The age of hardware firewalls and on-premises networks has long passed. Today’s firewall solutions must protect decentralized cloud environments. Firewalls must serve distributed remote workforces. And they need to deliver quality-of-life features that cloud users demand.
Cloud computing and software-defined networking bring new security threats. Attackers can work around traditional perimeter security measures. Virtualized environments have many endpoints and assets to target. Without cloud-native edge protection, a virtual network is virtually defenseless.
Virtual firewalls have stepped in to secure cloud deployments. Also known as cloud firewalls, virtual firewalls scale with virtual environments. They protect against north-south traffic and allow fine-grained segmentation within virtual networks.
If you maintain cloud assets, installing a virtual firewall probably makes sense. But there are some important things to know about these network security appliances. This article explains what they are and how virtual firewalls work. The result will be a solid grounding in cloud security.
Virtual firewall definition
A virtual firewall filters and monitors traffic within virtualized environments. It also secures the network edge where external networks and cloud platforms collide.
Virtual firewalls reside in cloud data centers. They protect assets on public clouds such as virtual machines and SaaS applications. But they also defend software-defined wide area networks (SD-WAN) and private cloud environments.
The role of a virtual firewall resembles traditional physical and next-generation firewalls. Packet filtering and content inspection assess incoming and outgoing traffic. This allows secure connectivity between the external network and cloud assets. It also creates a secure barrier between cloud assets and the public internet.
A virtual firewall segments public cloud deployments. The firewall can add logical separations between virtual machines. It applies network security rules to limit user freedom and block malicious east-west movement. This contains threats by reducing the internal attack surface. If intrusions occur, security professionals can contain attackers easily.
Why are virtual firewalls essential?
Traditional firewalls simply aren’t enough to protect modern, decentralized networks, operating in the cloud. A virtual firewall is critical because cloud environments are more exposed to threats than on-premises systems. Without the physical boundaries of a traditional network, businesses face a wider range of potential attacks.
A virtual firewall provides protection where the cloud meets external networks, shielding assets like virtual machines and SaaS applications. It also allows fine control within the cloud, preventing unauthorized access to sensitive data. Essentially, a virtual firewall safeguards the cloud, securing both external and internal traffic.
How virtual firewalls work
Virtual firewalls control incoming and outgoing traffic. Simpler versions use packet filtering to identify legitimate network traffic. More complex solutions add next-generation firewall features like deep packet inspection. This analyzes packet contents, detecting malware agents and the movement of sensitive data.
These features resemble standard firewalls. But virtual firewall systems only exist inside the cloud. They employ virtual switches to route traffic and segment cloud environments. Cloud firewalls also have two main modes: bridge mode and hypervisor mode.
- Bridge mode – In bridge mode, the virtual firewall acts as a “bridge” between the public cloud and the physical network. Just like physical firewalls, bridge mode assesses traffic entering and leaving the cloud. It diagnoses potential threats and allows or denies access.
- Hypervisor mode – In hypervisor mode, virtual firewalls are completely separate from the external network. The firewall operates as a virtual appliance within the cloud’s hypervisor kernel. This mode handles virtual network traffic. It segments applications from other virtual machines. Security teams can apply Zero Trust controls within the virtualized environment.
These two modes enable virtual network firewalls to protect cloud assets effectively. They also perform many valuable roles for real-world networks.
A virtualized firewall can extend physical data center coverage into a virtualized environment. This creates secure network interfaces to manage apps and transfer data. Or it could enable secure remote access for global workforces.
Key components and features of virtual firewalls
Virtual firewall systems include cloud-native components that protect virtual network assets. Critical security features of virtual security appliances include:
Microsegmentation to create zones of trust
Virtual firewalls use segmentation to create trust zones within cloud environments. The firewall limits lateral movement by screening access requests and tracking packet contents. When users seek access to a virtual machine, the firewall applies access control policies. Users with appropriate privileges can proceed. Other network traffic is blocked.
Cloud-native threat prevention
Virtual firewall solutions leverage a range of tools to neutralize cyber threats. Tools include:
- SSL decryption
- DNS filtering
- Anti-malware scanning
- DDoS blocking
- URL filtering
- Direct file blocking for sensitive data.
Threat prevention occurs in real-time, using data harvested from global threat intelligence.
Application-centric security policies
Cloud firewalls deliver security focused on virtual applications. The firewall can apply specific controls for every virtual machine deployed on the cloud network. The firewall also identifies cloud applications that are connected to the network. Automated provisioning tracks user activity and app changes. Application vulnerabilities trigger security alerts.
Automated scaling
Public cloud environments are dynamic. They can rapidly change in scale as new applications come online. Virtual firewalls adapt to changes in the virtualized environment. They automatically scale to meet the needs of continuous integration and continuous delivery programs. And firewalls also scale to handle new DevOps deployments.
Centralized visibility
Cloud environments are decentralized. But virtual firewall systems deliver centralized awareness. Control panels keep track of all connected virtual machines. Security professionals can calibrate access controls for every application. Traffic flows are legible and easy to manage. Threat alerts appear immediately, allowing prompt mitigation action.
Virtual firewalls make it easier to comprehend hybrid cloud deployments. Business clouds can become extremely complex. Security issues may be undetected for years. Centralized visibility and security controls are the only effective solution.
Benefits of using a virtual firewall
The features of virtual hardware solutions add up to comprehensive cloud security. But simple threat detection is not the only benefit associated with virtual firewalls. Advantages include:
- Easy cloud management. Keeping track of multi-cloud deployments is hard. Cloud-native firewalls centralize security. They apply policies consistently across all virtual machines and apps.
- Streamlined maintenance. Cloud firewall technology is simple to upgrade. Updates are provided by cloud security providers. Automation reduces the maintenance burden on IT teams compared with physical firewalls.
- Speed. Cloud users demand the ability to spin up virtual machines rapidly. Virtual firewalls make it possible to safely and quickly roll out new applications.
- Consistency. Security policies must extend to all cloud endpoints and assets. Virtualized firewalls cover the entire public cloud environment. Security teams can distribute security rules consistently from centralized dashboards.
- Affordability. Cloud firewalls are a cost-effective way to secure hybrid virtual environments at scale. Cost benefits are enhanced by easy scaling to add more bandwidth. And companies benefit from lower exposure to regulatory penalties.
- Cloud-native threat detection. Above all, virtual firewalls detect security breaches and malicious actors. They secure data and applications. And they manage access to reduce east-west movement. This is not possible with physical firewall infrastructure.
How virtual firewall differs from a traditional hardware firewall
Virtual firewalls perform a similar role to physical firewall systems. But they use cloud-native techniques to filter network traffic and manage security issues.
One way to understand the difference is as follows:
- Hardware firewalls protect local networks from external attackers. Virtual firewalls protect decentralized virtual networks.
Virtual firewalls have a different set of security features. But the core role is similar. All firewalls seek to block malicious attackers and allow legitimate access.
Virtual firewalls manage traffic flows into the public cloud. They create zones of trust by applying security policies in specific contexts.
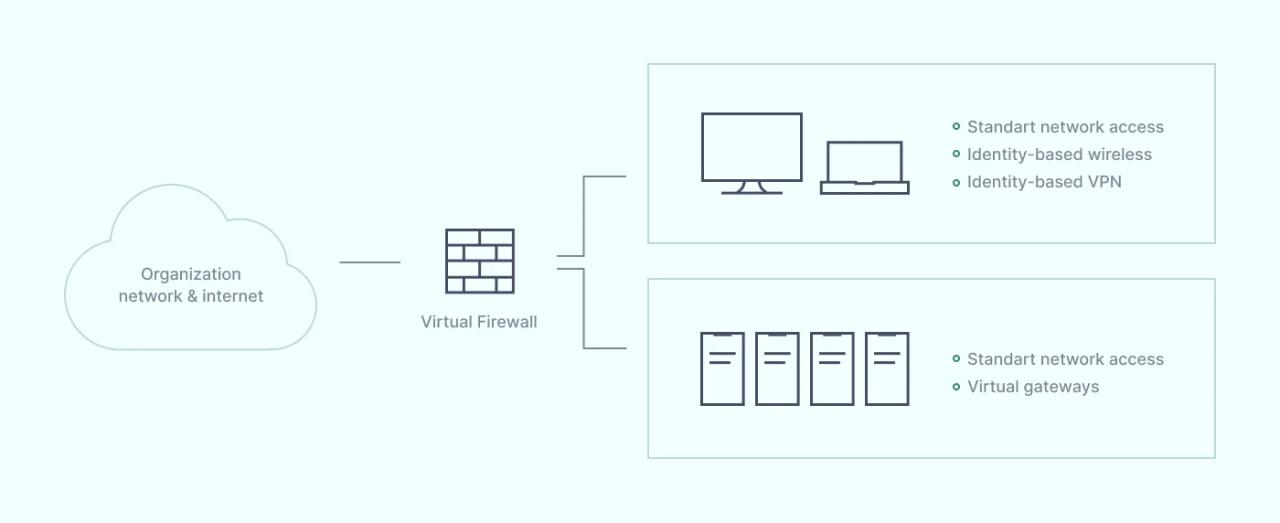
A virtual firewall exists within the cloud as a virtual machine. This virtual appliance operates as a cloud portal for external users. The firewall connects diverse cloud applications and data containers. And it applies cloud security rules across the entire virtualized environment.
Physical firewalls are deployed between the external internet and local networks. They screen traffic entering and leaving the network. They generally only apply security policies at the point of entry.
Physical firewalls connect to routers, servers, or individual workstations. But this does not suit cloud deployments. Users must backhaul data from cloud environments to the physical firewall – a complex and inefficient procedure.
Common use cases of virtual firewalls
Real-world use cases show that virtual firewalls are a crucial security solution. Here are some contexts where cloud firewalls make a major difference.
Cloud-based infrastructure protection
The cloud helps companies store data, communicate globally, and run virtualized infrastructure. Cloud infrastructure needs constant protection. Hardware firewalls are poorly placed to provide this. Virtual firewalls are ideally suited to protecting virtual traffic on complex cloud deployments.
Network segmentation
Network segmentation limits movement between different applications and devices. In the cloud, companies need to put in place barriers between virtual machines. Cloud firewalls perform this role, using logical separation to block east-west movement. Only authorized users can access sensitive data. Intruders are contained and their freedom is limited.
Protecting virtualized environments
Virtualized environments present specific security challenges. Company security services must ensure secure remote access. They must track access requests and detect malware. Security systems must also handle changes to cloud architecture across all users and branch locations. Virtual firewall protection is flexible and adaptive. It scales as cloud deployments change.
Compliance with regulatory requirements
Major data security regulations like GDPR or HIPAA cover private cloud and public cloud deployments. Users are responsible for securing customer data held in cloud containers. Virtual firewalls screen access to confidential data and apply segmentation. This makes it easier to meet regulatory demands.
Choosing the right virtual firewall solution
Not all virtual firewalls are equal. Solutions come with varying features and price points. And some products may have compatibility issues with the host operating system on cloud platforms. Planning the right virtual firewall purchase matters.
What to consider when selecting a virtual firewall solution
Factors to take into account when commissioning firewalls for the cloud include:
- Security depth – Do you need simple packet filtering or something more complex? Cloud firewalls can include Intrusion Prevention Systems (IPS) and packet inspection. Or they may leverage global threat databases. Extra security comes with higher costs.
- Pure cloud or hybrid? – Do you use a hybrid network featuring cloud and local infrastructure? Or will a pure cloud firewall do the job?
- User experience – Is the cloud firewall simple to set up and expand? Look for products with good support and easy scaling. Source an intuitive firewall application that provides complete visibility.
- Remote access – Many virtual firewalls manage remote access to private cloud and software-defined environments. But some are optimized for public cloud platforms. Choose a solution that combines well with remote access VPNs and IAM systems to create a secure remote work environment.
- Cost – Virtual firewalls are usually delivered via flexible subscription packages. Find a provider that matches your capacity and security needs. Some providers offer better rates for smaller deployments. Others blend security and value at scale.