Malicious software or “malware” is designed to infect and harm its targets. Malware attacks are a constant concern for businesses and individuals, and robust malware protection is essential.
This article introduces the history and concept of malware, explains the most common varieties, and suggests measures to protect against malware infection.
Malware definition
Malware is malicious software that infects targeted devices to cause harm. Attackers may spread malware to steal data or damage the networks of hostile organizations. In all cases, they do so without the target's knowledge and take steps to minimize the risk of detection.
The history of malware
Malware's origins are tied to early computing concepts. In 1966, famous mathematician John von Neumann published a “Theory of Self-Reproducing Automata.” This research paper outlined the form and function of malware agents, drawing attention to potential future threats.
Von Neumann's predictions were sound. Five years later, the Creeper virus began the first malware attack, spreading through ARPANET devices, just like modern worms. In 1982, Rich Skrenta created Elk Cloner, which anticipated rootkits by infecting Apple DOS operating systems.
In 1988, the Morris Worm became the first major worm to disrupt the internet. Within months, the Morris Worm infected 10% of devices connected to the early net. The worm's creator Robert Morris also made history, becoming the first person convicted of cyber fraud.
Since then, novel malware has expanded the arsenal of threat actors. 1999's Melissa Worm sparked the first email virus panic. In 2000, the ILOVEYOU virus added credential theft to the threat landscape. And 2007's Zeus was the first large-scale Trojan attack spread by phishing.
The 2010s saw the growth of ransomware and hard-to-detect “polymorphic” malware like Emotet. Botnets like Mirai also capitalized on expanding IoT infrastructure, resulting in a spike in denial-of-service attacks.
The 2020s have seen highly targeted attacks on national infrastructure (such as the Colonial Pipeline attack) and a boom in ransomware-as-service kits—making attacks more accessible for non-experts.
In 2023, companies reported just over 6 billion malware attacks worldwide. Email-based attacks are rising, while web attacks are becoming less common. Even so, malware still dominates the most common types of cyber-attacks.
The number of ransomware attacks has flattened, but high-profile attacks are becoming more frequent. The cost of ransoms also rose beyond $1 billion in 2023. This shows the importance of strong security and constant vigilance.
How does malware work?
Malicious software infects devices with code that carries out harmful or criminal tasks. Viruses are just one type of malware. Other types include trojans, worms, spyware, adware, ransomware, rootkits, and keyloggers. Each targets systems in different ways.
Most infections result from deception, and this happens in many ways.
- Phishing emails fool victims into thinking attachments or links are authentic and harmless.
- App download platforms host software that seems legitimate but delivers malware.
- Fake websites deliver payloads when victims click pop-ups or use compromised data fields.
- Attackers can load malware onto USB sticks and physically connect them to target devices.
After infection occurs, malware may start working immediately but can reside in the background for long periods. Whatever timing attackers choose, agents continue to operate until they are detected and removed or deliberately deactivated by their controllers.
Malware can significantly affect targets or have a minor impact. In the worst cases, companies experience crippling ransomware attacks or data breaches. Severe attacks lead to massive direct payments and—potentially—additional costs due to regulatory action and reputational damage.
Types of malware
Cyber-attackers use all possible methods to deliver malware agents. Some techniques target specific applications or fake websites. Others go to the root, targeting operating systems.
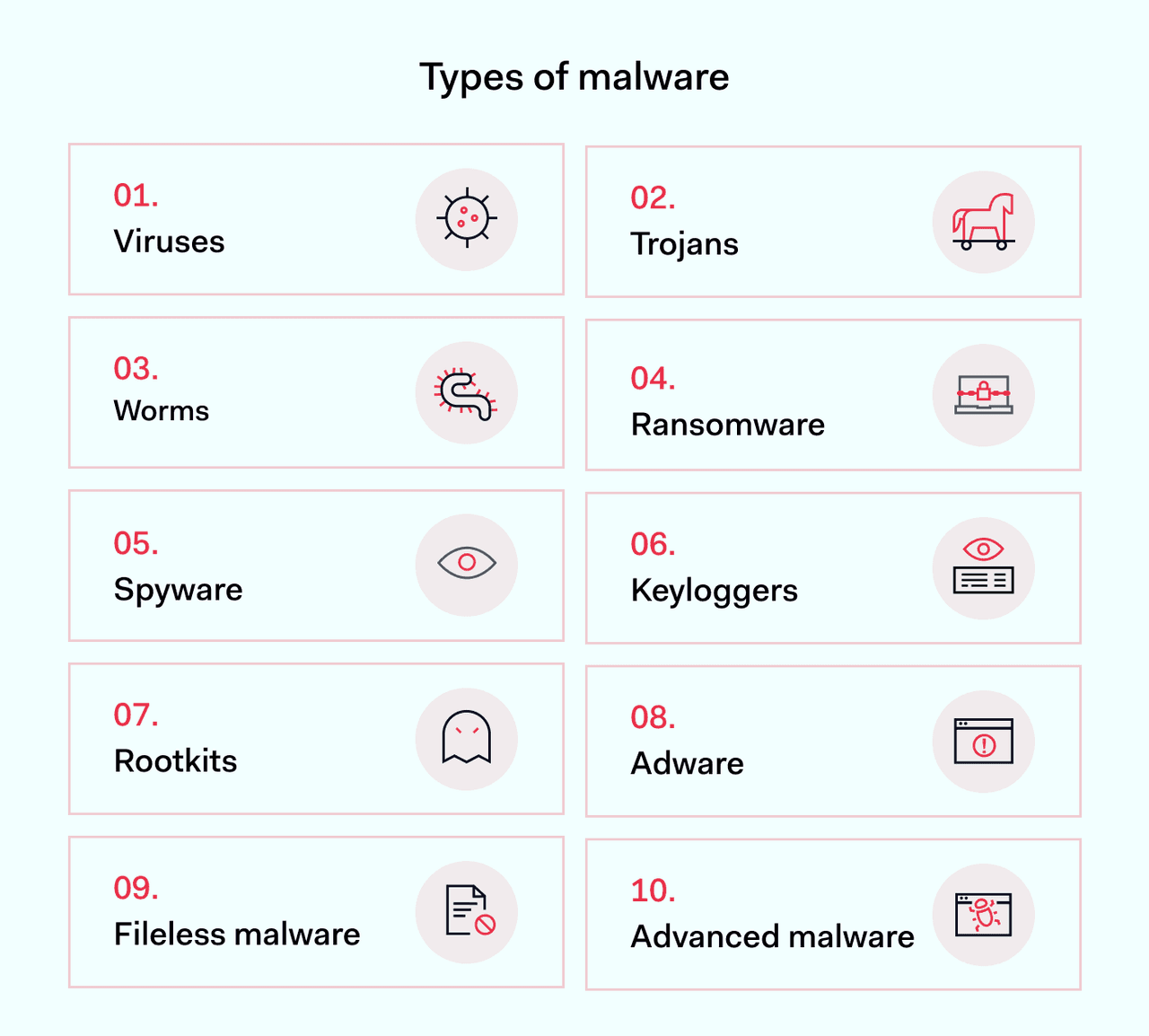
Organizations need policies to counter every threat listed below:
Viruses
Viruses are self-replicating programs that spread between applications and devices. They are one the oldest types of malware and probably the most familiar to internet users.
Viruses take many forms (some are covered independently below). For example, macro viruses target internal programs used by apps like Microsoft Excel. Boot sector viruses target system cores, while overwrite viruses erase file contents as they spread.
Trojans
Trojan viruses act like the mythical “Trojan Horse.” Attackers disguise malware agents as legitimate applications, documents, or even video games. Adopting a disguise entices targets to open infected files and launch malicious software.
When users activate Trojans, malware agents can modify, remove, or block data. They can send data to threat actors or compromise system performance by over-using bandwidth.
The good news is that potential victims often detect malware of this type before infections occur. Threat detection systems identify Trojan downloaders, provided that users regularly update threat databases.
Example: SocGholish is one of the most common forms of Trojan malware in 2024. This agent pretends to be a legitimate browser update. The update is available for download from otherwise legitimate websites, encouraging users to download it. When successful, the SocGholish agent paves the way for secondary malware, resulting in further damage.
Worms
Worms are so-named because they “worm” their way into networks via backdoors and can multiply without human input. This form of malicious software targets operating system vulnerabilities to gain access. When implanted, they spread quickly across all connected network infrastructure.
Once inside the perimeter, worms cause many network security problems. Common effects include file deletion, slowdowns, data exfiltration, and overuse of system resources.
Example: The most famous computer worm is Stuxnet, which attacked Iranian research facilities from 2010 onwards. The Stuxnet worm specifically targeted logical controllers, shutting down nuclear centrifuges and destroying over 1,000 devices.
Ransomware
Ransomware encrypts operating systems or applications, locking users out until a ransom is paid. Attackers may also use data-leak extortion, threatening to publish sensitive information if payments aren’t made. For some victims, avoiding public exposure can be an even greater motivation to pay.
Most targeted companies choose to pay ransoms, but not all payments are honored. Around 46% of the time, criminals return data in corrupted form. 80% of targeted companies also experience further ransomware incidents.
Attackers often stage multi-extortion attacks. In these attacks, criminals lock systems and exfiltrate sensitive data, demanding additional payments to return it.
Example: In June 2024, the eastern European malware collective BlackSuit locked IT systems at the automotive supplier CDK Global. System shutdowns cost partner dealerships almost $1 billion, while the eventual ransom reached $50 million.
Spyware
Spyware operates in the background, where malware agents collect data about user activity and identities. Spyware agents can infect desktops and laptop browsers, but all applications and mobile devices are potential targets.
Example: In the 2010s, Pegasus spyware harvested data from the devices of journalists across the world. Created by Israel's NSO Group, Pegasus was almost impossible to detect and affected over 50,000 targets.
Keyloggers
Keyloggers resemble spyware but have a specific role. They also operate in the shadows, collecting data about every key pressed by victims. If the keylogger evades detection, malware groups can extract login credentials, financial data, and other valuable information.
Example: The DarkHotel attack used keyloggers to target hotels. Hotels often provide unsecured wi-fi coverage—the ideal setting for malware attacks. DarkHotel also evades detection by remaining active for a defined period before deleting all traces.
Rootkits
Rootkits are powerful tools that give cybercriminals control over system operations. This form of malicious software targets the “roots” of networks and devices.
Rootkits target infrastructure like servers, hypervisors, operating systems, or kernels. This strategy allows attackers to assume extensive administrative privileges to extract data or cause disruption.
Moreover, rootkit attacks often prepare the way for secondary malware attacks. Admin privileges allow hackers to hide keyloggers or spyware effectively.
Example: The Zacinlo rootkit attack created havoc in 2018, using a fake VPN to implant malware on Windows 10 systems. When infected, Zacinlo blended Adware and Spyware functions.
Adware
Adware is a form of malware that forces target apps or devices to display digital advertisements. Sophisticated adware also tracks user activity. Agents use this data to serve ads and create profiles to sell to other threat actors.
Most adware attacks do not involve separate malware agents. Attackers bundle Adware agents with seemingly legitimate applications or browser extensions. Ads appear when users open these apps or appear as pop-ups while they use the web.
Example: Chinese-made Fireball adware has infected over 250 million devices, turning web browsers into “zombies” for ad delivery.
Fileless malware
Unlike other varieties, fileless malware does not implant separate agents on targeted systems. Instead, fileless malware alters system files to create backdoors.
Backdoors allow access to network assets but often appear legitimate to diagnostic tools. This strategy makes fileless attacks hard to detect and makes regular updates essential.
Fileless attacks have various targets. GootKit and Kovter attacks change Windows Registry code. The Duqu worm resides in system memory, while scripting attacks can implant malware in the code of documents and other legitimate files.
Example: The Equifax attack in 2017 used fileless vectors to compromise the data of 143 million Americans. In this case, attackers exploited an unpatched Apache Struts Java framework.
Advanced malware
Also known as Advanced Persistent Threats (APTs), advanced malware is harder to detect and remove than traditional variants. Hackers using advanced malware have greater command and control abilities. They can issue instructions about what data to steal, and how to spread.
Following attacks, advanced malware retreats into the background or deletes itself from the network infrastructure. This makes it difficult to trace the origins of attacks and the destination of extracted data.
Advanced malware is also associated with ransomware attacks, including high-profile agents like CryptoLocker and Cryptowall. Due to the consequences of successful ransomware, researching and counteracting advanced threats before attacks occur is vital.
How to detect malware
Malware protection is a critical task for security teams. Fortunately, companies have many ways to detect infections or attempted attacks before suffering harm.
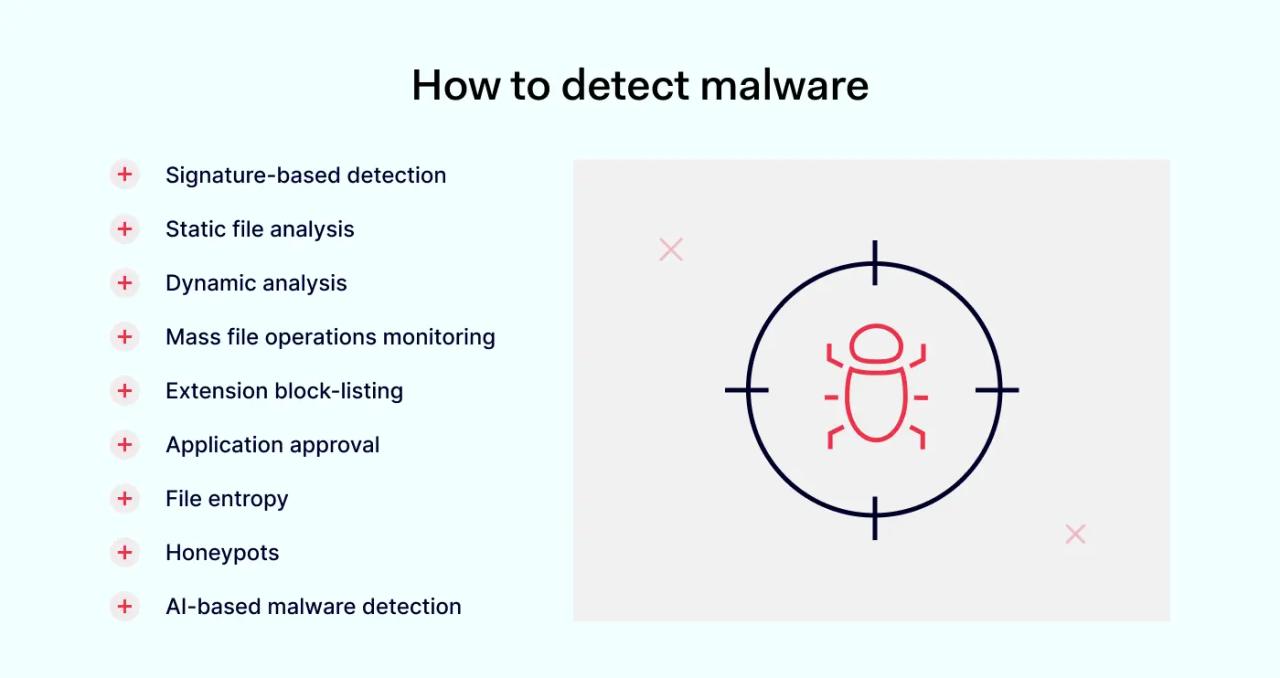
Detection methods include:
- Signature-based detection. Tools look for the trademark activity signature left by malware agents. This is a reactive measure that detects ongoing attacks. It does not prevent infection.
- Static file analysis. These tools analyze individual files for suspicious code markers. They also assess data associated with downloaded files, such as source IP addresses, encryption hashes, and header data. Checksum calculations can also detect file corruption.
- Dynamic analysis. Dynamic tools quarantine suspected malware in sandbox environments. Diagnostic tools execute quarantined files without risking escape into the wider network.
- Mass file operations monitoring. Malware often works by launching mass file operations such as move or delete commands. Scanning tools assess mass operations for signs of infection. Forensic auditing also dynamically analyses the integrity of file systems.
- Extension block-listing. Security teams can block the execution or download of files with high-risk extensions. This effectively blocks many Trojan viruses.
- Application approval. Users check applications to detect infected code or vulnerabilities. Security teams only allow access to apps or websites classed as malware-free.
- File entropy. Security systems monitor files to detect rapid changes in size or activity (common markers of malware infection).
- Honeypots. Malware honeypots act as attractors, exposing malware before it crosses the network edge.
- AI-based malware detection. Machine learning tools assess network activity to discover suspicious patterns.
How to avoid malware infections
All organizations must know how to prevent malware attacks. Malware detection tools help block and contain attacks, but prevention strategies are just as important. Security teams should adopt comprehensive endpoint protection measures, starting with DNS filtering and VPNs.
DNS filtering enforces security at the DNS level by restricting access to malicious or unsecured websites. This reduces the chances of accidental malware downloads from harmful sites.
VPNs also play a preventive role in malware defense:
- VPNs encrypt internet traffic, making it harder for threat actors to intercept sensitive data like passwords or financial details. This protects against attacks such as man-in-the-middle (MITM), which can lead to malware infections.
- VPNs hide your real IP address, reducing the risk of being targeted by threat actors. This makes direct attacks or malware delivery based on location much harder.
Combining DNS filtering with VPNs lowers the risk of malware infections.
Speaking about other measures, two-factor authentication (2FA) reduces the risks from stolen credentials. While it doesn’t protect against malware infections, it limits attackers’ ability to access systems. Even if malware compromises login details, 2FA adds a verification step that blocks unauthorized access.
Firewalls and allowlisting reduce risks if malware infects a system. These tools don’t stop malware directly but help limit access to sensitive data. This minimizes the chances of data leaks.
Incident management is crucial for handling malware threats. Security teams must consistently remove malware and prevent reinfection. Regular updates to anti-virus and anti-malware tools are essential for safe malware handling. A disaster recovery plan is also critical, ensuring quick restoration of operations after an attack. Periodic security audits help identify weaknesses and ensure systems stay prepared for evolving threats. Together, these measures provide comprehensive protection.
