Phishing, smishing, and vishing use persuasion and deception to convince targets to take risky actions. But while these cyberattack types are related, they work in different ways. This article explains each attack type and how they fit into cybersecurity strategies.
Phishing, smishing, vishing: understanding key differences
Phishing, smishing, and vishing are three types of social engineering attacks. All three techniques seek to deceive victims by imitating a legitimate company or contact.
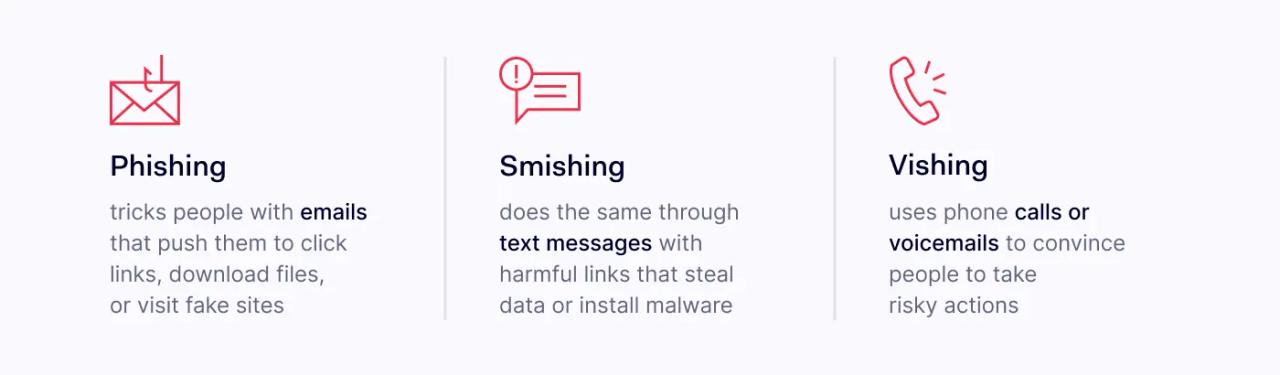
Successful attackers obtain valuable information to launch identity theft attacks. They may also gain access to private networks, leading to damaging cybersecurity incidents. However, while the underlying goal is similar, attack methods differ. Phishing uses emails, smishing uses SMS messages, and vishing uses voice calls to deceive targets into clicking links, downloading files, or providing sensitive information.
What is phishing?
Phishing attacks use emails to deceive targets. Attackers pose as trusted contacts, including personal connections, clients, or reputable companies. They use persuasive text to direct victims to follow clickable links or download attachments.
Skilled phishers know how to create an illusion of legitimacy. Professionally designed phishing emails closely resemble the real thing, while embedded links direct victims to credible websites that promote trust.
These tactics are extremely effective. Up to 91% of cyber attacks start with phishing emails. And the average cost of a phishing attack in 2024 reached $4.88 million.
When victims click through or download, the consequences can be severe. Attackers often design fake websites to collect personal information such as passwords, credit card numbers, or user IDs. This data is then funneled directly to cybercriminals, who may use it in secondary attacks or sell it via the dark web. Run a dark web scan to check if any of your company’s information has been leaked or exposed.
Phishing techniques include emails from Microsoft asking users to change their Teams or Office 365 credentials. Fake emails from Amazon also hook victims with false tracking information or failed delivery notices. In other cases, attackers create fake invoices from known clients or invite targets to open Google Documents from existing email contacts.
Conventional email phishing is not the only variety to worry about.
For instance, spear phishing focuses on high-value users with administrative privileges. Some phishing emails specifically target high-level employees. These whaling scams leverage in-depth research into the target's professional record, contacts, and interests. They focus on elite targets to gain maximum network access.
What is vishing?
Vishing attacks use phone calls to convince victims to take harmful actions. These calls mimic legitimate business contacts, using contextual information to boost their credibility.
For example, vishing scams might claim to represent tech support partners needing to reset security settings. Attackers could pretend to be previous clients and request fake invoice payments.
Call scripts often ask for personal data, including the target's name, role, license number, address, and social security card or credit card numbers. However, more sophisticated attacks use multiple calls to build trust and obtain sensitive information.
Criminals often rely on automated robocalls to make large volumes of phone calls. However, there are many other ways to launch vishing attacks. Criminals could spoof caller IDs, create fake VoIP numbers, or even deploy AI bots to gather information and make tailored calls.
Attacks vary in their level of sophistication. At the higher end, attackers can spoof internal phone numbers and imitate security teams, leading to operating system takeovers or unauthorized file transfers. Victims rarely know they are speaking to imposters before it's too late.
Vishing scams are common, but many companies neglect vishing training in security strategies. Simulated vishing phone calls manage to compromise 70% of businesses, especially in customer support departments. This underlines the need for comprehensive training for all social engineering threats.
What is smishing?
Like phishing, smishing deceives targets with engineered content. However, smishing uses engineered SMS messages to deceive victims.
Cybercriminals craft text messages that resemble everyday messages from brands, colleagues, or clients. For example, criminals may pose as vendors and send a link to a new product page. Mobile users clicking on what they believe are legitimate links arrive at fake contact forms instead.
The fake contact form looks like a genuine article. Moreover, identifying fake sites is harder on smartphones than computers as address data is often hard to read. Users may enter confidential information without realizing it.
Other smishing attacks infect mobile devices with malware. Attackers could deliver ransomware that locks the device until users make crypto payments, but adware or spyware agents are also common.
Users can often identify smishing texts by their tone of voice. Criminals try to encourage a sense of urgency. They want victims to act without thinking. For instance, attackers could send fake alerts about tax demands or bank withdrawals.
This focus on urgency makes it critical to stay calm and train staff to use mobile devices responsibly. A short SMS message can deliver malware that infects an entire network, making vigilance and awareness essential.
Smishing is a serious cybersecurity threat. Around 75% of organizations dealt with smishing incidents in 2023, with attackers exploiting hybrid bring-your-own-device practices and increased remote working. Click-through rates on SMS messages vary from 8.9-14.5%, compared with 2% for emails. These stats make SMS appealing even for low-skilled attackers.
How to prevent smishing, vishing, and phishing attacks
Companies need comprehensive strategies to prevent phishing, smishing, and vishing. Security teams cannot neglect any attack technique, as criminals will eventually find and exploit vulnerabilities.
The prevention methods below can help you reduce phishing risks.
Phishing prevention tips
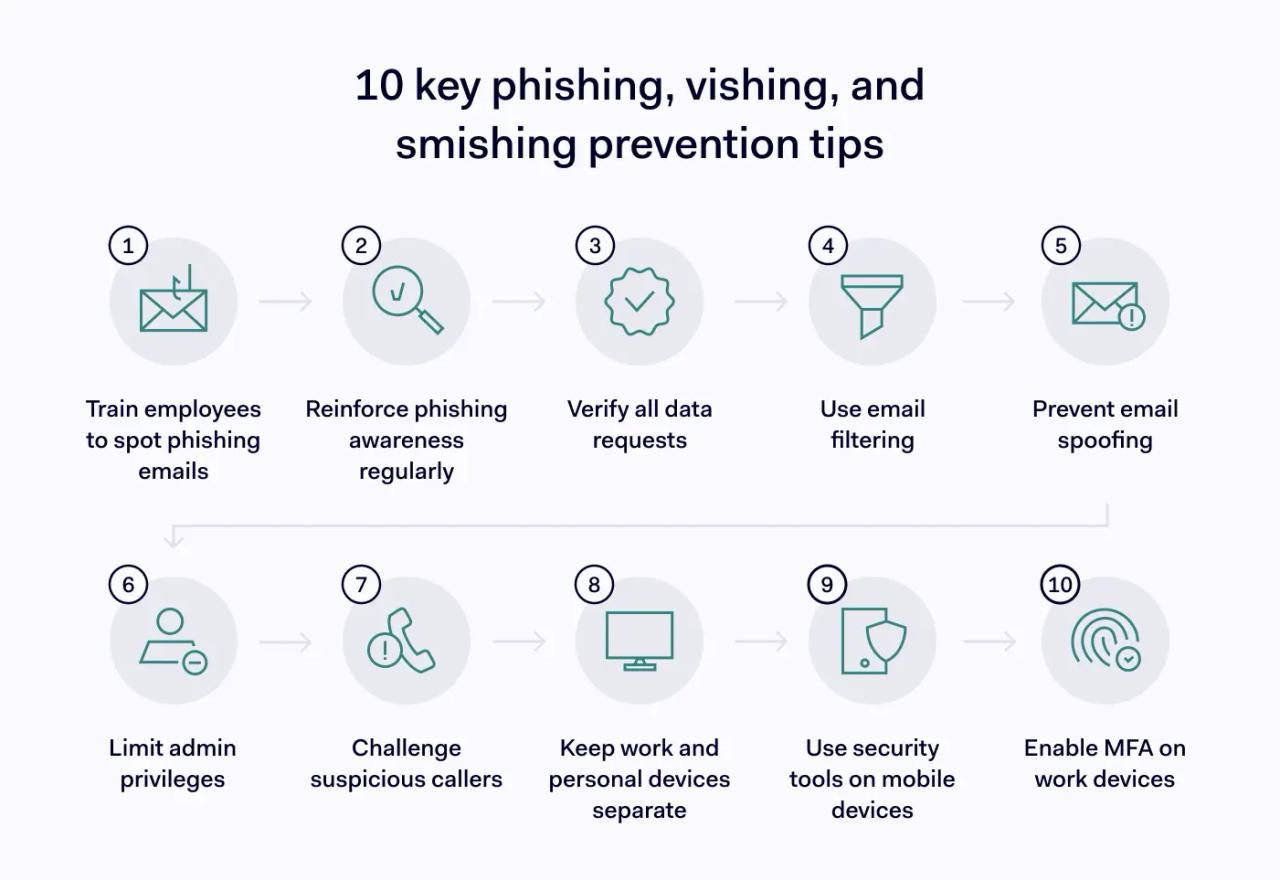
- Train staff to identify suspicious emails. Phishing awareness training is critical. Staff should be able to identify suspicious links and attachments, check for fake sender addresses, detect misspelled URLs, and parse email contents for tell-tale anomalies.
- Reinforce employee knowledge. Phishing awareness fades over time. Maintain vigilance and knowledge with annual phishing training, including scenario-based exercises to identify phishing emails.
- Never trust requests for confidential information. Treat all data requests as suspicious unless you have specifically requested them. Verify with the organization contacting you that the request is legitimate and meets a business need.
- Implement email filtering. Email filters use threat intelligence databases to scan incoming messages for known threats.
- Prevent internal email spoofing. DMARC, DKIM, and SPF protocols help you authenticate every internal email. Use these protocols to detect spoofed messages and ensure trust within your organization.
- Manage privileges to shrink the attack surface. De-escalate administrative privileges promptly. Apply the principle of least privilege to limit the freedom of successful phishers.
Vishing prevention tips
- Enforce secure communications policies. Employees should not provide personal or confidential information to unknown callers. Verify the identity of every caller, even if they claim to represent a legitimate company.
- Train staff with vishing workshops. Introduce vishing tactics with real-world call scenarios. Show how easy it is to deceive people via simple requests, and suggest ways to assess risks related to each phone call.
- Don't be afraid to challenge callers. Vishers rely on goodwill from their targets. Don't fall into their trap. Offer to call back, then contact the caller's organization to check their identity. Legitimate callers won't mind, and you may catch malicious actors.
- Use up-to-date caller ID tools. Identify every caller via cutting-edge technology. Update caller ID systems to stay ahead of spoofing techniques.
- Inform partners about vishing attacks. Vishers often imitate trusted clients or partners. Share information about attack methods and collaborate to identify the source of the problem.
- Check for data leaks or other phishing attacks. Well-informed criminal callers need a source of information about your organization. Assume there is another data breach or identity theft attack, and take appropriate action.
Smishing prevention tips
- Separate work and personal devices. Employees need a dedicated smartphone for professional tasks and should not mix personal emails or social media with daily workflows.
- Train employees to use mobile devices safely. Employees should know the risks linked to every text message. Train staff to avoid links from unknown contacts and avoid entering sensitive information without obtaining verification first.
- Use security tools to identify suspicious downloads. Ensure employees install antivirus tools and URL scanners that actively scan each text message for malicious content or risky links.
- Minimize reliance on SMS for business purposes. Use secure communication channels and collaboration platforms. Don't routinely send confidential information via text messages.
- Require MFA on work devices. Multi-factor authentication demands multiple credentials for network or device logins. This guards against credential theft, making successful smishing attacks less damaging.
Remember that phishing relies on human error. Security professionals depend on an informed and knowledgeable workforce to detect suspicious calls or text messages.
Combine phishing, smishing, and vishing training to cover every base. Comprehensive training drives home the point that even simple text messages or casual phone calls may compromise network security.
