L2TP is often part of a Virtual Private Network (VPN). But what is L2TP? It is encountered in VPN setups, which work with other protocols to create secure connections.
L2TP and PPTP were both developed by Microsoft and Cisco, with L2TP being introduced as a more secure replacement for the older PPTP protocol. It combines elements of PPTP and Cisco’s Layer 2 Forwarding Protocol (L2F) to establish point-to-point connections at the OSI model’s Layer 2. In 2005, L2TP was upgraded to L2TPv3, which improved its speed and encapsulation capabilities. It became a standard feature in VPNs today, often paired with IPSec for encryption and security.
What is the L2TP VPN protocol?
The Layer 2 Tunneling Protocol (L2TP) is a protocol that creates a secure tunnel for sending data between two points in a network. While it doesn’t encrypt data on its own, it’s often paired with encryption protocols like IPSec. L2TP is mainly used in VPNs to secure connections over public networks.
L2TP protocols & components
The Layer 2 Tunneling Protocol actually comprises two protocols: Microsoft's PPTP and Cisco's LTF. In practice, there are two endpoints of a tunnel created via L2TP: the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS):
L2TP Access Concentrator
The LAC receives data from remote devices and routes it securely to the LNS. The LAC negotiates a Point-to-Point (PPP) connection to transmit data frames. It could reside in company data centers, but LACs can also be integrated into ISPs to route L2TP traffic across the internet.
L2TP Network Server
The LNS is at the other end of the L2TP tunnel and functions as the termination point for PPP sessions. It acts as a gateway between public and private networks and allows encrypted traffic to access network assets.
How does L2TP work?
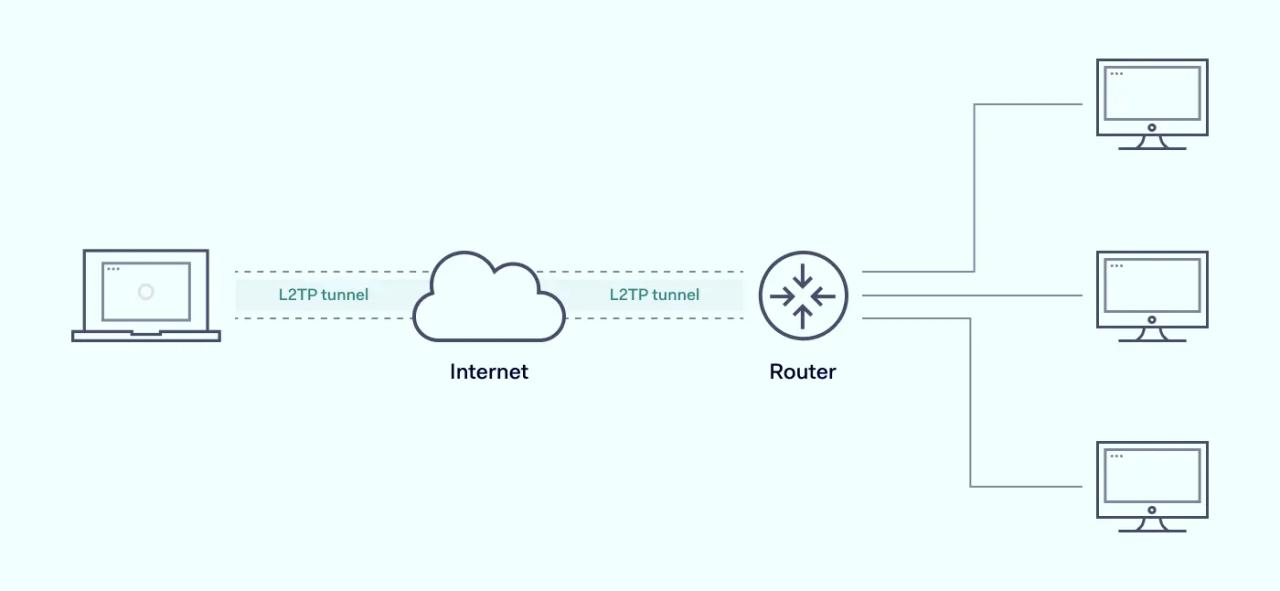
L2TP carries OSI Layer 2 traffic across Layer 3 networks. It achieves this in a three-stage process.
- Firstly, L2TP must create a connection between the LAC and the LNS. The LNS and LAC serve as endpoints for the point-to-point tunnel, and they must negotiate the relationship between them before transmitting any data. Each device in the chain will be assigned an IP address.
- The second stage involves negotiating the transfer. L2TP must enable the PPP link layer, creating the conditions for data transmission. Data frames are then encapsulated and prepared for transfer.
- Finally, L2TP creates the tunnel. This is generally a direct link between the remote workstation and a LAC at their local Internet Service Provider (ISP). The LAC accepts the tunnel and assigns a network slot. The LNS creates a virtual PPP interface and frames travel between the endpoints. The LNS then removes encapsulation information and passes every individual IP packet to the local network server as a regular frame.
As the example shows, this enables Layer 2 network identities to communicate across long distances. Remote workstations and central servers can establish a secure single tunnel for transferring confidential data and workflows.
How IPSec works with L2TP
L2TP does not work alone. The protocol itself lacks encryption and authentication features, and an additional protocol must supply both security functions. In most cases, Internet Protocol Security (IPSec) provides these data protection services, which is why we commonly use the designation L2TP/IPSec.
IPSec enables L2TP to serve as a VPN connection with end-to-end security. The two protocols encrypt payloads and IP headers via 256-bit AES encryption and Internet Key Exchange (IKE) handshakes. Data passes over UDP port 500 and is also prepared for transfer as an Encapsulated Security Payload (ESP).
ESP allows the LAC and LNS to determine the origins of data payloads, and to authenticate transfers. Encrypting multiprotocol packets and IP headers conceals information about the actual data and allows routing via virtual networks. L2TP acts as the tunneling agent, setting up connections to send this encrypted data.
What is L2TP used for?
The initial purpose of L2TP was to replace dial-up connections for remote networks. Companies required a way to connect workers, central offices, and branches without incurring large dial-up bills. Layer 2 tunneling made connecting via the public internet easier, reducing the cost of communication. It is also built on older tunneling protocols, adding new security features.
Since 2000, the protocol has found many uses in the business world. Here are just a few common use cases that show how versatile L2TP can be:
L2TP as a VPN
L2TP cannot be used alone as a VPN protocol. To create a VPN connection it must be paired with an additional protocol – to deliver end to end security and anonymity. This companion protocol is usually IPSec.
Layer 2 VPN tunnels are an effective option for connecting remote devices to central offices. Remote workers can install L2TP/IPSec clients and route traffic via L2TP VPN servers. The L2TP protocol creates a direct tunnel for layer 2 traffic, while IPSec provides encryption and authentication. ESP also wraps IP information and data in another layer of encryption, creating a format that is well-suited to VPN routing.
An L2TP/IPSec VPN connection will rarely require the installation of new software. Clients come built into Microsoft Windows, macOS, and Linux. The protocol also offers iOS and Android compatibility, completing extremely wide device coverage.
L2TP to extend a LAN
Companies can use L2TP to extend their LAN-based corporate network to include remote devices. This is a useful feature for work-from-home arrangements and on-site remote work.
The protocol creates stable tunnels between remote devices and the central LAN. Various LANs can also be bundled together by L2TP tunnels. This is a good way to link together branches or company departments in different locations.
LCCE endpoints in each location make LAN extension with L2TP possible. The LCCE center acts as a bridge, linking local ethernet data with L2TP payloads. IPSec is added over the top, encrypting communications between different LANs.
L2TP as a part of an ISP network
ISPs use LANs to resell portions of their capacity and route traffic for private clients. For example, ISPs with spare capacity may sell bandwidth to other providers for their own traffic. Layer 2 tunnels owned by the buyer can route traffic from their customers without interfering with the host ISP.
In cases like this, the wholesale ISP runs a LAC, and clients lease secure connections. IPSec encryption above the L2TP tunnel ensures that traffic is not visible to the wholesale ISP, keeping customer IP address information private.
L2TP in a public-access Wi-Fi network
L2TP tunneling is regularly used to construct and secure public wi-fi networks. This is a common feature of networks owned by large organizations such as colleges, schools, libraries, or airports.
Organizations maintain a network of wi-fi access points. Customer devices connect with individual access points, which create an L2TP session.
Layer 2 Tunneling Protocol appeals to many organizations because it reduces the cost of supplying internet to diverse access points. It is not necessary to arrange individual connections at each access point. Traffic can be securely routed to a single provider via tunneling protocols.
The benefits and drawbacks of L2TP
L2TP/IPSec is a popular means of creating VPN systems. But it isn't the only protocol around and it isn't without its flaws. Let's quickly run through some pros and cons to understand where L2TP fits into the wider picture.
Advantages of L2TP VPN services
- Strong security with IPSec. When Layer 2 Tunneling Protocol combines with IPSec, data should remain secure and private. IPSec delivers strong encryption that is virtually uncrackable. There are rumors that the NSA cracked IPSec, but no hard evidence exists that the protocol is compromised.
- Easy to use. Setting up an L2TP VPN connection is simple. The tunneling protocol is built into major operating systems. For instance, users can set up an L2TP VPN in seconds via Network Settings in Microsoft Windows.
- The flexibility of L2 networking. Level 2 connectivity has some advantages over Level 3 VPNs. Companies can share infrastructure between different locations more easily. It is also easier to shift Virtual Machine infrastructure between physical devices as needed. L2TP can also use a variety of tunnel media, unlike PPTP which is only capable of handling IP tunnels.
- Speed. The Layer 2 Tunneling Protocol is known for its speed. In many cases, using L2TP is as fast as non-encrypted connections.
Disadvantages of L2TP
- Problems with firewalls. L2TP operates on port 500, which can lead to issues when traversing firewalls and NAT gateways. In most cases, an L2TP passthrough is required, for the transparent transmission of several protocols over firewalls.
- Speed drops with IPSec. The speed advantages of raw L2TP may disappear when IPSec encryption is applied. This is especially true when double encapsulation is in use on a VPN connection.
- Instability. Firewall and general connectivity issues mean that using L2TP/IPSec is often less stable than an alternative VPN protocol such as WireGuard or OpenVPN.
What port does L2TP use?
Most L2TP connections use the UDP 500 port to connect devices. UDP 500 is used with IPSec when IKE encryption keys are required. UDP port 4500 may be used for NAT traversal, while the L2TP server uses port 1701 and does not receive inbound traffic.
Does L2TP provide encryption on its own?
No. This is an important fact about using L2TP. On its own, L2TP simply creates stable tunnels between devices. The protocol does not apply strong encryption to make data payloads unreadable. It also does not authenticate each individual IP packet as it passes between devices, and the IP address of packets will also be exposed while in transit. L2TP does not provide sufficient safeguards to ensure data integrity and guard user data against attacks. That is why IPSec generally accompanies L2TP, and the two protocols work together.
L2TP vs. PPTP
L2TP (Layer 2 Tunneling Protocol) provides stronger security than PPTP (Point-to-Point Tunneling Protocol) because it uses IPSec for encryption, while PPTP relies on weaker encryption methods. L2TP is better for applications that need strong data protection, while PPTP offers faster speeds but less security. For instance, a company needing secure remote access for employees would likely choose L2TP vs. PPTP to safeguard sensitive information.
L2TP vs. IKEv2
When comparing L2TP vs. IKEv2, L2TP is a VPN protocol that uses IPsec for data security, but it can be slower because of double encapsulation. IKEv2 (Internet Key Exchange version 2) also works with IPsec but offers faster speeds, better stability, and automatic reconnection. For instance, IKEv2 is preferred on mobile devices because it quickly reconnects if the connection drops, such as when switching between Wi-Fi and mobile data.
Understanding L2TP tunneling
L2TP offers layer 2 tunneling between networks and devices. It has many uses as a bridge between LANs, while L2TP is also a popular component of Virtual Private Network services when paired with IPSec. To recap, let's run through what we know about the protocol's strengths and weaknesses.
- L2TP must be used with an extra protocol that delivers encryption and data authentication. This protocol is generally IPSec.
- L2TP works at OSI layer 2, making it well-suited to linking local networks and forming bridges between branch locations.
- L2TP is embedded in Microsoft Windows, macOS, Linux, and mobile operating systems. It can work with most devices and is easy to configure.
- L2TP/IPSec is a secure VPN protocol and delivers relatively fast speeds. It can link remote workers with central offices, and lock down data transfers across the public internet.
- Companies may encounter problems with firewalls and NAT gateways when using L2TP. Passthrough methods may be needed to ensure smooth traversal. As a result, other tunneling protocols may be preferable.