches its destination without interception.
Cons
- TLS only secures web resources. One of the biggest drawbacks of TLS is that it is restricted to web contexts. Unlike IPSec, TLS does not provide thorough network perimeter protection outside this context. In situations with a diverse application mix, security gaps may put data at risk. Users can install desktop agents to cover specific apps, but this adds to maintenance overheads. Not all apps are compatible with unsigned Java, which can also pose compatibility issues.
- Users may experience connection speed issues. When you engage TLS on a web browser, the VPN will make access requests every time you click a link and change sites. This starts the handshake and encryption process, adding latency. New techniques such as TLS False Start and TLS Session have reduced access times, but if you need high VPN performance, IPSec may be preferable.
- Implementation can be complex. While using TLS as a VPN is simple, setting up VPN protection can be tricky. Creating TLS certificates is a complex process and comes with high upfront costs. Website owners must also ensure that all sub-domains and web apps are configured for TLS security.
- Vulnerability to DDoS attacks. Denial of Service Attacks can cause issues with the TLS protocol. Attackers can mount TCP floods that render session tables inoperative and may cause website or network downtime.
History of SSL & TLS VPN protocols
The history of Secure Sockets Layer stretches back to the birth of the World Wide Web. Browser company Netscape introduced SSL in 1994 as a way to secure web traffic via an encrypted link. SSL 2.0 followed in 1995 and SSL 3.0 in 1996.
Unfortunately, TLS and SSL proved vulnerable to man-in-the-middle attacks like POODLE and DROWN. In 2011, the Internet Engineering Task Force deprecated SSL 2.0, and SSL 3.0 was deprecated in 2015. Both are now deemed almost completely unsafe by the US government and industry experts.
TLS arrived in 1999 as security concerns about SSL grew. TLS 1.1 appeared in 2006, and TLS 1.2 in 2008, before TLS 1.3 debuted in 2018. Obsolete protocols and ciphers have been removed at every stage, while developers have streamlined the handshake procedure. The result is a web-friendly transfer protocol that delivers data security and privacy, while striving for maximum speed.
Difference between TLS and HTTPS
TLS (Transport Layer Security) is a protocol that encrypts communication and secures data transfer between a client and a server. HTTPS (Hypertext Transfer Protocol Secure) uses TLS to protect data sent over HTTP. So, when you see "https://" in the address bar of your browser, it means that TLS is being used to protect your data, such as when making online purchases or logging into your email.
Are SSL and TLS the same?
While SSL and TLS have the same family tree, they are definitely not the same. The most important difference is effectiveness. SSL has been delisted as a recommended transfer protocol, while TLS continues to improve and find new uses. But there are other differences that make TLS superior:
- Compatibility. Many browsers and apps now lack support for SSL 3.0. TLS is widely recognized and used to secure web content. TLS certification is even used by Google's search algorithm as a positive metric when ranking websites.
- Encryption keys. SSL supported very few encryption key formats. That has changed with TLS. Users can choose from many different key formats, providing more flexibility and interoperability. SSL also used Message Authentication Code (MAC) encryption. TLS uses stronger Hash-based Message Authentication Code (HMAC) encryption.
- OpenVPN. OpenVPN has become a standard foundation for VPNs worldwide, but it does not work with SSL. On the other hand, users can combine OpenVPN with TLS to create web-based privacy configurations.
It's important to note that the term "SSL certificates" is still common. But these certificates are not based on SSL encryption. Almost all use TLS instead. The name "SSL" has simply been retained due to familiarity.
SSL/TLS VPN most frequent use cases
SSL/TLS is a mainstay of the cybersecurity world. You have probably used it today when surfing the web without realizing it. There are many potential use cases for TLS security, including:
Remote access VPN
Companies may want to ensure remote users have secure access to centralized resources. In that case, a web-based TLS Virtual Private Network could be useful. Workers can access secure connections via standard browsers. The VPN works on almost any device and OS, and protection follows users around the world.
Using public wifi
Sometimes, we need to work remotely on public networks. VPN coverage is essential, as public wifi networks are notoriously vulnerable to man-in-the-middle cyber attacks. With a TLS based VPN, user browsing will remain private, blocking potential attackers.
Connecting across firewalls
TLS can easily traverse NAT routers and firewalls. Port 443 is open on almost all standard firewalls, allowing encrypted VPN traffic to pass through unimpeded. This is not the case with VPNs based on UDP data such as IPSec.
TLS — strong web encryption for business users
Transport Layer Security delivers almost unbreakable encryption and reliable authentication for web users. With a TLS VPN in place, users can access websites and exchange confidential information with minimal data loss risks. Companies can create secure gateways to web applications, including SaaS tools, for better TLS security for data exchanges.
TLS has a few weaknesses. TLS VPNs may not cover every app in use on a corporate network. IPSec can beat TLS in terms of speed and is also more resistant to threats like DDoS attacks. However, TLS remains a leading security option for securing Layer 4 traffic.